Why Is Security Traffic Analysis So Important?
The continuous increase in network attacks requires NTA (Network Traffic Analysis) to focus on security aspects that is security traffic analysis, in addition to traditional monitoring (i.e. latency monitoring, service availability…).
Especially the new challenges include:
- Encrypted traffic analysis
- Detection of vulnerable protocols and ciphers
- Full visibility, including potentially problematic IoT devices (such as tag readers)
- Real-time threat and suspicious incident recognition
Network Security Classification
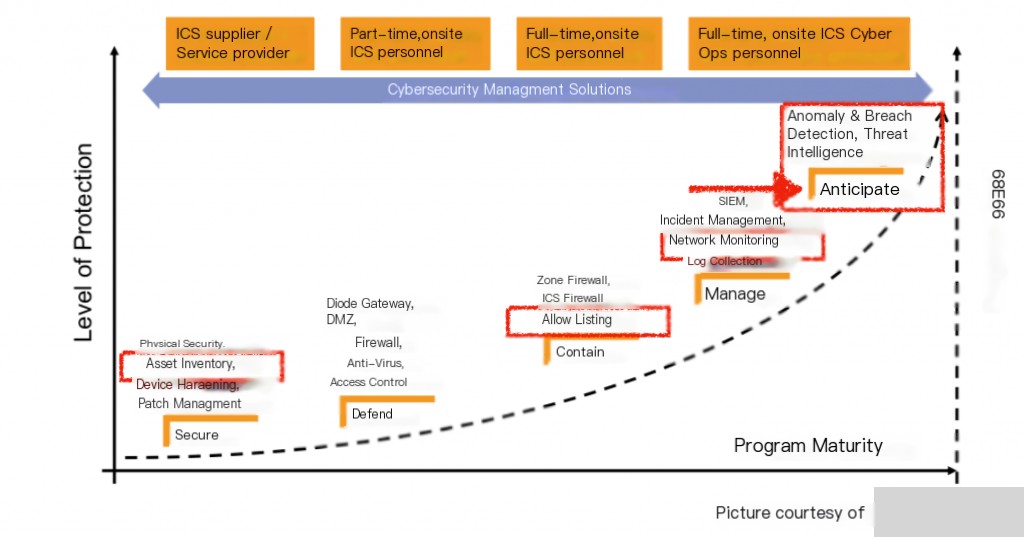
Network Security Monitoring: Requirements
- Distributed monitoring platform
- Network edge traffic monitoring + centralized analysis
- Deep network traffic analysis, detecting encrypted traffic (increasingly popular).
- Interpreting traffic monitoring data to create alerts from raw signals and triggering actionable insights (e.g., mitigating identified issues)
- Exporting monitoring information in an open format to multiple consumers/users
