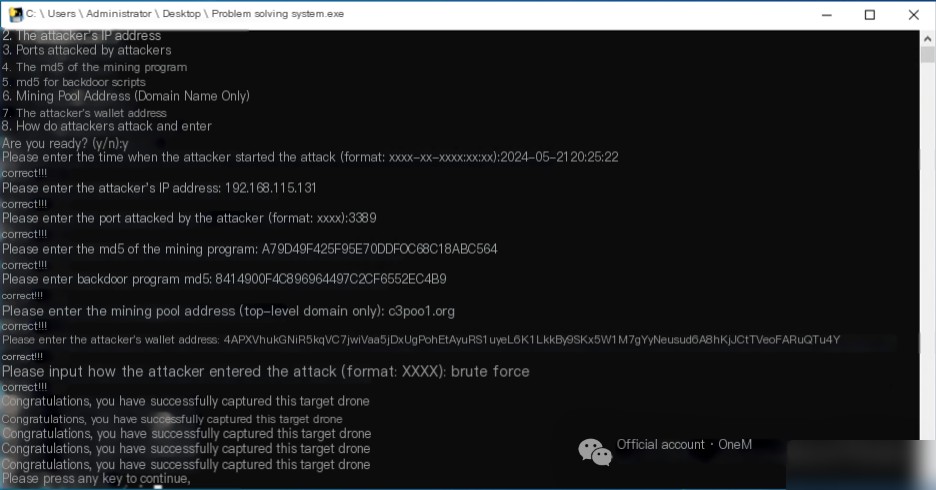
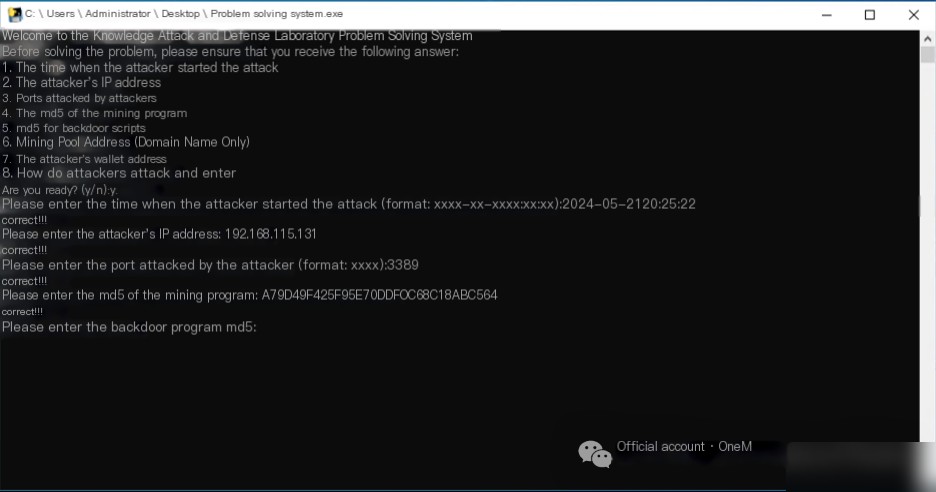
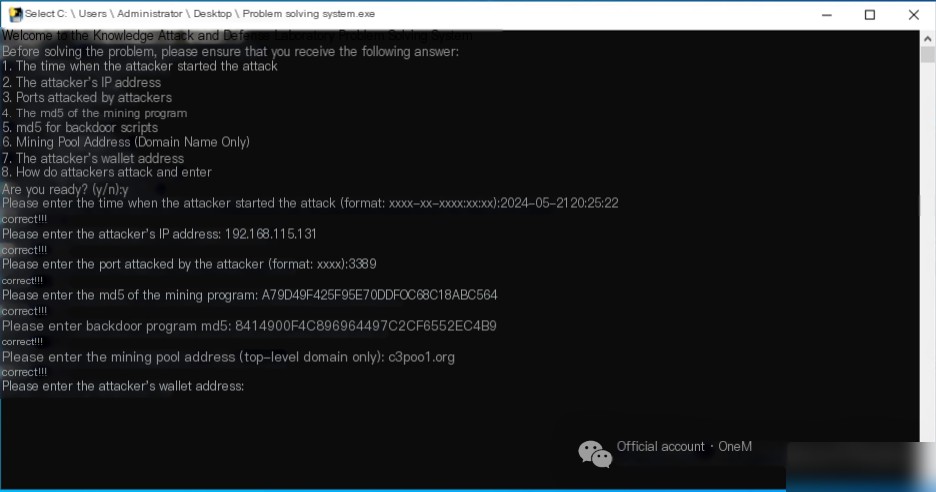
I. The Time the Attacker Started the Attack
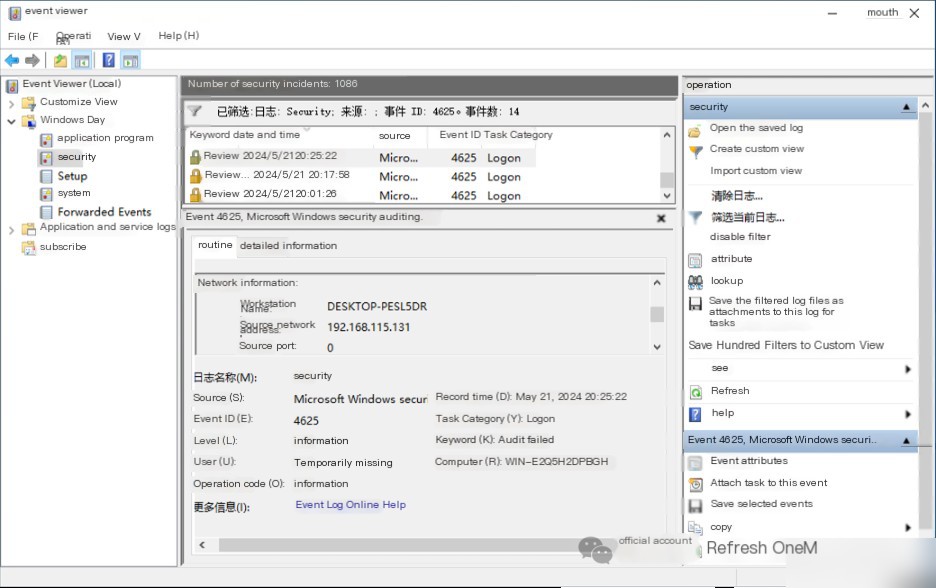
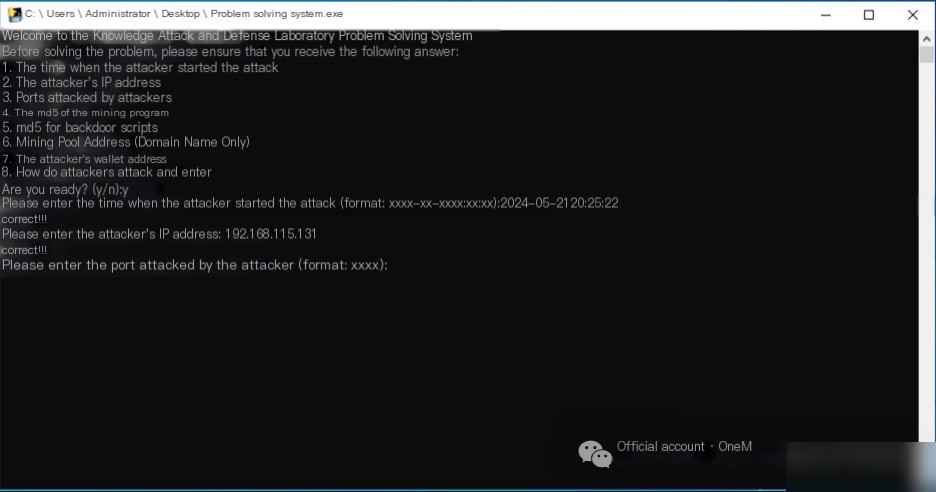
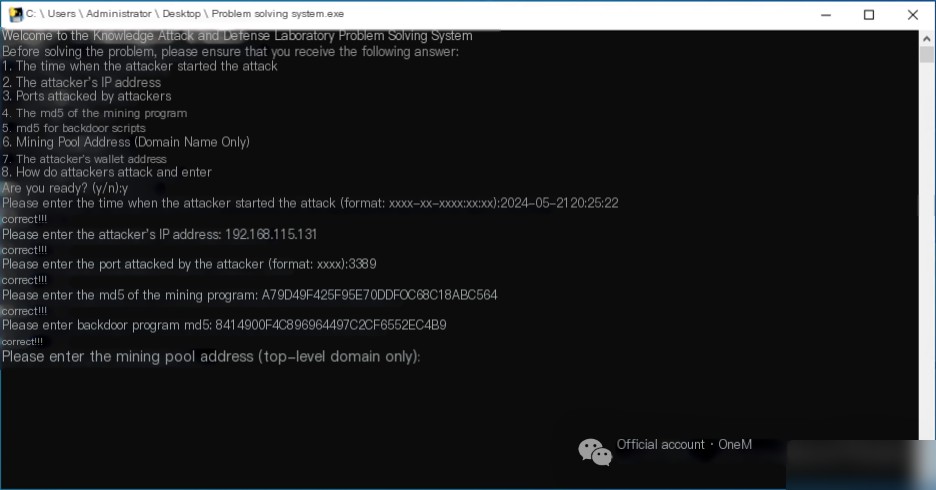
The server has no web service deployed, and it is initially suspected that the attacker infiltrated through RDP, SMB, or other methods. To investigate, use