HOLIDAY
CS Traffic Feature Analysis
Author: wal613@Deep Blue Offensive and Defensive Lab
01
Configuration Information
This section compares the default profile configuration with a modified profile[1]. The modified profile in this article adopts the following configuration.

The main change is that in http-get and http-post, information is hidden within jquery*.js:
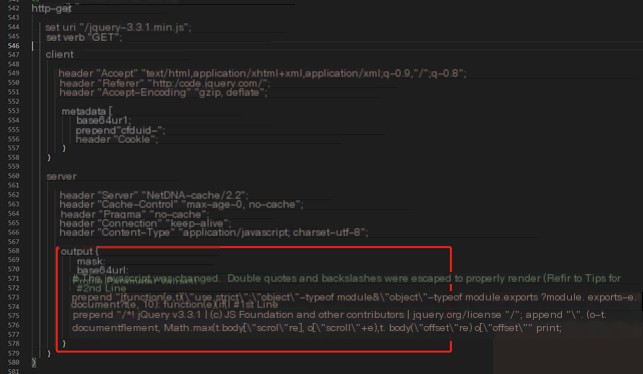
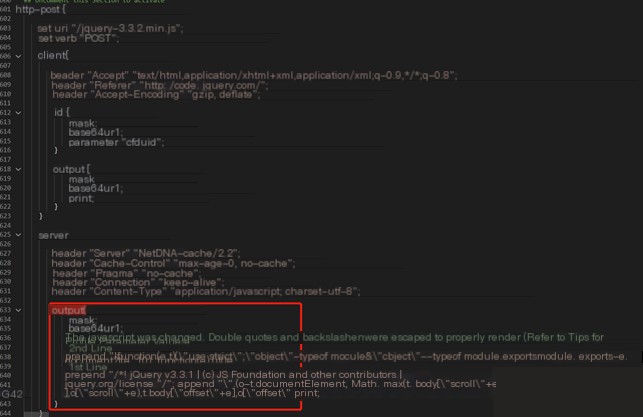
02
HTTP
2.1
Command Feature Analysis
#2.1.1. Heartbeat Packet
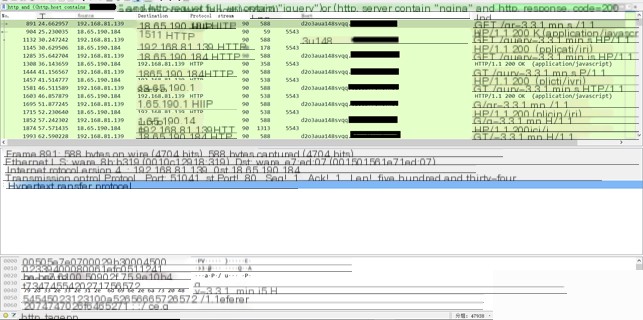
The requested URL is /jquery-3.3.1.min.js, the response packet size is 5543, and the time interval between the response packet and the next request packet is the heartbeat interval.
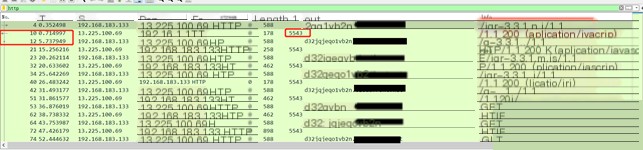
#2.1.2. sleep
The requested URL is /jquery-3.3.1.min.js, the response packet size is 5607, and it contains command data. After execution, the next request packet sends a heartbeat packet according to the new time interval.
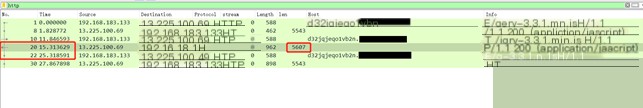
#2.1.3. shell
The shell command here corresponds to “shell whoami”. The requested URL is /jquery-3.3.1.min.js, the response packet size is 5628, and it contains command data. The next packet sends a POST request to /jquery-3.3.2.min.js, with the body containing the command execution result, which is 96 bytes in size. Additionally, the time interval from receiving the command to executing it and returning the result is 0.098093s.
