August 25 News – Attackers are gradually moving away from using the Cobalt Strike penetration testing suite in favor of lesser-known alternatives. The open-source, cross-platform tool Sliver is now replacing Brute Ratel as a preferred weapon among attackers.

Over the past few years, Cobalt Strike has been widely abused by various attackers, including ransomware operators, who use it to deploy “beacons” within compromised networks and move laterally to high-value systems.
However, defenders have developed effective methods to detect and block Cobalt Strike attacks, prompting attackers to explore other tools that can evade Endpoint Detection and Response (EDR) and antivirus solutions.
A Microsoft report highlights that attackers, ranging from state-sponsored groups to cybercriminal gangs, are increasingly using Sliver, a Go-based security testing tool developed by researchers at the cybersecurity firm BishopFox.
Microsoft has tracked a group using Sliver, identified as DEV-0237. This group, also known as FIN12, has ties to various ransomware operators.
The group has previously distributed ransomware payloads for multiple ransomware operators (Ryuk, Conti, Hive, Conti, and BlackCat) using various malware loaders such as BazarLoader and TrickBot.
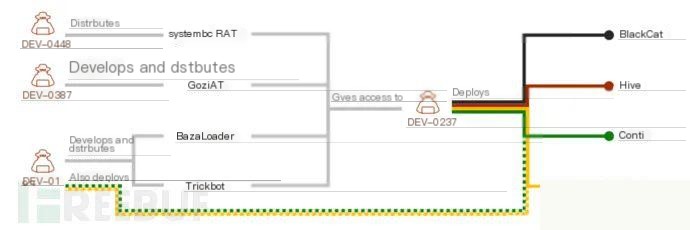
【Various ransomware payloads distributed by the FIN12 group】
According to a report from the UK Government Communications Headquarters (GCHQ), APT29 (also known as Cozy Bear, The Dukes, Grizzly Steppe) has also used Sliver in its attacks.
Microsoft noted that the Conti ransomware gang recently deployed Sliver in its attacks, using the Bumblebee (Coldtrain) malware loader instead of BazarLoader.
However, malicious activities involving Sliver can be detected through analysis of its toolkit, operational mechanisms, and components, leading to effective threat-hunting queries.
Microsoft has provided a set of Tactics, Techniques, and Procedures (TTPs) that defenders can use to identify Sliver and other emerging Command and Control (C2) frameworks.
Since the Sliver C2 network supports multiple protocols (DNS, HTTP/TLS, MTLS, TCP), accepts implant/operation connections, and can host files to mimic legitimate web servers, threat hunters can set up listeners to detect anomalies in network traffic associated with Sliver infrastructure.
“Some common artifacts include unique HTTP header combinations and JARM hashes, the latter being an active fingerprinting technique for TLS servers,” Microsoft noted.
Microsoft also shared insights on detecting Sliver payloads (shellcode, executables, shared libraries/DLLs, and services) generated using the official, non-customized C2 framework codebase.
Detection engineers can create loader-specific detections (e.g., Bumblebee) or, if the shellcode is not obfuscated, establish rules for identifying shellcode payloads embedded within loaders.
For Sliver malware payloads with limited context, Microsoft recommends extracting configurations when they are loaded into memory, as the framework must deobfuscate and decrypt them for execution.
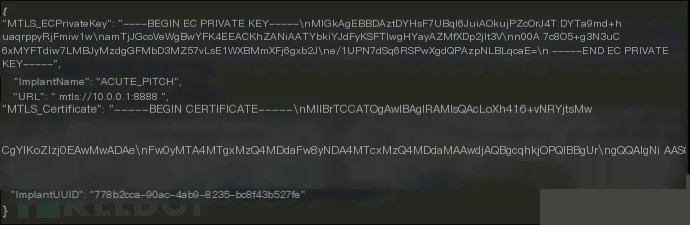
【Extracting configurations when Sliver loads into memory】
Scanning memory can help researchers extract details such as configuration data.
Threat hunters can also look for process injection commands commonly found in the default Sliver code, including:
Migrate (command) – Migrate to a remote process
Spawndll (command) – Load and execute a reflective DLL in a remote process
Sideload (command) – Load and execute a shared object (shared library/DLL) in a remote process
msf-inject (command) – Inject a Metasploit Framework payload into a process
execute-assembly (command) – Load and execute a .NET assembly in a subprocess
Getsystem (command) – Spawn a new Sliver session as the NT AUTHORITY/SYSTEM user
Microsoft noted that the toolkit also relies on extensions and aliases (Beacon Object Files (BFOs), .NET applications, and other third-party tools) for command injection.
The framework also utilizes PsExec to execute commands that enable lateral movement.
To help enterprises identify Sliver activity within their environments, Microsoft has created a set of hunting queries that can be executed in the Microsoft 365 Defender portal.
Microsoft emphasized that the provided detection rule sets and hunting guidance are based on the currently public Sliver codebase, and Sliver variants developed from modified versions may impact query results.
Reference Link:
Recommended Articles