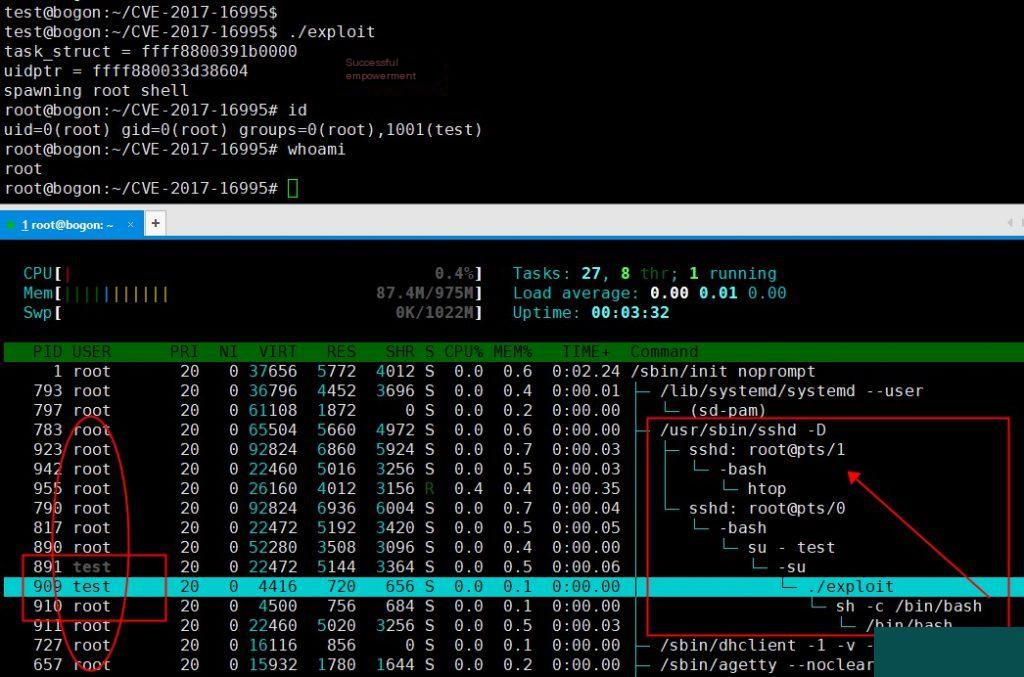
I opened two terminals simultaneously: the top one was used to perform privilege escalation through an exploit vulnerability, while the bottom one ran `htop` to monitor process changes. Observing the process chain, you can see that the exploit is executed as the `test` user, but its child process runs as `root`. Since the `test` user does not have `sudo` privileges, this behavior appears highly suspicious.
Although this method can be used to detect privilege escalation, there is a possibility of false positives. At this point, Master Li Yang and I have not yet discussed a better approach. This is just a conceptual idea for now, and further testing and discussion of more scenarios are needed. Additional updates will be provided later.
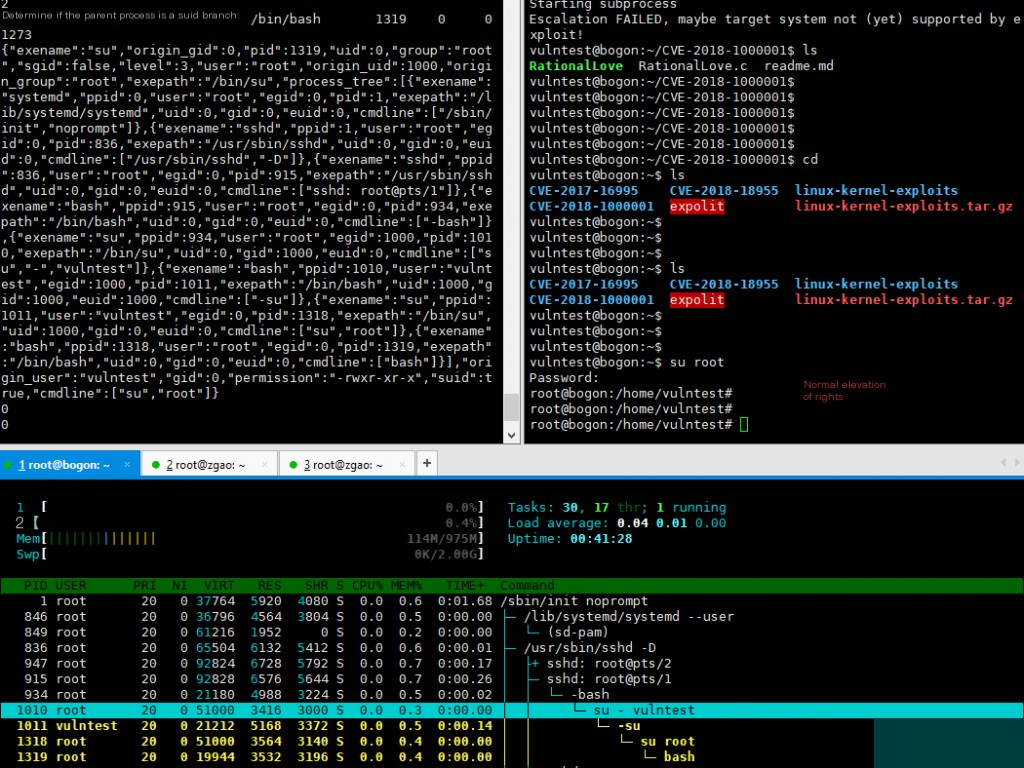
Below is a demonstration of a normal privilege escalation.
