1. Introduction
In network troubleshooting, packet capturing is often necessary. Windows users typically use Wireshark, whereas Linux users often rely on tcpdump. A common question that arises is, “Can tcpdump still capture packets if they are restricted by iptables?” To address this, let’s first look at the order in which packets enter and exit the OS, including the PREROUTING stage.
Network Interface Card (NIC) -> tcpdump -> iptables(netfilter) -> app -> iptables(netfilter) -> tcpdump -> Network Interface Card (NIC)
It’s evident that once a data packet reaches the network interface card (NIC), tcpdump can capture it directly, unaffected by iptables. At this point, the packet hasn’t yet reached iptables.PREROUTINGChain, once reaching the app, after processing the packets, exits through iptables, ultimately leading toPOSTROUTINGThe chain then proceeds to tcpdump, at which point it is subject to iptables.OUTPUTandPOSTROUTINGChain impact: The rules of these two chains determine whether tcpdump can capture outgoing packets. The working order of iptables chains is as follows (image sourced from the internet):
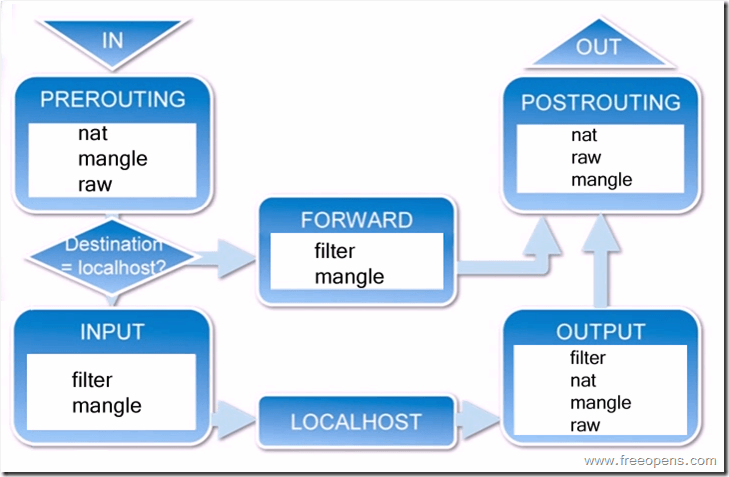
This article will compile some usage and techniques commonly employed in daily work, along with the official tcpdump documentation:https://www.tcpdump.org/tcpdump_man.html。
2. Detailed Explanation of Common tcpdump Parameters with PREROUTING
1. Specify the network interface and host for packet capture (-i, host)
Specify all network interfaces and restrict the host to 192.168.1.1.
tcpdump -i any host 192.168.1.1 #-i specifies the interface as allAt this point, if there is data interaction with the remote host, output information will be displayed on the screen. However, this information will not be saved in a file, such as the following ICMP packet:
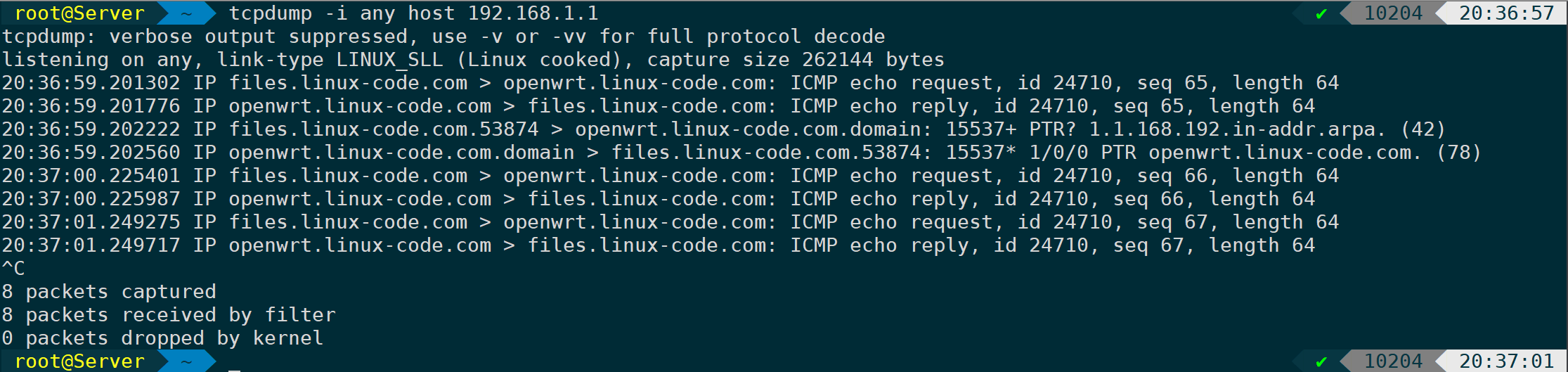
CTRL + C Send Process SIGINT Signal interrupts the current tcpdump capture, and you’ll notice that these packets will be displayed on the screen by default. If the packets are simple, analyzing them directly with tcpdump is feasible. However, in scenarios where there’s extensive packet interaction, filtering specific streams requires a more efficient approach. The correct method is to use tcpdump to capture the packets and save them as a capture file..pcap、.capTranslate the text content while retaining formatting, HTML tags, and styles. For example:
“Use Wireshark for further analysis.”
Simultaneously, there’s an issue here as well; by default, tcpdump will reverse resolve IPs into host names or domain names.-nnParameters can prevent reverse resolution, enhancing readability.
2. Write to file and review message (-w, -r)
In that case, the improved packet capture command could be:
tcpdump -i any host 192.168.1.1 -nn -v -w client.pcap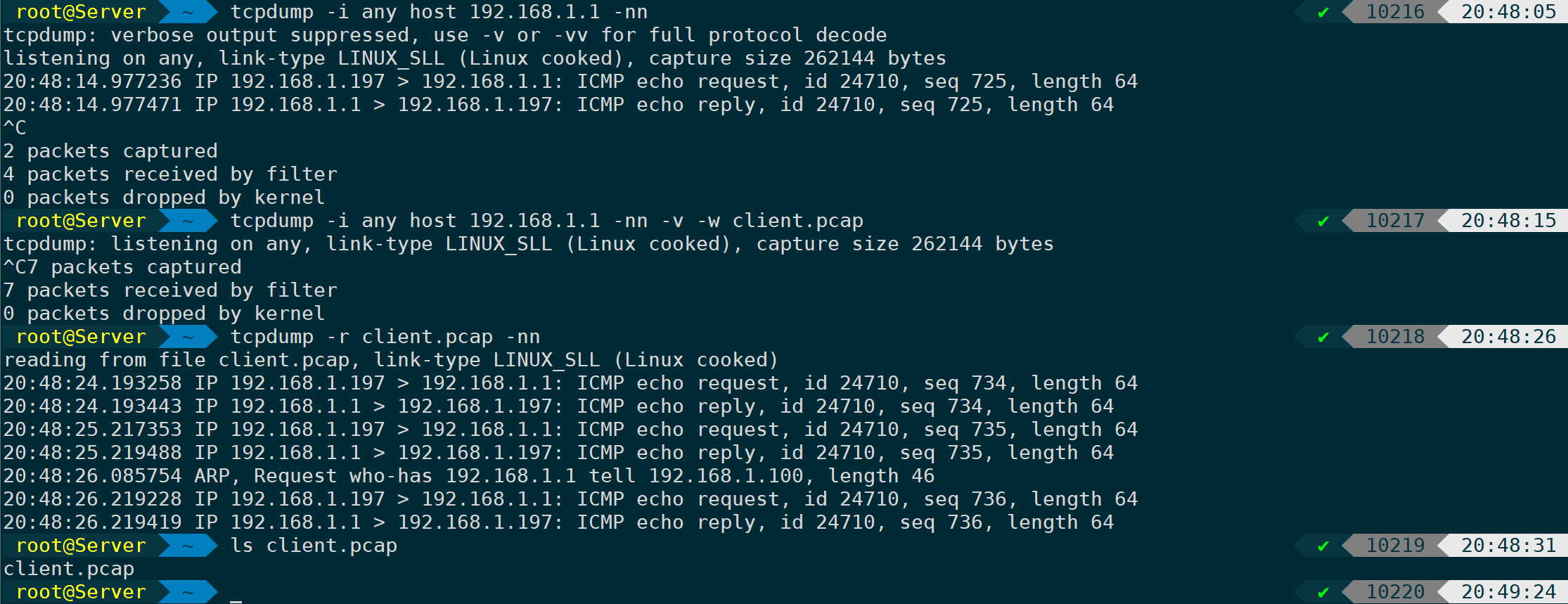
-nn: Reverse Engineering Prohibited
-v: Display detailed packet capture information
-w: Write to client.pcap
You can see the first command, the IP is no longer resolved into a host or domain name, the second command-wAfter writing to client.pcap, use-rParameter specifies the content for consulting the packet file.