the command eventvwr.msc to open the Event Viewer. Navigate to Windows Logs->Security, and click on Filter Current Log to filter for Event ID 4625, which indicates login failures. The logs reveal that as early as 2024/5/21 20:25:22, the IP address 192.168.115.131 attempted to brute-force weak RDP passwords, highlighting concerns about RDP security.
II. The Attacker’s IP Address
In the first question, the attacker’s IP address was found: 192.168.115.131.
III. The Port Attacked by the Intruder
In the first question, it was found that the attacker targeted the RDP service on port 3389.
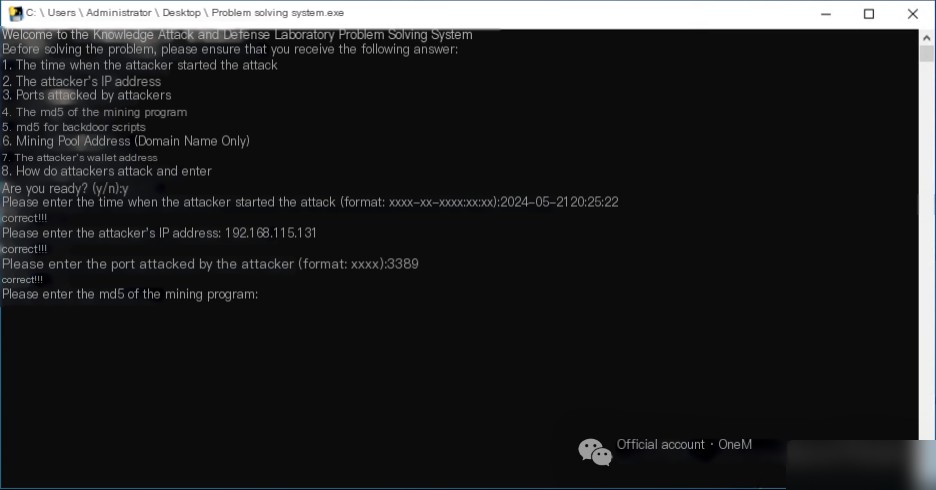
IV. MD5 of the Mining Program
Investigating the backdoor, use the command msinfo32 to open System Information. In Software Environment->Services, a suspicious service: c3pool_miner is seen. The corresponding program is: C:\Users\Administrator\c3pool\nssm.exe.