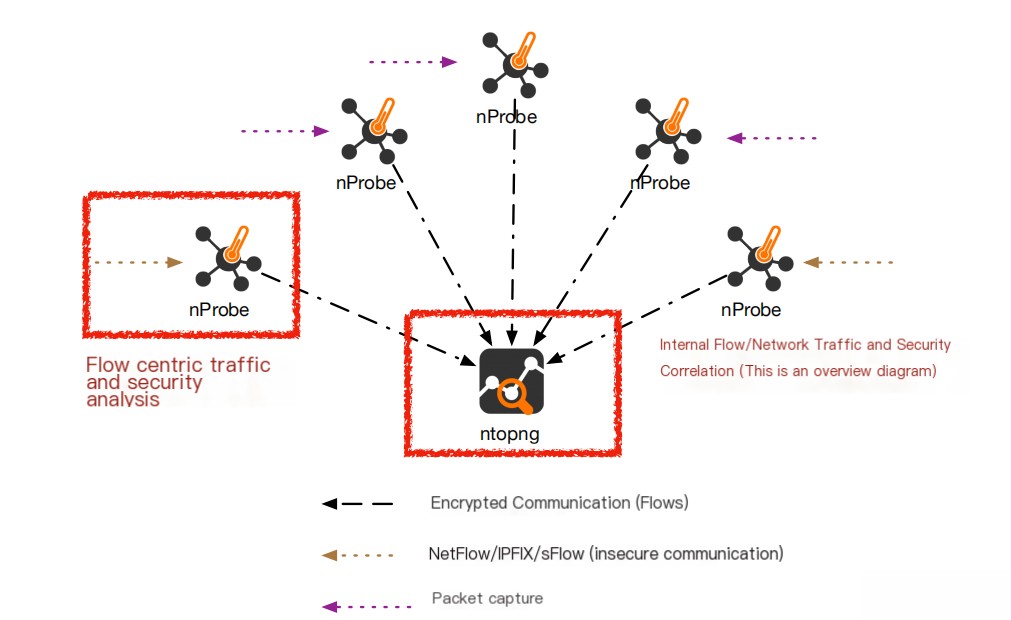
Typical Deployment: Traffic Processing
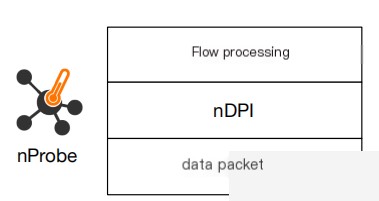
nDPI is an open-source DPI toolkit, upon which nProbe can compute flow statistics, including:
- Decoding initial flow packets of detected application protocols (like Google Maps)
- Analyzing encrypted traffic to detect issues with hidden but undetectable payload content.
- Extracting metadata from selected protocols (such as DNS, HTTP, TLS…) and matching with known algorithms to detect specific threats (like DGA hosts, domain generation algorithms).
nDPI Identifies Traffic Risks:
- XSS (Cross-Site Scripting)
- SQL Injection
- Arbitrary Code Injection/Execution
- Binary/.exe Application Transfer (e.g., in HTTP) known protocols on non-standard ports
- TLS Self-Signed Certificate
- TLS Outdated Version
- TLS Weak Cipher
- TLS Certificate Expiry
- TLS Certificate Mismatch
- HTTP Suspicious User-Agent
- HTTP Connection with Numerical IP Host
- HTTP Suspicious URL
- HTTP Suspicious Protocol Headers