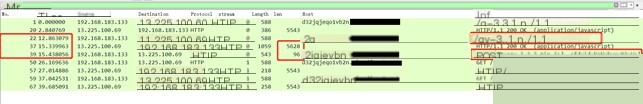
#2.1.4. file
The traffic packet in the example contains two command contents. The first command’s characteristics are: the requested URL is /jquery-3.3.1.min.js, and the response packet size is 5607. Then, after an interval of 0.0071820s, a POST request is sent to /jquery-3.3.2.min.js, with the body containing the command result, which is 395 bytes in size. The second command’s characteristics are: the requested URL is /jquery-3.3.1.min.js, and the response packet size is 5607. Then, after an interval of 0.012044s, a POST request is sent to /jquery-3.3.2.min.js, with the body containing the command result, which is 75 bytes in size.

#2.1.5. hashdump
The requested URL is /jquery-3.3.1.min.js, the response packet size is 115580, and it contains command data as well as the DLL used for hashdump. The next packet sends a POST request to /jquery-3.3.2.min.js, with the body containing the command execution result, which is 288 bytes in size. Additionally, the time interval from receiving the command to executing it and returning the result is 1.140577s.
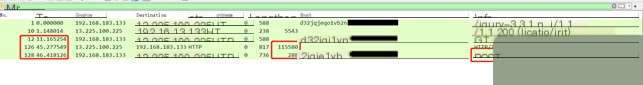
#2.1.6. screenshot
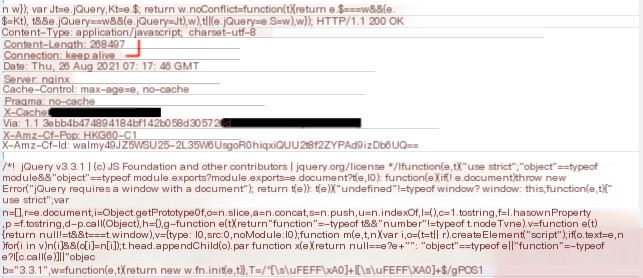
The requested URL is /jquery-3.3.1.min.js, the response packet size is 268497, and it contains command data as well as the DLL used for screenshots. The next packet sends a POST request to /jquery-3.3.2.min.js, with the body containing the command execution result, which is 304566 bytes in size. Additionally, the time interval from receiving the command to executing it and returning the result is 31.417141s.
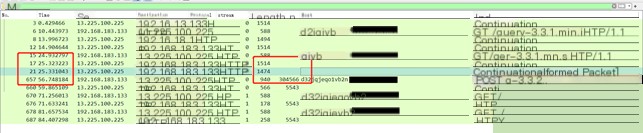
2.2
Traffic Packet Analysis
In the command feature analysis, it is observed that traffic packets can be analyzed based on domain/IP, command length (heartbeat response packet length), command result length (response result packet length), and command execution time (time interval between POST packet and command packet). For a given HTTP traffic packet, data filtering can be performed to identify malicious HTTP traffic.
2.3
Summary
Compared to normal HTTP traffic, CS HTTP communication traffic has the following characteristics:
A. Heartbeat Packet Features
a) Communication occurs at fixed intervals, and the data length of upstream and downstream traffic remains constant at the stream level.
B. Domain/IP Features
a) If not using CDN or domain fronting, the domain name and IP are exposed.
b) If using CDN or domain fronting, the real IP is hidden.
C. Command Features
a) Commands are received via heartbeat packets, and the server-side response packet is longer, sometimes containing DLL module data.
b) After executing a command, the client sends the execution result via a POST request, with the body encrypted and base64-encoded.
c) Different commands have different execution time intervals, which can be determined by analyzing the interval between POST and GET requests.
D. Data Features
a) Communication data is hidden within jquery*.js in the response packets.
