I just returned from Russia last month, where I perused numerous security books at a library in Moscow. I was impressed by the advanced hacking techniques of the Russians. These security books are outstanding, and I decided to translate the entire content using a combination of human effort and GPT.
Table of Contents
- Annotations
- Preface
- Introduction
- Chapter 1: The History of Modern Ransomware Attacks
- Chapter 2: The Lifecycle of Modern Ransomware Attacks
- Chapter 3: Incident Response Process
For four consecutive years, ransomware attacks have been one of the most severe and destructive cyber threats, even being called the number one cyber threat. Victims can range from multinational companies like Toshiba or Colonial Pipeline to small private businesses. A successful attack can completely paralyze production, causing companies to lose funds (ransom amounts can reach hundreds of millions of dollars) and sensitive data, which attackers can download and sell to force victims into compliance. While the primary targets of ransomware remain in North America, Latin America, Europe, and the Asia-Pacific region, Russia has also ceased to be a safe haven in recent years. According to Group-IB, ransomware attacks on Russian companies increased by over 200% in 2021 alone. In the first half of 2022, this number quadrupled compared to the first quarter of 2021. When occasional arrests occur, ransomware operators temporarily hide and clean up traces, rebranding themselves. However, it is too early to say that the era of ransomware has ended. The Group-IB computer forensics team began focusing on ransomware threats before most people recognized their severity. Author Oleg Skulkin is a significant figure in the field of digital forensics, both in Russia and internationally. He has worked in information security for over a decade, writing and co-authoring five books on forensics and incident investigations. Oleg is a regular author of research reports, webinars, and technical blogs covering the development of the ransomware empire and the most active criminal groups: Conti, OldGremline, LockBit, Hive, and REvil. Readers will gain detailed insights into the history of ransomware, the tactics and techniques used by operators, and how to investigate these attacks. This book is essential for professionals in digital forensics, incident response, proactive threat hunting, cyber intelligence, and related fields.
Group-IB
Introduction
Human-operated ransomware attacks have fundamentally changed the modern threat landscape, becoming a primary threat faced by many organizations—this is why various organizations are raising their vigilance and preparing to respond to such incidents.
This book will take you into the world of modern ransomware attacks. It focuses particularly on proactive defense methods based on threat intelligence analysis to help counter and prevent such attacks.
Who is this book for?
This book will appeal to a wide range of technical experts—from students learning about cybersecurity to system and network administrators of small and medium-sized enterprises, and even incident response experts and cyber threat analysts who want to delve into human-operated ransomware attacks.
What does this book cover?
Chapter 1, “The History of Modern Ransomware Attacks,” introduces the world and history of human-operated ransomware attacks.
Chapter 2, “The Lifecycle of Modern Ransomware Attacks,” briefly describes how modern attackers operate during ransomware attacks.
Chapter 3, “Incident Response Process,” describes the response process for incidents related to ransomware attacks.
Chapter 4, “Cyber Intelligence and Ransomware,” provides an overview of cyber intelligence related to ransomware attacks.
Chapter 5, “Tactics, Techniques, and Procedures of Ransomware Gangs,” details the tactics, techniques, methods, and tools commonly used by ransomware attackers.
Chapter 6, “Collecting Threat Intelligence Data Related to Ransomware,” outlines different sources and methods for collecting intelligence related to ransomware attacks.
Chapter 7, “Digital Forensic Evidence and Its Main Sources,” provides an overview of various forensic evidence sources that can be used to reconstruct the attack lifecycle during incident response.
Chapter 8, “Initial Access Methods,” offers practical research on the initial access methods used by attackers.
Chapter 9, “Post-Exploitation Methods,” discusses various post-exploitation methods used by attackers.
Chapter 10, “Data Exfiltration Methods,” examines the methods used for data exfiltration.
Chapter 11, “Ransomware Deployment Methods,” studies different methods of ransomware deployment.
Chapter 12, “Unified Ransomware Attack Lifecycle,” describes the unique concept of the attack lifecycle and the use of ransomware.
Chapter 1: The History of Modern Ransomware Attacks
Ransomware attacks have become the second pandemic attack method after COVID-19 in 2020—unfortunately, they continue to evolve. Some attackers cease their activities, but a new generation of cybercriminals quickly fills their place.
These attacks are now well-known, but they began long before the infamous WannaCry and NotPetya ransomware outbreaks. Unlike uncontrolled ransomware, these are operated by different operators and their accomplices. Detailed reconnaissance of IT infrastructure vulnerabilities and their preparation for deploying ransomware can bring cybercriminals millions of dollars in cryptocurrency revenue.
There are many notable ransomware attack cases. In this chapter, we will focus on several historically significant cases, including the most representative threat in the modern IT environment—Ransomware-as-a-Service.
We will discuss the following cases:
- 2016: SamSam Ransomware
- 2017: BitPaymer Ransomware
- 2018: Ryuk Ransomware
- 2019 to present: Ransomware-as-a-Service
2016: SamSam Ransomware
The SamSam operators emerged in early 2016, fundamentally changing the ransomware threat landscape. Their targets were not ordinary users and individual devices but various companies attacked manually, infiltrating networks and encrypting as many devices as possible, including those containing the most critical data.
The attack targets were diverse, including businesses in the healthcare and education sectors and even entire cities. A typical example is the city of Atlanta, Georgia, which was attacked in March 2018, costing approximately $2.7 million to restore infrastructure.
Typically, attackers exploited vulnerabilities in public applications, such as the JBOSS system, or guessed passwords for RDP servers to gain initial access to the target network. To gain higher privileges, they used a series of common hacker tools and exploit programs, including the notorious Mimikatz, which can obtain domain administrator credentials. Afterward, SamSam operators scanned the internal network to gather information on available hosts, copied the ransomware to each host, and used another common dual-purpose tool, PsExec, to run it.
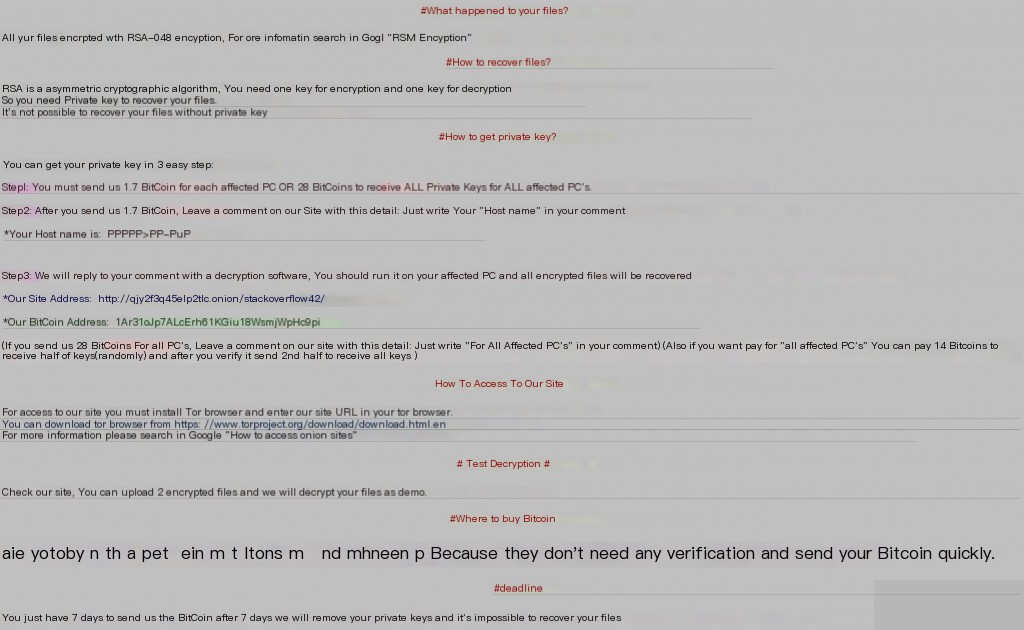
Image 1.1: Example of a SamSam ransom message
Attackers used payment websites on the dark web. Victims received notifications of ransom demands and decryption information generated by the ransomware (see Image 1.1).
According to Sophos, attackers earned approximately $6 million between 2016 and 2018 (source: https://www.sophos.com/en-us/medialibrary/PDFs/technical-papers/SamSam-The-Almost-Six-Million-Dollar-Ransomware.pdf).
The Masterminds Behind SamSam Ransomware
On November 28, 2018, the FBI released an indictment accusing Faramarz Shahi Savandi and Mohammad Mehdi Shah Mansouri of being involved in the international spread of SamSam ransomware.