- TLS Connection without HTTPS (e.g., VPN over TLS)
- Suspicious DGA Domain Connection
- Malformed Packets
- SSH/SMB Outdated Protocol/Application Version
- TLS Suspicious ESNI Usage
- Usage of Unsecure Protocols
ntopng Traffic Aggregation
- nProbe is a flow-oriented probe for monitoring edge traffic, while ntopng is a data collector for correlating signals from distributed probes and:
- Correlating intra-flow at the host, AS, and network interface level to uncover higher-level threats.
- Providing actionable insights that can react to detected issues.
- Network-based reporting and exporting to external systems.
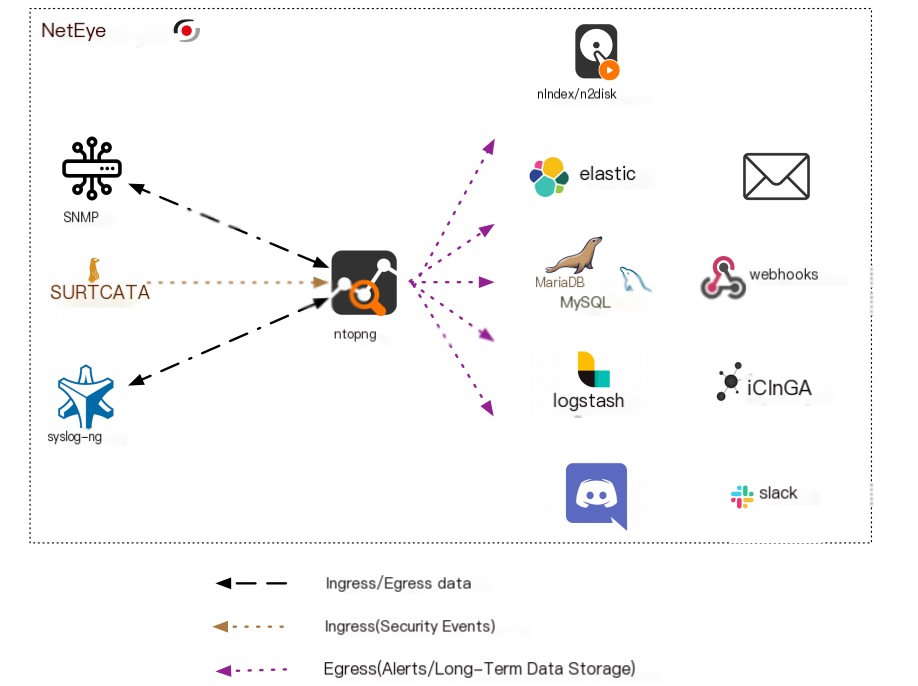
Use Cases
ETA Encrypted Traffic Analysis
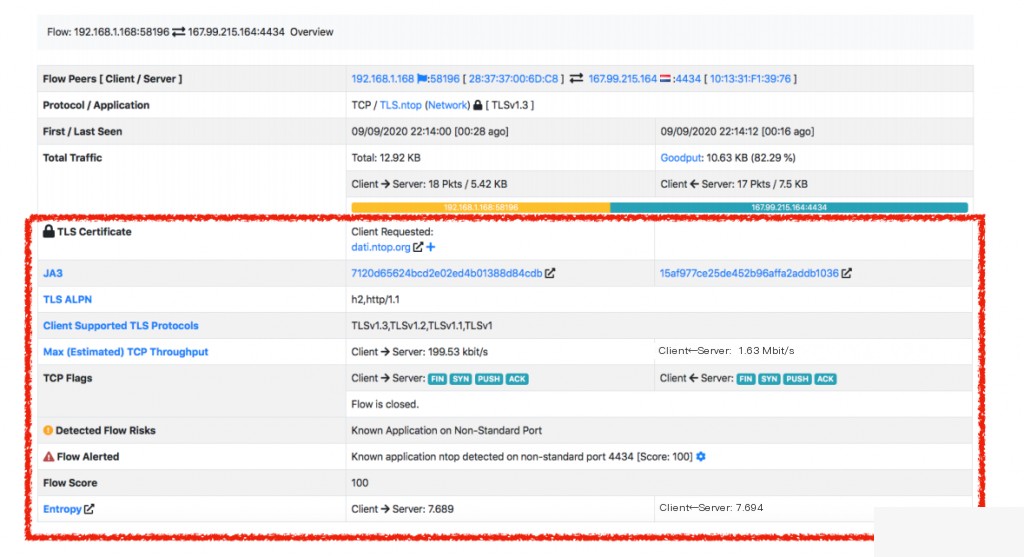
Threat Detection Through User Scripts
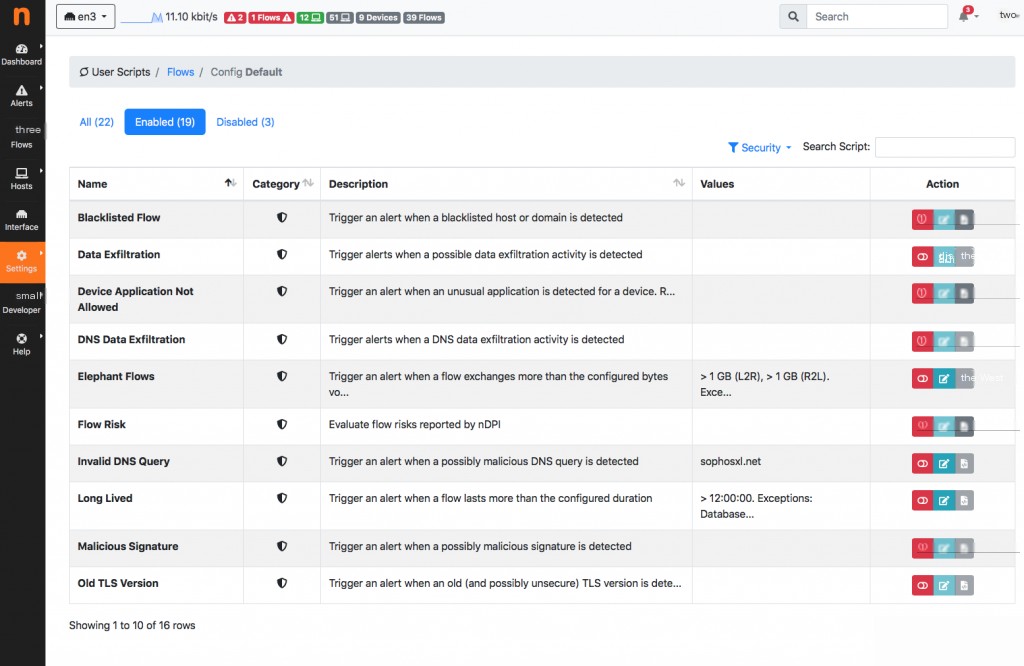
Searching for Needle Traffic in Noise Traffic
Low-bandwidth periodic connections may conceal abuses (e.g., periodic tasks), botnet command and control communications, unauthorized surveillance.
