1. Introduction
Earlier, two packet capture tools were introduced, which should be sufficient to handle issues encountered in daily work. However, some people left comments asking Brother Hong to explain Wireshark, a packet capture tool. To be honest, Brother Hong hadn’t used this tool before either, so he’s sharing as he learns. In other words, it’s learning and sharing at the same time. I hope you don’t mind, and Brother Hong’s sharing here is just for your reference. Any errors are welcome to be pointed out. You can also delve deeper into it yourself.
2. Software Introduction
Wireshark (formerly known as Ethereal) is a free, open-source network sniffing packet capture tool and the world’s most popular network protocol analyzer! Network packet analysis software captures network packets and displays as much detailed information about them as possible. Wireshark uses WinPCAP as an interface to directly exchange data packets with network cards, enabling real-time detection of network communication data. It examines network communication snapshot files and can view detailed content in each layer of network packets through its graphical interface. Its powerful features include a strong display filter language and the ability to view reconstructed TCP session streams, supporting hundreds of protocols and media types.
The function of network packet analysis software can be imagined as an “electrician using a multimeter to measure current, voltage, resistance” – except this is migrated to the network, replacing wires with network cables. In the past, network packet analysis software was very expensive or specialized for proprietary use. The appearance of Ethereal changed all that. Under the protection of the GNU GPL General License, users can obtain software and its source code for free and have the right to modify and customize its source code. Ethereal is currently one of the most widely used network packet analysis software worldwide.
Wireshark is frequently used in network troubleshooting, displaying layers 2 through 5 of the network model (link layer, network layer, transport layer, application layer). Network engineers, network security engineers, hackers, and software development engineers will often use Wireshark.
3. A Brief History of WireShark
In 1997, Gerald Combs needed a tool to track network problems and wanted to learn about networks. So he began developing Ethereal (the previous name of the Wireshark project) to meet his own needs.
In 1998, Ethereal version 0.2.0 was born. Not long after, more and more people discovered its potential and contributed to its underlying analysis.
Wireshark is a free and open-source packet sniffer/analyzer used to capture packets on the network. The initial version of Wireshark was called Ethereal, released by Gerald Combs in 1998. His name is prominently visible on both the software and the official website:
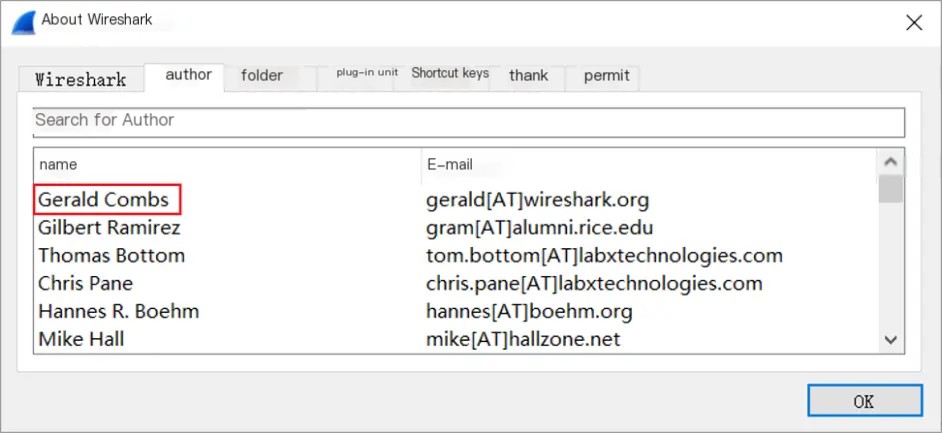 />
/>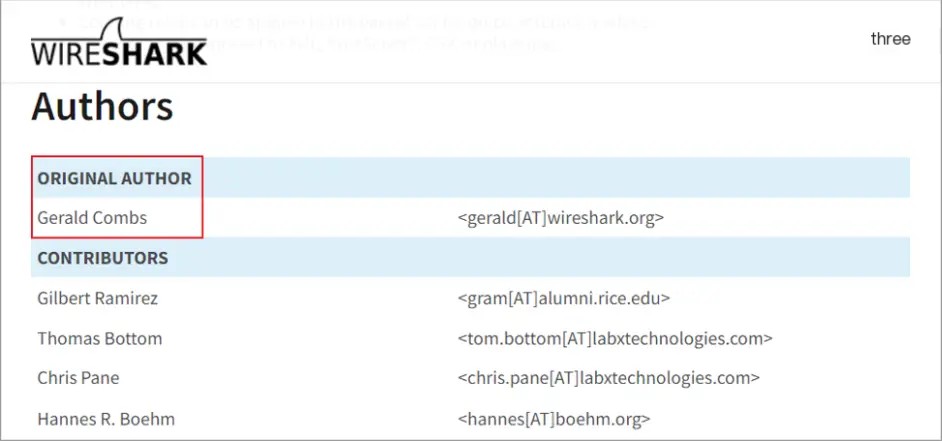 />
/>
In May 2006, Gerald Combs went to work at CACE Technologies but was unable to secure the trademark rights for Ethereal. To ensure the project continued running successfully, Combs and his development team renamed the project Wireshark around the middle of 2006.
