On the 10th, the National Internet Emergency Center released a report stating that the web security testing situation will become increasingly severe this year. Probing, infiltration, and attacks on the interconnected information systems of key industries such as our country’s internet infrastructure, finance, securities, transportation, energy, customs, taxation, industry, and technology will gradually increase. With the rapid development of new network technologies and applications, and the trial and promotion of technologies such as three-network convergence, IPv6, cloud computing, and the Internet of Things, new security issues will continue to emerge. When I saw this news online, my heart tightened a bit. Security issues cannot be ignored, especially in today’s rapidly developing network technology. When it comes to network security and information leakage, no one can take it lightly. This is an issue that everyone must seriously face and consider.
Security covers a wide range, including network security, system security, database security, web security, program security, email security, etc. It can be said that security is an overall characteristic that is reflected in many aspects, like the barrel effect, where the shortest board determines the height of the water. Any overlooked weak link can become a potential danger and a breakthrough point for intruders. In this article, I will briefly discuss my thoughts on web security testing and hope everyone can share their views and learn together.
When it comes to web security, let’s first talk about web services and web architecture. Web services refer to services provided through the B/S architecture using the HTTP protocol, also known as web architecture. With the development of Web 2.0, there have been changes such as the separation of data and service processing, and the distribution of services and data, greatly enhancing its interactive performance. Some people also call it the B/S/D three-layer structure. On the web server, there are two types of data that need to be kept “clean” and require special protection. One is page files (.html, .xml, etc.), including dynamic program files (.php, .asp, .jsp, etc.), which are generally stored in specific directories on the web server or middleware server; the other is the backend database, such as Oracle, SQL Server, etc., where data needed for dynamic web page generation and business management data, and operational data are stored. Web services are relatively simple to develop, but the technical level of team members varies. Due to non-standard programming, weak security awareness, or simplified testing due to tight development schedules, application vulnerabilities are very common. The most common is SQL injection, which is a vulnerability that occurs during the application programming process.
Web architecture reference diagram:
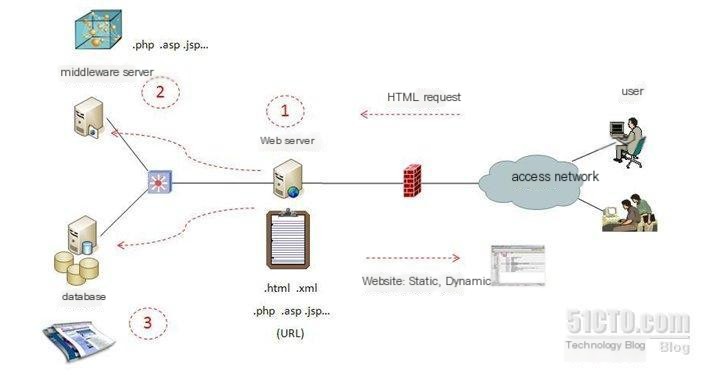
The rapid popularity of the internet is due to the simplicity of web deployment and development, and the widespread use of the internet has also led to the prosperity of web applications. With the rapid development of web applications, websites have become very important in daily life. However, many websites suffer from various attacks due to web application vulnerabilities. 75% of destructive activities occur at the application layer. For example, websites are hacked, SQL injections lead to page tampering, important data is modified or lost, websites are blacklisted, and web application hosts become controlled bots. Given the various exploitable vulnerabilities, relying solely on developers to avoid bugs is no longer sufficient. Therefore, we need specialized web security testing tools for detection and evaluation to provide effective defense.
Web security testing is mainly divided into two categories: white-box testing and black-box testing. White-box tools analyze application source code to find issues, while black-box tools report issues by analyzing the results of application operations. So how do we conduct web security testing in actual projects? To quickly and conveniently perform security testing, I used two powerful testing tools in my projects, which I will compare and introduce here.
First, IBM WEB APPSCAN (hereinafter referred to as AppScan), is an industry-leading web application security testing tool that provides scanning, reporting, and remediation recommendations. Of course, it is a black-box testing tool. It can detect all web application layer vulnerabilities, including SQL injection, cross-site scripting, frame phishing, web trojans, etc., and can automate the entire professional security assessment process, generating professional reports. The scanning process takes a long time, but the interface is user-friendly, and the problem information, consultation, and suggestions are quite comprehensive. Its use is relatively simple, so I won’t elaborate further.



Second, Acunetix Web Vulnerability Scanner (hereinafter referred to as WVS), is also an industry web vulnerability security scanning tool. It tests your website security through web crawler technology, detecting popular attacks such as cross-site scripting, SQL injection, etc. Of course, it is a black-box testing tool. The scanning speed is faster than AppScan, and it is more effective in scanning for cross-site and injection vulnerabilities. However, its report analysis is not as detailed and convenient as AppScan’s.



These two software tools are based on “crawler” technology for cyclic scanning. Crawler technology was first “invented” by search engines. Search websites release numerous small “crawlers” to cyclically scan websites around the world, collect new information on websites, and build databases for the world to search. This way, everyone can find whatever they want from search portals like Google and Baidu.


