Preface
This article provides a practical guide to integrating Zeek with GrayLog for real-time network traffic monitoring and log visualization. It begins by introducing Zeek as a powerful, flexible network security monitor capable of deep protocol analysis and high-performance traffic inspection. The guide walks through deploying Zeek on CentOS 7 using RPM packages, configuring the NIC in promiscuous mode, and enabling JSON log output. It then details how to use graylog-sidecar and Filebeat to forward Zeek logs to GrayLog, where logs are parsed and visualized through dashboards. Key steps include setting up traffic mirroring, editing Zeek config files, and configuring GrayLog inputs and extractors. The article concludes with tips for extending functionality, such as integrating with the ThreatBook API for threat intelligence. Overall, it demonstrates a complete workflow for building a Zeek+GrayLog network monitoring solution.
1. Zeek
The Zeek Network Security Monitor:A powerful framework for network traffic analysis and security monitoring.
Zeek Network Security Monitor: A powerful framework for network traffic analysis and security monitoring, Zeek network monitoring offers deep insights into network behavior, enabling effective threat detection and incident response.
- 1. In-Depth Analysis: Zeek comes with analyzers for many protocols, enabling high-level semantic analysis at the network application layer.
- 2. Highly Adaptable and Flexible: Zeek’s domain-specific scripting language allows for site-specific monitoring policies, meaning it’s not limited to any particular detection method.
- 3. Efficiency: Zeek is designed for high-performance networks and is deployed and running on many large-scale sites.
- 4. Advanced Statefulness: Zeek maintains extensible state information about the network application layer it monitors and provides advanced archiving of network activity.
Official Documentation
Copy
https://github.com/zeek/zeek
https://docs.zeek.org/
Reference Links
Copy
https://linux.cn/article-14770-1.html
http://www.senlt.cn/article/171944181.html
https://blog.csdn.net/u013613428/article/details/110728269
After reading the article https://linux.cn/article-14770-1.html titled “Integrating Zeek with the ELK Stack”
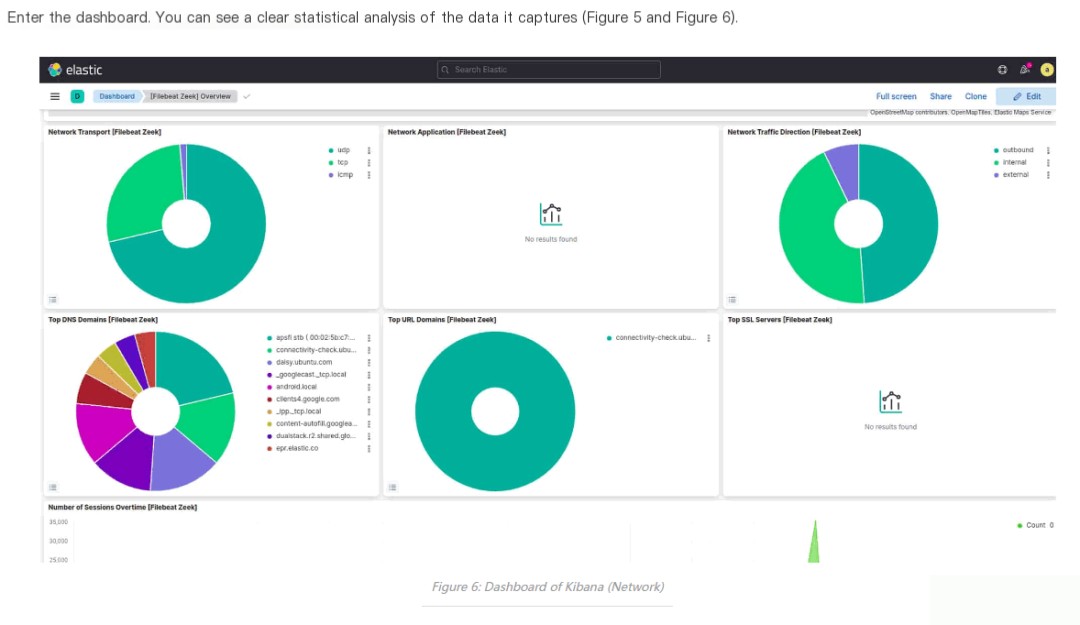
I decided to explore whether Zeek’s network traffic monitoring logs could be sent to GrayLog and visualized there.
Summary of the implementation approach and issues to be addressed:
- 1. Zeek deployment (whether it can be deployed via RPM packages, as compiling is too time-consuming)
- 2. Traffic mirroring: how to configure the Zeek server’s NIC in promiscuous mode and how to configure switch traffic mirroring
- 3. Zeek traffic analysis log reading: convert Zeek logs to JSON format, use graylog-sidecar + filebeat to read them, and extract fields using a JSON extractor
- 4. Querying and configuring dashboards in GrayLog
The detailed implementation process is as follows:
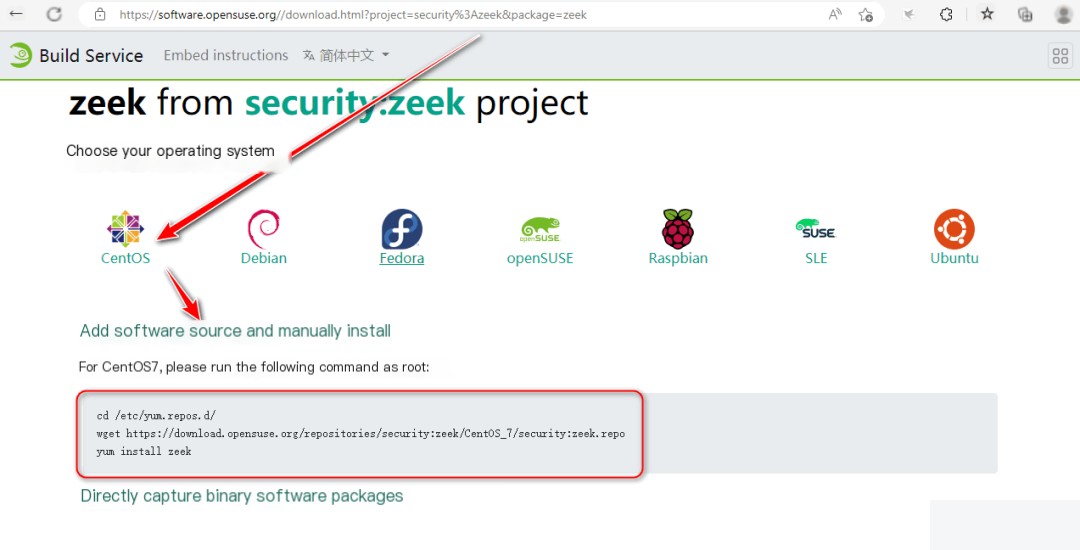
2. Download and Deploy Zeek Using CentOS7 RPM Packages
Copy
https://zeek.org/get-zeek/
Due to network speed issues, I manually downloaded the necessary Zeek RPM dependency packages in advance.