As Combs and other contributors maintained the Wireshark code and released new versions over the next decade, Wireshark has become one of the world’s most popular packet analysis/sniffing software.
The above history of Wireshark is easy to find online, but these materials do not mention why Combs named the software Wireshark (if readers can find it, please point it out in the comments section).
However, the official website has a question to consider:
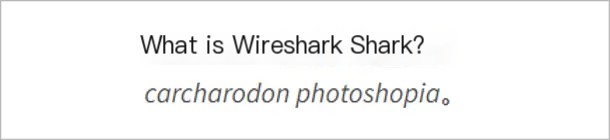
The answer here with “carcharodon” undoubtedly reminds one of the most famous shark—the Great White Shark (Carcharodon carcharias). Sharks are known for their extremely sensitive sense of smell, able to detect wounded prey from kilometers away, making the name shark quite fitting for a packet sniffer.
Even the Wireshark logo is shaped like a shark fin, as shown in the image below:

In 2008, after ten years of development, Wireshark released version 1.0.
4. What Can WireShark Do?
In short, the main function of WireShark is to capture packets from various ports, including wired network ports, wireless network ports, USB ports, LoopBack ports, etc., making it very convenient for protocol learning, network analysis, system troubleshooting, and other follow-up tasks.
Supports real-time data capture and saving as pcap files
Supports reading data from already captured packets;
Supports parsing more than 1000 types of standard/proprietary protocols
Supports creating plugins to parse private protocols;
Supports capturing and displaying filters to refine data;
Supports TLS protocol decryption (set up is relatively complex, it is easier to use charles/burp/fiddler)
The above points are mainly summarized as three purposes:
① Analyzing network layer protocols,
② Solving network fault problems,
③ Identifying network security issues.
5. What Wireshark Cannot Do
For security reasons, Wireshark can only view packets but cannot modify packet contents or send packets.
Does not support editing or modifying packets (use WireEdit for packet editing)
Does not support intrusion/detecting abnormal traffic
6. Wireshark VS Fiddler
Fiddler is a program that runs on Windows, specifically for capturing HTTP, HTTPS.
Wireshark can capture HTTP and HTTPS, but cannot decrypt HTTPS, so Wireshark cannot understand the content within HTTPS.
7. Other Similar Tools
1. Microsoft’s Network Monitor
2. Sniffer
3. Omnipeek
4. Fiddler
5. Httpwatch
6. Kole Network Analysis System
8. Who Would Use Wireshark
1. Network administrators use Wireshark to check network problems
2. Software test engineers use Wireshark to capture packets to analyze the software they are testing
3. Engineers engaged in socket programming use Wireshark for debugging
4. IT operation and maintenance engineers
5. Network engineers
6. Security engineers
7. It is heard that most engineers at Huawei and ZTE use Wireshark.
In short, anything related to the network might use Wireshark.
9. Platform Support
Wireshark can run on the following platforms:
① Windows
② MacOS
③ Linux/Unix
10. Relevant URLs
1. Official Website: https://www.wireshark.org/
2. Books: http://www.wiresharkbook.com/
3. Wiki Documentation: https://wiki.wireshark.org/
11.Wireshark Packet Capture Principle
Wireshark uses WinPCAP as an interface to directly exchange data packets with network cards. Wireshark’s environment is generally divided into two types: a standalone environment where the computer is directly connected to the network and a network environment, which is commonly used and involves connecting switches.
In a “standalone situation”, Wireshark directly captures the network traffic of the local network card;
In a “switch situation”, Wireshark obtains the network traffic in the local area network through port mirroring, ARP spoofing, etc.