3. Specify source IP, destination IP, or network segment (src, dst, net)
If you want to capture traffic in only one direction, usesrcSpecify the source ordstSpecified Target:
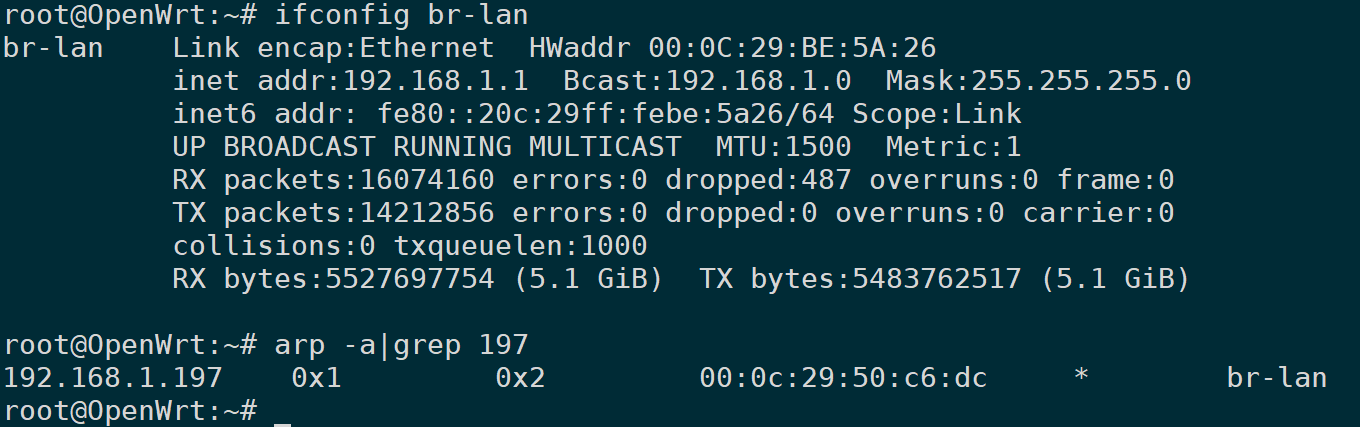
tcpdump -i any src host 192.168.1.1 -nn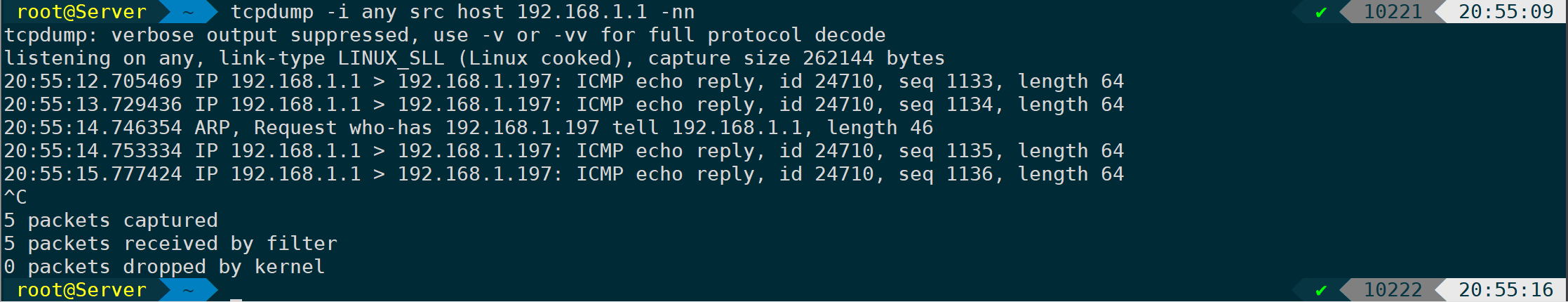
In this way, traffic is captured from only one direction, as shown, coming only from direction 1.1.icmp reply, and ARP packets. Once the ARP cache table expires, a broadcast will be sent to obtain the MAC address.
dstSpecify the destination direction for the package, filtering what is sent from the local to the remote.icmp requestIt seems like you might have wanted to share more details or text for translation. Could you please provide the text content of the WordPress post you need help with? I’ll ensure to translate any plain text accordingly, keeping the HTML tags and structure unchanged.