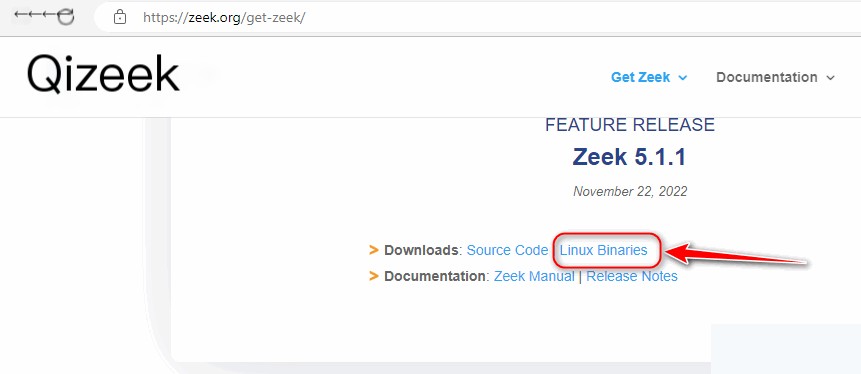
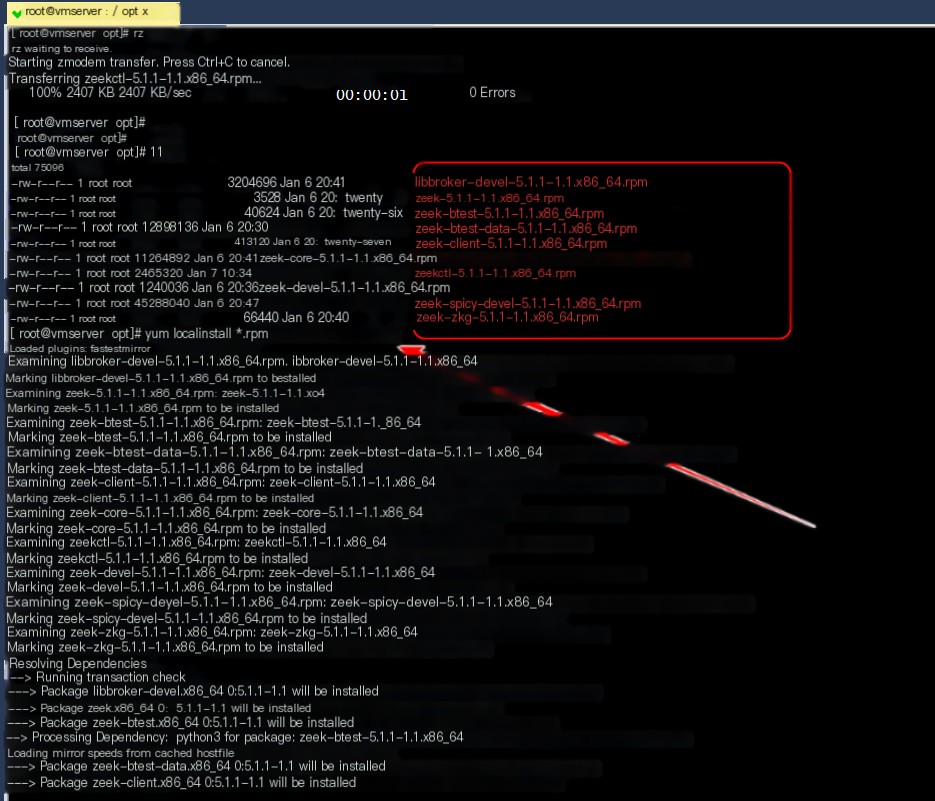
1. Install Zeek for Zeek network monitoring
Copy
yum localinstall *.rpm
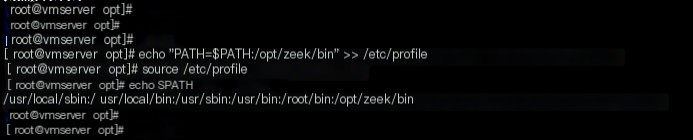
2: Add /opt/zeek/bin to the PATH environment variable for Zeek network monitoring
Copy
echo "PATH=$PATH:/opt/zeek/bin" >> /etc/profile
source /etc/profile
echo $PATH
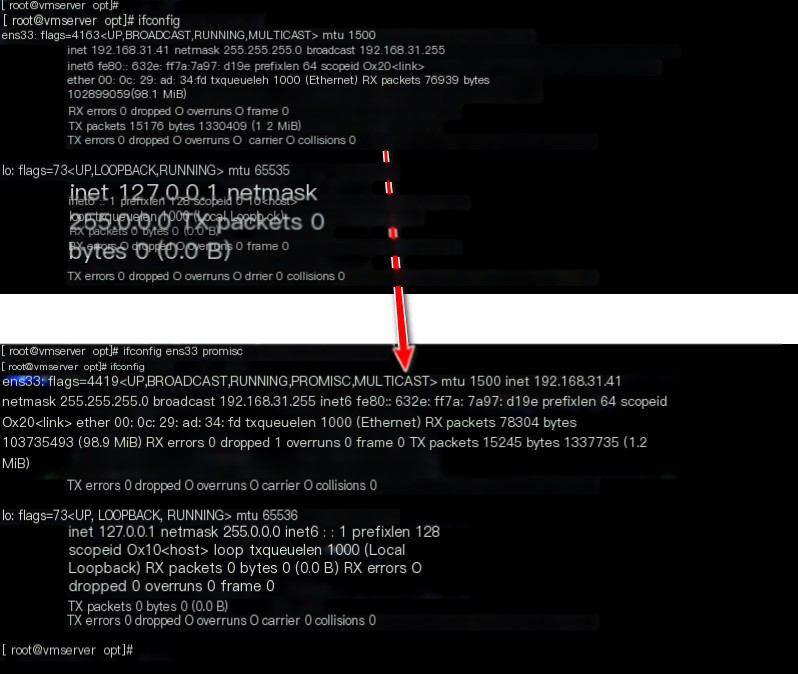
3. Enable promiscuous mode on the NIC for Zeek network monitoring
Copy
ifconfig ens33 promisc
Switch traffic mirroring configuration is not demonstrated here. Please refer to the article in the following link and configure it based on your actual network environment:
Copy
https://blog.csdn.net/u013613428/article/details/110728269