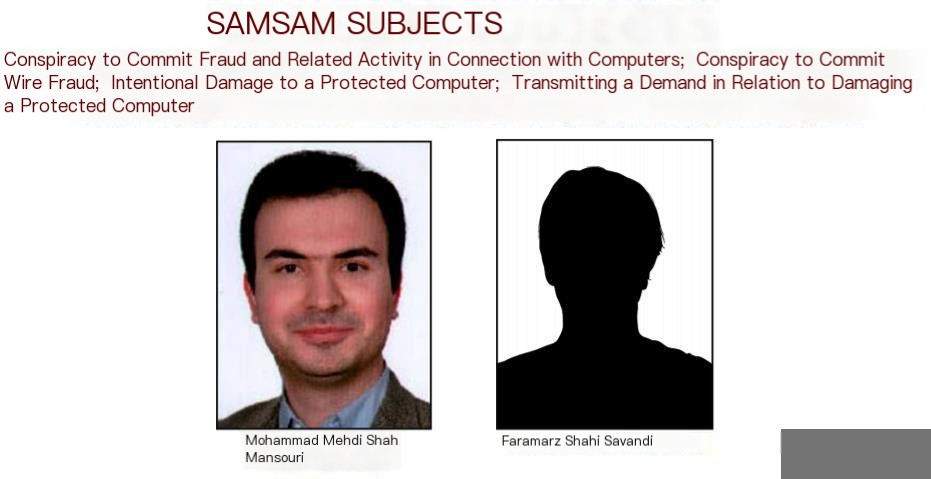
Image 1.2: Excerpt from the FBI wanted poster
These two suspects are from Iran. After the indictment was released, these criminals ceased their activities, at least under the name SamSam.
The SamSam case demonstrated that ransomware attacks on companies could be highly profitable, leading to the emergence of new similar criminal groups. One example is the BitPaymer ransomware.
2017: BitPaymer Ransomware
BitPaymer ransomware is associated with Evil Corp, a cybercrime organization believed to originate from Russia. This ransomware marked a new trend in human-operated attacks—hunting large targets.
It all started in August 2017 when BitPaymer operators successfully attacked several hospitals in NHS Lanarkshire, demanding a ransom of up to $230,000 (53 bitcoins).
To gain initial access, the group used its long-used tool—the Dridex trojan. The trojan allowed attackers to load PowerShell Empire, a popular post-exploitation framework, to move laterally within the network and gain elevated privileges, including using Mimikatz, similar to the SamSam operators. The criminals used Group Policy modifications to deploy ransomware across the enterprise, enabling them to send scripts to each host to launch ransomware instances.
Attackers communicated with victims via email and online chat.
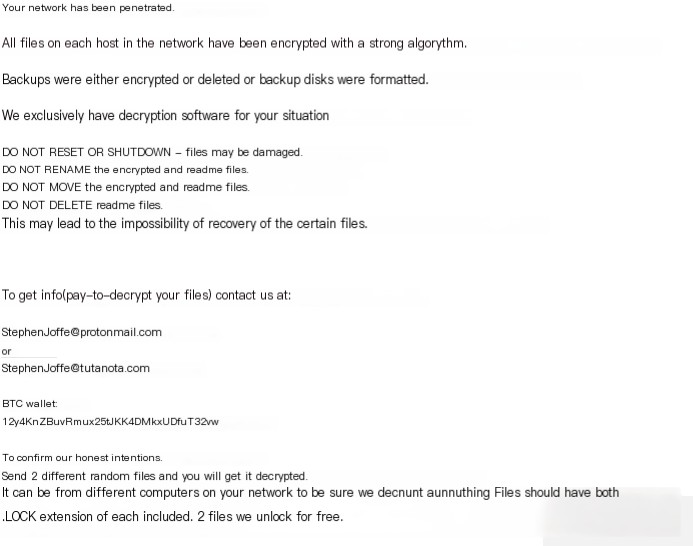
Image 1.3: Example of a BitPaymer ransom message
In June 2019, a new ransomware called DoppelPaymer, based on BitPaymer, emerged. It is reportedly managed by a subgroup of Evil Corp.
The Creators of BitPaymer Ransomware
On November 13, 2019, the FBI issued a statement accusing Maxim Viktorovich Yakubets and Igor Olegovich Turashev of operating the Dridex trojan.

Image 1.4: Excerpt from the FBI wanted poster
Maxim Viktorovich Yakubets is currently wanted for multiple cybercrime charges. Reportedly, a $5 million reward is offered for his capture.
Of course, Dridex is not the only trojan used in human-operated ransomware attacks. Another notable example is Trickbot, closely associated with Ryuk ransomware.
2018: Ryuk Ransomware
Ryuk ransomware took the hunting of large prey to a new level. This ransomware is associated with the Trickbot organization (also known as Wizard Spider) and remains active to this day.
According to AdvIntel, the organization has attacked various organizations throughout its history, earning at least $150 million (source: https://www.advanced-intel.com/post/crime-laundering-primer-inside-ryuk-crime-crypto-ledger-risky-asian-crypto-traders).
At certain times, Ryuk was called a triple threat because infections typically started with the Emotet trojan, which then downloaded Trickbot, used to load post-exploitation tools and ultimately deploy ransomware. Typically, Trickbot was used to load PowerShell Empire agents or Cobalt Strike Beacon, another popular post-exploitation framework.
Recently, the gang changed its toolset, starting to use a new trojan called Bazar. Notably, they began using “vishing” (voice phishing). Phishing emails did not contain malicious files or links but only fake subscription information and a phone number to cancel the subscription. If the victim called the number, the operator would guide them to download a malicious Microsoft Office file, open it, and enable macros, infecting the computer with the Bazar trojan. Like Trickbot, this trojan was used to load and run post-exploitation frameworks—usually Cobalt Strike.
Attackers used various methods to launch Ryuk, including the previously mentioned PsExec and Group Policy modifications. Initially, they provided email addresses for victims to contact them, but soon began using Tor’s onion services.

Figure 1.6. The work environment of Emotet operators
Despite the arrest of the attackers, the “ransom game” continues to attract more cybercriminals. Consequently, another phenomenon has emerged—Ransomware as a Service (RaaS).
2019 to Present: Ransomware as a Service (RaaS)
The year 2019 saw the rise of Ransomware as a Service (RaaS), and it remains a significant trend. Many ransomware developers began offering their products to various attackers in exchange for a portion of the ransom.
REvil, LockBit, Ragnar Locker, and Nefilim are just a few ransomware families spread through the RaaS model. Even if multiple attackers use the same type of ransomware, their strategies, techniques, and procedures can vary significantly.
However, many attackers currently use the same method: exfiltrating data before deploying the ransomware. This trend was set by the Maze ransomware operators in 2019. Nowadays, almost all attackers conducting similar attacks have their own Data Leak Sites (DLS).
Below is an example of a DLS used in the DoppelPaymer ransomware operation.
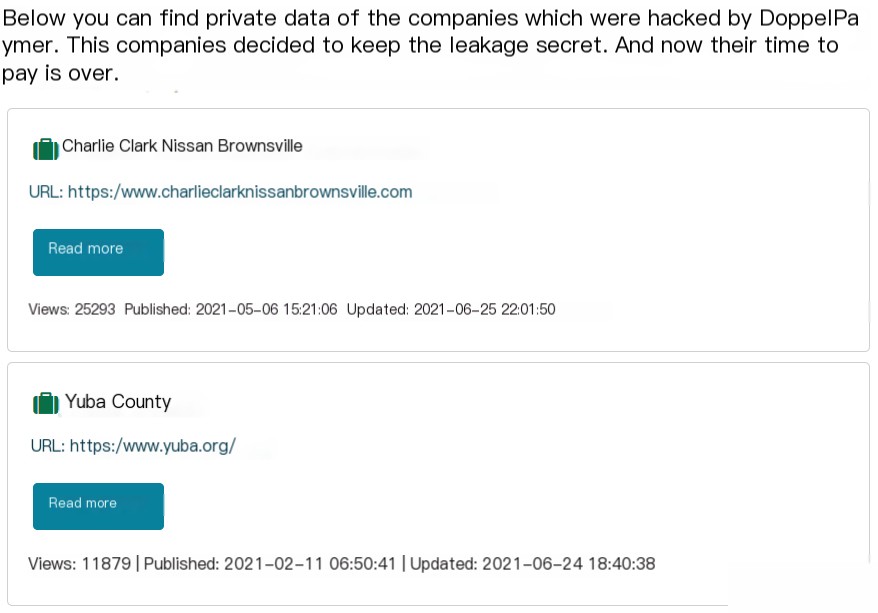
Figure 1.7. DoppelPaymer’s DLS[4]
Typically, the initiators of the attack do not manage the entire attack lifecycle themselves but instead utilize the services of other attackers. For instance, they might collaborate with Initial Access Brokers who provide access to compromised company networks. In some cases, they might pay professional penetration testers (pentesters) to escalate privileges or bypass protections, enabling seamless ransomware deployment across the enterprise.