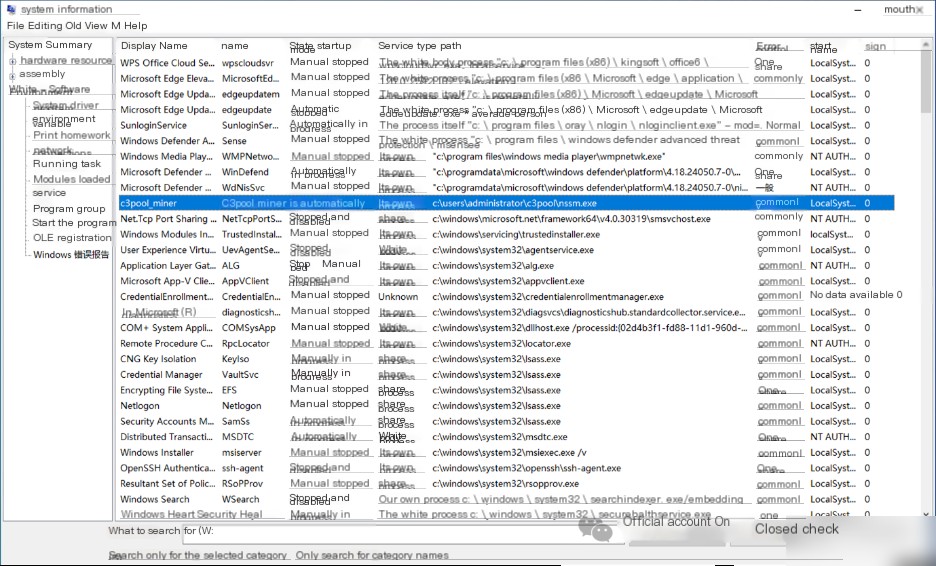
Investigating processes, two suspicious processes, nssm.exe and xmrig.exe, were found, with xmrig being the infamous Monero cryptocurrency miner.
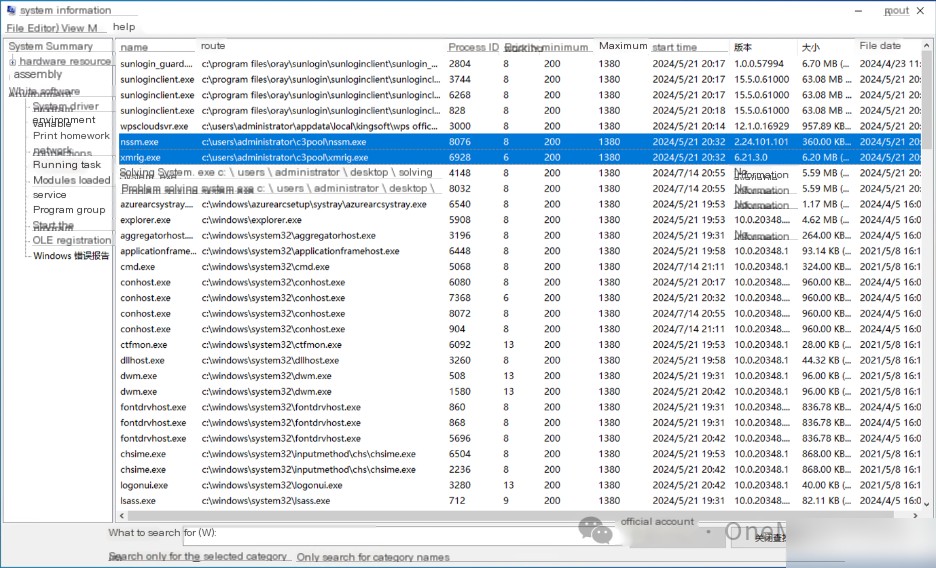
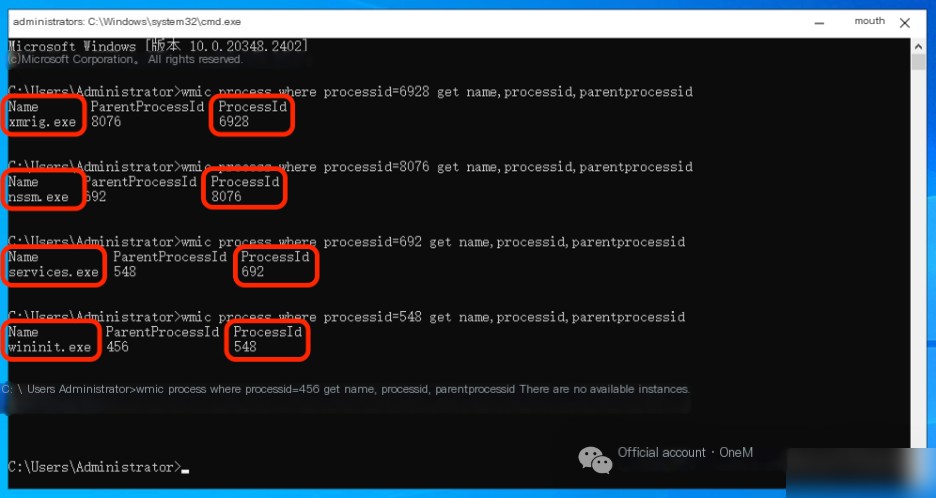
Use wmic process where processid=6928 get name,processid,parentprocessid and other commands to continually investigate the parent process of the mining program, revealing:
1. Initially, the Windows system startup program wininit.exe with PID 548 created the service program services.exe with PID 692;
2. Then, the service program services.exe created the service management software nssm.exe with PID 8076;
3. Finally, the service management software nssm.exe created the mining program xmrig.exe with PID 6928.
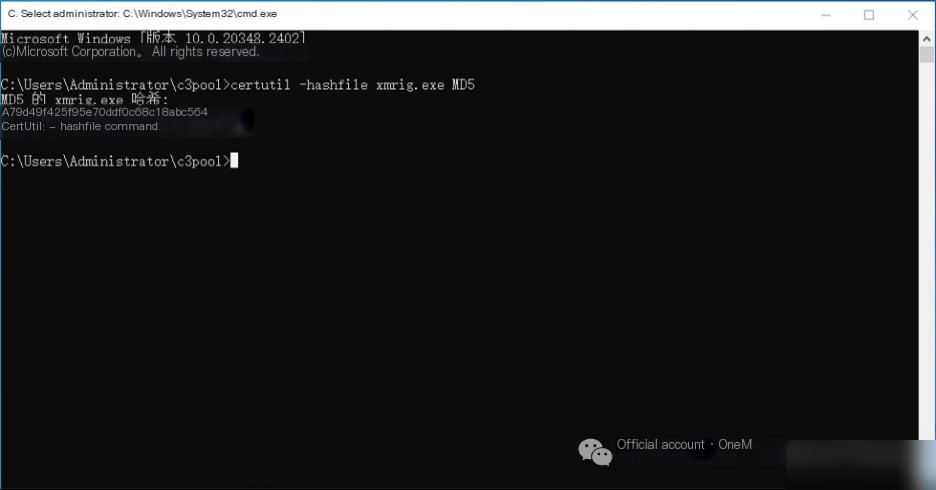
Using the command certutil -hashfile xmrig.exe MD5, calculate the MD5 value of the mining program, which is A79D49F425F95E70DDF0C68C18ABC564.