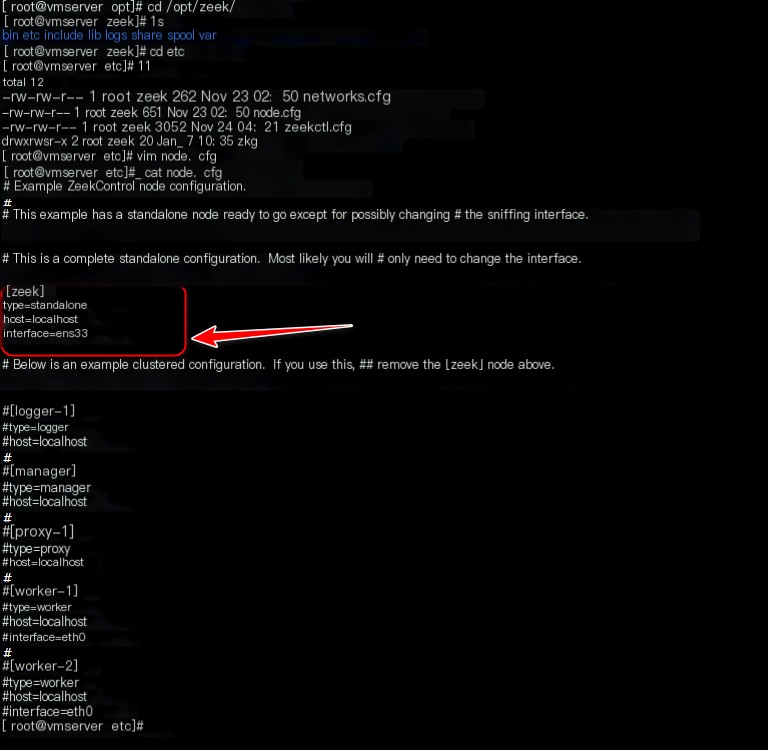
4. Edit the ‘node.cfg’ file for Zeek network monitoring
Copy
cd /opt/zeek/etc
vim node.cfg
Modify the interface to match the actual NIC
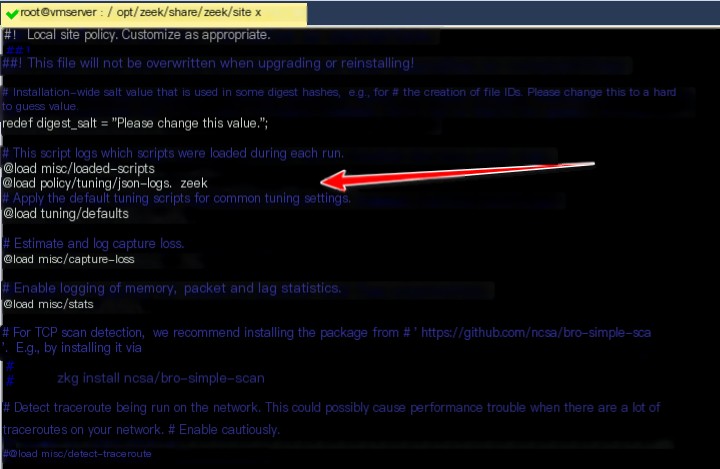
5. Edit the ‘local.zeek’ file for Zeek network monitoring
Copy
cd /opt/zeek/share/zeek/site/
vim local.zeek
Add the following line at the specified location:
@load policy/tuning/json-logs.zeek
6. Start Zeek
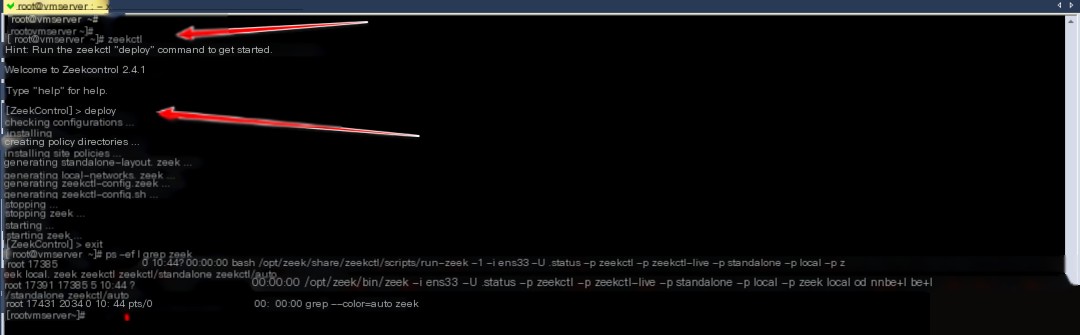
Copy
zeekctl
[ZeekControl] > deploy
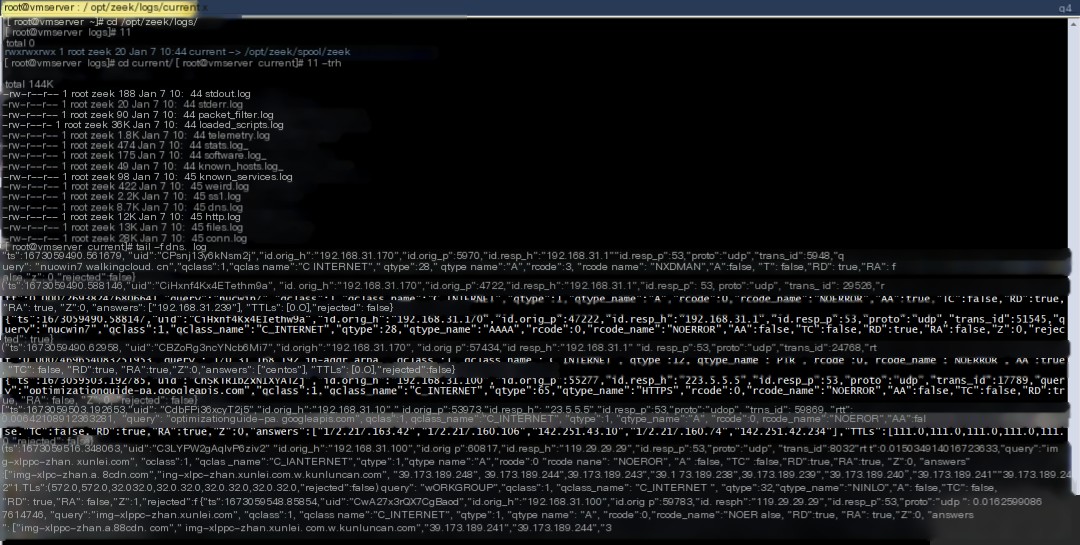
7. View Zeek network monitoring traffic analysis logs
Copy
cd /opt/zeek/logs/
cd current/
ll
Currently, all logs are in JSON format.