03
DNS
3.1
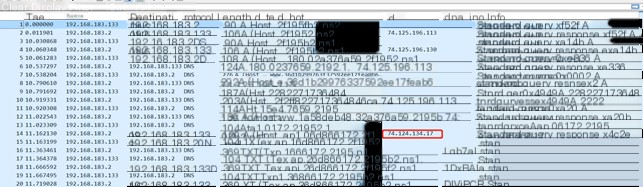
Command Feature Analysis
—
This translation maintains the original HTML structure while ensuring accurate and specialized terminology in American English. Let me know if you need any modifications!Here is the translated content while preserving the original formatting, HTML tags, and styles:
—
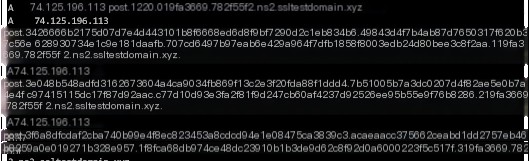
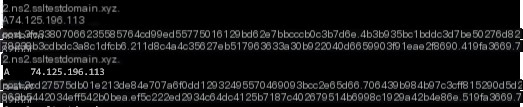
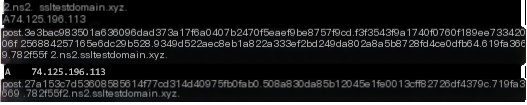
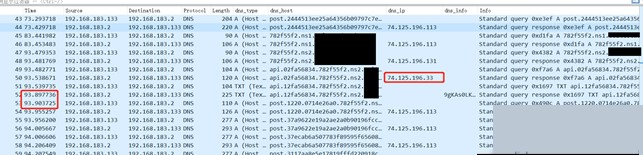
#3.1.5.file
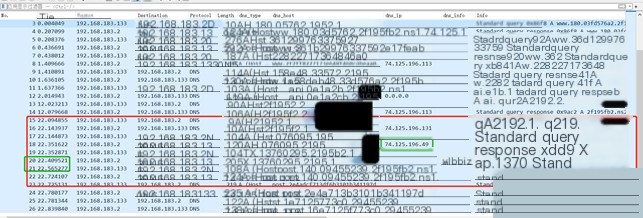
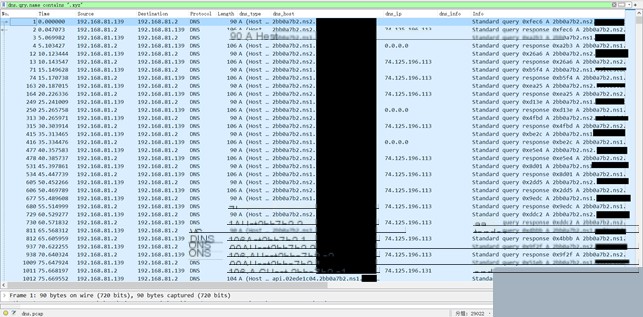
The “file” command here includes three instances. The received command lengths are 74.125.196.49, 74.125.196.33, and 74.125.196.49, respectively. After execution, the returned data lengths are 0x150, 0x220, and 0x240, with execution times of 0.008949s, 0.005989s, and 0.008816s.