V. MD5 of the Backdoor Script
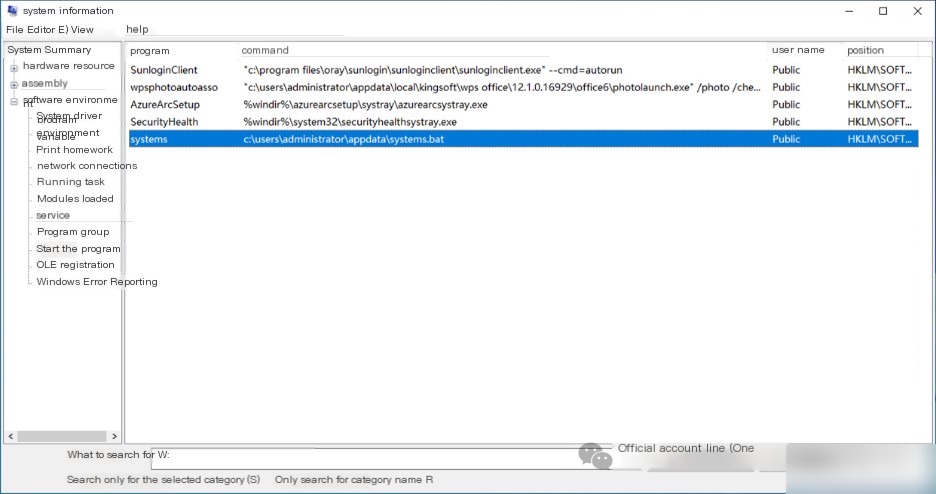
Use the command msinfo32 to enter System Information. In Software Environment->Startup Programs, a suspicious startup program: systems, is found to execute a script: C:\Users\Administrator\AppData\systems.bat.
Use the command taskschd.msc to enter Task Scheduler. In Task Scheduler Library, a suspicious scheduled task systemTesst is found to execute a script: C:\Users\Administrator\AppData\systems.bat.
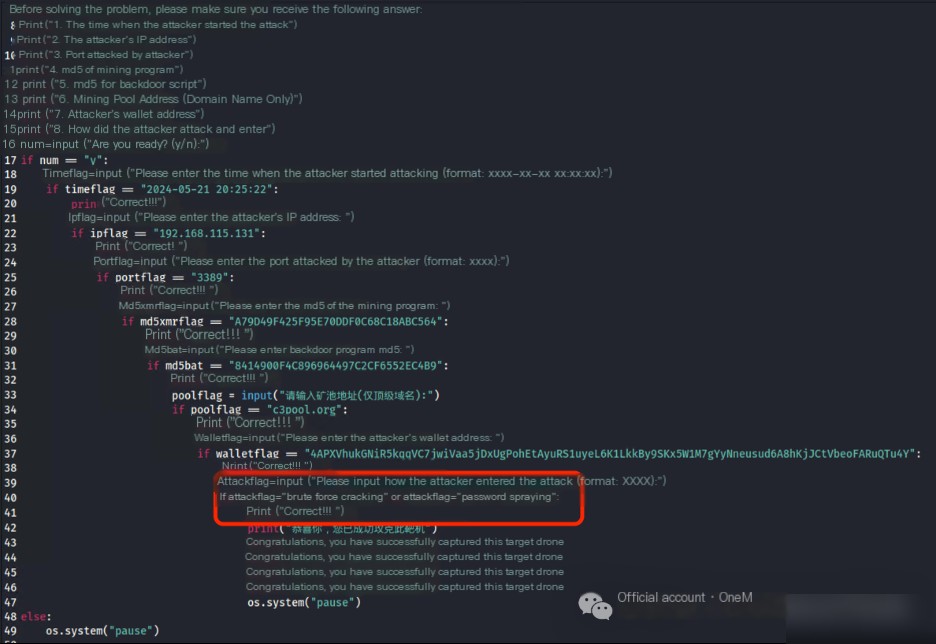
Reviewing the C:\Users\Administrator\AppData\systems.bat script, it is found to be a backdoor script left by the attacker, which downloads and executes a mining program deployment script.