3. Deploy graylog-sidecar + filebeat to Read Zeek Logs
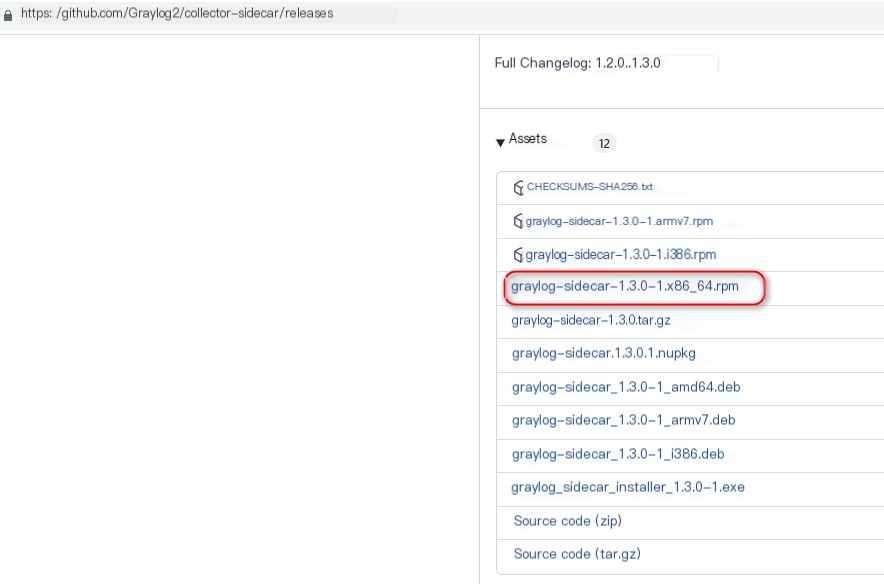
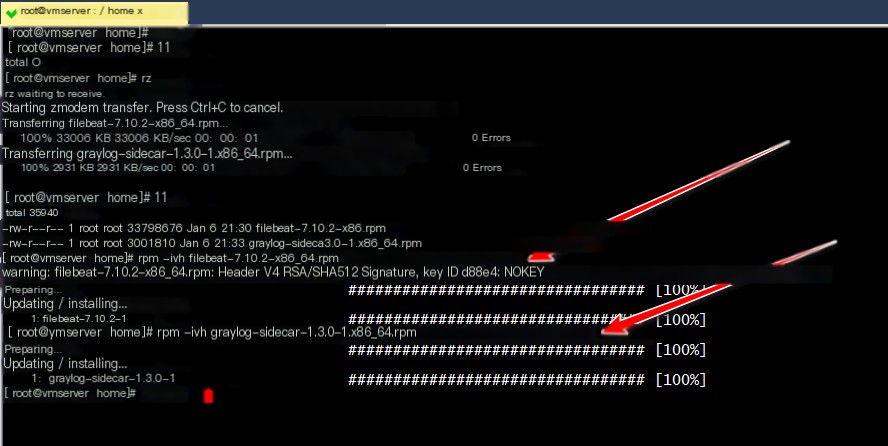
1. Download and install the RPM packages for graylog-sidecar and filebeat for Zeek network monitoring
Copy
https://github.com/Graylog2/collector-sidecar/releases
https://mirrors.cloud.tencent.com/elasticstack/7.x/yum/7.10.2/filebeat-7.10.2-x86_64.rpm
rpm -ivh filebeat-7.10.2-x86_64.rpm
