1. Experiment Content
The full alert mode of Snort generates a Snort alert file.
2. Experiment Objectives
1) Learn common usage methods of Snort.
2) Write appropriate rules and apply them based on log information.
3. Experiment Principles
1) Snort can capture and analyze packets on the network. Unlike other sniffers, it can respond and process based on defined rules. After analyzing the captured packets according to its rules, Snort can take one of five response mechanisms based on the rule chain: Activation (alert and activate another dynamic rule chain), Dynamic (called by other rule sets), Alert (alert), Pass (ignore), and Log (do not alert but log network traffic). Snort has multiple functionalities, including packet sniffing, packet analysis, packet detection, and response processing. Each module implements different functions, and all modules are integrated with Snort via plugins, making functionality expansion convenient. For example, the preprocessor plugin operates before rule-matching misuse detection, performing tasks such as IP fragment reassembly, HTTP decoding, and Telnet decoding. Processing plugins handle tasks like checking protocol fields, closing connections, and responding to attacks. Output plugins log or alert based on the processed results.
4. Experiment Content and Steps
1. Full Alert Mode of Snort
1.1 Open the host with the address 192.168.1.2. Open the terminal and enter the command “snort –c /etc/snort/snort.conf –A full”.
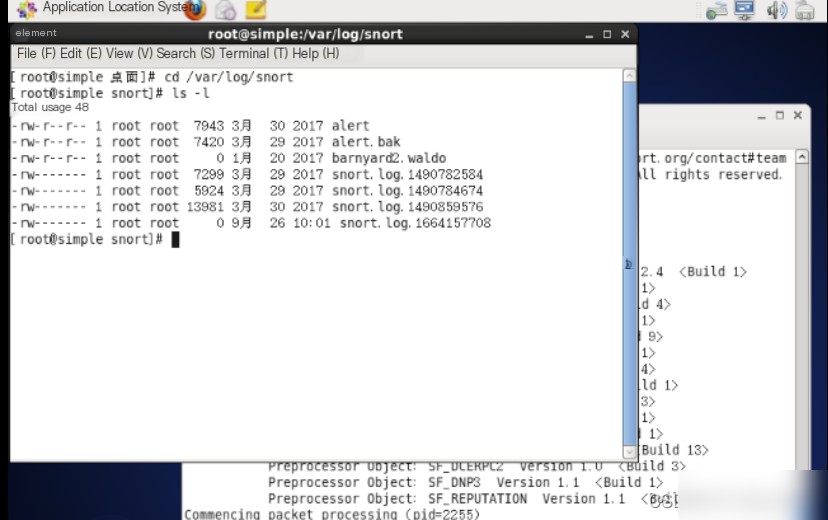
1.2 Open a new terminal and switch to the path “/var/log/snort”. View the files in this directory.
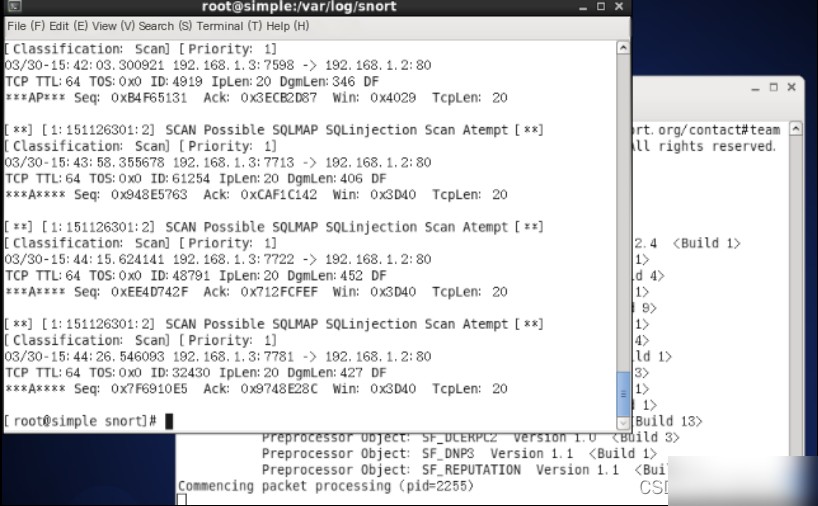
1.3 Use the `cat` command to view the contents of the alert file and find that it is not empty.
1.4 Use the `vim` command to edit the “/etc/snort/rules/local.rules” file.
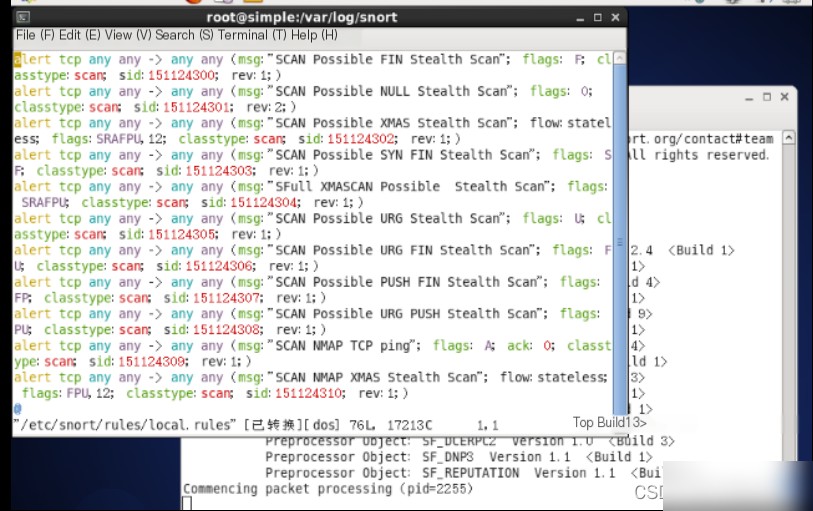
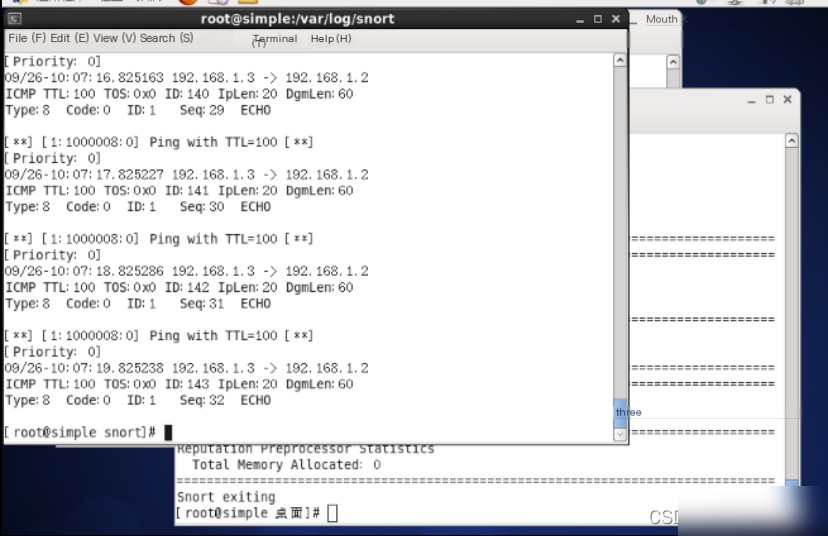
1.5 Add a Snort rule at the end of the local.rules file. The rule is: “alert icmp any any -> any any (msg:‘Ping with TTL=100’; ttl:100; sid:1000008;)”.