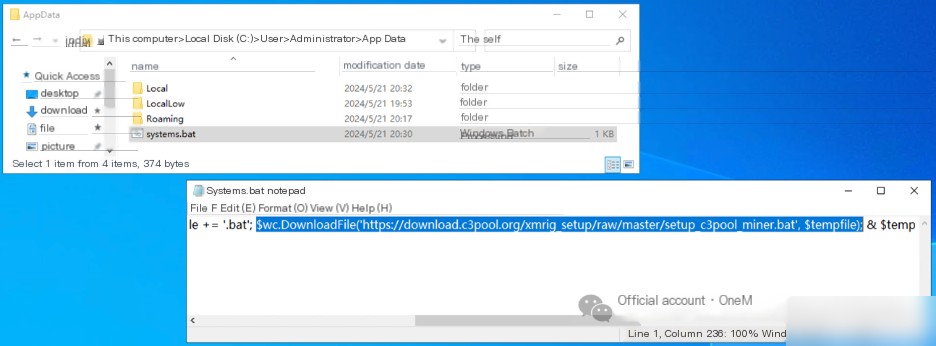
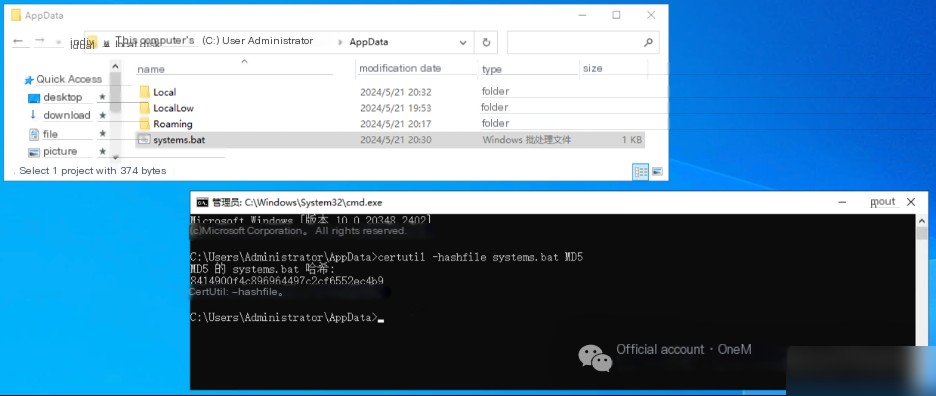
Using the command certutil -hashfile systems.bat MD5, calculate the MD5 value of the backdoor script, resulting in: 8414900F4C896964497C2CF6552EC4B9.
VI. Mining Pool Address
Online investigation of the xmrig mining program’s configuration methods suggests that the config.json file’s url parameter is the mining pool address.
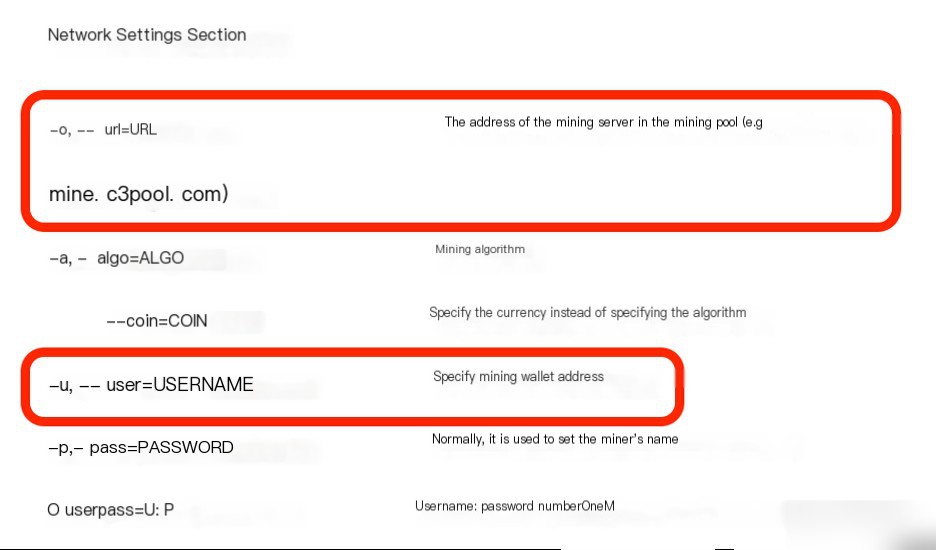
Reviewing the config.json file’s url parameter acquires the mining pool address: c3pool.org.