rpm -ivh graylog-sidecar-1.3.0-1.x86_64.rpm
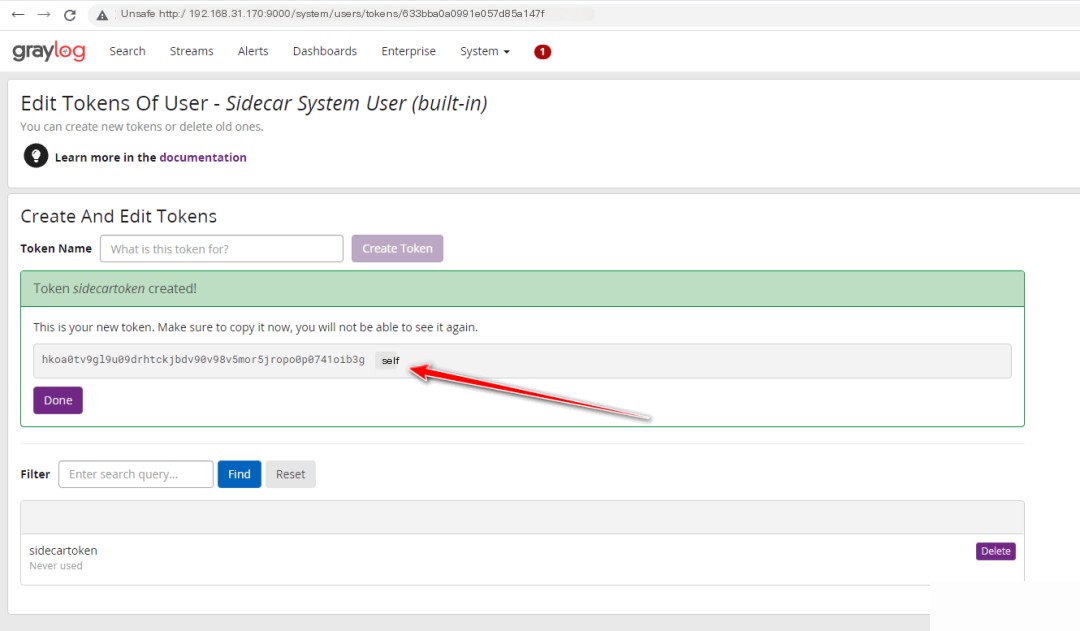
2. Generate a token for the sidecar and update its configuration for Zeek network monitoring
Copy
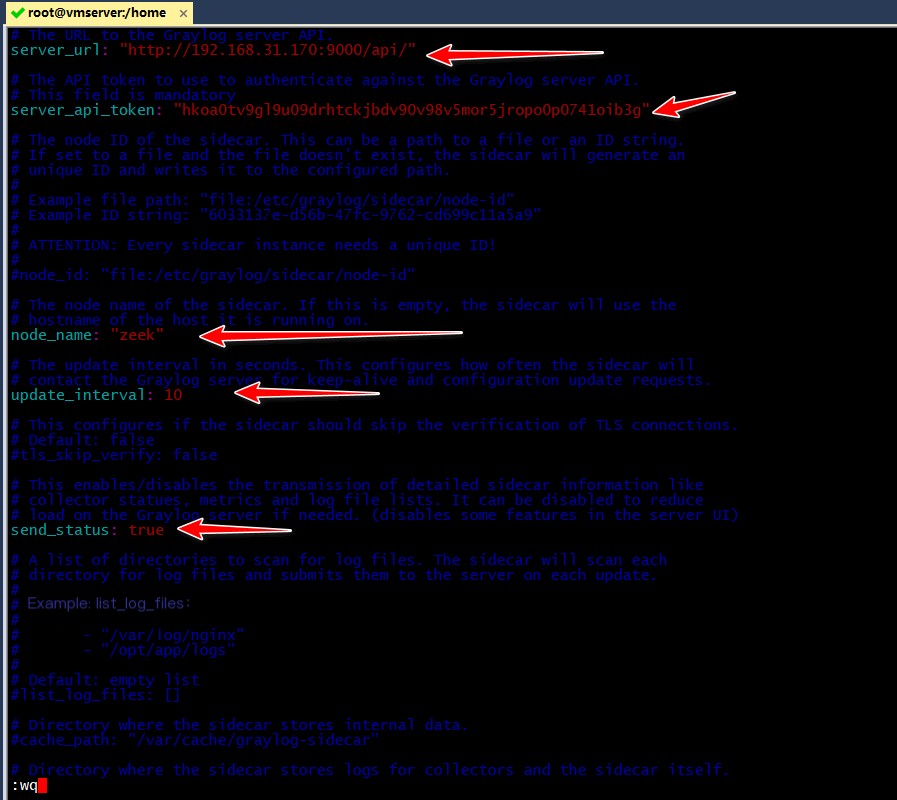
vim /etc/graylog/sidecar/sidecar.yml
Modify the following 5 settings:
server_url: "http://192.168.31.170:9000/api/"
server_api_token: "hkoa0tv9gl9u09drhtckjbdv90v98v5mor5jropo0p0741oib3g"
node_name: "zeek"
update_interval: 10
