In the latest version of ntopng, to facilitate understanding of network and security issues, alerts have been significantly enriched with metadata. In this post, we focus on the “attacker” and “victim” metadata used to enhance flow alerts and tag hosts. Specifically, when the client or server of a flow is likely the initiator of one or more security issues, it is marked as an “attacker.” Similarly, when clients or servers are deemed to be under attack, they are labeled as “victims.” For use cases not security-oriented (such as severe packet loss), affected hosts are still highlighted with high scores but are not tagged as attackers/victims since these terms are reserved for the security domain.
For example:
- In DNS requests to suspicious DGA domains, the client is considered the “attacker” as it initiates these potentially malicious requests.
- When remote code execution (RCE), cross-site scripting (XSS), and SQL injection attempts are detected, the client is the “attacker” while the server is the “victim,” as it is being probed/attacked by the client trying to exploit its vulnerabilities.
- When a binary/.exe application is downloaded via HTTP masquerading as a benign file like a PNG image, the client is considered compromised, and the server is considered malicious due to it being the source of the suspicious file, thus both are labeled as “attackers.”
- For a DNS data exfiltration alert, both the client and server are labeled as “attackers” since data exfiltration requires both a client and server running exfiltration software, like iodine.
Example in This Article: ntopng
In the alerts covered in this article, we analyze a Hancitor infection (provided by Malware-Traffic-Analysis pcap) to demonstrate the efficacy of ntopng and its new “attacker” and “victim” metadata in detecting such security issues.
The Hancitor infection essentially is a multi-stage event chain leading to the target host downloading a malicious software file, effectively transforming it into a malicious host under the attacker’s control.
Let’s see what happens when we analyze a pcap with a Hancitor infection using ntopng. You can start ntopng in the following way:
ntopng -i 2021-06-01-Hancitor-with-Cobalt-Stike-and-netping-tool.pcap -m "10.0.0.0/8"Alert Analysis
Initially, it is quite evident from the header bar that suspicious activities are underway as there are thousands of flows with errors and warnings. Note that the number of alerted flows can vary based on your configuration (see the sidebar menu on the left “Settings”-> “User Scripts”).
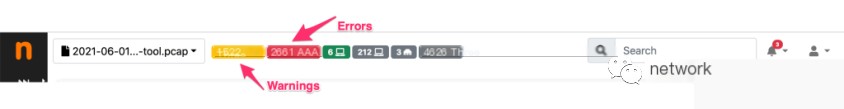
Clicking on the red “Error” tag takes us to the flow page, filtered for erroneous flows. By opening the “Status” drop-down menu, it’s clear that there are suspicious activities like several suspicious DGA domain requests and over 2000 suspicious file transfers.
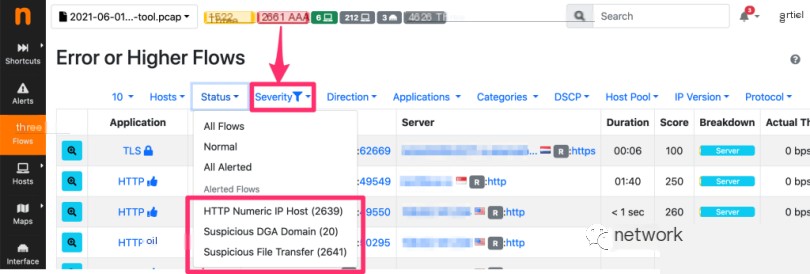
However, this page is insufficient to determine if an attack is occurring and the source of the trouble. This becomes even more apparent upon accessing the flow alert page. Before browsing the alerts, we set a filter to view only security-related alerts with “attackers.”
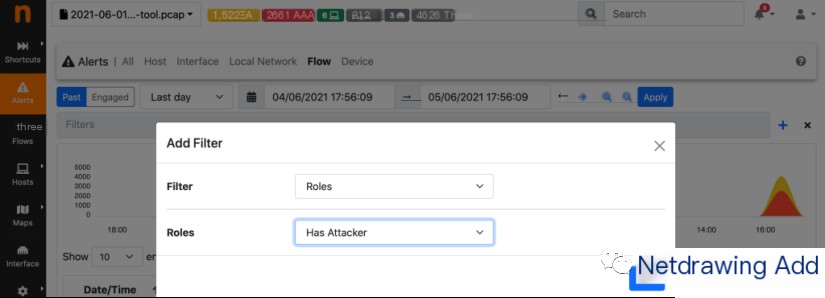
Equipped with this filter, ntopng only displays alerts linked to detected attackers. Indeed, suspicious DGA domain alerts begin to stand out. The “skull” symbol helps identify the “attacker,” in this case, the Windows client host infected by Hancitor.