Attackers involved in the project can receive different shares of the ransom. Usually, developers get about 20%, the initiators of the attack receive about 50%, Initial Access Brokers get 10%, and the remaining portion goes to auxiliary attackers, such as penetration testers or negotiators.
Ransomware as a Service is currently very prevalent. According to the Group-IB Ransomware Uncovered 2020/2021 report ( https://www.group-ib.com/resources/research-hub/ransomware-2021/), 64% of ransomware attacks in 2020 were carried out by individuals associated with RaaS.
Who is Behind Ransomware as a Service?
One individual associated with the NetWalker ransomware, Sebastien Vachon-Desjardins, a Canadian citizen, was charged in January 2021. He allegedly earned over $27.6 million through ransomware.
Another example involves two individuals associated with the Egregor ransomware who were arrested with the help of French authorities by tracking ransom payments made to them. Additionally, individuals associated with the Clop ransomware, who assisted attackers in laundering money, were also arrested in June 2021.
Therefore, Ransomware as a Service has enabled many cybercriminals—even those lacking skills and resources—to join the “ransom game.” This is a significant factor in making human-driven ransomware attacks a cyber pandemic.
Conclusion
In this chapter, you have learned about the history of modern ransomware attacks and gained insight into the attackers’ strategies, techniques, and procedures, their business models, and even some of the individuals behind the scenes.
https://www.group-ib.com/resources/research-hub/ransomware-2021/
In the next chapter, we will delve into the modern threat landscape related to ransomware and focus on the lifecycle of an attack—from initial access to the actual deployment of ransomware.
Chapter 2: The Lifecycle of Modern Ransomware Attacks
Ransomware attacks can be highly complex, especially when involving large enterprises. Therefore, understanding the typical lifecycle of an attack is crucial before diving into technical details. Knowing the lifecycle helps security professionals accurately reconstruct incidents and make appropriate response decisions at each stage.
As you learned in Chapter 1, “The History of Modern Ransomware Attacks,” Ransomware as a Service can be managed by a group of people or a series of individual attackers. This means that strategies, techniques, and procedures can vary greatly, but in most cases, the attack lifecycle is roughly the same because attackers usually have two main goals—stealing confidential information from the target network and deploying ransomware enterprise-wide.
In this chapter, we will briefly discuss the stages of human-driven ransomware attacks to form a clear understanding of these attack lifecycles and prepare for in-depth technical details.
This chapter will cover the following topics:
- Initial attack vectors
- Post-exploitation
- Data theft
- Ransomware deployment
Initial Attack Vectors
Any attack begins with gaining initial access. This can be achieved through connecting to an internal network via VPN, spreading trojans through targeted phishing, exploiting web interfaces of public applications, or even through supply chain attacks (another term is third-party attacks).
The three most common initial attack vectors are gaining access via Remote Desktop Protocol (RDP), targeted phishing, and exploiting software vulnerabilities.
Below are statistics on the most common ransomware attack vectors as of Q2 2021, collected by Coveware (source: https://www.coveware.com/blog/2021/7/23/q2-ransom-payment-amounts-decline-as-ransomware-becomes-a-national-security-priority).
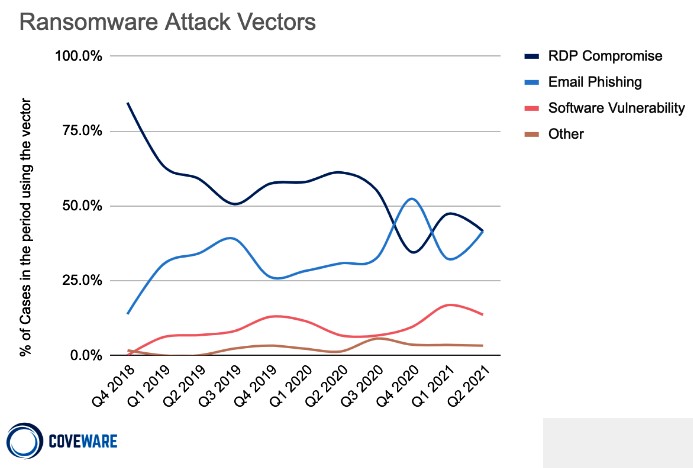
Figure 2.1. Coveware’s view on the most common ransomware attack vectors
We will explore each in detail, supplemented with examples.
Gaining Access via Remote Desktop Protocol (RDP)
Over the years, RDP has been the most common way for attackers to access target networks. From Chapter 1, “The History of Modern Ransomware Attacks,” you know it was used by SamSam operators. Of course, SamSam is not the only example. Currently, many attackers use this vector—including occasional attackers like Dharma ransomware operators and targeted organized groups like REvil.
The pandemic exacerbated this situation—many companies provided remote work opportunities for employees, having to open their servers, making them targets for various attackers, including ransomware operators.
For example, millions of devices can be seen with port 3389 (the default port for RDP) open through the Shodan search tool.
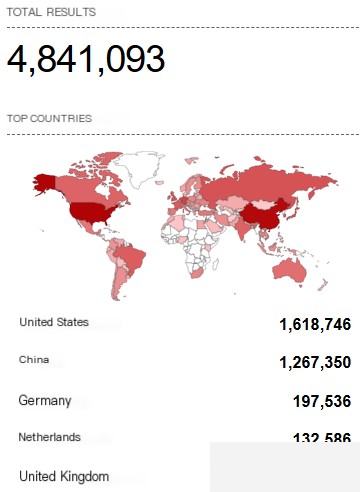
Figure 2.2. Number of devices with port 3389 open
A simple search returns millions of results—this is one reason why this initial attack vector is so popular among ransomware operators.
In practice, attackers do not necessarily attack these servers themselves; they might purchase access to them. Ransomware as a Service operators can rent ransomware and buy access to enterprise networks from so-called Initial Access Brokers. These brokers usually do not participate in the post-exploitation stage; more commonly, they sell or share initial access for a share of the ransom (typically around 10%).
Sometimes ransomware operators even post on underground forums to attract the attention of Initial Access Brokers. For example, Crylock ransomware operators posted a message indicating their interest in purchasing various types of enterprise network access.
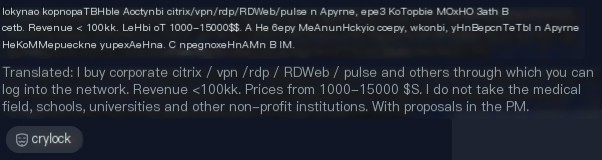
Figure 2.3. Post on an underground forum
Next, we will discuss another very popular initial attack vector—targeted phishing.
Targeted Phishing
Targeted phishing involves using social engineering. Attackers manipulate users into opening malicious attachments or clicking dangerous links to obtain credentials for VPN access or, as you learned in Chapter 1, “The History of Modern Ransomware Attacks,” to infect devices with trojans. Initially, many attackers used these malware for banking fraud, but they are also used to gain initial access to enterprise networks.
The most common examples of such trojans include:
- BazarLoader
- Hancitor
- IcedID
- Qakbot
- Trickbot
Of course, this is not an exhaustive list—these are just the most common tools paving the way for ransomware operators.
Typically, operators of these trojans conduct large-scale spam campaigns, primarily targeting enterprise users. The most common practice is using email chain hijacking—attackers send malicious files as replies to genuine emails from compromised email addresses.
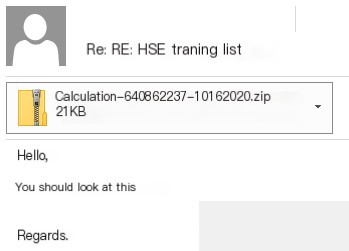
Figure 2.4. Example of email chain hijacking by Qakbot operators[5]
In some cases, attackers use more sophisticated methods: as mentioned in Chapter 1, “The History of Modern Ransomware Attacks,” BazarLoader operators also used voice phishing (vishing).
Below is an example of such phishing emails.
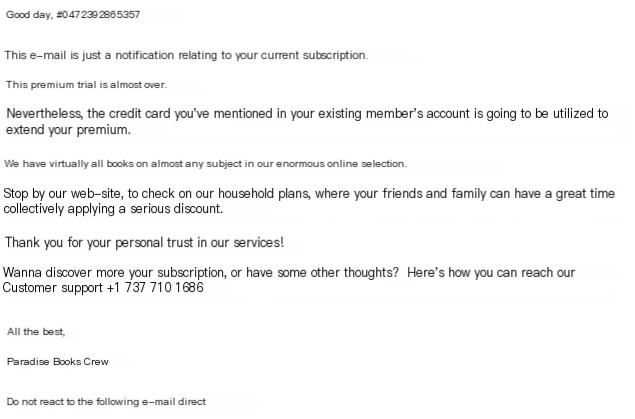
Figure 2.5. Example of a phishing email used to spread BazarLoader[6]
As you can see, there is no malicious attachment in this case. Instead, the attackers ask the victim not to reply to the email but to call a fake company to unsubscribe.