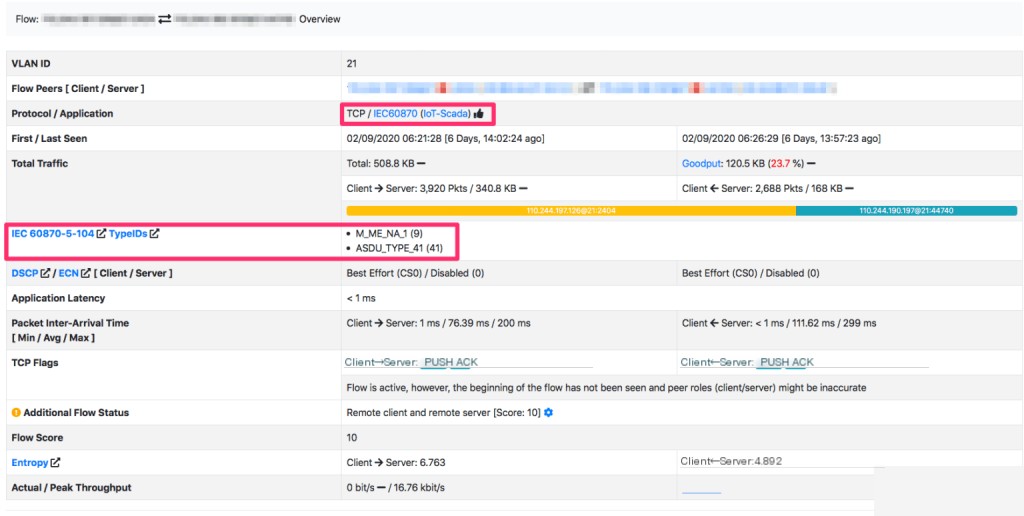
Industrial IoT/Scada Monitoring
- nDPI supports several common IoT/Scada protocols including modbus, DNP3, and IEC 60870.
- IEC 60870 is crucial because it can be used to detect issues such as:
- Unknown telemetry addresses
- Connection loss and recovery
- Loss of data from remote systems
- ntopng has persistent monitoring capabilities for IEC60870, capable of detecting industrial anomalies in addition to traditional traffic monitoring.