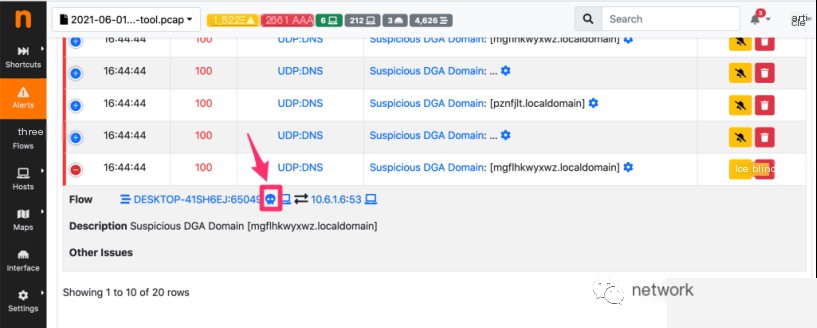
When we continue browsing the alerts with attackers, we also see thousands of suspicious file transfer alerts. For this type of alert, two skull symbols are shown. In fact, not only is the attacked Windows host marked as an “attacker,” but also the server distributing malicious files is tagged as an “attacker.”
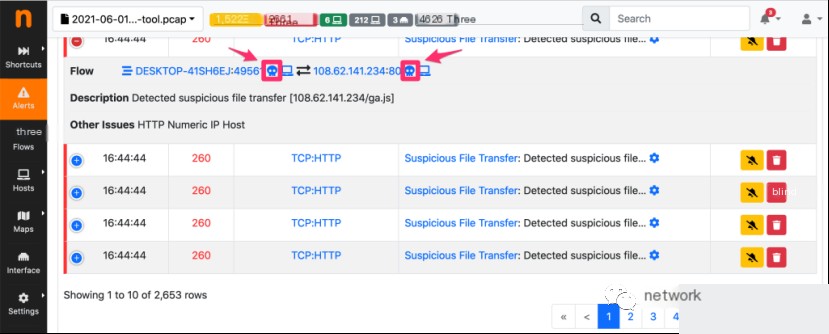
How to Verify?
But why is the seemingly harmless file transfer of ga.js considered suspicious? Because, in practice, these are not JavaScript files at all! Sometimes they’re just empty files, other times they’re binary files of unidentified content. Simply use Wireshark to extract these ga.js files to verify this and prove the effectiveness of ntopng in detecting these suspicious transfers occurring within the network. Merely by browsing these alerts can other suspicious files be uncovered. These include downloads of Ficker Stealer and Cobal Strike requests.
You can identify attackers/victims in the “Host Map” (sidebar menu on the left “Map”-> “Hosts”).
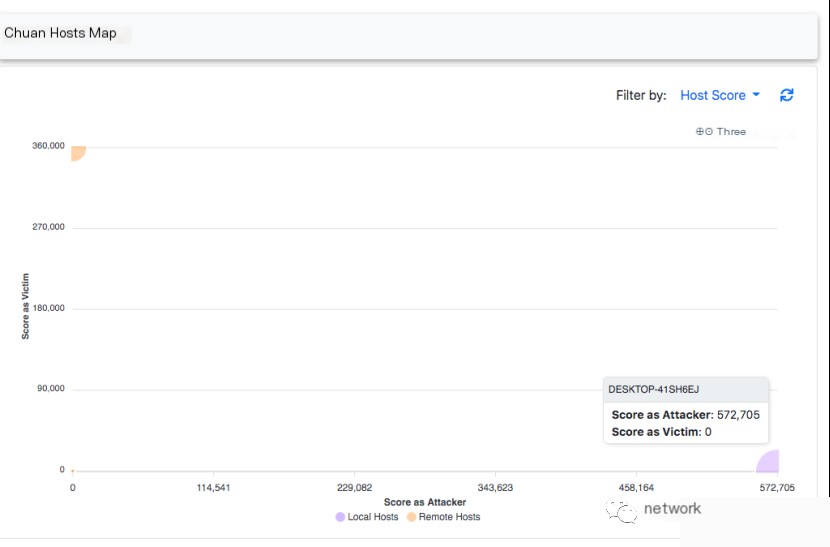
Because they are two outliers on the X/Y axis. Clicking the bubbles lets you jump directly to the host page to see what’s happening, as discussed in this article.
Value-added Features
Lastly, it’s worth mentioning that “attacker” and “victim” metadata can also be used for host alerts to discover hosts involved in suspicious activities such as SYN scans or high DNS or ICMP traffic. Besides the real-time scoring used as shown above, you can monitor scores over the long term to detect deviations from expected behavior. This is necessary for detecting “soft” behavior changes that won’t be caught by the scoring techniques illustrated above but are used to uncover attackers with more aggressive behavior.


