What is SSH Brute Force Attack?
Here’s the situation of an SSH brute force attack: I have an old second-hand server at home, mainly for personal amusement. One day, while browsing Zhihu, I suddenly came across a blogger sharing their experience of frequent attacks on their Raspberry Pi. Intrigued, I logged into my own server and discovered a large number of attack logs.
SSH attacks have become quite common on the internet. Perhaps someone is conducting 24/7 brute force attacks on all accessible IP addresses online. According to statistics from Tencent Cloud’s CloudShield Lab, SSH brute-force attacks have spread to over 160 countries worldwide. These attacks primarily target users who use default usernames and passwords. Attackers typically test with commonly used weak passwords. If you happen to use a weak password, the risk of being successfully compromised is very high.
How to Tell is Under SSH Brute Force Attack
Given the high risk of SSH attacks on servers, how can you tell if your server is being targeted? It’s possible that attacks are ongoing without your server speaking up and informing you.
Method 1: Check the auth.log
In my case, using Ubuntu, the auth log is located by default at /var/log/auth.log. Upon inspection of the file size, I was shocked. The auth.log file is 68MB in size, comprising 530,000 lines, with 20,000 lines related to SSH password errors…
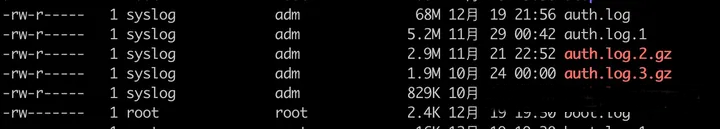
# Check file size
sudo ls -alh /var/log/auth.log
# Count number of lines in the file
sudo wc -l /var/log/auth.log
# Count number of lines with SSH password errors
sudo grep "Failed password" /var/log/auth.log | wc -l
# Count the number of attack instances
sudo grep "Failed password for" /var/log/auth.log | awk '{print $11}' | sort | uniq -c | sort -nr | moreMethod 2: lastb command
The Linux lastb command is used to list information about users who have unsuccessfully attempted to log into the system. When executed alone, the lastb command reads the file named btmp located in the /var/log directory. It displays a list of usernames that have been recorded in this file due to failed login attempts.
From the execution results of this command, it is evident that there are numerous attacks occurring simultaneously at certain times. These attacks are specifically targeting the root user account for testing purposes.
➜ ~ sudo lastb
root ssh:notty 159.223.128.108 Sun Dec 19 20:59 - 20:59 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:59 - 20:59 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:59 - 20:59 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:59 - 20:59 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:58 - 20:58 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:57 - 20:57 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:57 - 20:57 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:57 - 20:57 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:57 - 20:57 (00:00)
root ssh:notty 159.223.128.108 Sun Dec 19 20:57 - 20:57 (00:00 How to Detect SSH Brute Force Attack – Sax2 IDS
Detecting SSH bruteforce attack requires professional intrusion detection tools, such as: Sax2 IDS, Snort, etc., let’s use Sax2 IDS to detect SSH bruteforce attack, Sax2 IDS intrusion detection engine has a variety of built-in brute force attack modules, it is very simple to use, you only need to start the application, click the “Start” button to detect network attacks, switch to the event window page, if you find an attack, you can see the corresponding event, please see the following figure:
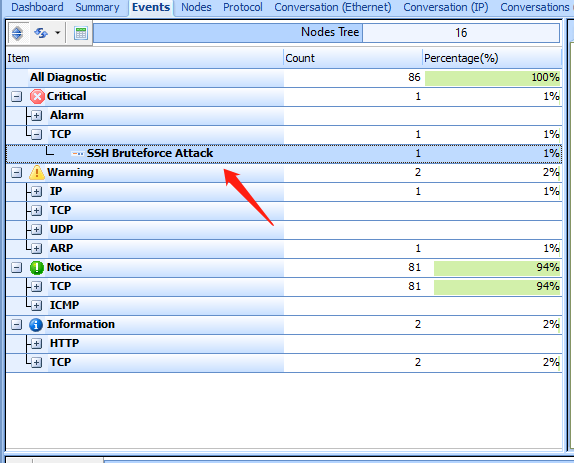
How to Prevent SSH Brute Force Attacks
There are various methods to prevent SSH brute-force attacks, with the most basic being to close the port. If external access isn’t necessary, SSH should not be exposed on a public network address, as it will inevitably face SSH brute-force attacks. However, when external access is necessary, the following simple methods can be considered:
Method 1: Disable External Password Authentication
The principle of this method is to prohibit password-based logins from external networks, rendering SSH brute-force attacks ineffective.
Step 1: Copy your SSH key to the server
ssh-copy-id username@your_server_host
Step 2: Adjust the sshd_config configuration file
vim /etc/ssh/sshd_config
# PasswordAuthentication yes (enable password login)
PasswordAuthentication no # disable password login
# Add internal network address matching logic at the end of the file
Match Address 10.0.0.0/8,172.16.0.0/12,192.168.0.0/16
PasswordAuthentication yes
Step 3: Restart the SSHD service
service sshd restart
Method 2: Ban Access After Multiple Failures
This method involves blocking access from IPs that repeatedly fail login attempts, preventing further damage. A common Linux tool for this purpose is fail2ban. Fail2ban scans error logs to block requests from specific IPs by modifying firewall rules. For proper usage of Fail2ban, it’s recommended to search for detailed instructions.
Conclusion
Many network attacks, like SSH brute-force attacks, don’t require highly advanced techniques. With access to common password databases, attackers can exploit weak passwords such as ‘123456’ or default passwords. Using complex passwords generally prevents successful intrusion attempts. Nonetheless, seeing numerous error logs can be unsettling, prompting additional protective measures for peace of mind.