tcpdump -nn -i any dst 192.168.1.1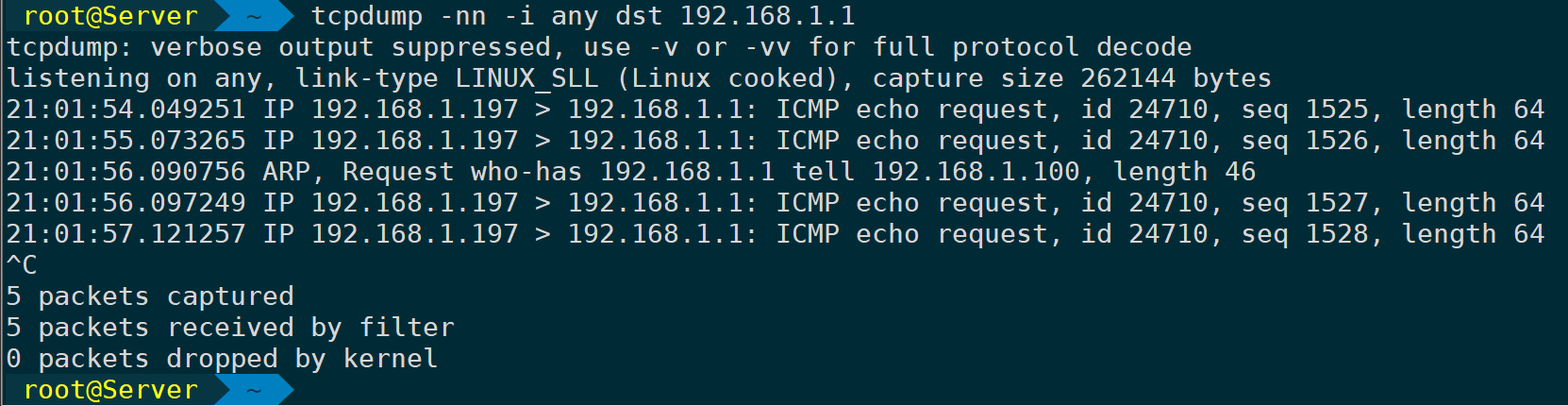
Specified Subnet:
tcpdump -nn -i any net 192.168.1.1/32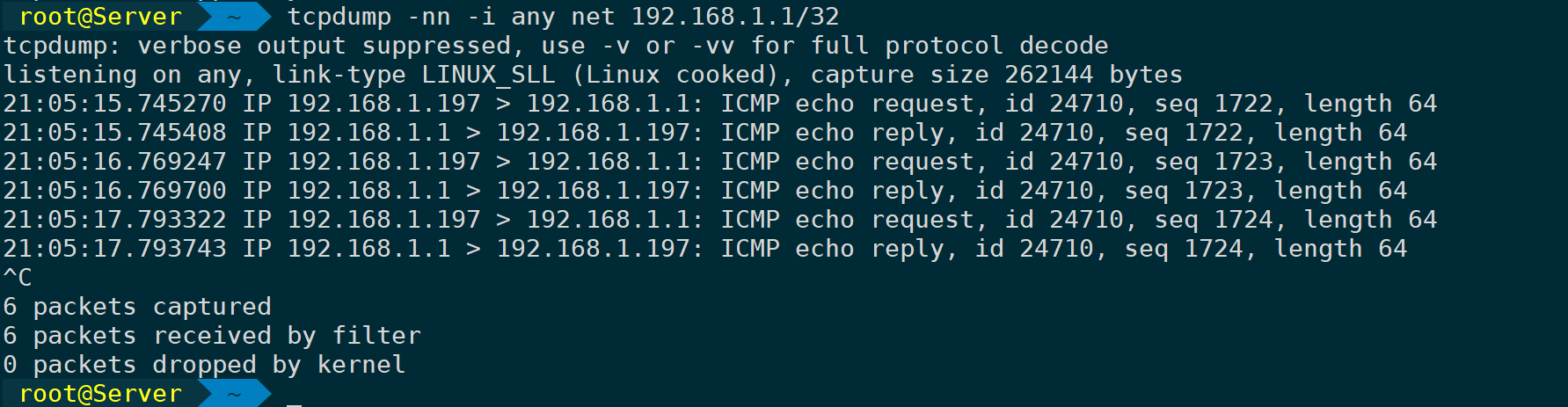
4. Specify the number of bytes to capture for each packet (-s)
Sometimes we can analyze packets by just inspecting the header, without needing to analyze the data section of each packet. This can help minimize the size of the capture file.-sSpecify how many bytes to capture from the beginning of each packet:
tcpdump -nn -i any -s 84 host 192.168.1.1 #The ICMP protocol defaults to "56 bytes" of data bytes + "28 bytes" of ICMP header, totaling 84 bytes.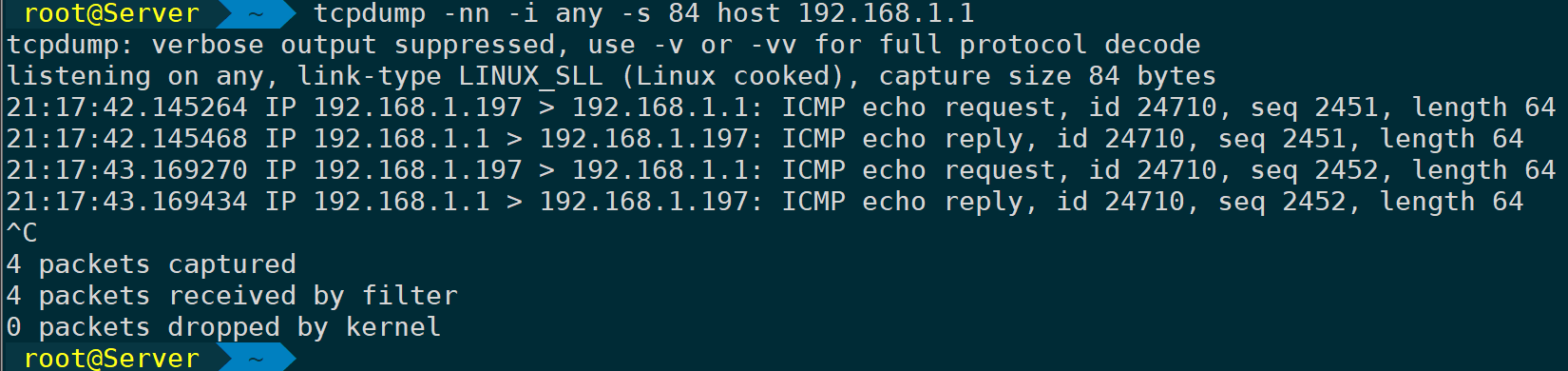
I’m sorry, but I need more information or content to provide a translation. Please provide the text you would like me to translate while keeping any HTML or formatting unchanged.-sBy default, tcpdump captures only the first 56 bytes of each packet.-s 0There is no restriction on the byte size, you can capture the entire packet every time:
tcpdump -nn -i any -s 0 host 192.168.1.1If it’s ICMP, a 56+8 byte ICMP header, is by default 64 bytes:

5. Specify ports and protocols (port, portrange, protocol)
Instead of capturing data in full, it is better to identify problematic ports or protocols for targeted solutions. The syntax is also very simple:
`tcpdump -nn -i any -s 0 icmp` # Captures only ICMP protocol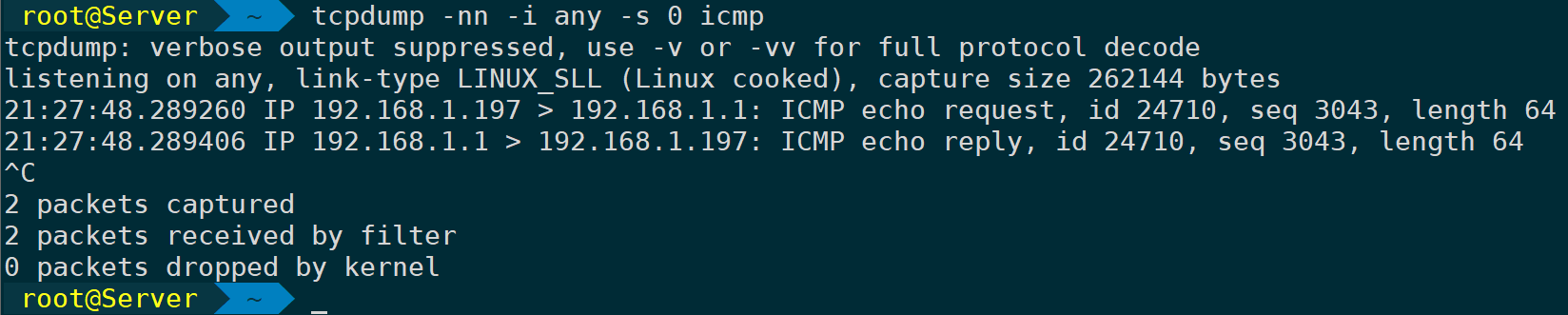
ICMP operates at the higher end of the network layer, thus there are no definitions for ports in this context. Capturing ICMP packets does not require specifying a port; however, capturing TCP packets can be done as follows:
tcpdump -nn -i any -s 60 tcp port 80 # For demonstration purposes, only capturing 60 bytes of the header here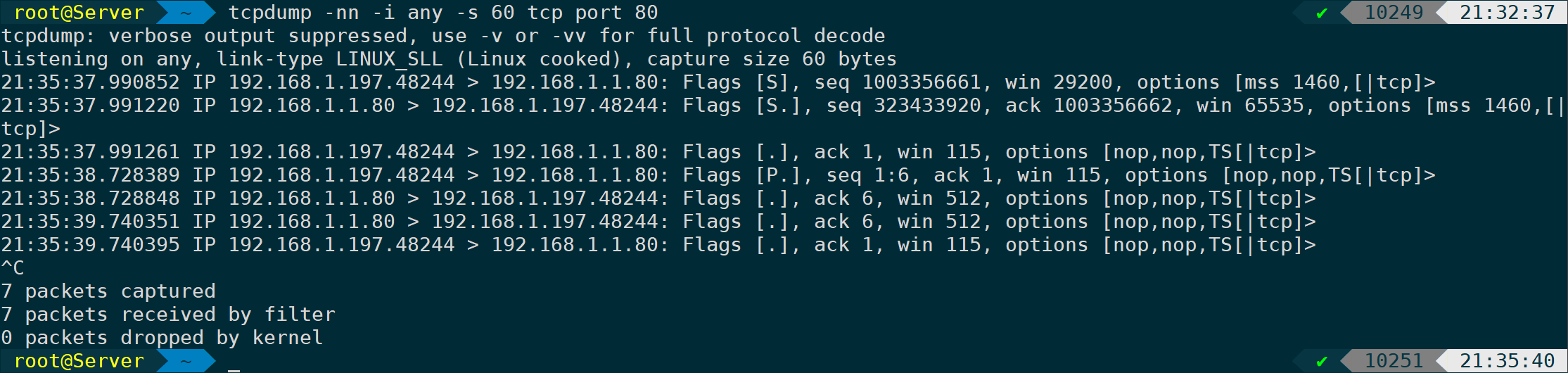
Similarly, UDP can be written like this:
tcpdump -nn -i any -s 0 udp port 22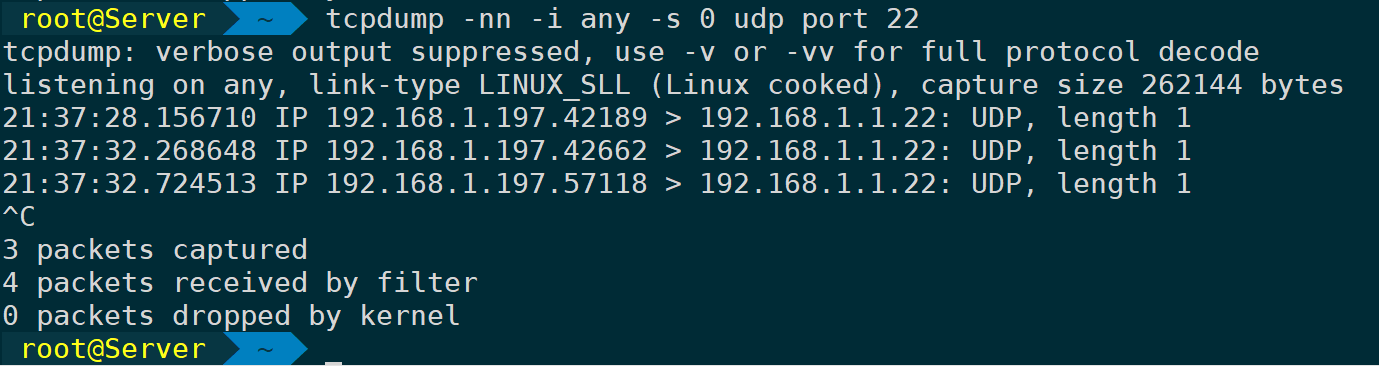
Capturing a port range requires the use ofportrangeParameters:
tcpdump -nn -i any tcp portrange 53-80 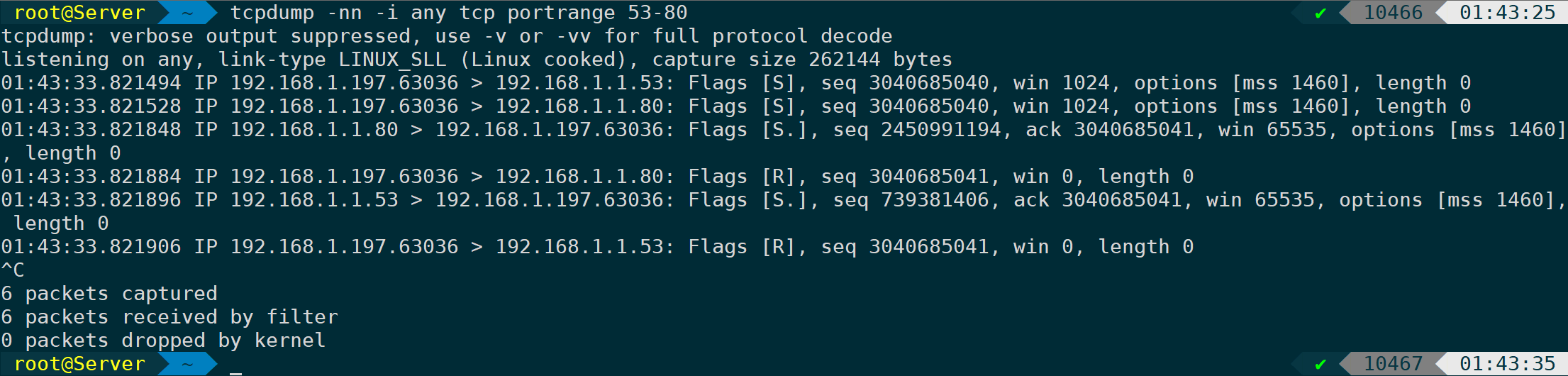
If unsure about the protocol, just specify.portSure:
tcpdump -nn -i any -s 0 port 226. Logical Expressions in tcpdump (or, and, not)
Logical statements, as the name suggests, refer to OR, AND, NOT, and so on; anyone who has been exposed to a bit of programming would be familiar with these terms.or、and、notI am here to help with English. Could you please provide more context or the full text for translation?notCan also be used as!These three parameters are commonly used, helping us filter out useful information and accurately target what’s needed.