Port Mirroring: Use the switch’s interface to forward the network traffic of the local area network to the network card of the specified computer.
ARP Spoofing: The switch forwards data based on MAC addresses and can disguise another terminal’s MAC address to obtain network traffic from the local area network.
The packet capture principle is divided into network principles and underlying principles: 1. Network Principles: 1) Local Environment – Directly capture the flow in and out of the local network card: Directly installing Wireshark on the terminal allows capturing the network card’s traffic communication with the Internet. 2) Hub Environment (Old Network) – Hub: Flood to all other ports, capturing the packets inside the whole local area network.
11.1 Network Packet Capture Principle
In the network, no matter what is transmitted, it is ultimately sent as binary bits through a physical medium, resembling a Bit stream like 0101. Pure text (string) often uses UTF-8 encoding in Chinese and ASCII encoding in English; non-pure text such as audio, video, images, compressed files, etc., is encapsulated with different encodings, converted into binary for transmission. In IP networks, the raw data captured by Wireshark is all binary.
In which network circumstances can packets be captured? Let’s combine the network principles to explain. There are three main situations for network packet capture: local environment, hub environment, and switch environment.
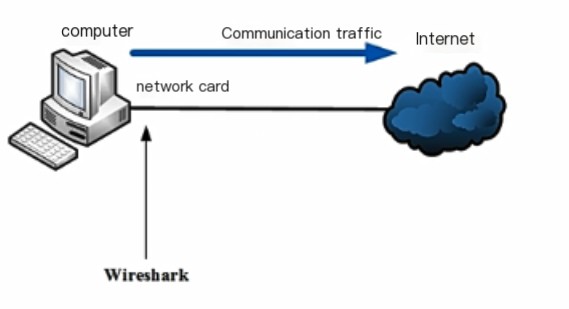
11.1.1 Local Environment
In the local environment, the flow in and out of the local network card is directly captured. Wireshark binds with our network card and can capture our network communication traffic without the need for third-party devices (switches, routers). This is the most basic way to capture packets, directly capturing the traffic packets that go in and out of the local network card. In this case, Wireshark will bind to a network card of the local machine.
11.1.2 Hub Environment
In the hub environment, traffic flooding can be done within the same collision domain. The English word for hub is “Hub,” which means “center,” and the main function of a hub is to regenerate, shape, and amplify received signals to extend the network’s transmission distance while centralizing all nodes at its core. It operates at the physical layer of the OSI reference model.
Suppose three computers communicate, and Wireshark is installed on PC1. When PC2 and PC3 send data packets into the hub’s network (collision domain or broadcast domain), since a hub is a physical layer product and cannot recognize MAC addresses or IP addresses, it floods the received packet to all other interfaces. At this point, Wireshark can capture data packets sent from other computers on the same hub, i.e., packets from the local area network. This is a typical practice in older networks, now mostly obsolete.
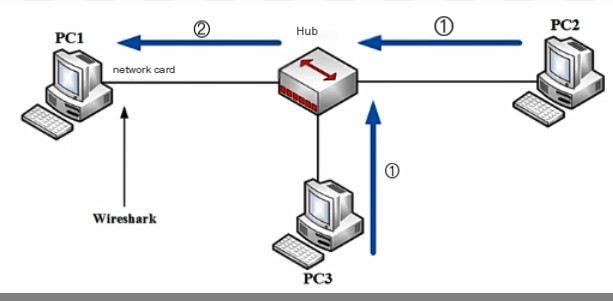
It is used to capture flooding traffic, packets within the collision domain, i.e., packets of the entire local area network.
11.1.3 Switch Environment
The switch environment is a more common method, including port mirroring, ARP spoofing, MAC flooding.
11.1.3.1 Port Mirroring
A switch is a product of the data link layer or even the network layer, which strictly follows the MAC address table on the switch for communication. So normally, the communication traffic between PC2 and PC3 is difficult to reach the network card of PC1. When PC2 and PC3 communicate, PC1 cannot capture packets through Wireshark. However, we can perform a SAPN port mirroring operation on the switch, which will copy the flow of the other two ports to PC1’s network card and set Wireshark to promiscuous mode for packet capture. This model is commonly used by many paid traffic analysis software. Under this method, the switch forwards packets strictly according to the tenlnet table and mac address table. When PC2 and PC3 communicate, by default PC1 cannot capture packets, but it is possible to set a policy on the switch, namely port mirroring. This way, communication packets between PC2 and PC3 are copied to the switch port connected to PC2, allowing PC1 to capture PC2 and PC3’s communication packets.