If the victim calls, the fake call center staff will guide them to a website, where they will open a malicious document and enable macros to download and run BazarLoader.
We will discuss the launch and obfuscation techniques of these trojans in later chapters, but remember that attackers can use these trojans to download other tools on the compromised host to perform post-exploitation steps and gain privileged accounts to move laterally within the network.
Before we conclude the discussion on initial attack vectors, we will review some software vulnerabilities that allow ransomware operators to gain network access.
Software Vulnerabilities
Software vulnerabilities have earned many Initial Access Brokers hundreds of thousands of dollars but have generated millions through Ransomware as a Service.
Of course, not every vulnerability can provide attackers with initial network access. The most commonly used vulnerabilities are those that allow remote code execution or credential file acquisition.
A good example of a vulnerability is the Pulse Secure VPN application. For instance, the CVE-2019-11510 vulnerability allows attackers to obtain usernames and unencrypted passwords fromFinally, in some cases, attackers can even exploit zero-day vulnerabilities—these are vulnerabilities in systems or devices that are known but not yet patched. In July 2021, the REvil group successfully exploited multiple vulnerabilities in Kaseya VSA remote management service and launched a malicious update package, leading to the deployment of ransomware. This attack affected many of Kaseya’s customers, including managed IT infrastructure service providers, resulting in a ransom demand of $70 million.
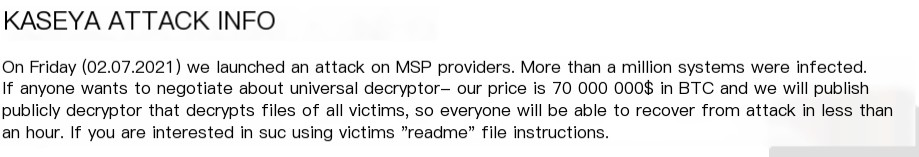
Figure 2.6. Information related to the REvil attack on DLS7
Of course, gaining initial access to the network is just the first step. In most cases, attackers need to escalate privileges, obtain credentials, conduct network reconnaissance, and perform other post-exploitation activities.
Post-Exploitation
Accessing the network is only half the battle. In many cases, attackers are not familiar enough with the network and can only access accounts with limited privileges, unable to disable security controls and move through the network to obtain sensitive data and deploy ransomware.
Post-exploitation activities depend on the type of access. For example, if attackers have VPN access, they can scan for vulnerabilities within the network to ensure their advancement.
Don’t be surprised—the infamous EternalBlue vulnerability (CVE-2017-0144) is still very common in many enterprise networks, including some large corporations.
Another widely used vulnerability by ransomware operators is Zerologon (CVE-2020-1472). It allows attackers to access domain controllers within a few clicks.
Attackers using various Trojans often start by diagnosing the network and Active Directory directory services using built-in Windows services like net.exe, nltest, etc., and then load third-party tools onto the compromised hosts. The most common tools include:
- AdFind
- Bloodhound (Sharphound)
- ADRecon
These tools allow the collection of information about users and groups, computers, subnets, domain permissions, and trust relationships within Active Directory.
If attackers access compromised nodes via RDP, they typically use various tools—from network scanners to password dumpers. Here are some of the most commonly used tools:
- SoftPerfect Network Scanner
- Advanced IP Scanner
- Mimikatz
- LaZagne
- Process Hacker
- ProcDump
- NLBrute
In some cases, especially when attackers already have initial access to a server, they can almost immediately obtain elevated account credentials by loading part of their toolkit, such as creating a snapshot of the LSASS (Local Security Authority Subsystem Service) process memory.
Another typical feature of modern ransomware attacks is the extensive use of various post-exploitation frameworks. I am almost certain you have heard of Cobalt Strike. It is the most widely used framework, not only by cybercriminals but also by state-sponsored hackers.
But this is just one example. When responding to ransomware attacks, you may also encounter:
- Metasploit
- PowerShell Empire
- CrackMapExec
- Koadic
- PoshC2
These services enable ransomware operators to solve various tasks: scanning the network, escalating privileges, dumping credentials, loading and running third-party tools and scripts, and moving laterally within the network using various methods.
Another important step is ensuring backup access. Specifically, they may spread the Trojans already used to gain initial access, launch components of post-exploitation frameworks on remote hosts, or even install legitimate remote access software like TeamViewer on some servers.
Once attackers have gained sufficient understanding of the network they have infiltrated and obtained elevated privileges, they can begin to achieve their primary goals—data theft and ransomware deployment.
Data Theft
Data theft, sometimes referred to as data breach, data exfiltration, or data leakage, is very popular among ransomware operators. Almost all attackers involved in human-operated ransomware attacks have their own data leak sites (DLS). They post information about successful attacks on these sites—even releasing stolen data if the company refuses to pay the ransom.
The amount of stolen data can vary significantly. In some cases, it is just a few gigabytes, while in other cases, it can reach terabytes. The exfiltrated data may include credit card information, Social Security Numbers (SSN), Personally Identifiable Information (PII), Protected Health Information (PHI), and National Provider Identifiers (NPI), as well as the company’s private and confidential information.
The following image shows an example of a DLS used by Conti ransomware.
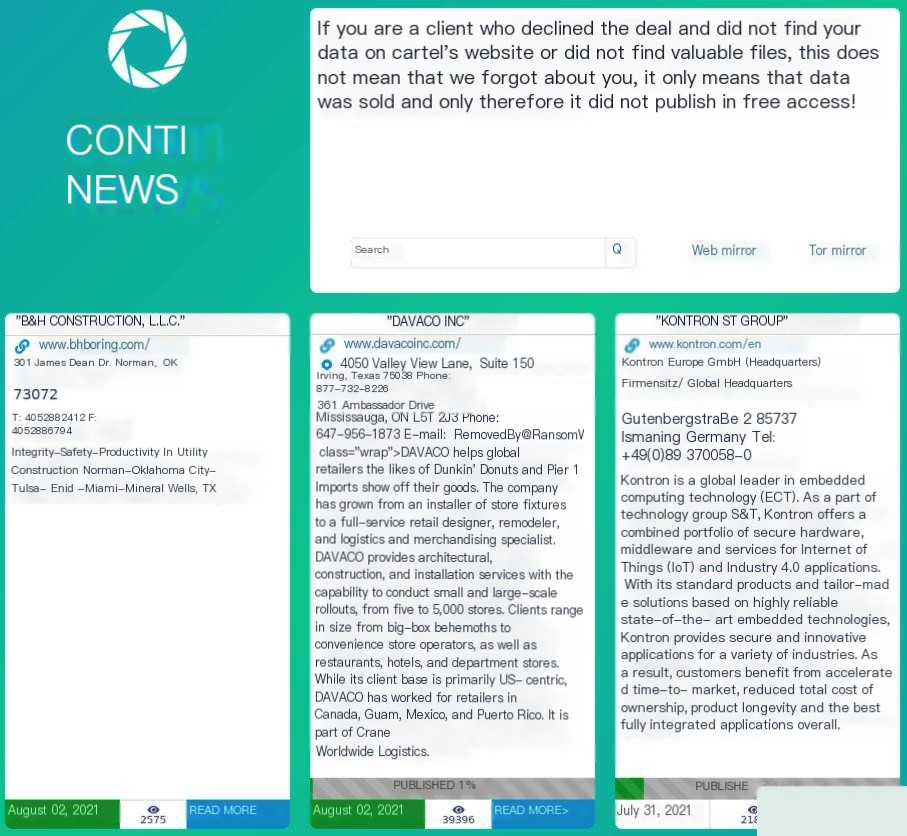
Figure 2.7. Conti ransomware’s DLS8
Most of these sites are located on the dark web and are typically accessed via the Tor browser. If you want to track changes on these sites using a regular web browser, it is recommended to use the Ransomwatch project (https://www.ransomwatch.org/). This site automatically captures and publishes screenshots of various ransomware operators’ DLS.
Attackers may spend a considerable amount of time extracting data from the compromised network—sometimes for several months. During this period, they may find the most sensitive data and ensure additional remote access methods to prevent the initial access method from being discovered and blocked.
There are generally two methods of data exfiltration. In the first case, attackers may set up a server for this purpose or use the server from which the attack was launched, for example, through post-exploitation frameworks.