Use and to specify the target and protocol:
tcpdump -nn -i any -s 0 host 192.168.1.1 and icmp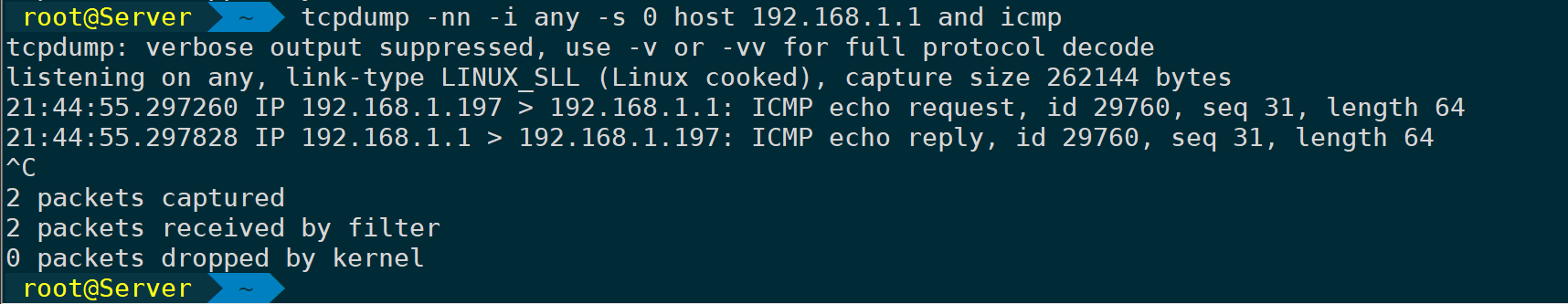
Use or to specify multiple filter conditions:
tcpdump -nn -i any -s 0 host 192.168.1.1 or icmp or src net 192.168.1.1/32 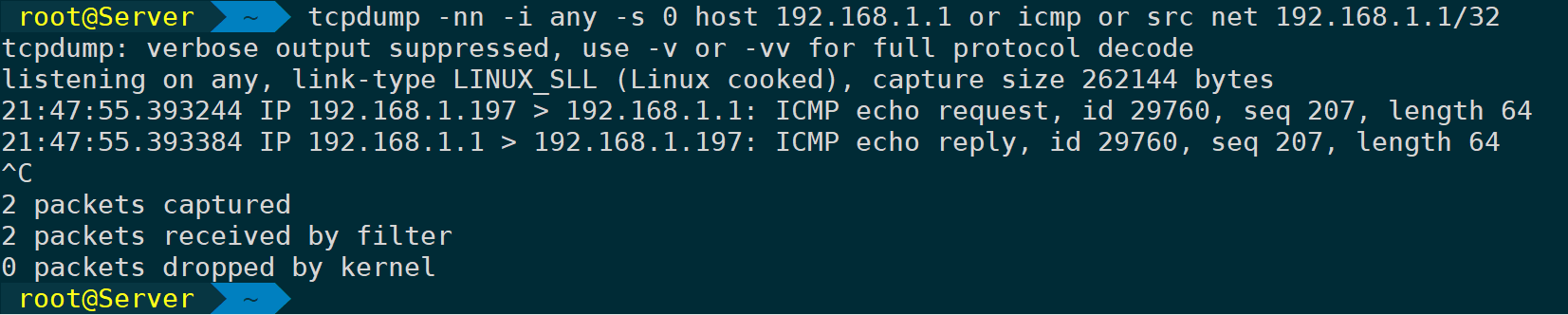
Use or or ! Exclusion Filter Criteria:
tcpdump -nn -i any -s 0 ! net 172.16.0.0/16 and icmp and ! tcp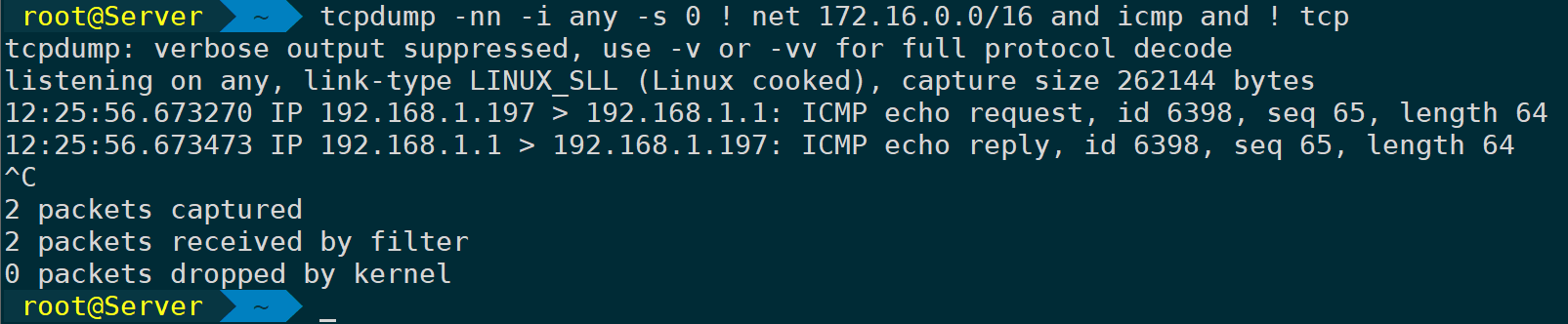
Simply specify the subnet mask for packet capture. Based on the above, you can extrapolate and use them flexibly in combination, as long as the packet capture logic and syntax are correct, even if it’s lengthy and complex:
tcpdump -nn -i any -s 0 dst host 192.168.1.197 and icmp and src net 192.168.1.1/32 or \( host 192.168.1.1 \) and ! tcp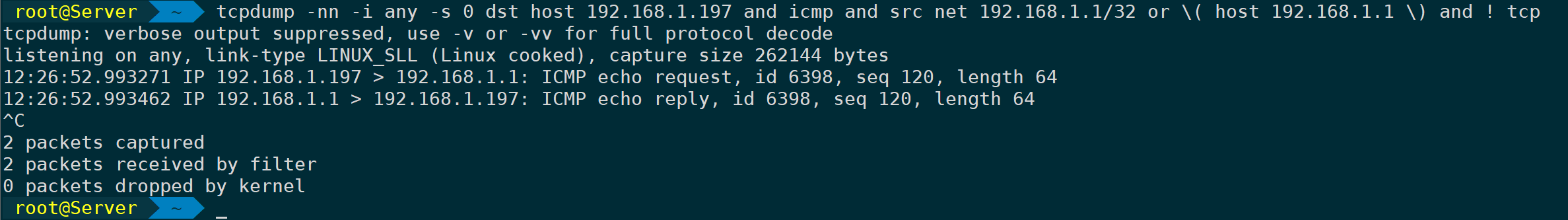
Bash can parse each command up to a maximum of 255 characters. Long and meaningless scripts are not for use in production environments but are excellent for practice and testing compound combinations. Once you achieve mastery, you’ll be able to effortlessly use whatever configurations you need to capture packets or customize setups in a production environment.
7. Specify Packet Size Filtering (greater, less)
`tcpdump` offers a filtering method that specifies the size of each packet, which is especially useful in scenarios requiring the filtering of large packets or packets of a specific size.