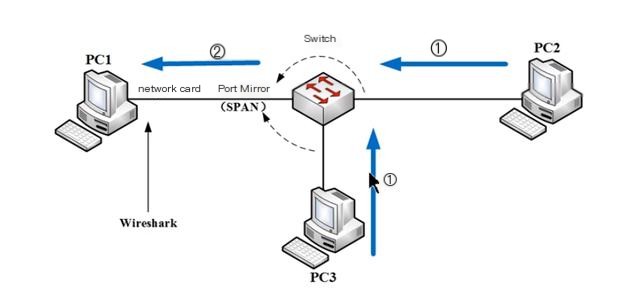
11.1.3.2 ARP Spoofing
Suppose we don’t have permission to perform port mirroring on the switch, but since there is a MAC address table and we want access to the flow within the local area network, intercepting the flow on PC2 and PC3. This can be achieved through the infamous ARP attack tool Cain&Abel, whose procedure is:
- First, PC2 sends an ARP request broadcast packet, and the switch forwards it to PC1 and PC3.
- PC1 and PC3 receive it, and in normal circumstances, PC1 will discard this packet since it’s looking for PC3, but ARP spoofing will reply “I am IP3, corresponding to MAC1,” which is a typical ARP spoofing or ARP virus.
- Finally, PC2 will encapsulate the traffic to the underlying MAC1 for transmission. If both PC3 and PC1 respond, ARP has a characteristic called last-in-first-out, which will create an erroneous binding, sending data packets to MAC1, resulting in PC2 and PC3’s communication flowing through PC1, which is also typical of traffic hijacking, local area network attacks.
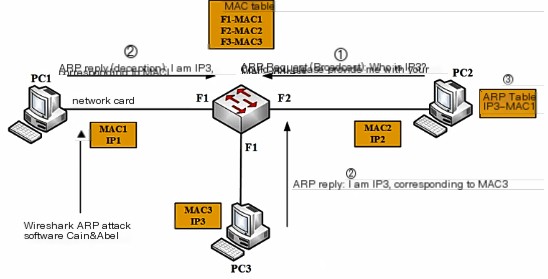
Steps are as follows:
(1) PC2 wants to communicate with PC3, so it broadcasts to the switch.
(2) Under normal circumstances, PC1 would discard this packet (since it’s not the target it seeks), but PC1 performs ARP spoofing here, telling PC2 it is the PC3 it’s looking for.
(3) Due to ARP’s last-in-first-out feature, PC2 is likely to mistake PC1’s MAC address as the PC3 it’s searching for.
(4) Thus, PC2 and PC3’s communication turns into communication between PC2 and PC1.
(5) Whether PC1 forwards the data (possibly modified) to PC3 subsequently, or not, depends entirely on PC1’s intentions.
Above is the typical situation of ARP attacks in a local area network.
11.1.3.3 MAC Flooding
By flooding with junk packets, creating numerous MAC addresses, the MAC address table of the switch will become like the table on the right (overloaded), squeezing out MAC2 and MAC3 from the MAC address table. Once such MAC addresses are forced out of the MAC address table, according to switch principles, if the received packet is unknown, it will flood outward. At this point, PC2 and PC3’s outbound traffic floods.
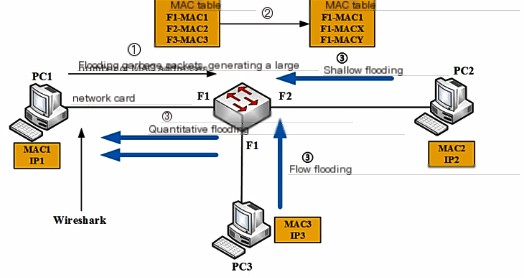
In this case, PC1 does not have port mirroring permission, so it cannot directly intercept the network’s traffic. So, what can be done?
(1) PC1 sends loads of junk packets, generating a large number of MAC addresses, causing the MAC table to overflow.
(2) The data packets sent by PC2 and PC3 are broadcast throughout the network since they couldn’t find a destination address, allowing PC1 to intercept the total network flow.
11.2 Underlying Principles
So, what is the underlying architecture of packet capture? Let’s start explaining Wireshark’s underlying principles.
Underlying principles: Wireshark is a tool for capturing packets at the bottom layer.