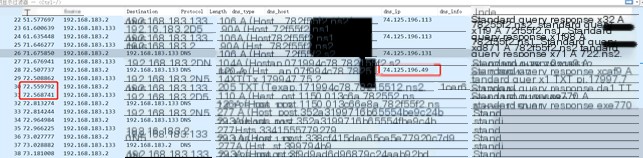
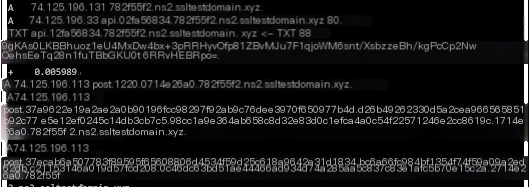
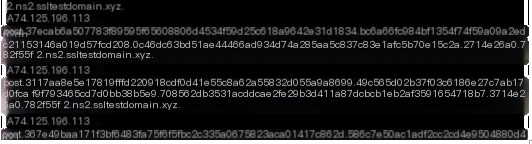
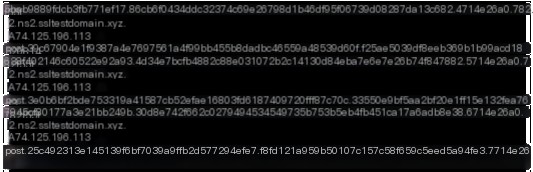
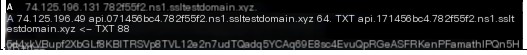
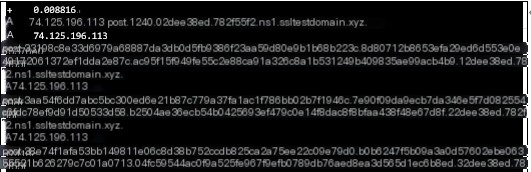
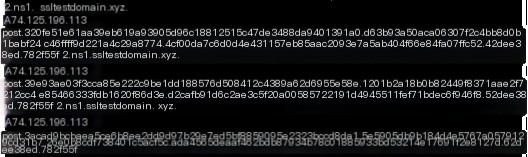
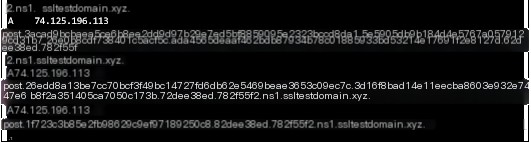

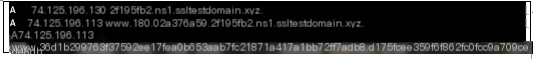
#3.1.6.hashdump
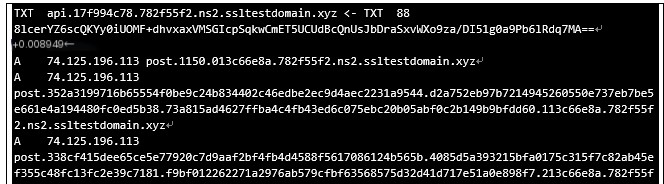
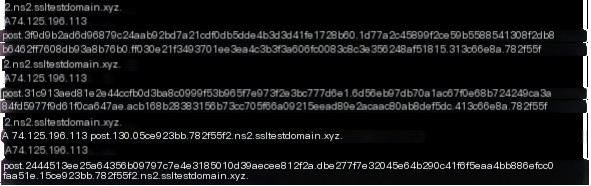
The “hashdump” command sends an API A record query, retrieving data with a length of 74.124.134.17. This is followed by an API TXT record query to obtain the corresponding hashdump DLL. Then, a POST A record is sent to return the results. The returned data length is 0xd0, and the command execution time is 1.148639s.
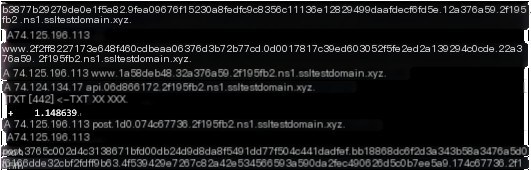
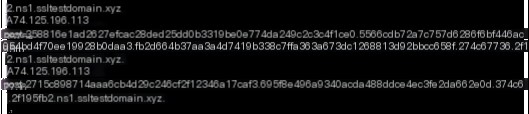
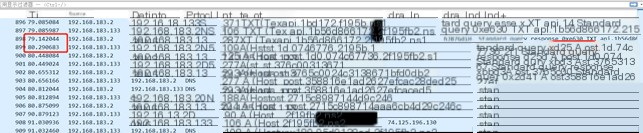
#3.1.7.screenshot
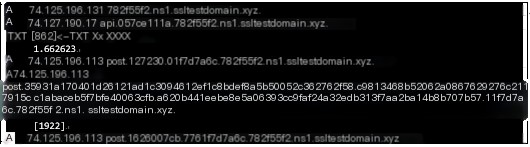
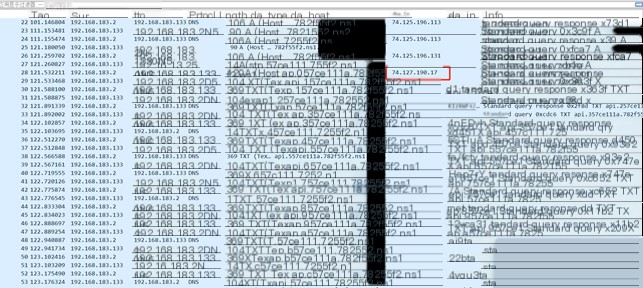
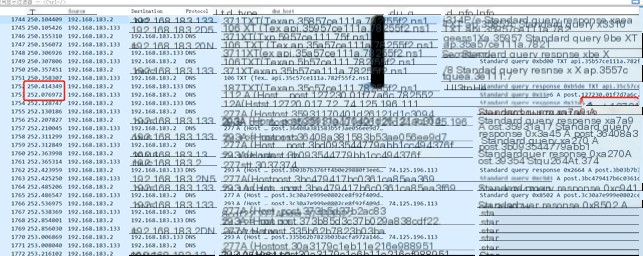
The “screenshot” command initiates an API A record query, returning an execution command data length of 74.127.190.17. It then uses an API TXT record to receive the screenshot DLL and command data. After executing the screenshot command, the results are returned via a POST A record. The returned data length is 0x27230, and the execution time is 1.662623s.
3.2