In this case, attackers usually use legitimate tools like WinSCP or FileZilla for data theft. Detecting these tools can be very challenging, especially if the company’s security team does not have a dedicated threat monitoring group.
Typically, data needs to be collected first, but in some cases, it can be extracted directly from file servers without archiving.
The other method is using public cloud storage services like MEGA, DropMeFiles, etc. Attackers can use these storage services to post data on their DLS.
Below is an example of data stolen by Everest ransomware operators uploaded to DropMeFiles.
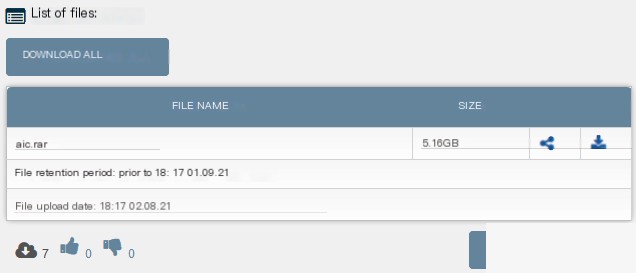
Figure 2.8. Stolen data posted by Everest ransomware operators
To upload data in this way, attackers can use a regular web browser or, in some cases, the corresponding client application. For example, Nefilim ransomware operators installed MEGAsync on target hosts to upload data.
Another notable example is Mount Locker’s affiliates using Amazon S3 storage to steal collected data. AWS and other cloud solutions are very helpful for large-scale data theft, making these solutions advantageous for attackers if not properly managed and monitored.
Once all sensitive data (at least from the attackers’ perspective) has been extracted, the victim’s network is ready for ransomware deployment.
Ransomware Deployment
Who do you think is the biggest enemy of ransomware operators? That’s right—backups, if they are protected and stored securely. But they have a significant weakness—attackers can delete them.
Unfortunately, system administrators often forget the 3-2-1 rule (3 backups stored on 2 different media, with 1 stored offsite) and the necessity of using separate accounts and enabling multi-factor authentication for backup servers. Nowadays, properly protecting backups is crucial not only for preventing ransomware but also for ensuring compliance with industry regulations.
Without adequate security measures, attackers can easily access backup servers and delete all available backups. In such cases, the victimized company has no choice but to pay the ransom.
Some ransomware includes features to delete typical backup solution file extensions. For example, the list of backup file extensions deleted by TinyCryptor includes:
- vbm
- vib
- vbk
- bkf
- vlb
- vlm
- iso
You may know that the Windows operating system has a built-in backup mechanism called Volume Shadow Copy Service. It creates backups of files and even volumes, allowing users to restore data to a previous state.
Naturally, ransomware operators have taken note of this Windows feature—most ransomware will disable it and delete all available shadow copies.
Backups are not the only enemy of ransomware operators. Another enemy is security software that can effectively block ransomware execution—of course, if it is functioning properly.
Attackers can add ransomware to exclusion lists or directly disable existing security software. At this point, attackers usually have domain administrator privileges, so they can deploy batch scripts and manipulate group policies to achieve their goals. Of course, this is not the only method—they can also disable it through the security software’s console interface.
There are many methods for ransomware deployment, including modifying group policies, using PsExec, or even manually copying and launching it—depending on the cybercriminals’ preferences.
Another important point is that the system must remain accessible so that the victim can receive emails or links to contact the attackers. This is why many ransomware programs add system folders to exclusion lists. Here are the folders included in Darkside ransomware’s exclusion list:
- $recycle.bin
- config.msi
- $windows.~bt
- $windows.~ws
- windows
- appdata
- application data
- boot
- mozilla
- program files
- program files (x86)
- programdata
- system volume information
- tor browser
- windows.old
- intel
- msocache
- perflogs
- x64dbg
- public
- all users
- default
Interestingly, the exclusion list includes the tor browser folder because Darkside has a victim portal on the dark web, accessible only via the Tor browser.
Once the ransomware deployment is complete, attackers are ready to negotiate the ransom amount with the victim. Sometimes they demand separate ransoms for decryption and for deleting the stolen data.
Sometimes the attack does not end there. For example, it is well known that attackers associated with the REvil group will launch DDoS attacks on victims who refuse to pay.
Conclusion