send_status: true
3. Start graylog-sidecar and apply the configuration
Copy
graylog-sidecar -service install
graylog-sidecar -service start
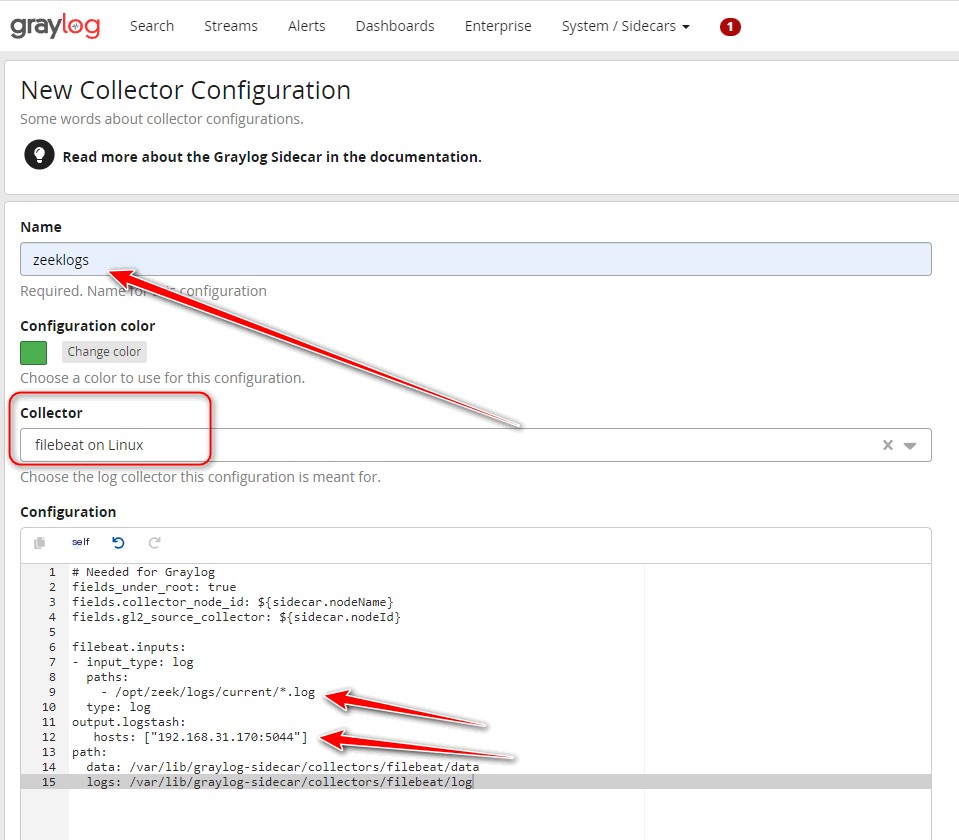
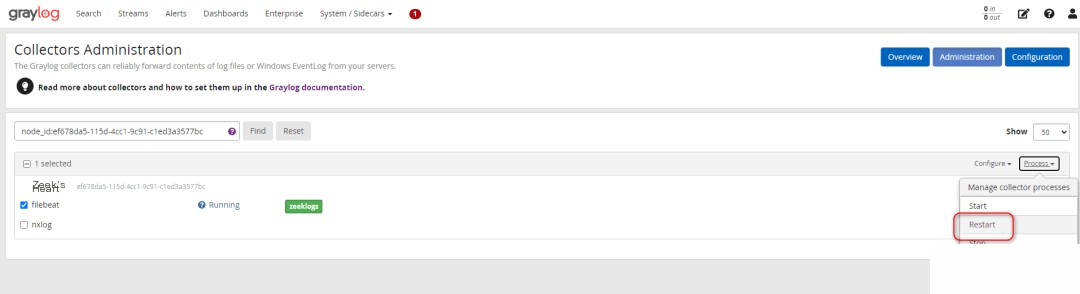
4. Configure a Beat-type Input in Graylog
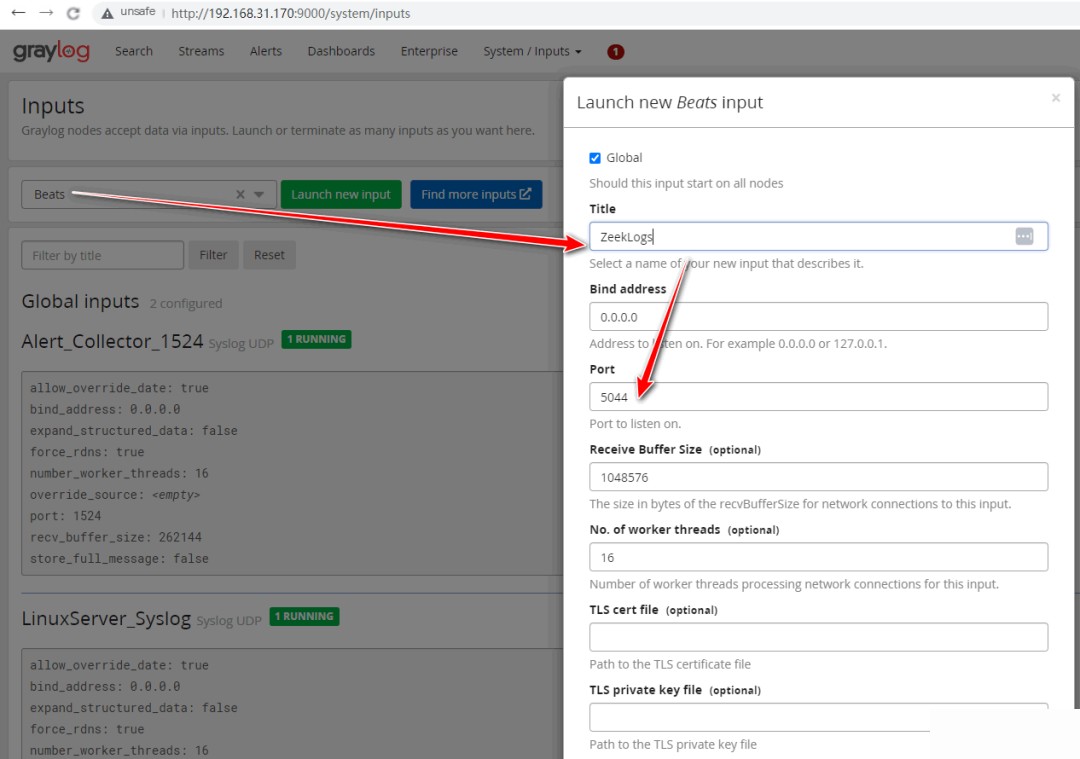
Open port 5044 in the firewall
Copy
firewall-cmd --permanent --zone=public --add-port=5044/tcp
firewall-cmd --reload
