1. What is botnet
A botnet attack is a collection of Internet-connected programs communicating with other similar programs in order to perform tasks. This can be as mundane as keeping control of an Internet Relay Chat (IRC) channel, or it could be used to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation.
2. What is botnet attack
A botnet attack typically first requires creating numerous botnets or a botnet army. Once the attack is initiated, these botnets are used to send network/Internet-based requests to the target system in a large quantity. These requests can be in the form of simple ping messages to bulk email messages. The attack can slow down the network/server, making it busy enough that other legitimate users are unable to access it or temporarily freeze the server.
Distributed denial of service (DDOS) is common example of a botnet attack that utilizes a number of botnet devices to send a large number of simultaneous requests/packets to the targeted system.
3. Build a policy to detect botnet attack
Before botnet attack, it will send large amounts of DNS packets to query IP address of “control” computer, to scan and sum DNS packets, we can find out the “control” computer. After extensive analysis and research, we found that some uncommon domains be used usually by botnets , for example: *.ws,*.biz and so on. About botnet domain, click following URL to learn to more information:
http://www.anva.org.cn/sites/main/list/newlist.htm?columnid=92
http://www.malwaredomains.com/wordpress/?page_id=23
http://www.cert.org.cn/
The following example will demonstrate that how to build a policy of sax2 to detect botnet attack:
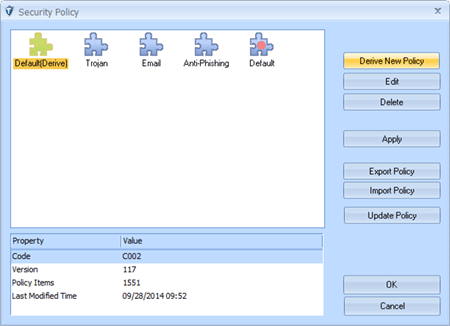
Step1: Launch Sax2 and open the “security policy” window, then derive a new policy set from the “default” policy set, see the following figure:
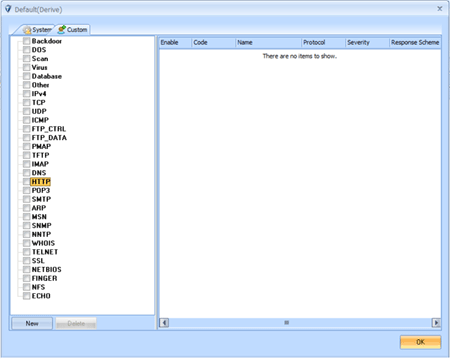
Step2: Select the new policy set and click the “edit” button on left to open setting window, see the following figure:
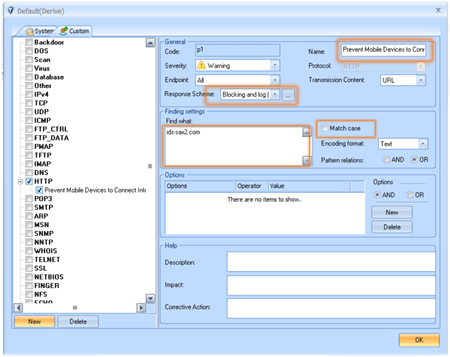
Step3: Switch to “Custom” page and select the “DNS” item in right pane, click the “New” button to create a new policy, then enter the name of policy, select ” Log” response scheme, enter botnet domains to “find what” edit box, for example: 001.sky88.cn, 024xuyisheng.com, 52z.query.kuai8.com and so on. Ok, the settings has been finished, see the following figure:
Step4: Save settings of policy and apply the new policy set, now we can botnet attack.