After we have been engaged in security analysis with security devices like situational awareness for a long time, we tend to develop inertial thinking, thus forgetting how to conduct manual security analysis. Sometimes the advice given to the client does not solve the actual problem, so it becomes especially important to combine manual analysis and master skills to effectively solve real-world problems.
Situation Overview
On a certain day in 2021, just after having lunch, I opened the situational awareness platform, ready for a casual routine, when an alert caught my attention. So I quickly traced and investigated the relevant alert and, within an hour, generated a decent security analysis alert traceability report. I promptly contacted the relevant unit to act on the findings. Likewise, while I was leisurely having dinner, I was suddenly pulled into a WeChat group. The host administrator informed me that the virus scan couldn’t detect anything and needed my help. I was puzzled, thinking, “Is virus scanning that difficult? Do I have to handle it personally?” Later, I found out the situation wasn’t as simple as I imagined…
Security Analysis
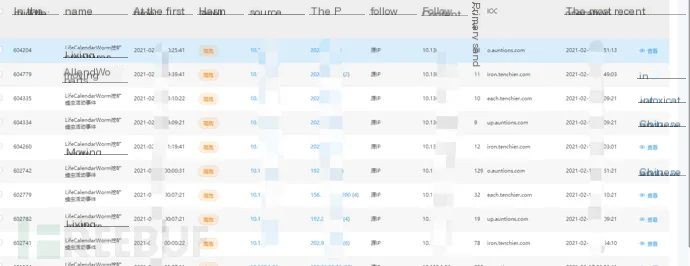
1. On a certain afternoon in 2021, the situation on the situational awareness platform was as follows: A certain organization’s host was suspected of being infected with the LifeCalendarWorm mining worm.
 />
/>
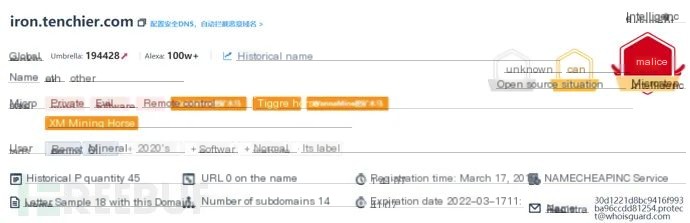
2. Traceback analysis revealed that the source IP: 10.x.x.x connected to a malicious domain every 10 minutes. The malicious domain was verified as an effective threat in the threat intelligence database. Here’s an example:
 />
/>
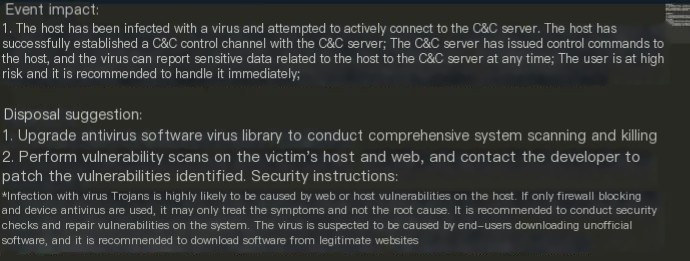
3. After analysis, it’s basically confirmed that the host is infected with a mining virus. A security incident traceability report was swiftly issued and sent to the corresponding unit for disposal. Security recommendations are as follows:
Manual Analysis
After issuing the analysis report, while eating dinner carefree, I was suddenly brought into a WeChat group. The engineer in charge of the host said the virus could not be removed.
Me: It can be removed.
Him: It can’t be removed.
Me: It can be removed.
Him: It can’t be removed.
Me: Try a different antivirus software, use the enterprise version.
Him: Tried three different ones.
Me: ……
At this moment, a metaphorical herd of wild thoughts ran through my mind, thinking, “Are you questioning my two and a half years of expertise?” I’ll show you onsite how it’s done, moving from basic to advanced virus removal.