Traffic Packet Analysis
From the above analysis, we can see that command length (API A record and API TXT record), command result length (POST A record), and command execution time (time interval between POST A record and command packet) can be used as reference indicators. For a given DNS traffic packet, filtering can be applied to identify malicious DNS traffic.
3.3
Summary
Compared to normal DNS traffic, CS’s DNS communication traffic has the following characteristics:
A. Heartbeat Packet Characteristics
a) Communication occurs at regular intervals using A record queries.
b) Heartbeat packets 1 and 2 are determined by the return address of the initial A record.
B. Domain Name
a) Clear domain name resolution characteristics.
C. Command Characteristics
a) Commands are received via heartbeat packets, switching to TXT record queries, sometimes including DLL module data.
b) After execution, the client sends a POST A record query to return the result.
c) Different commands have different execution time intervals, which can be analyzed based on the interval between TXT record queries and A record queries.
04
HTTPS
4.1
Command Characteristic Analysis
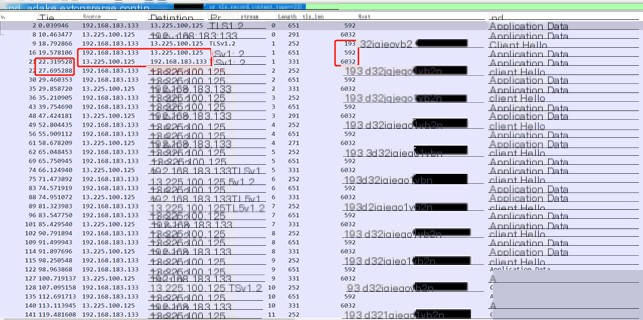
#4.1.1.Heartbeat Packet
The heartbeat packet has distinct characteristics: the controlled endpoint sends data with a length of 592, the CS server returns data with a length of 6032, and the interval is 5 seconds.