Now you have a clear understanding of the typical stages of a ransomware attack. Although these attacks can vary greatly in tactics, techniques, and procedures, the main goals are almost always the same: gaining full control of the domain, stealing the most valuable confidential data, and deploying ransomware.
In the next chapter, we will explore the incident response process and its six stages for dealing with modern ransomware attacks.
Chapter 3: Incident Response Process
You already have a good understanding of modern ransomware attacks, so it’s time to explore the incident response process. The analysis process may seem a bit tedious, but understanding it is very important—it will help you respond to incidents more quickly.
We will not dwell on things you already know. Instead, we will explore the classic incident response process developed by the National Institute of Standards and Technology (NIST) and explain it with real事件准备
- 威胁检测与分析
- 控制、消除与恢复
- 事件后处理
事件准备
事件准备是事件响应过程中的一个重要部分。这不仅涉及团队,还涉及被攻击的IT基础设施。想象一下,如果您必须应对一个与勒索软件相关的事件,但您的基础设施完全被加密,并且只运行基础级别的日志记录和防病毒软件。听起来很可怕,但这正是我所调查的许多事件的实际情况——公司在受到攻击之前不会考虑安全问题。
非常重要的是要认识到您的基础设施缺乏安全控制和人员。为此,您不需要等待实际的事件发生——在许多情况下,简单的渗透测试就足够了。
一些公司即使在成功的勒索软件攻击之后也不考虑安全问题。一个显著的例子是澳大利亚的运输和物流公司Toll Group。2020年2月,该公司遭到Netwalker勒索软件运营者的攻击。5月,Toll Group恢复正常运行,立即又被另一个团伙Nefilim勒索软件成功攻击。
如您所见,勒索软件的世界非常残酷,因此准备团队和IT基础设施应对威胁至关重要。
团队
实际上,公司不一定需要内部的事件响应团队。许多服务公司提供此类服务,包括识别和分析威胁,并提供消除威胁的指导。
此外,公司还可以利用外部管理检测和响应(Managed Detection and Response, MDR)团队的服务,这些团队负责监控和响应。
当然,如果需要,公司可以在内部创建事件响应团队,作为安全部门或内部安全运营中心(Security Operations Center, SOC)的一部分。
首先,这种团队必须具备响应事件的能力。以下是具体含义:
数据收集能力
在事件响应过程中,能够收集必要的数据至关重要——从单一的运行进程的工件到完整的事件日志或注册表文件。我们一直使用自己的扩展检测和响应(Extended Detection and Response, XDR)解决方案Group-IB MXDR,这是市场上众多解决方案之一。重要的是,选择的解决方案能够监控整个基础设施,从任何主机收集数据,并在必要时进行主动威胁搜索。虽然这些任务可以通过部署各种脚本来解决,但这种方法可能不太高效,并显著增加事件响应的时间。
数据分析能力
数据收集很重要,但分析更重要。XDR数据可以节省大量时间,但如果不可用,您需要使用各种数字取证工具,包括商业和开源工具。这些工具可以提高处理速度,但不幸的是,它们无法加速分析——因为勒索软件攻击的分析,和这些攻击本身一样,总是由人来执行。另一个重要的点是,必须访问良好的威胁情报来源:这将加快分析速度,并帮助您更好地理解您正在寻找的内容。最后,需要进行培训。培训可以通过各种形式进行:在教练指导下,通过预录视频,借助网络研讨会——甚至只是阅读一份好的威胁报告或书籍(例如这本书)。
沟通能力
这是一个非常重要的方面。在事件响应团队中应分配职责——至少一个人负责与管理层的互动,另一个人负责与技术人员的沟通。
基础设施
本节中写的内容仅适用于内部事件响应团队成员,也就是说,您可以与其他团队沟通并向他们提供IT基础设施配置建议。
在事件响应过程中,最糟糕的情况是缺乏通讯和空白(或太短)的事件日志。如您所知,在某些情况下,攻击者在实际部署勒索软件之前可能会在基础设施中待上数周,为了追踪他们到第一个被攻破的主机,您需要该期间内的所有日志。
这在实践中是如何运作的?假设您通过命令jump psexec_psh发现主机上运行了Cobalt Strike Beacon——这种情况很常见,通常会记录创建新服务的事件ID为7045的系统日志。我们首先关注的通常是启动源——这并不难找到,例如,通过系统登录(事件ID 4624)。难题出现在服务创建两周前,而您的安全日志仅记录了最近三天的事件。
另一个例子是防火墙。防火墙确实不能阻止0day,但它们可以在事件响应中非常有用——当然,前提是您保留了需要的时间段的日志。
我曾处理过一个案例,我们在一个小时内确定了所有用于初始访问的主机。攻击者使用目标钓鱼电子邮件附件获取初始访问权限,但这次他们攻击了四台主机。我们快速找到其中一台主机,因为它被用于部署勒索软件——我们发现该主机在四个月前被攻破。客户妥善保存了日志,因此我们能够回溯四个月,通过与命令和控制服务器的通讯识别其他受感染的主机。
在我的实践中,有一次我们在一个小时内确定了所有用于初始访问的主机。攻击者通过带有恶意附件的目标钓鱼电子邮件获取了初始访问权限,但这次他们攻击的不止一台主机,而是四台。我们很快找到了其中一台,因为它被用于部署勒索软件——我们发现这台主机在四个月前被攻破。我们的客户很好地保留了日志,因此我们能够回溯四个月,通过与命令和控制服务器的通信识别出另外三台主机。如果没有这些日志,查找工作可能会花费更多时间,而攻击者也有机会改变战术、技术和程序(TTPs),并植入新的后门。
我想你已经明白,仔细保存日志对于应对任何事件至关重要。如果你目前还没有保存日志,一定要实施日志保存和管理流程。每个行业都有自己的规则和规定,涉及到日志的保存和管理。一定要查清哪些要求适用于你的组织。
另一个与基础设施相关的重要方面是技术安全措施。我之前提到过XDR(扩展检测和响应)。你可能会问,为什么是XDR,而不是市场上的其他许多解决方案?原因在于,XDR可以用于监控、威胁搜寻、收集取证数据,更重要的是,它可以阻止恶意文件并隔离受感染的主机。当然,安全信息和事件管理(SIEM)工具也能提供监控、警报和威胁搜寻功能,但它们不能阻止恶意文件或隔离主机,而这在应对勒索软件攻击时尤为关键。另一方面,SIEM工具可以长期保存日志,因此如果你处理的是长期事件,正确配置的SIEM可能发挥关键作用。
当然,这不仅仅是关于XDR:它只是最现代和有效的防止和应对事件的工具。工具越多,处理事件就越容易。
现在我们来看看威胁检测和分析的阶段。
威胁检测和分析
这是事件响应过程中最重要的两个阶段。为什么?如果检测和分析失败,很可能你的基础设施或客户的基础设施将被某种勒索软件加密。
有两种可能的情况:
- 一切已经被加密——也就是说,已经发生了攻击,需要重建事件。
- 网络中出现了勒索软件的前兆,需要尽快定位并消除。
通常,如果攻击已经发生,确定你遇到的勒索软件变种并不难——只需阅读勒索信息。这些信息通常包含指向门户网站的链接,受害者可以在这些门户网站上与攻击者进行谈判。
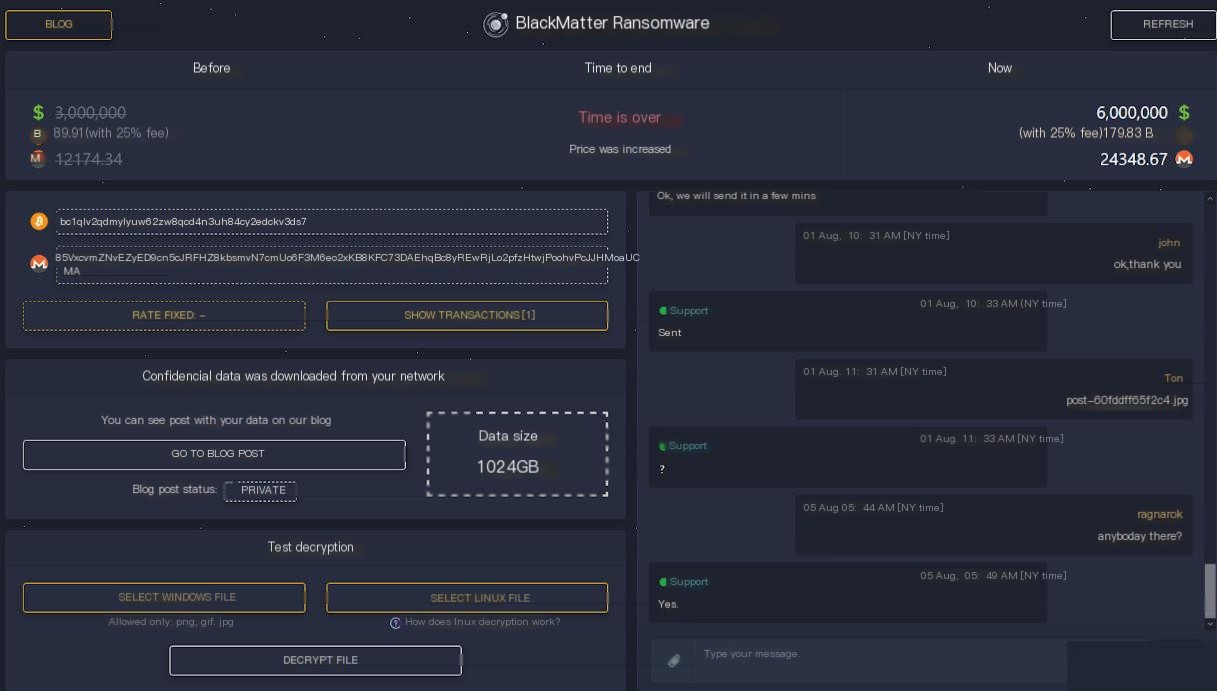
图3.1. BlackMatter勒索软件的门户网站
如图3.1所示,这些门户网站向受害者提供了大量信息,包括赎金金额、支付细节、被盗数据——甚至提供测试解密和聊天支持。但更重要的是,屏幕顶部显示了勒索软件家族的名称——BlackMatter。利用这些信息,你可以继续了解该攻击者通常使用的TTP。
你可以从各种公开来源获得一些信息,我们将在第6章“收集勒索软件相关的网络威胁数据”中详细讨论这一点。此外,访问商业网络威胁分析平台也非常有用。
图3.2. Group-IB威胁情报平台上的BlackMatter档案
为什么这很方便?这些平台包含了关于勒索软件的丰富信息,包括战略、操作和战术层面的内容。你可以找到关于勒索软件TTP的信息,包括它们使用的工具、漏洞等。此外,你还会看到许多不同的妥协指标,如哈希值、文件名和IP地址。最后,通常还有关于目标国家和行业的信息。我们将在第4章“网络威胁情报和勒索软件”中更详细地讨论这个主题。
拥有这些信息后,你就可以推测攻击者如何获得初始访问权限,并使用了哪些手段来提升权限、获取凭证、在网络中横向移动等。
让我们看看我们在前几章中讨论过的一个例子——Ryuk勒索软件。
如果攻击已经发生并且文件已被加密,你需要找到勒索软件的部署源及其使用的方法。Ryuk通常从域控制器部署。假设你很幸运找到了具体的控制器,但问题在于,由于日志记录不足,你无法看到连接到这台服务器的源头。
然后你分析已有的网络威胁信息,发现与Ryuk相关的攻击者通常使用Cobalt Strike、AdFind和Bloodhound等工具,并通过目标钓鱼邮件获得初始访问权限,传送Trickbot或BazarLoader。
现在你知道该找什么——勒索软件运营者非常喜欢使用各种后期利用框架,如Cobalt Strike,而这些框架通常会留下大量的痕迹,可以在事件响应过程中找到。关于数字取证工件的来源,你可以在第7章“数字取证工件及其主要来源”中了解更多。
重要的是,威胁主体的TTP信息不仅对于事件响应很重要,也对预防事件有帮助,因此,如果你或你的团队成员找到了关于攻击者行为的信息,应立即调整安全措施以应对。
让我们看看当攻击还未发生时的情况——勒索软件尚未部署,但已经有一些入侵前兆。它们是什么样的?