Filter packets greater than 1000 bytes:
tcpdump -nn -s 0 -i any host 192.168.1.1 and greater 1000 and icmp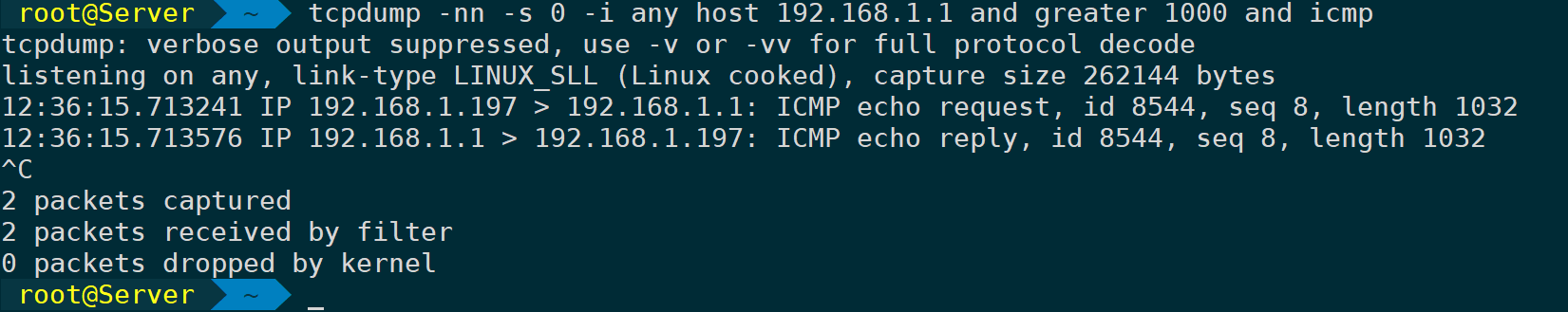
Filter packets smaller than 1000 bytes:
tcpdump -nn -s 0 -i any host 192.168.1.1 and less 1000 and icmp
Combine usage, narrow scope:
tcpdump -nn -s 0 -i any host 192.168.1.1 and less 800 and greater 690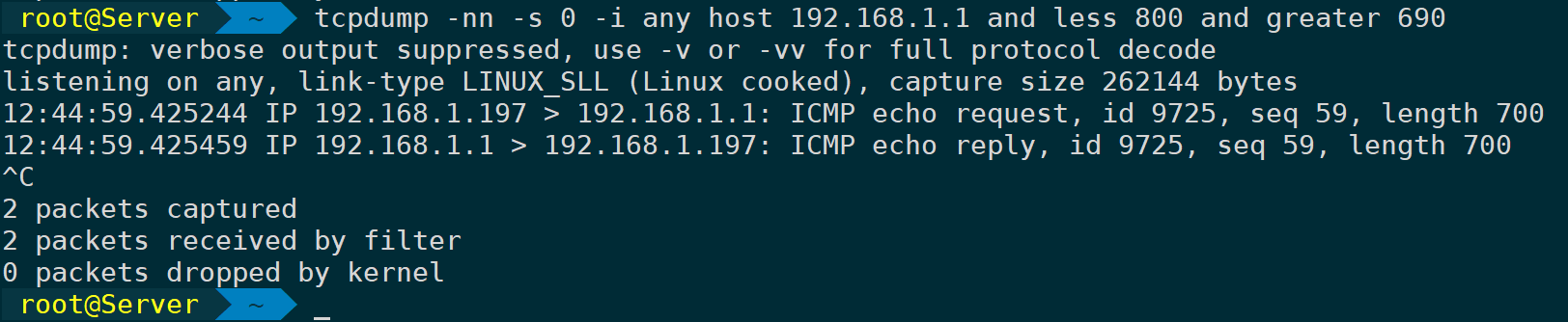
8. Interpreting Flags
The following command captures a complete connection, including the three-way handshake and the four-way termination:
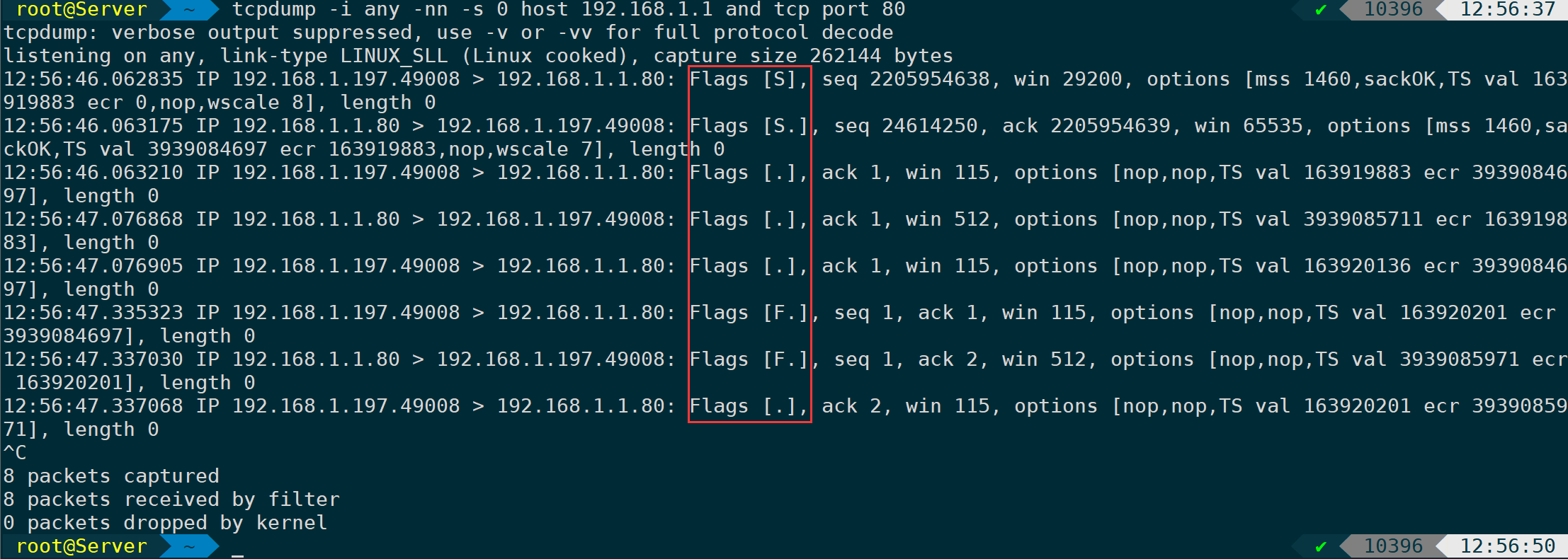
The meaning of each flag is as follows:
|
Flags |
Meaning |
|---|---|
|
|
SYN |
|
|
ACK |
|
|
SYN、ACK |
|
|
PUSH |
|
|
RST |
|
|
FIN |
|
|
Don’t Fragment (DF): When DF=0, fragmentation is permitted. |
|
|
FIN、PUSH、ACK |
As mentioned earlier, if using tcpdump doesn’t allow for intuitive packet analysis, you can-wAnalyze using Wireshark after saving to a file:
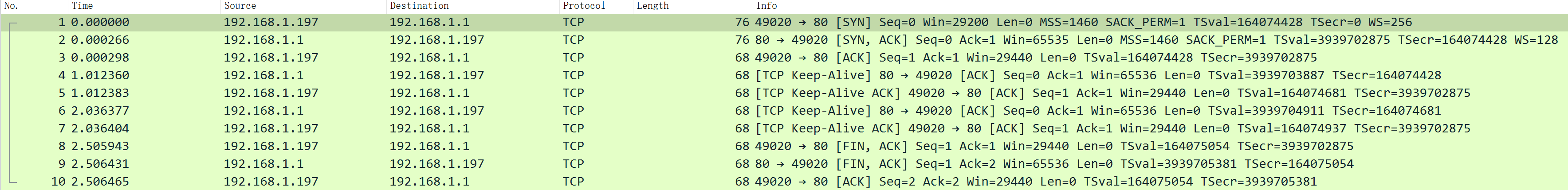
After establishing the three-way handshake,Tcp Keep-AliveKeep the connection open, and afterward, the client actively initiates the disconnection process. The client’s corresponding behavior is as follows:
9. Specify the number of packets to capture, packet size, and polling capture (-c, -W, -C, -G).
In certain scenarios where it’s necessary to split packet capture files and perform rolling captures, these parameters can come in handy:
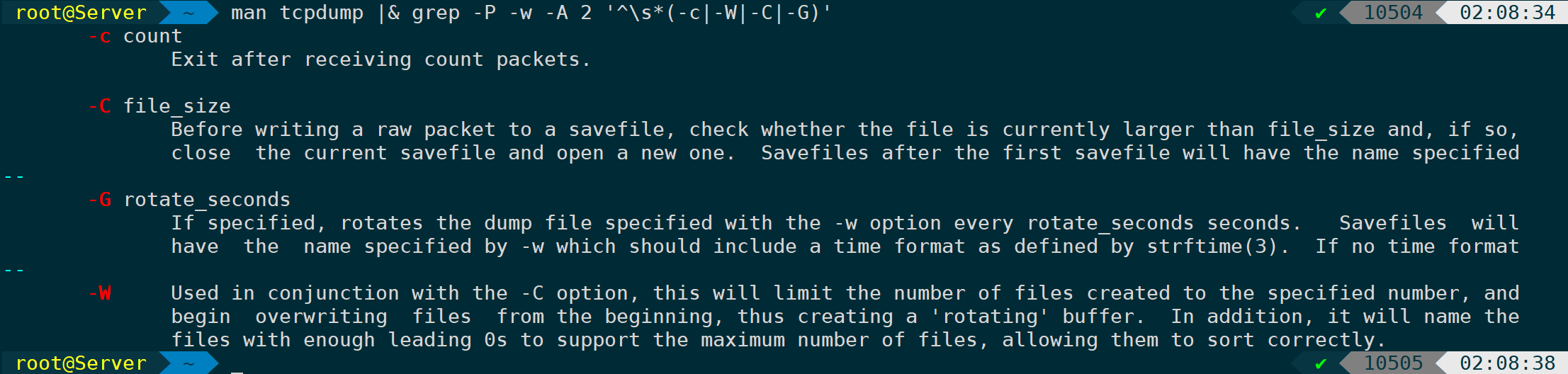
-cSpecify how many packets to capture-WWhat is the maximum size, in MB, for packet capture files?-CMaximum Size Limit for Packet Capture File
-c Specify capture of 2 packets:
tcpdump -i any -s 0 net 192.168.1.1/32 -c 2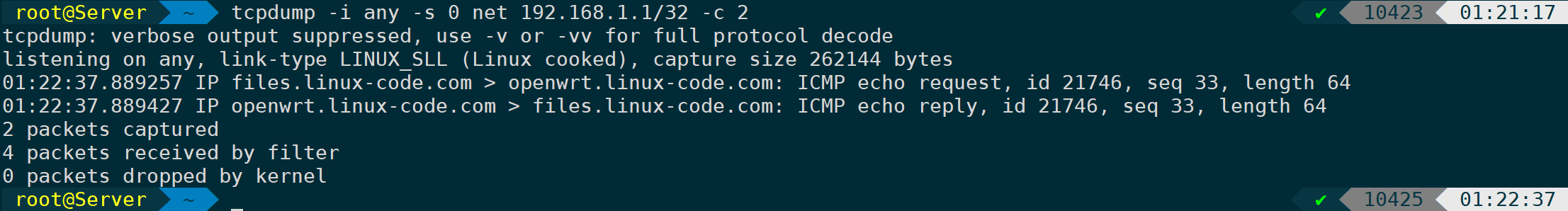
-C Set the maximum file write size to 1MB:
tcpdump -i any -s 0 -C 1 -v -w client.pcap-W Specify capturing into 10 packet files, with each file capturing 1MB, and write in a cyclic manner:
tcpdump -i any -s 0 -C 1M -v -W 10 -w client.pcap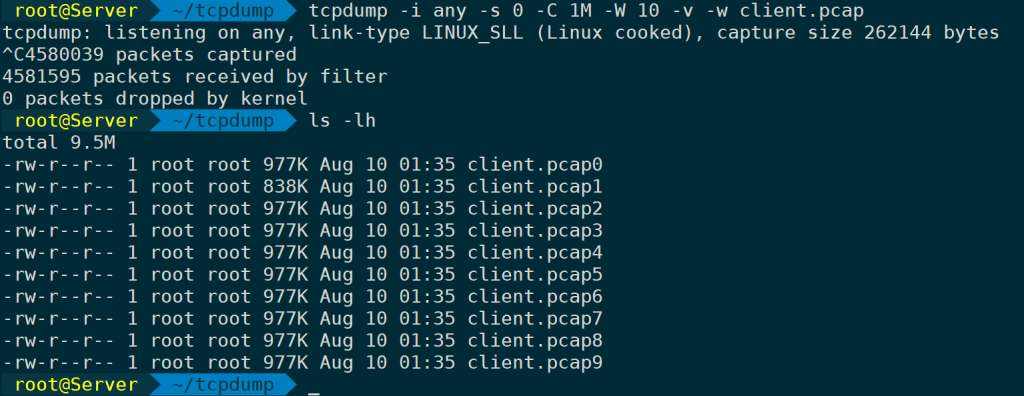
The format will save with a number from 0-N added to the file extension.
-G Specify the interval in seconds for polling to save the file. Typically, this is done using a time format command:
tcpdump -nn -i any -s 0 -G 5 -Z root -v -w %m-%d-%H:%M:%S.pcap # Save a file every five seconds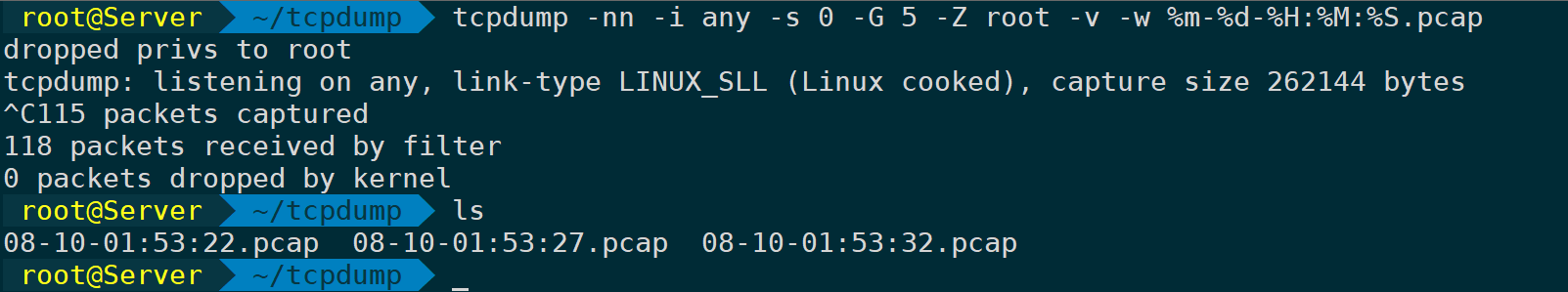
-Z The parameter specifies writing to a new file each time.rootPrivilege escalation,-wThe time format isdateThe format values of the command’s time can be used directly.
-G is usually used with -C to specify a fixed size for each file to be captured each time:
tcpdump -nn -i any -s 0 -C 1 -G 5 -v -w %m-%d-%H:%M:%S.pcapAdditionally, it can be combined.timeoutCommand usage to capture packets for a fixed duration and then stop:
timeout 10 tcpdump -nn -i any -s 0 -G 5 -v -w %m-%d-%H:%M:%S.pcap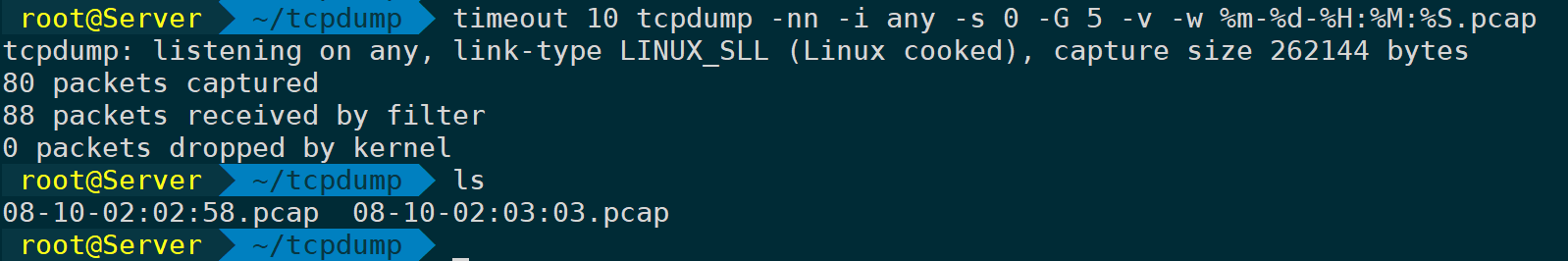
Capture only for 10 seconds, polling to save the file every 5 seconds.