12. Overall Architecture of Wireshark
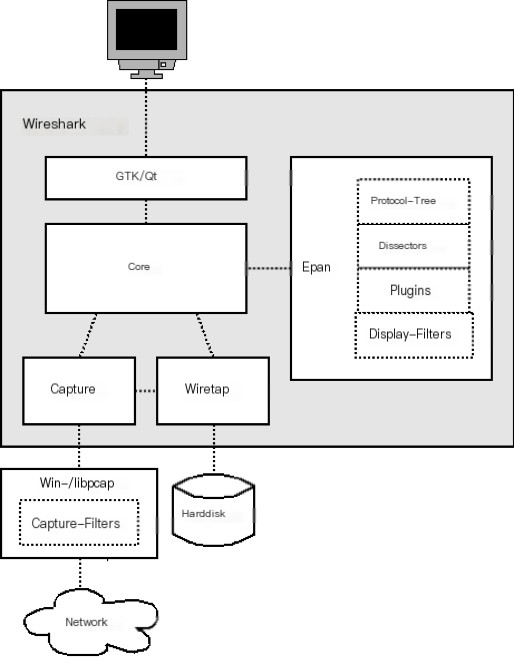
Wireshark comprises a five-layer architecture:
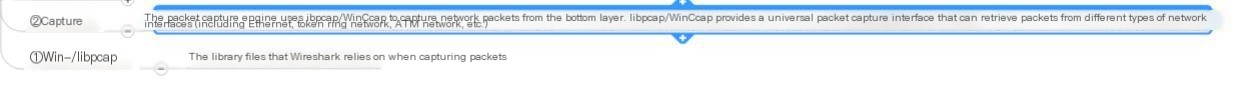
The lowest layer Win-/libpcap: Wireshark’s bottom-layer driver software, library files (driver files, library files) Wireshark depends on when capturing packets
Capture: Capture engine; uses the underlying libpcap/WinPcap to capture network packets, offering a general packet capture interface able to obtain packets from different network interfaces (including Ethernet, Token Ring, ATM networks, etc.)
Wiretap: Converts captured binary data into the required format files; the data obtained is some bitstreams. Through Wiretap (format support engine), one can read packets from capture files, supporting multiple file formats
Core: Core engine; connects other modules together through function calls, playing a role in interlinking and invoking them, Epan (Packet Analysis Engine): Protocol-Tree (stores protocol information of data packets in a tree structure, process each layer of protocol from root node through function handles), Dissectors (supports decoding over 700 kinds of protocols, recognizer identifies protocol fields and displays field values, Wireshark uses a protocol tree format to process each level of protocol in the data flow), Plugins (some protocol decoders are implemented as plugins, source files in the plugins directory), Display-Filters (engine for display filters, source files in the epan/dfilter directory).
GTK1/2: Graphic processing tools; handle user input/output displays, ultimately storing to Harddisk.
PS: Understanding fundamental principle knowledge is quite important, especially for subsequent topics.
13. Functional Modules
|
Module Name |
Function |
Source Code Subdirectory |
|---|---|---|
|
GTK/Qt |
Handles all user input/output (all windows, dialogs, etc.) |
/uiGTK: /ui/gtkQt: /ui/qt |
|
Core |
Main “glue code,” it combines other blocks together |
/ |
|
Epan (Ethereal Packet Analyzer) |
Protocol Tree – Saves protocol information data of capture files |
/epan |
|
Dissectors – Multiple protocol parsers |
/epan/dissectors | |
|
Plugins – Some protocol analysers implemented with plugins |
/plugins | |
|
Display-Filters – Display filter engine |
/epan/dfilter | |
|
Wiretap |
The Wiretap library is used for reading/writing libpcap format or other capture file formats |
/wiretap |
|
Capture |
Capture engine interfaces |
/ |
|
Dumpcap |
Capture engine. This is the only part that needs elevated permissions to execute |
/ |
|
WinPcap/libpcap |
(Not part of the Wireshark package) – Platform-dependent packet capture library, includes capture filter engine. This is why we have different display and capture filtering syntax – because two different filter engines are used |
– |
14. WireShark Code Flow Diagram
15. Summary
Alright, and with that Brother Hong has basically covered and shared the past and present of the Wireshark tool. It’s getting late today, so let’s end here! Thank you for your patience in reading~~
I am participating in the 2023 Tencent Technology Writing Training Camp Phase III Essay Contest, teaming up to win big prizes!