我们已经知道,攻击者通常使用Trickbot或BazarLoader来获得初始访问权限。这意味着我们必须对任何与这些威胁相关的事件作出反应,例如来自防病毒软件的警以下是一些用于勒索软件攻击的恶意软件常用的持久性机制:
- 注册表启动键或启动文件夹
- Windows服务
- 计划任务
如果你已经删除了恶意软件,有时可以不删除持久性机制,但这有时可能导致误报威胁。有一次我的客户发现了一个与Cobalt Strike相关的恶意服务——我的团队立即做出了反应,但很快发现这只是几年前客户团队处理过的一次攻击的残留物。
所以,你已经阻止了命令服务器,修改了泄露账户的密码,删除了恶意软件和攻击者的工具。这样够了吗?你准备重新启动这个工作站或服务器了吗?如果你百分之百确信一切都已清除,那为什么不呢?如果不确定,最好重新从映像中部署系统。
另一种情况是,网络已经被加密。在这种情况下,通常只有两个选择:与网络犯罪分子谈判并支付赎金,或者从头开始重建基础设施。
在第一种情况下,攻击者提供的解密器可能会带来额外的问题。以下是另一个例子:ProLock勒索软件运营者在2020年4月至6月期间活跃,一些受害者同意支付赎金并获得了解密器。但问题在于,解密器不能正常工作,解密过程中超过64MB的文件会被损坏。当这个问题曝光后,攻击者的声誉受损,不久ProLock就消失了。
当然,并非所有解密器都工作不良。许多攻击者提供的可执行文件确实能够解密所有文件。但这并不保证支付赎金后系统的安全——已知有攻击者一次又一次地攻击同一家公司,试图赚取更多的钱。
因此,在成功的攻击后——尤其是如果组织决定支付赎金——改善安全状况以防范未来的攻击是极其重要的。这就是事件后处理阶段的目的。
事件后处理
在最后阶段,事件响应团队应该帮助受害公司了解攻击者为何成功,以及如何避免类似的情况。
根据使用勒索软件的不同,事件的生命周期可能完全不同。根据你发现的内容,你可以提供一系列建议。让我们看看一些通用的建议。
如我们所知,许多勒索软件攻击始于公开可访问的RDP服务器,因此一个好的建议是选择其他远程访问方法,或为这些RDP连接实施多因素认证。
对于公开可访问的基础设施部分,组织应确保修补所有漏洞,特别是那些允许攻击者获取有效账户凭证或远程执行代码的漏洞。
如果攻击者通过目标钓鱼获取访问权限,可能需要对员工进行额外培训,或提高邮件流量的安全性,例如实施恶意软件“沙箱”系统,这些系统会分析所有进出邮件中的附件和链接。
同样地,内部网络安全产品——在某些情况下,只需正确配置它们,而在其他情况下,则需要更换它们。此外,可能还需要额外的监控能力和受过培训的人员。
最后,如果现有的备份最终被删除(如你所知,这是攻击者的常见策略),组织应考虑备份保护,例如实施3-2-1规则,为备份服务器使用单独账户,并为任何类型的访问实施多因素认证。
这不是事件后处理的全部内容,而只是一些示例,帮助你理解通常在这个阶段做什么。
希望现在你对典型的事件响应过程有了更清晰的理解。你可以在NIST编写的《计算机安全事件处理指南》中找到更多信息。
结论
在这一章中,我们讨论了事件响应过程的各个阶段,让你对抗击勒索软件攻击的主要步骤有了清晰的认识。我们将继续研究这个问题,以便你能够更好地了解细节。
你已经知道,网络威胁情报是事件响应过程的重要组成部分,因此在下一章中,我们将讨论不同层次的分析,并特别关注勒索软件攻击。我们将查看公开的威胁报告,并从中提取不同类型的数据,以便充分了解它们的区别。
第4章 网络威胁情报和勒索软件
网络威胁情报是应对事件的重要组成部分。读完前一章后,你应该对当前的威胁形势和攻击者使用的方法有了清晰的了解。现在,快速进行分析并进入应对事件的下一阶段是至关重要的。
接下来,我们将讨论各种类型的网络威胁信息:战略信息、操作信息和战术信息。实践总是胜过理论,因此在我们的讨论中,我们将分析一个公开的报告,尝试从中提取各种类型的分析数据。
因此,在本章中,我们将通过勒索软件的视角来审视所有类型的网络威胁数据:
- who and why?——网络威胁的战略信息。
- how and where?——网络威胁的操作信息。
- what?——网络威胁的战术信息。
网络威胁的战略信息
网络威胁的战略信息通常面向决策者:首席信息安全官(CISO)、首席信息官(CIO)、首席技术官(CTO)等。它包括对攻击者活动和动机的全局描述,并回答“谁”和“为什么”的问题。这些信息为CISO、CIO和其他网络安全领导者提供技术和战术知识,帮助他们预见威胁领域的新趋势。
因此,“谁”指的是针对组织的攻击者,而“为什么”则是他们的动机。
从动机的角度来看,网络犯罪分子相当可预测,他们的主要目标是从受害者那里获取金钱。通常,这涉及到相当可观的金额。
另一个重要的问题是哪些组织成为攻击目标。例如,一些勒索软件运营者不会攻击医院、政府机构、关键基础设施等。BlackMatter运营者就是一个很好的例子,他们禁止其同伙攻击某些类别的组织(见图4.1)。
现在让我们看看SentinelLabs团队的公开报告《Hive攻击:针对医疗行业的人类操作勒索软件分析》(Hive Attacks | Analysis of the Human-Operated Ransomware Targeting Healthcare)。报告可在以下链接查看: https://labs.sentinelone.com/hive-attacks-analysis-of-the-human-operated-ransomware-targeting-healthcare/
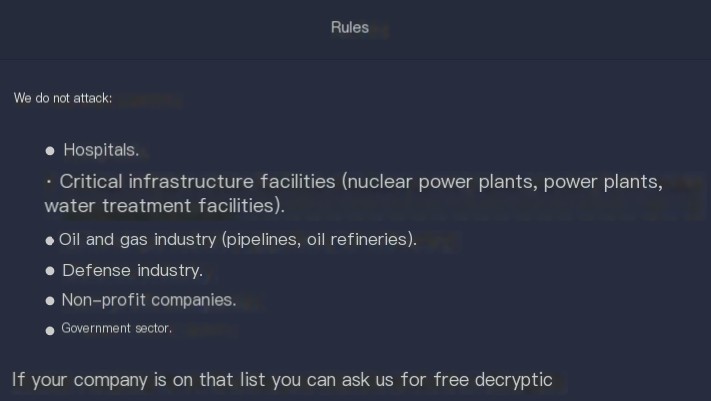
图4.1. BlackMatter勒索软件网站上的规则部分
第一个重要的战略事实是,使用Hive勒索软件的攻击者的目标是医疗机构。是的,一些运营者及其同伙可能专门针对特定的业务领域或行业,有时是在特定的国家。例如,研究人员描述了对俄亥俄州Memorial Healthcare System医院的攻击,导致该组织不得不将急诊患者从其多个医院转移到其他机构。攻击者非常清楚,医疗行业是一个有利可图的环境,包含大量数据。医疗行业有许多入口点,允许攻击者随心所欲地渗透和移动。如果我们尝试深入分析这一点,并分析在攻击者泄漏数据网站(DLS)上可以找到的受害者数据,可以发现更多与攻击相关的数据(见图4.2)。
由于受害者名单不仅限于医疗机构,分析可以提供更详细的目标概览。这使得决策者能够清楚地了解他们的业务是否真的面临威胁。
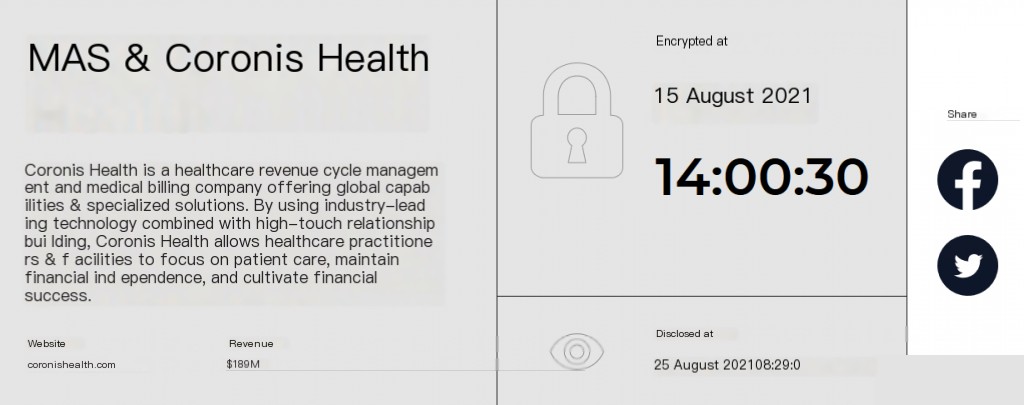
图4.2. Hive泄漏数据网站上的受害者信息
此外,从报告中可以看出,使用Hive勒索软件的团伙非常活跃。他们在2021年6月底开始活动,已经进行了至少30次成功的攻击。这一事实也有助于在防御策略中确定优先事项。
让我们进一步分析报告中可以提取的网络威胁的操作信息。
网络威胁的操作信息
网络威胁的操作信息帮助我们了解攻击者的能力,了解他们的基础设施,当然还有他们的战术、技术和程序。这种信息让我们知道“如何”和“在哪里”,因此它面向安全运营中心(SOC)分析师、事件响应专家、威胁猎人等。
你可能已经明白,“如何”的答案让安全人员能够收集关于犯罪者使用的各种战术、技术和程序的信息,并帮助发现和消除它们。回答“在哪里”可以让我们知道在哪里寻找实施各种战术、技术和程序的痕迹,这使得我们可以采取预防性措施。
让我们继续分析SentinelLabs关于Hive勒索软件的报告,并专注于“技术分析”部分。
描述战术、技术和程序(TTPs)的最佳结构之一是MITRE ATT&CK®。
MITRE ATT&CK®是一个关于攻击者在网络攻击中采取的行动的知识库和分类系统。它由以下主要部分组成:
- 战术——攻击者的战术目标,如获得对目标网络的初始访问权限。
- 技术——攻击者为实现目标使用的一般方法定义,例如目标钓鱼。
- 子技术——更具体的方法描述,例如使用恶意附件。
- 程序——攻击者具体如何使用技术或子技术,例如在目标钓鱼电子邮件中嵌入恶意的Microsoft Office文档。
在本书中,我们将频繁引用MITRE ATT&CK®,因此如果你不熟悉这个知识库,可以访问官方网站: https://attack.mitre.org/
在SentinelLabs报告的“技术分析”部分,首先我们看到初始攻击向量可能不同。遗憾的是,报告中没有具体说明可能的选项。
但我们立即了解到攻击者最喜欢的后期利用框架是Cobalt Strike。不过,报告中没有详细说明它在攻击中的具体使用方式。与此同时,研究人员分享了有关另一种工具的信息,即ConnectWise——一种被攻击者用于维持对被攻破网络访问的合法远程管理工具。正如你从第3章“事件响应过程”中所知,这种工具在与勒索软件相关的团伙中非常普遍。
MITRE ATT&CK®中记录了这种方法。其ID为T1219,名称为Remote Access Software(https://attack.mitre.org/techniques/T1219/)。该方法的要
Here we delve into the sub-technique of clearing traces on a host—file deletion (T1070.004).