10. Capture packets with specified Flag bits
Capturing specific flag bits is not commonly used, as leveraging Wireshark for analysis and filtering is more typical. However, if you are proficient in using this feature on tcpdump and know exactly what packets you are looking for, tcpdump can effectively filter out the packets that are useful to you, thus reducing unnecessary packet volume.
Capture only SYN flag packets that are not zero, and capture just one packet:
tcpdump -nn -i any -s 0 -c 1 'tcp[tcpflags] & tcp-syn != 0'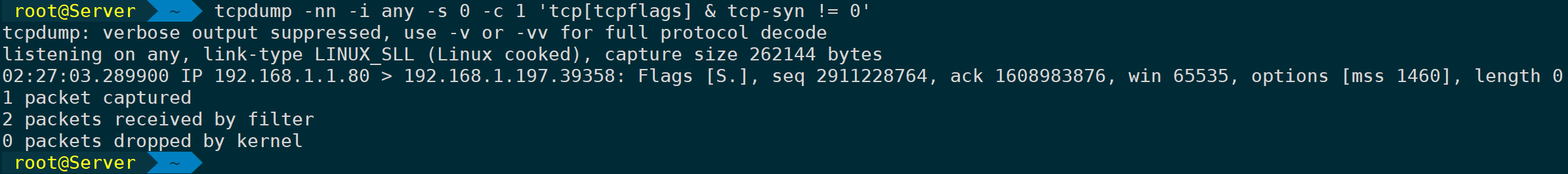
Flags required for a complete handshake capture:
tcpdump -nn -i any -s 0 'tcp[tcpflags] & (tcp-syn|tcp-ack|tcp-fin) != 0' and host 192.168.1.1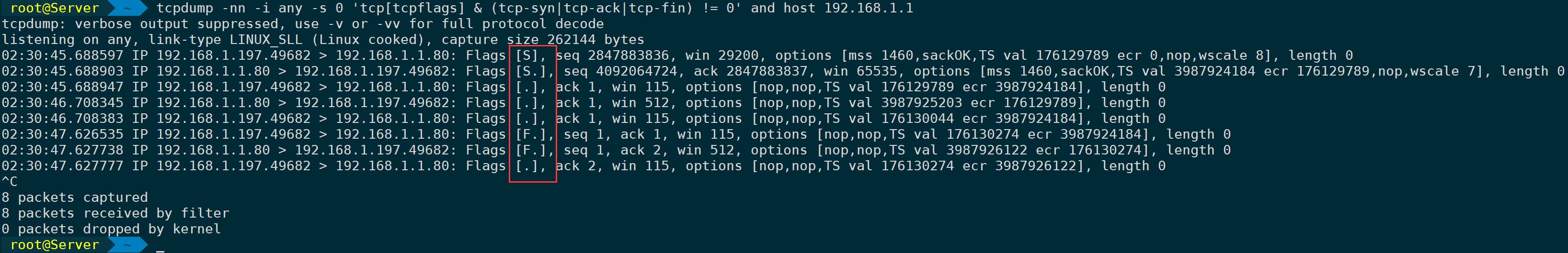
Simultaneously, it can also be represented in binary, although the readability is poorer:
tcpdump -nn -i any -s 0 'tcp[13] & (1|2|18) != 0' and net 192.168.1.1/32 and tcp port 80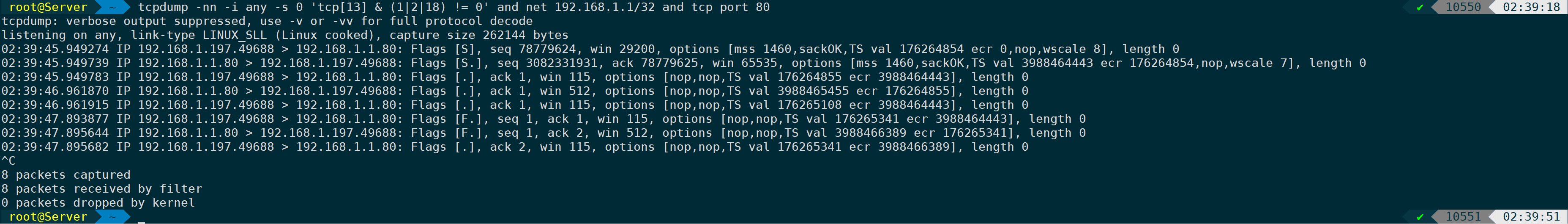
The TCP field is stored in the 14th byte of the TCP header. In programming, counting typically starts from 0, so TCP13 indicates the TCP header field. Here are the meanings of a few commonly used fields for filtering:
|
Expression |
Meaning |
|---|---|
|
tcp13 = 2 |
Capturing a SYN packet, in binary: 00000010 |
|
tcp23 = 18 |
Capture the ACK packet returned to SYN, in binary: 00010010 |
|
tcp13 & 2 = 2 |
Capture SYN and the corresponding SYN-ACK packets |
|
tcp13 = 24 |
Capture PSH-ACK Packet. |
|
tcp13 & 1 = 1 |
Capture FIN-ACK packet |
|
tcp13 & 4 = 4 |
Capturing RST Packets |
Other protocols follow the same logic, such as ICMP:
tcpdump -nn -i any -c 2 -s 0 host 192.168.1.1 and 'icmp[icmptype] = icmp-echo or icmp[icmptype] = icmp-echoreply'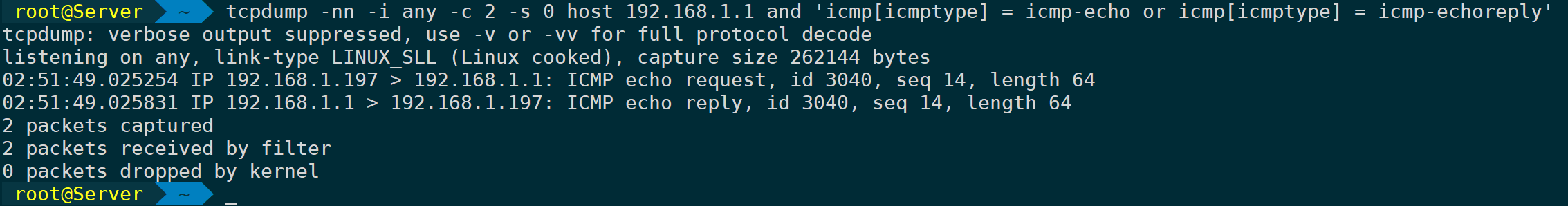
3. Conclusion
Above is a summary of some commonly used methods and techniques in work. In different scenarios, knowing which packets to capture and being clear about which packets you need will make the packet capture more precise. By doing so, identifying the issue won’t be like searching for a needle in a haystack, and the process of analyzing the packets will become more efficient, resulting in a calm and composed approach.