(Translation continues similarly for the remaining sections.)Here is the translated content while preserving the original formatting, HTML tags, and styles:
—
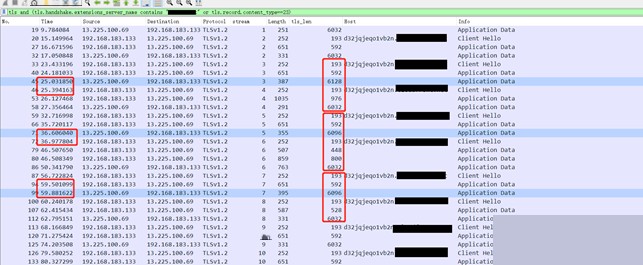
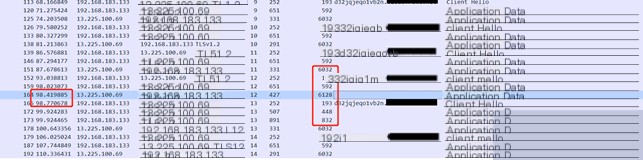
#4.1.5.hashdump
The `hashdump` command receives a relatively large amount of data on the controlled endpoint, including the hashdump tool and command. The execution time is 1.509852 seconds, and the returned data packet size is 736.
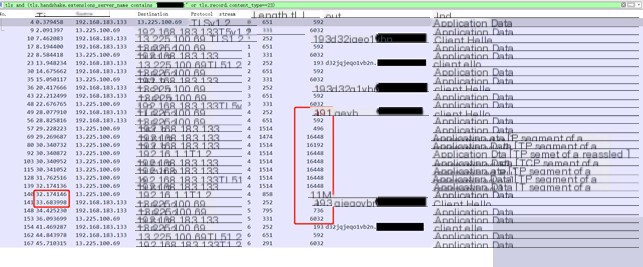
#4.1.6.screenshot
The `screenshot` command receives even more data than `hashdump`, including the screenshot tool and execution command. The execution time is 2.060741 seconds, and the data returned to the CS server is also the largest in size.
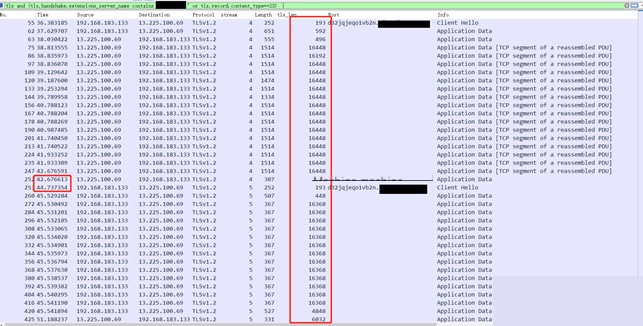
4.2
Traffic Packet Analysis
From the above analysis, we can see that the command length (data length received by the controlled endpoint’s heartbeat packet), command result length (data length sent by the controlled endpoint to the CS server after executing the command), and command execution time can be used as reference indicators. For a given HTTPS traffic packet, filtering can be performed to identify malicious HTTPS traffic.
4.3
JA3/JA3S
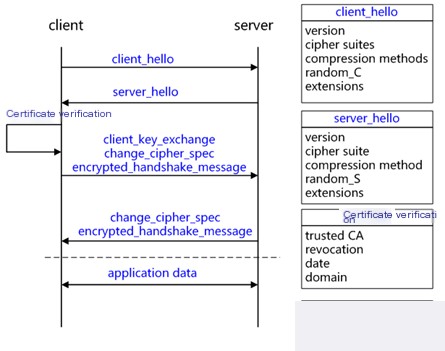
#4.3.1.TLS/SSL Handshake Process
Based on the RSA key exchange process.
#4.3.2.JA3
The JA3 algorithm [6] is used to collect information from the “Client Hello” message in SSL, including SSLVersion, Cipher, SSLExtension, EllipticCurve, and EllipticCurvePointFormat. These details are concatenated into a string, hashed, and then used to detect whether the SSL/TLS traffic is malicious.