1. Check CPU and memory operation status. CPU and memory operations are normal, and no process is taking up a lot of CPU:
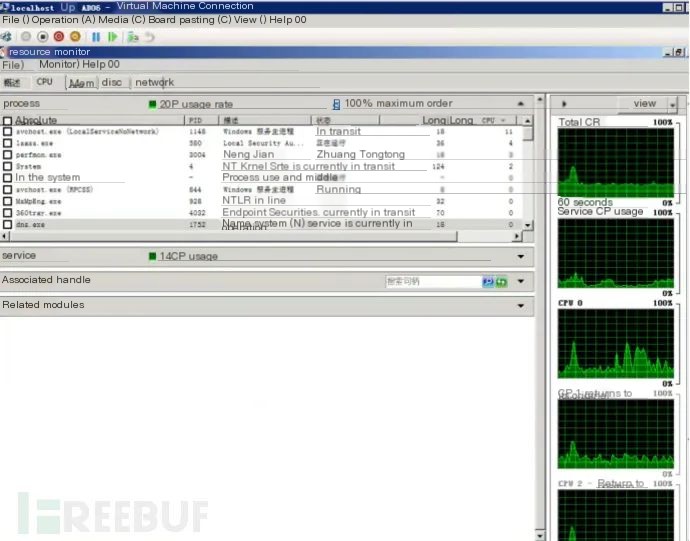
2. Memory usage is normal
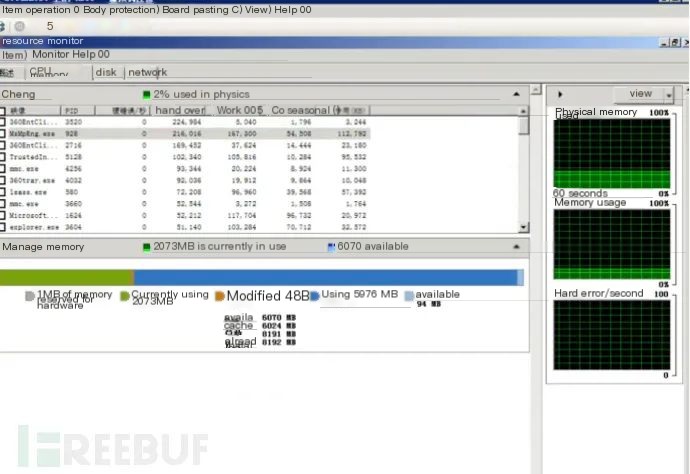
3. Use netstat -ano to check the machine’s external connection status, no connection to malicious IPs found:

4. Check user status in win+r by entering msc, the machine is found to be a domain controller
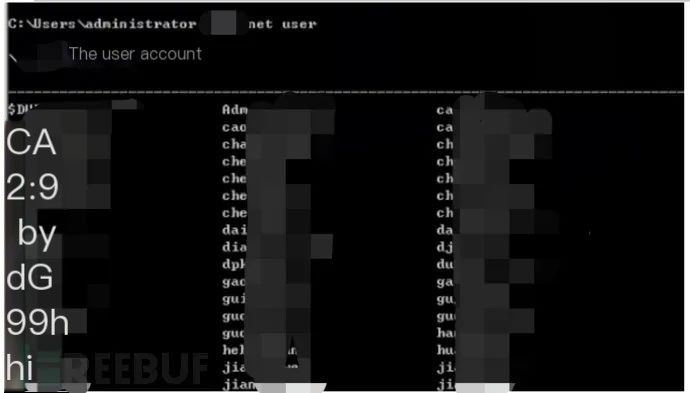
5. Use net user to check user status, finding multiple users, and this is normal for a domain controller
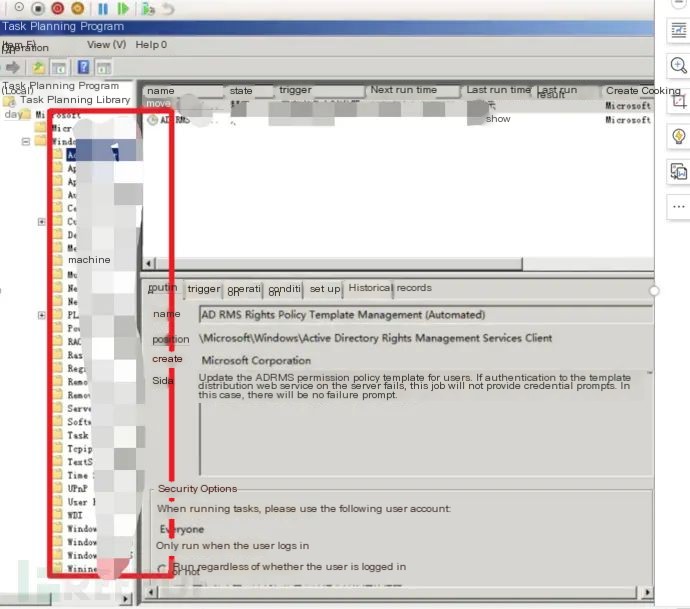
6. Check scheduled tasks with the administrator and found no abnormal scheduled tasks
7. In Task Manager’s network connection, dns.exe process reported the IP by the situational awareness platform
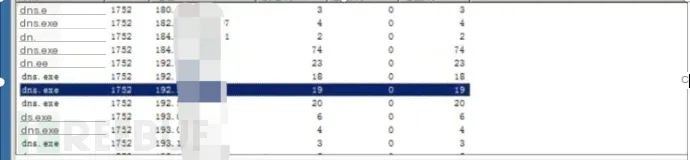
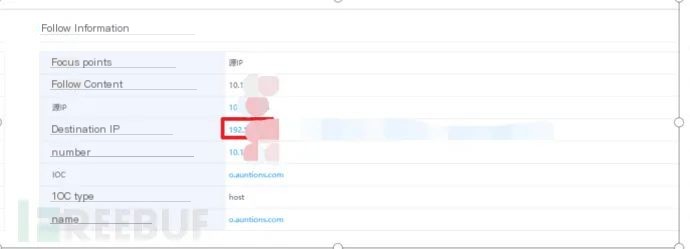
Preliminary Analysis Conclusion:
It’s not that the host is infected with a virus or trojan. The host is suspected to be a domain controller containing DNS services. Other sub-hosts within the domain use this host for DNS resolution, causing the situational awareness platform to alert the source IP as this host, but the actual infected machine is a sub-host within the domain.
Trace the Victim
It’s a big surprise that the alert platform was misleading me, a 22-year-old veteran. Since the probe was deployed at the core switch position, it did not track down the actual victim machine. No worries, since the problem is identified, we’ll let the administrators handle virus removal on the lower machines. But at this point, the client requested that the actual infected machine be