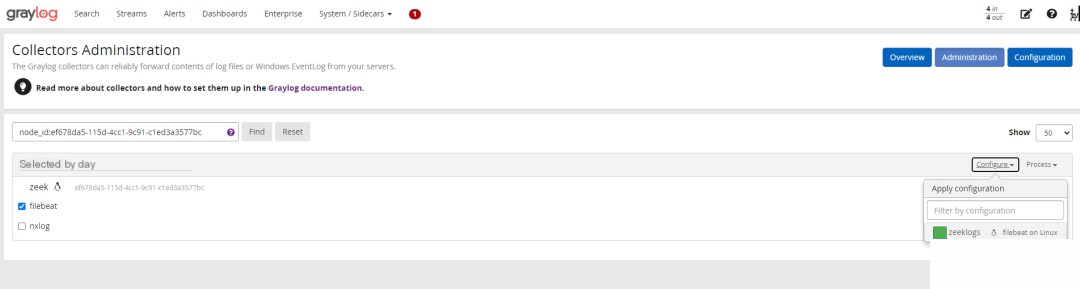
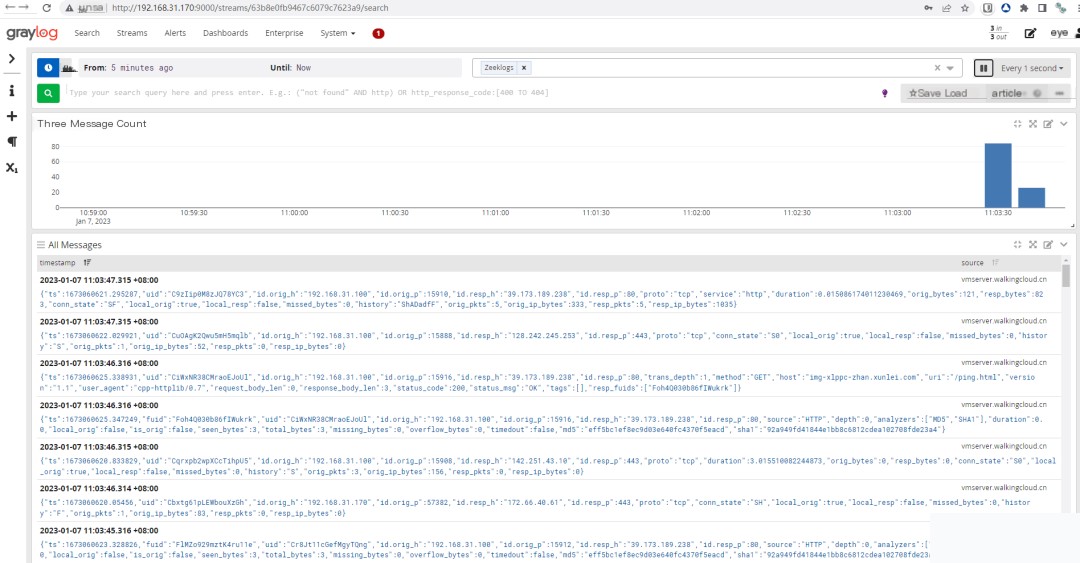
5. Confirm log reception
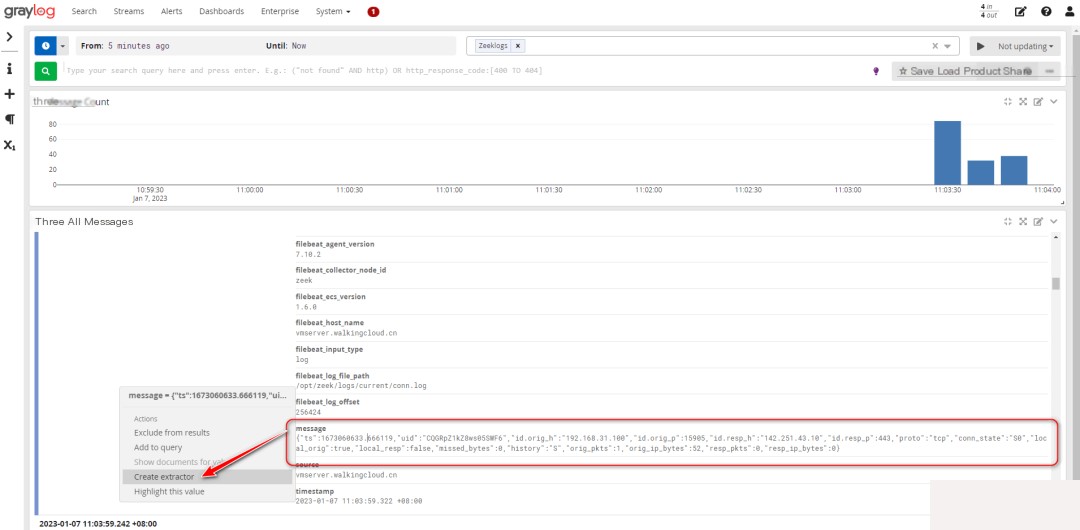
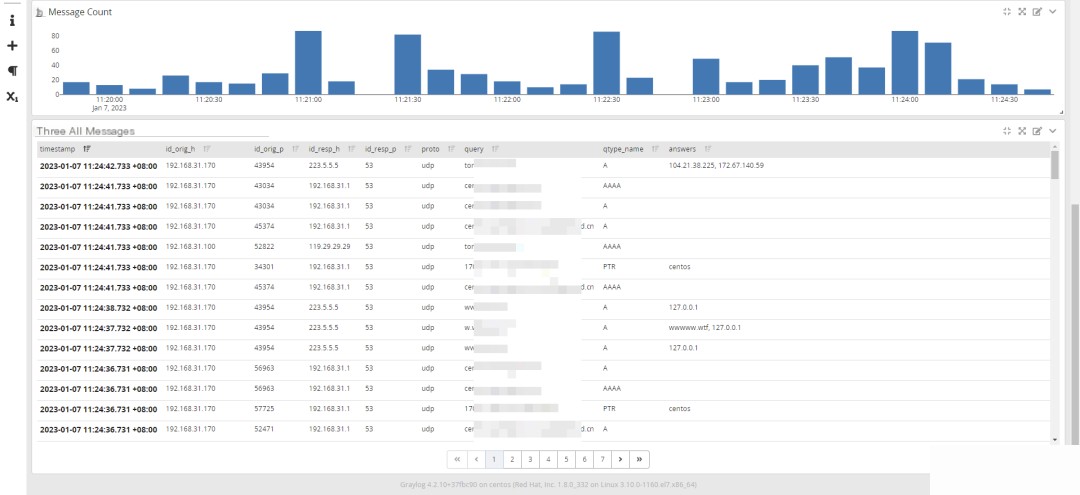
4. Configure JSON Field Extraction and Dashboard in Graylog
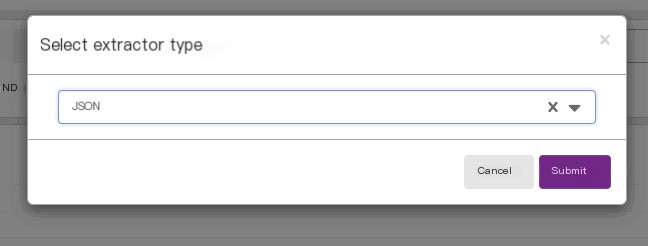
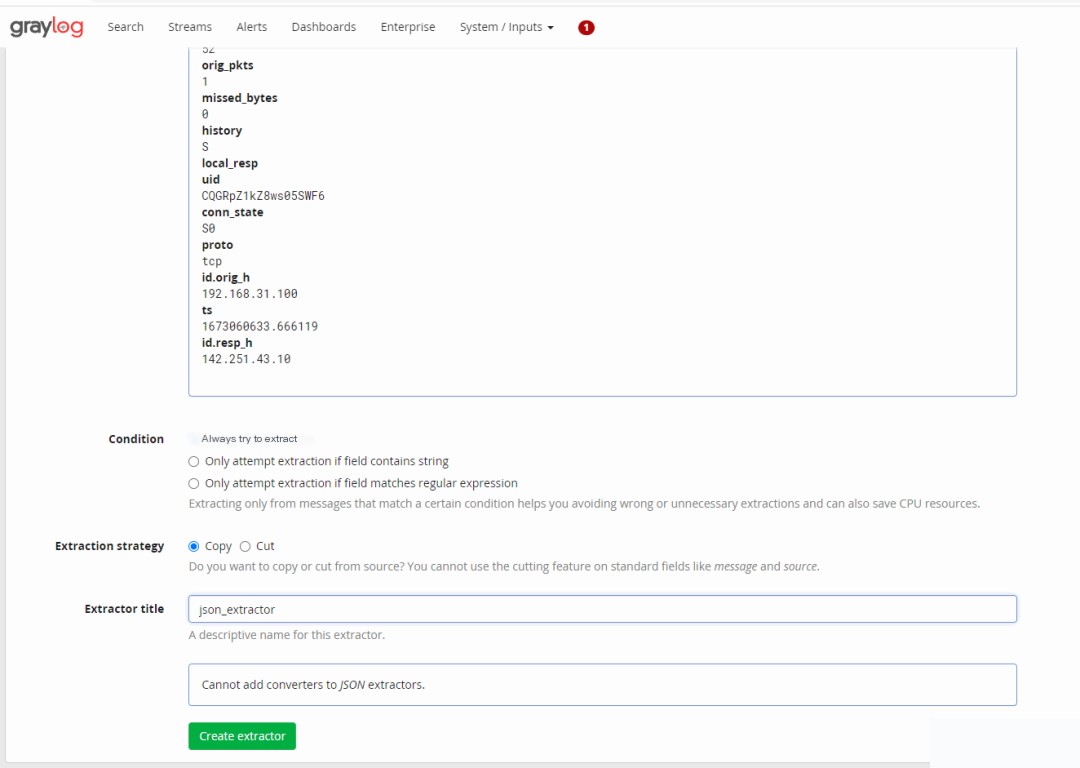
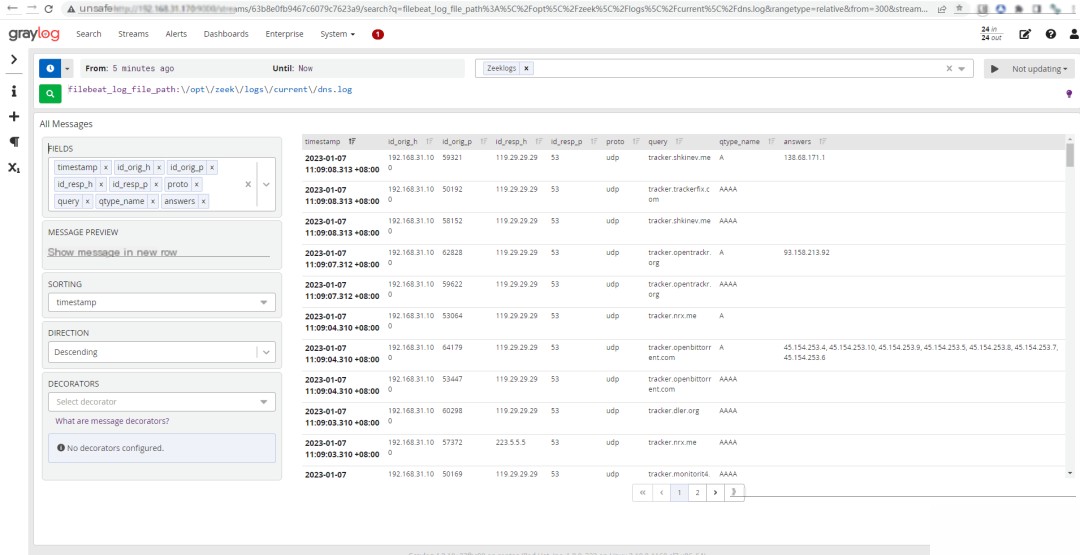
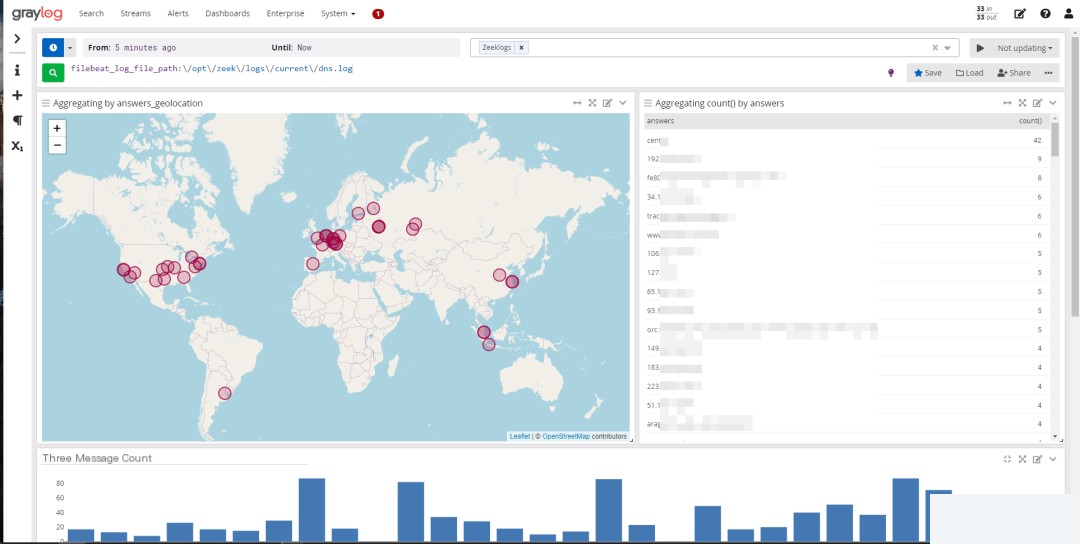
5. Summary
1. All RPM installation packages used in this article have been bundled. Download link:
Copy
Link: https://share.weiyun.com/knIqb1EA Password: bk2un9
2. Extension
If possible, Zeek traffic logs can be integrated with the ThreatBook API for correlation queries, enabling detection and alerting of abnormal DNS and other traffic.
Refer to the previous article:
Using HTTP JSONPath in GrayLog to Call ThreatBook Online Cloud API for Threat IP Identification