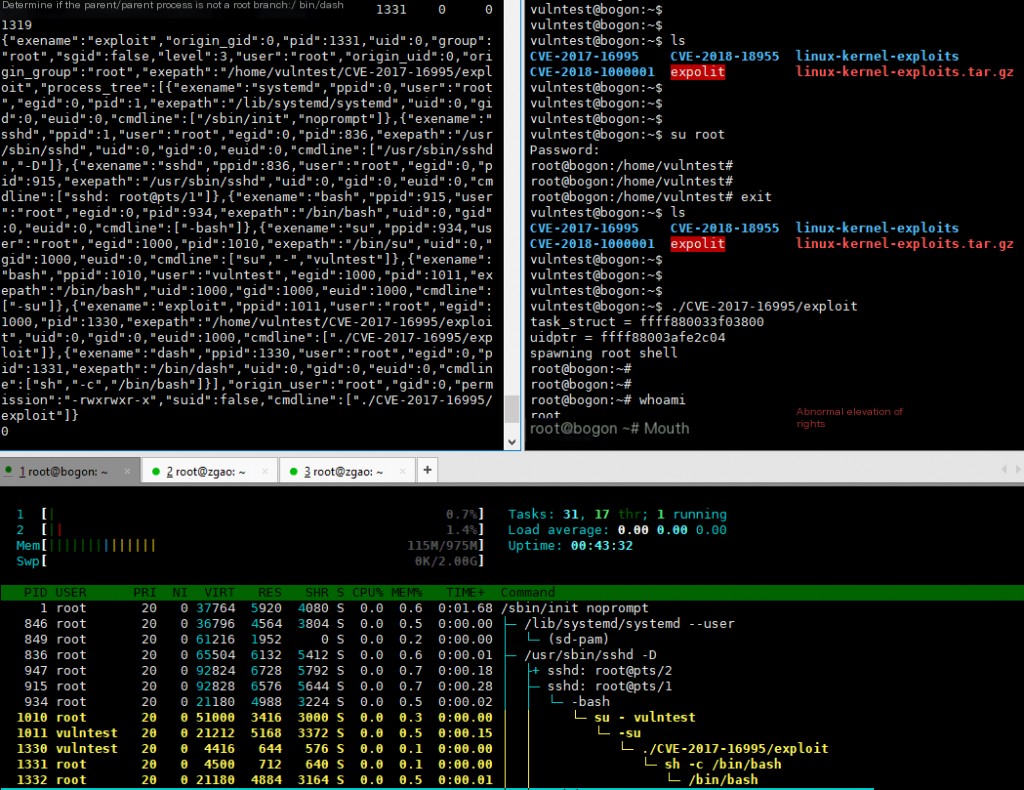
And an abnormal privilege escalation.
Regarding the privilege escalation vulnerability mentioned above, there might still be some shortcomings. If anyone has high-quality privilege escalation vulnerabilities to share, feel free to leave a comment below. After reproducing them, I will add them to this post.
During my second week of interning at Changting, I feel like I’ve made significant progress. Let’s keep pushing forward!
Update on July 31:
Solution for errors encountered when replacing the kernel version that prevent the virtual machine from booting.
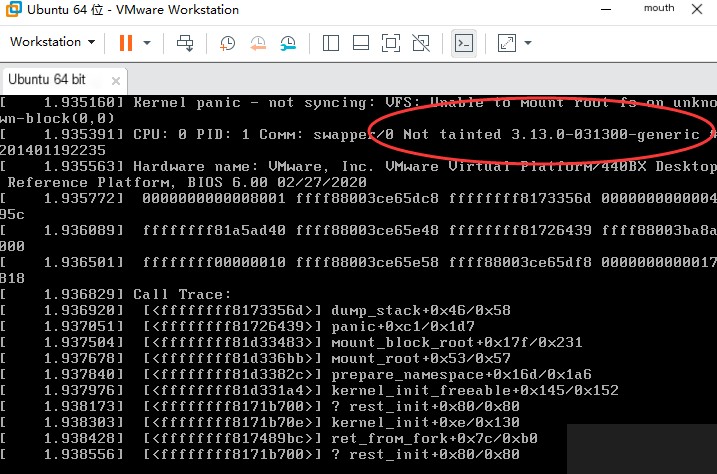
This error occurred when I replaced the kernel, causing the virtual machine to fail to boot. The screen directly displayed this interface, and I couldn’t select other kernels.

Solution: During the virtual machine startup, press and hold the `Shift` key to enter the kernel version selection menu. Select the previous kernel version, and it should work.