Below is the JA3 fingerprint of HTTPS traffic under the default configuration of CS 4.4:
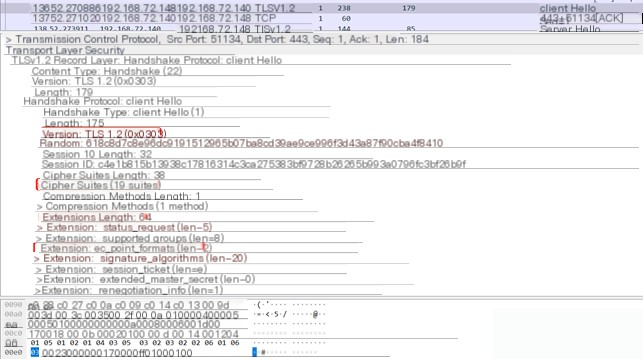
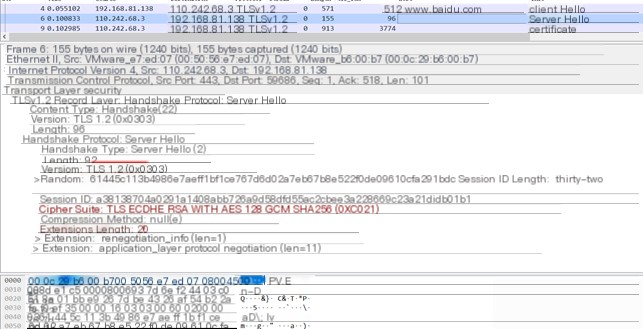
The JA3 fingerprint of a normal browser accessing https://www.baidu.com:
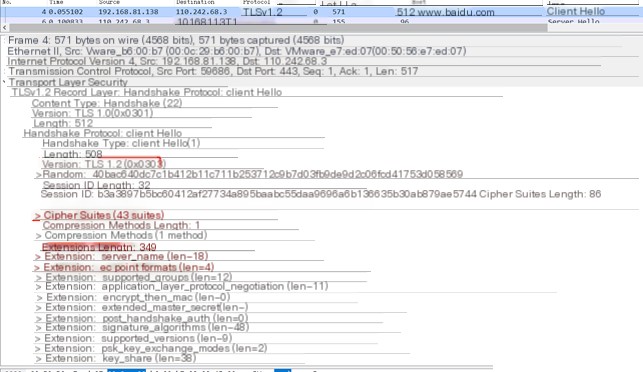
The `ja3` [5] tool allows direct input of a pcap file to compute the SSL/TLS JA3 information, as shown below.

You can use [2] to query JA3 fingerprint information.
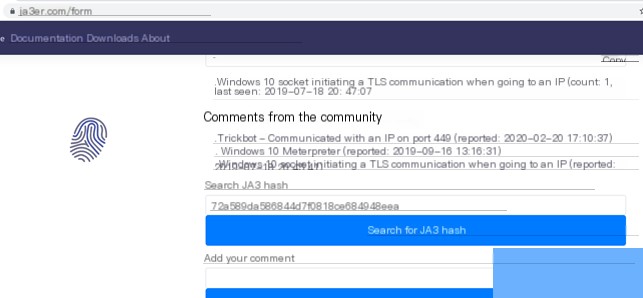
#4.3.3.JA3S
The JA3S algorithm [4] collects information from the “Server Hello” message in SSL/TLS communication, including SSLVersion, Cipher, and SSLExtension fields. These details are concatenated into a string, hashed, and then used to detect whether the SSL/TLS traffic is malicious.
Below is the JA3S fingerprint of HTTPS traffic under the default configuration of CS 4.4:
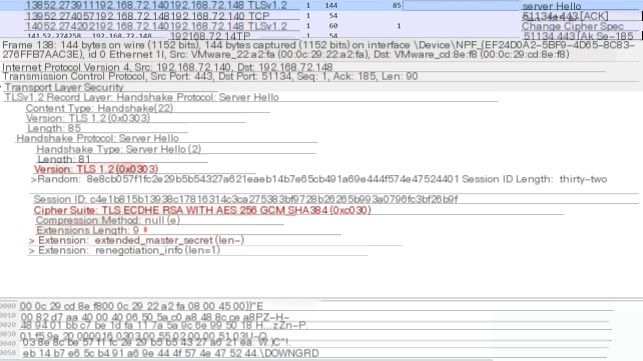
The JA3S fingerprint of a normal browser accessing https://www.baidu.com:
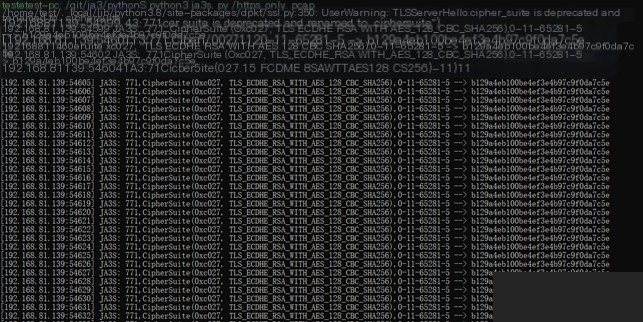
The `ja3` [5] tool allows direct input of a pcap file to compute the SSL/TLS JA3S information, as shown below.
