When conducting a security analysis on an app, it’s often crucial to verify if the app’s network interface requests are secure and whether the network protocol interactions might be vulnerable to exploitation. This requires running the app and capturing its network data interactions with the server for further analysis. Previous articles have covered capturing HTTP and HTTPS packets; this article focuses primarily on capturing the app’s TCP traffic capture and UDP traffic data. Let’s begin.
If tcpdump is not found, you can try adding the following source
Use the command to view the network interfaces that need to be captured by tcpdump, as shown below
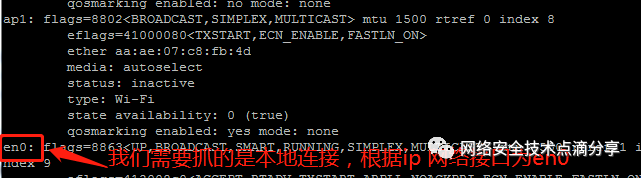
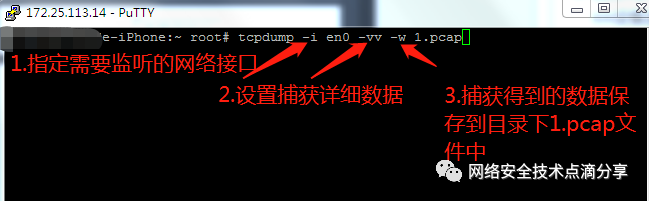
Start tcpdump to monitor the network interface identified above, capture its data stream, and save it, as shown below. Capture TCP and UDP commands:
Run the app you need to analyze to generate network data, as shown below
Continue to use tcpdump for capturing packets. Do not close the app right after running it, as we’re preparing to view the app’s traffic characteristics
After running the app, don’t immediately close the app process. We need to identify which entities are communicating with the app, for easier filtering with Wireshark later on
Open a new terminal and SSH into the iOS device again to view the app’s process PID (for example, the app process PID is 11524), as shown below
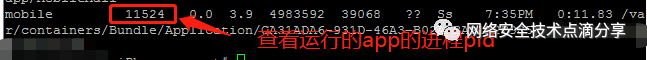
After finding the app’s process PID, check the app’s network interactions. We use lsof, which can view file usage in the system. In a broad sense, network sockets also count as file descriptors, so lsof can be used to view this information, as shown below
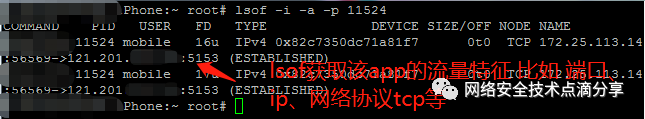
lsof -i -a -p # The process PID we found above
-i indicates listing all network connections
-a specifies the current user
-p specifies a particular process (PID)
We can then see the app’s network interactions, IP addresses, etc.
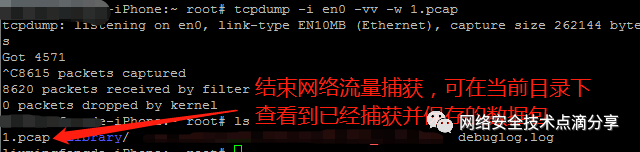
Finally, stop tcpdump to capture the app’s network data and end the packet capture

Drag Wireshark to the Applications

Use Wireshark to open the network data packets, as shown below

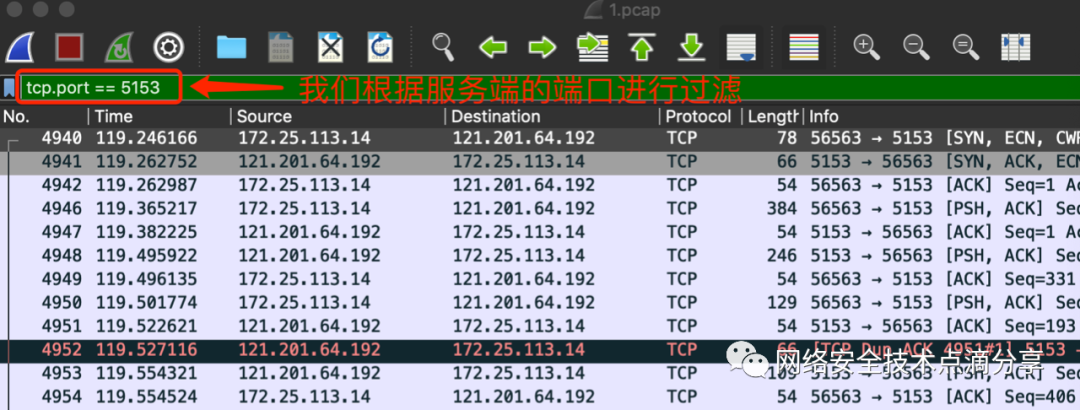
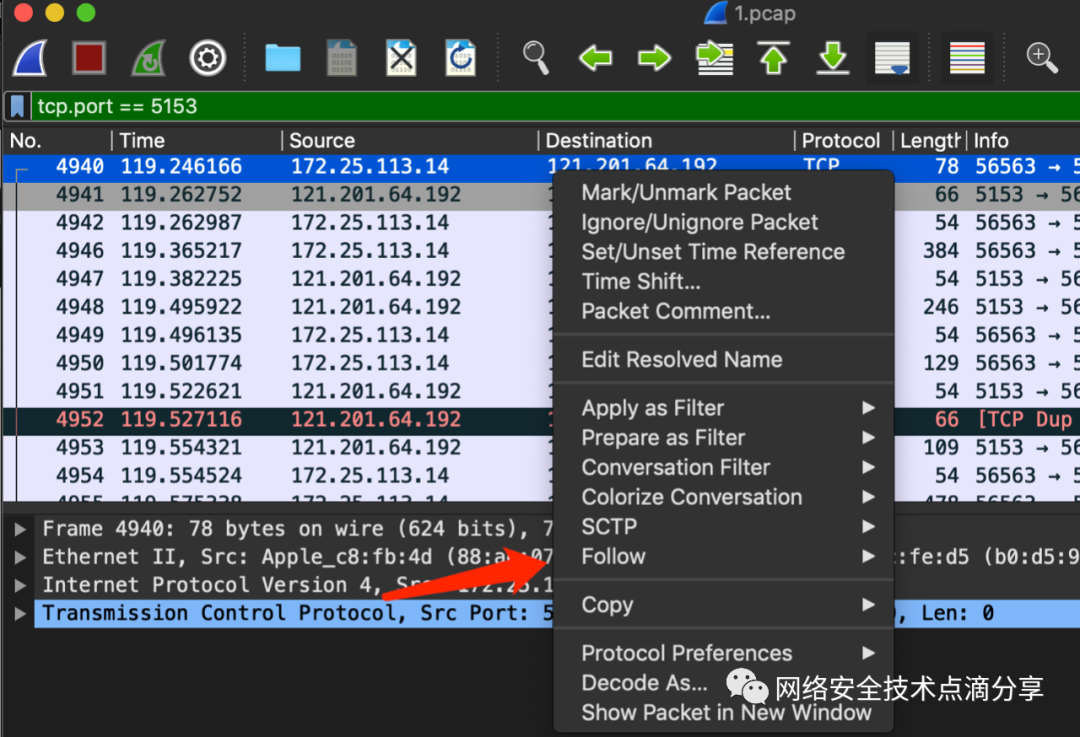
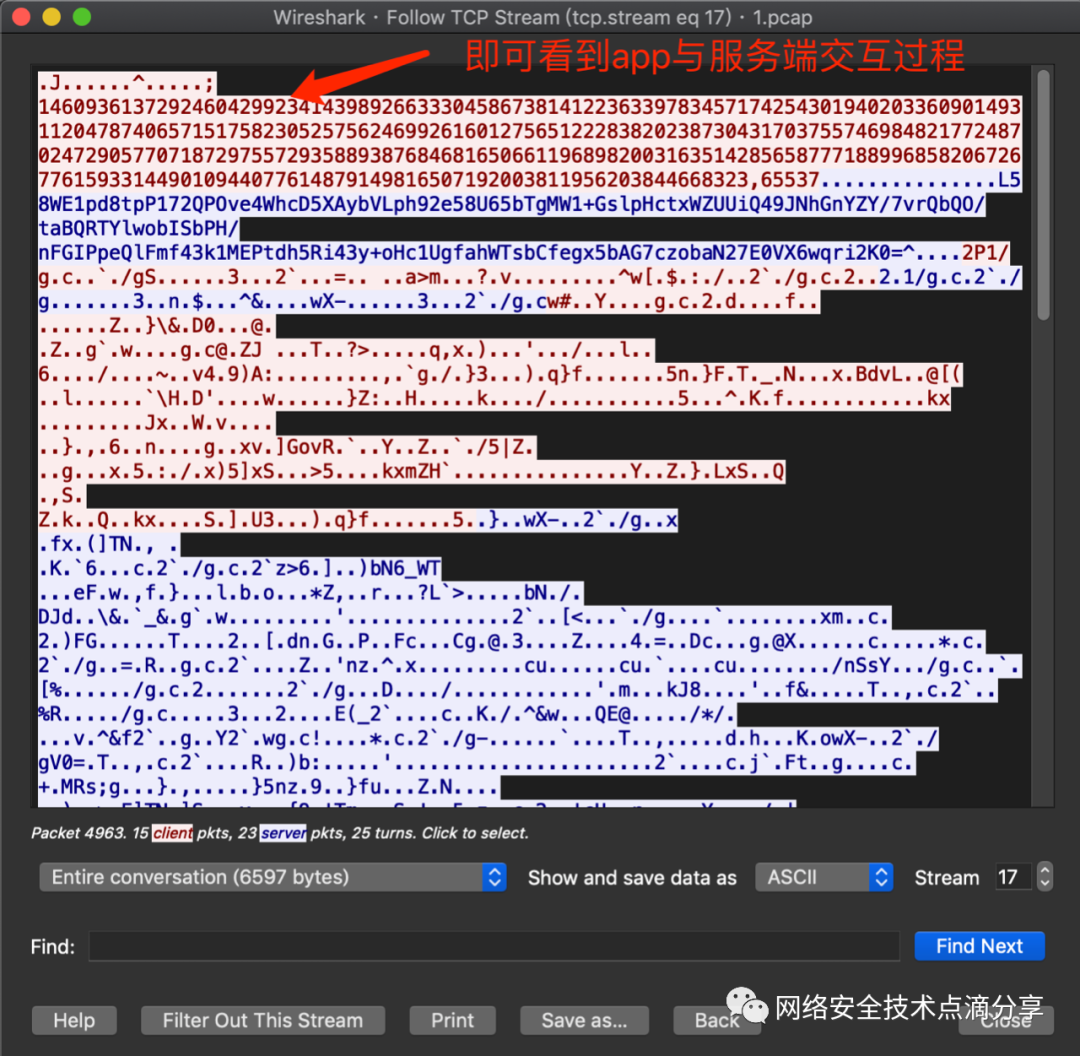
Then select the TCP stream
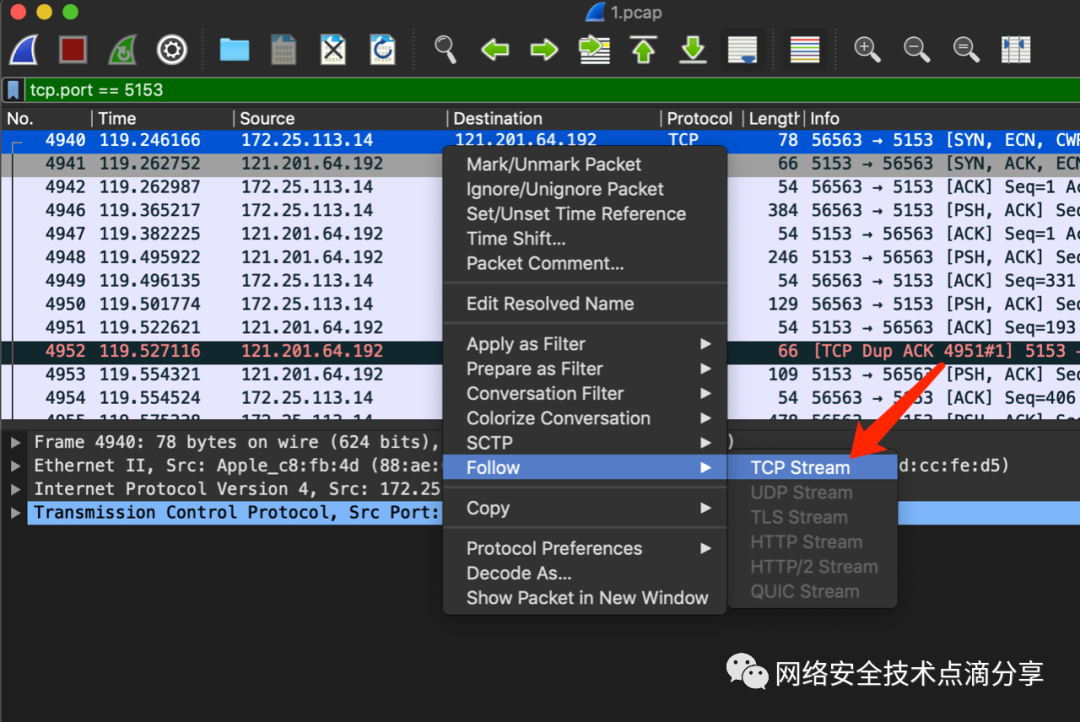
You can then see the TCP network interaction process between the app and the server