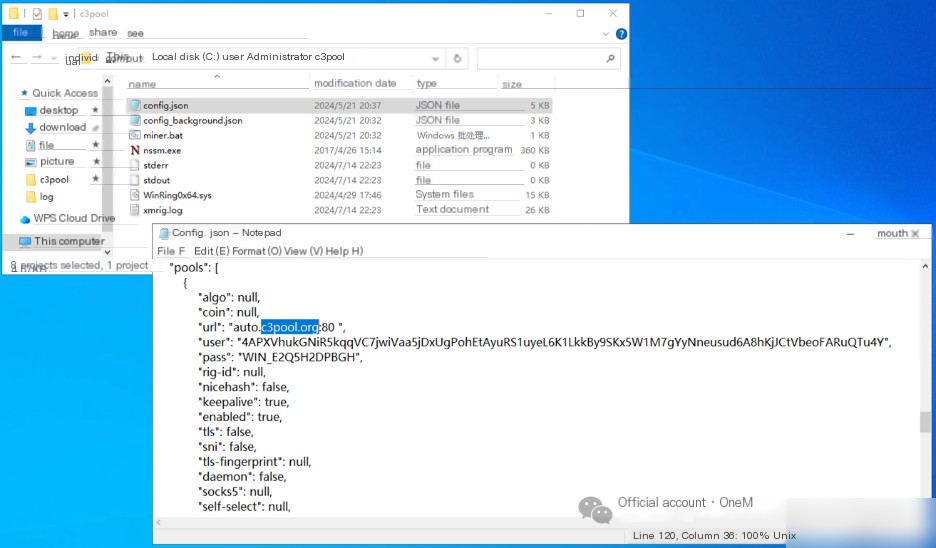
VII. Wallet Address
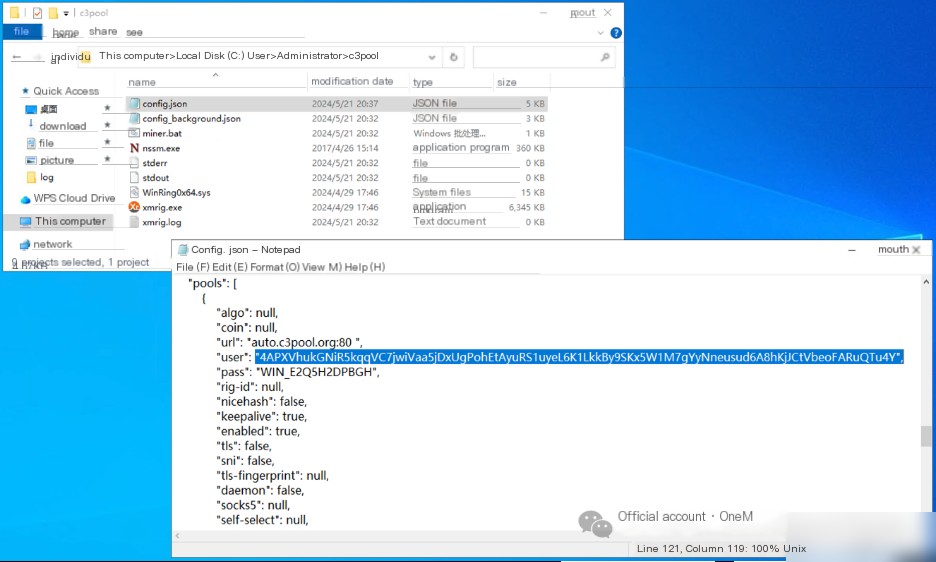
Online research of the xmrig mining program’s configuration methods indicates that the config.json file’s user parameter is the wallet address for xmrig.

Checking the config.json file’s user parameter obtains the wallet address: 4APXVhukGNiR5kqqVC7jwiVaa5jDxUgPohEtAyuRS1uyeL6K1LkkBy9SKx5W1M7gYyNneusud6A8hKjJCtVbeoFARuQTu4Y.
VIII. How the Attacker Breached the Server
From the first question, we already know that the server was first brute-forced through an RDP weak password by IP 192.168.115.131 on 2024/5/21 20:25:22, indicating that the attacker gained access through weak passwords or password brute-force attacks.

However, due to the vast and profound nature of Chinese, capturing the author’s intended answer in fill-in-the-blank questions is challenging. By unpacking and decompiling the “solution system.exe” and reviewing the source code, it was revealed that the author’s intended answer is: brute force or password spraying.