#4.3.4.Go Implementation of Features
[TODO] Refer to [9].
4.4
Machine Learning Applications
#4.4.1.DataCon2020
DataCon2020 included challenges related to traffic analysis, focusing on detecting encrypted malicious traffic. The HawKEye team from Tsinghua University [7] achieved excellent results.
The challenge scenario involved detecting infected IPs in a residential network where malware was using TLS/SSL encrypted communication. The task was to analyze encrypted traffic on port 443 at the network gateway.
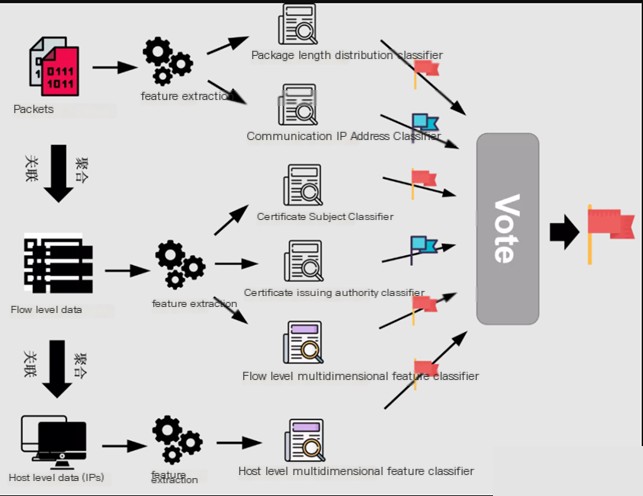
HawKEye extracted features from three dimensions: packets, flows, and hosts:
A. Packets: Analyzing packet length and communication IP addresses.
B. Flow-level data: Extracting features from certificate subjects, certificate issuers, and multi-dimensional flow characteristics.
C. Host-level data: Extracting multi-dimensional features at the host level.
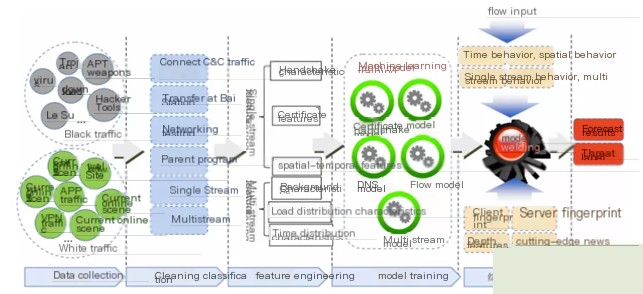
#4.4.2. Domestic Detection Techniques
A Chinese company proposed a machine learning-based SSL encrypted threat detection method [8].
4.5
Summary
Compared to normal HTTPS traffic, CS HTTPS communication has the following characteristics:
A. Heartbeat packet characteristics:
a) Regular communication intervals with fixed upstream/downstream data lengths.
B. Domain/IP:
a) Blacklist/whitelist checks.
C. Certificate characteristics:
a) Self-signed, validity period, server name, JA3 fingerprint, encryption suite, and extension list.
D. Command characteristics:
a) Commands are received via heartbeat packets, with longer server response packets that may include DLL module data.
b) After execution, client upstream data increases significantly, while downstream data remains stable.
c) Different commands have varying execution time intervals.