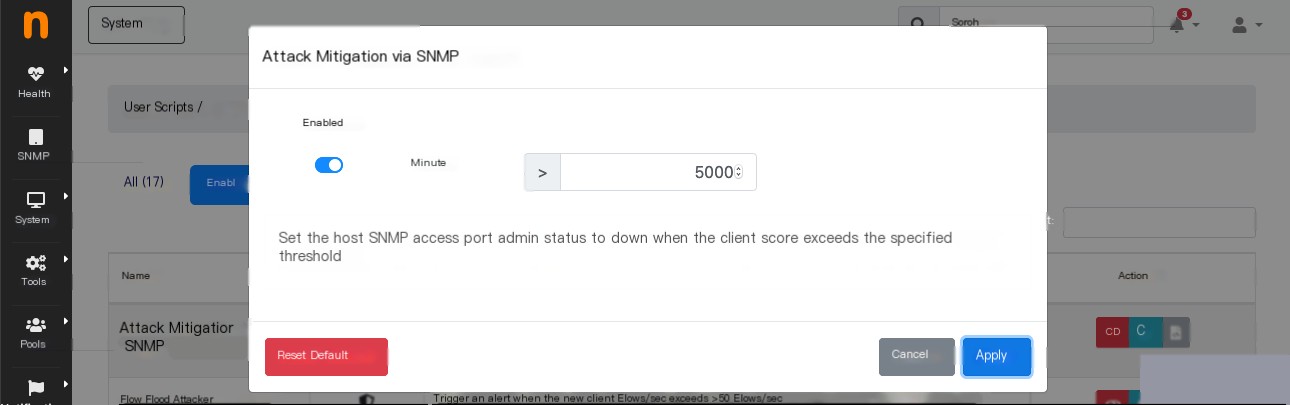
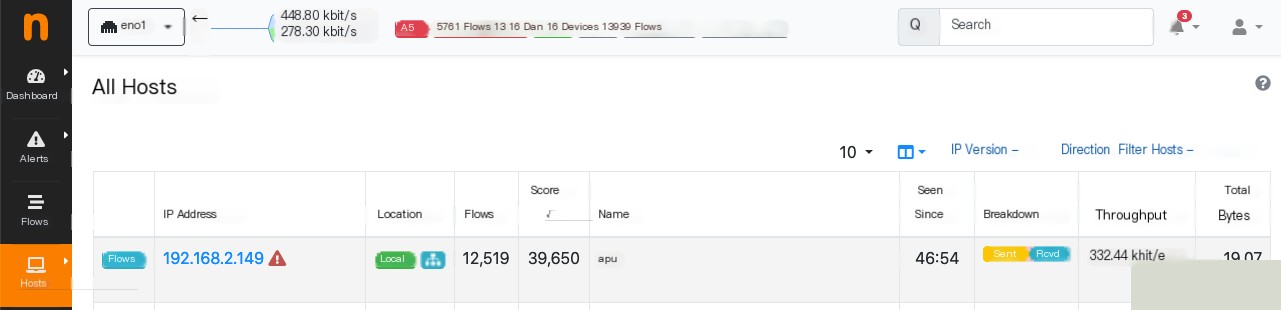
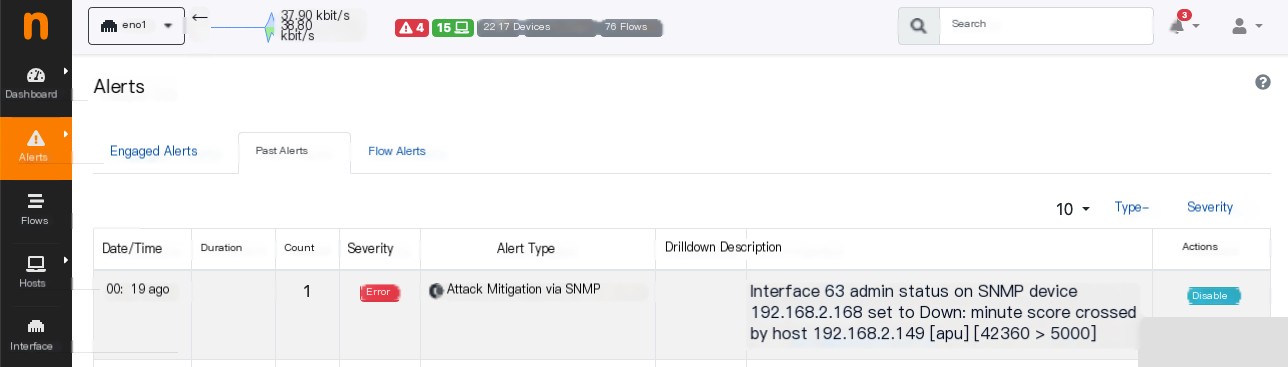
Actionable Insights: Attack Mitigation via SNMP
- Score is a metric used to detect issues with hosts, AS, networks, etc.
- SNMP can be used for polling but also for modifying device configurations.