traced, and I thought to myself, “Have I used up my flash of inspiration?” Faced with sudden difficulty, I almost typed up a resignation letter in Word. But then I remembered the girlfriend waiting for me to take her out for dinner with the salary, and I shrank back. ‘Worker spirit, worker soul, workers are super, let’s do it.’
1. Packet capture tool Wireshark: To analyze network sessions, Wireshark must be installed on this host. Surprisingly, the machine froze during the WinPcap installation to a complete standstill. This is a business-critical host, and the engineer beside me saw it.
Engineer beside me: “Oh no, G worker, prepare for unemployment.”
Me: “……”
2. Contact the host administrator for a reboot. Luckily no issues emerged.
3. Download the portable version of Wireshark and capture packets according to the pattern of the virus’s external domain connection timeframe, identifying the real infected host
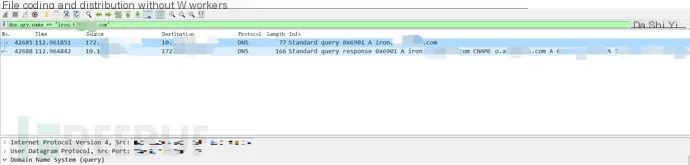
4. Inform the host administrator of the victim’s IP for virus removal. Incident resolved!!!
Conclusion
This year, we’ve been too reliant on security device alerts for analysis work, overlooking traditional skills. In the future, more manual handling and perfecting Wireshark skills should be done. Many new insights and skills were discovered during this incident handling. Thanks to all-powerful search engines, more manual analysis should be practiced later to refine intuition. Also, for business-critical machines, if they are virtual machines, it’s best to ask the administrator to take snapshots before our operations; for physical hosts, have the necessary software installed and avoid unauthorized operation!