1.6 Switch to the host with the address 192.168.1.3 and open the cmd command window.
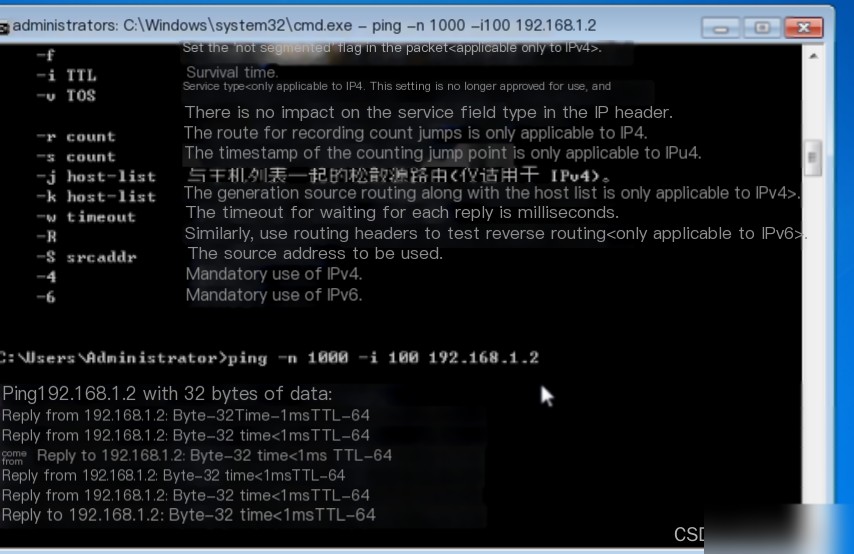
1.7 Enter the command “ping –n 1000 –I 100 192.168.1.2” in cmd and press Enter to confirm.
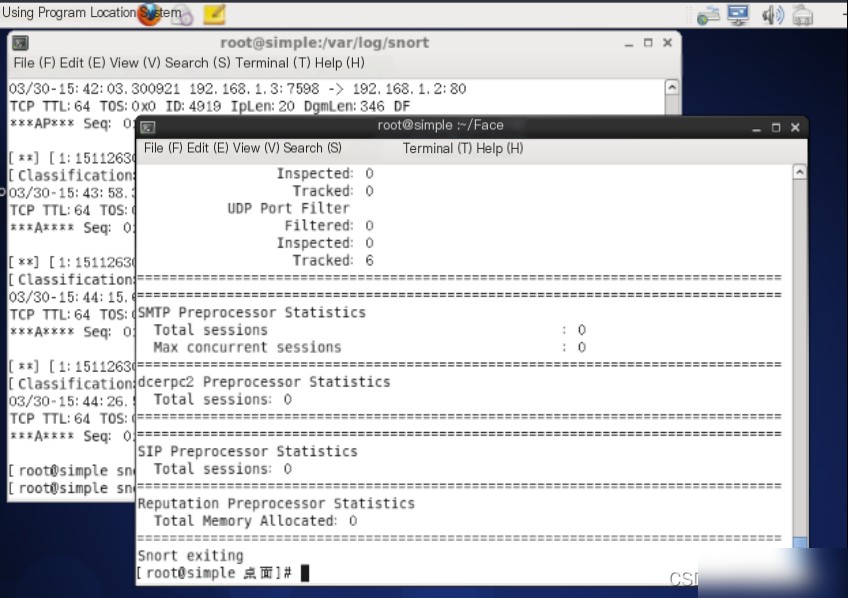
1.8 Switch back to the host with the address 192.168.1.2. Use the Ctrl+C key combination to terminate the Snort process.
1.9 Use commands to switch to the “/var/log/snort” directory and use the `cat` command to view the alert file.
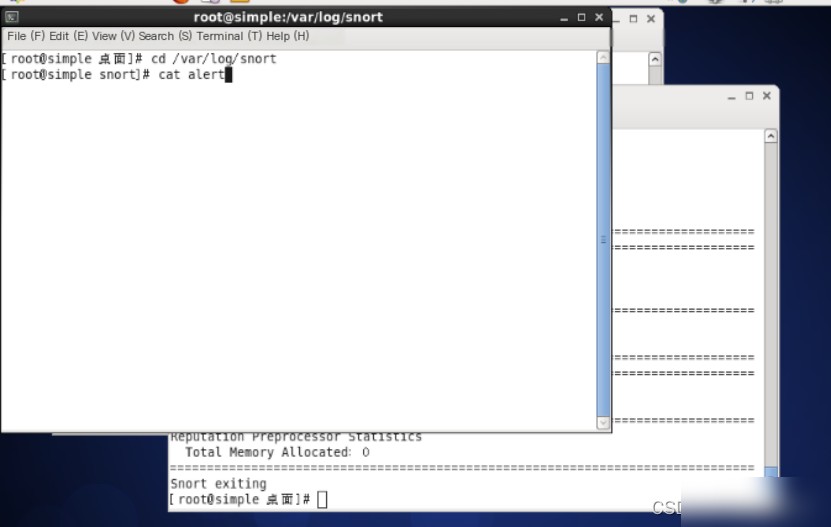
1.10 The content of the alert includes the SID (rule ID) and alert information.