This is not the only batch file created by the ransomware. Another file named shadow.bat is used to delete shadow copies to prevent file recovery using the operating system’s built-in features.
The contents of the command file are as follows:
This involves methods to suppress system recovery capabilities (T1490).
Finally, one of the most crucial techniques of ransomware is encrypting data to exert influence on the victim (T1486).
Let’s compile the data we found into a table.
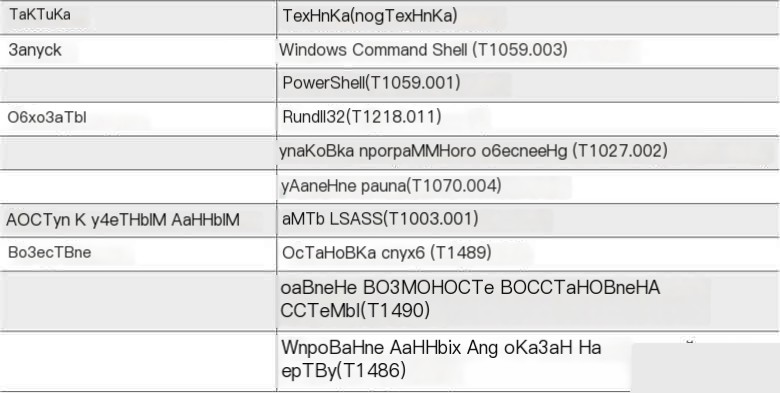
Table 4.1. MITRE ATT&CK Summary Table
As shown in the table, we cannot reconstruct the entire attack lifecycle from the report, but we still extracted many TTPs, which can be used in incident response and proactive threat hunting.
We will continue analyzing available reports in Chapter 6, “Collecting Cyber Threat Data Related to Ransomware.”
Tactical Information on Cyber Threats
Tactical information on cyber threats is used in various security products such as Security Information and Event Management systems (SIEM), firewalls, Intrusion Detection/Prevention Systems (IDS/IPS), etc. These products utilize Indicators of Compromise (IoC).
This level of cyber threat information focuses on the “what”—what exactly happened. Traditionally, this type of analysis is the most common, with many vendors providing so-called feeds—news feeds or latest information feeds, but more and more organizations are now turning to TTPs because the lifecycle of traditional indicators is very short.
In most cases, these indicators include IP addresses, domain names, and hash values. Typically, hash values come in the following types:
- MD5
- SHA1
- SHA256
These indicators can be shared through cyber threat analysis platforms like MISP and can be used for research and detection.
Returning to the report we are analyzing. The report has a section on “Indicators of Compromise.” It contains multiple hash values, including SHA1 and SHA256 types. Since these are hash values of the same file, we focus on the first type—SHA1:

If you use services like VirusTotal (https://www.virustotal.com/) to analyze various malicious content, you can find that all these hash values are related to variants of Hive ransomware.
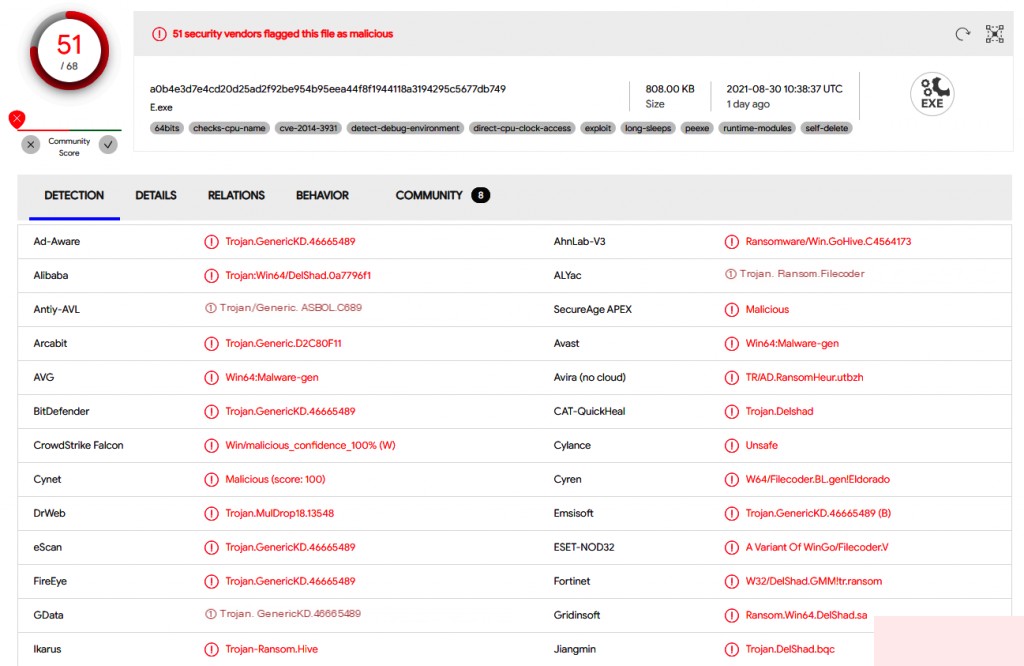
Figure 4.3. Record of a hash value in VirusTotal
From a detection perspective, they are not very useful because, in most cases, ransomware versions are customized for each attack, meaning their hash values will not match.
Additionally, the report mentions IP addresses related to Cobalt Strike Beacon. You can always gather more information about IP addresses, especially those associated with various post-exploitation frameworks. For example, you can check if a server is associated with Cobalt Strike (see Figure 4.4).
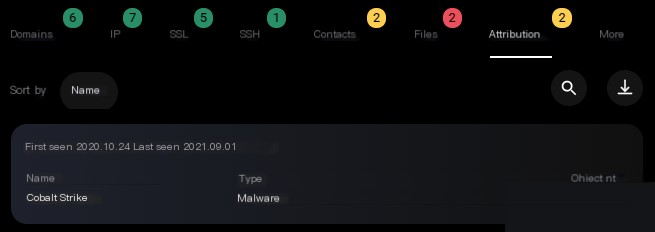
Figure 4.4. Information collected about the checked IP address by Group-IB MXDR platform
The Group-IB MXDR platform has a feature to build relationship graphs, which can be used to gather more information about the indicators you have collected. In Figure 4.4, we see that IP address 176.123.8.228 belongs to a Cobalt Strike server, so the security team should block or inspect it.
As you can see, even by analyzing a brief public report, an experienced analyst can gather enough cyber threat information, which is very useful for incident response.
Conclusion
In this chapter, we discussed various types of cyber threat information, including strategic information, operational information, and tactical information, their differences, and target audiences. We also analyzed a public threat report, extracting different types of data so you can clearly understand their differences.
You now know that TTPs are the most crucial elements of attacker behavior. Therefore, in the next chapter, we will discuss many real-life examples to provide you with a rich source of practical information on human-operated ransomware attacks.


