RITA (Real Intelligence Threat Analytics) is an open-source tool for cybersecurity analysis and threat detection. It collects, parses, and analyzes network traffic data, providing insights into network activities and allowing security professionals to detect and respond to security incidents. RITA offers real-time alerts and allows users to perform network forensics and incident response tasks.
The framework receives Zeek Logs in TSV format and currently supports the following main features:
- Beacon Detection: Searches for signs of beaconing behavior within and outside the network.
- DNS Tunneling Detection: Searches for signs of covert channels based on DNS.
- Blacklist Checking: Queries blacklists to search for suspicious domains and hosts.
- URL Length Analysis: Searches for excessively long URLs that indicate malware.
- Scan Detection: Searches for signs of port scanning in the network.
Installing Zeek with Real Intelligence Threat Analytics
Zeek: https://zeek.org/
Download Link: https://github.com/zeek/zeek/wiki/Binary-Packages
Zeek Documentation: https://docs.zeek.org/en/current/install.html
Zeek is an open-source network security monitoring framework that provides a comprehensive platform for performing network traffic analysis. It includes capturing and analyzing network traffic, identifying security threats, and generating reports. Network administrators and security professionals use Zeek to detect and respond to security incidents and analyze network traffic for performance and optimization.
For example, for the latest Zeek 6.0 LTS version on Ubuntu 22.04, the steps are as follows:
echo 'deb http://download.opensuse.org/repositories/security:/zeek/xUbuntu_22.04/ /' | sudo tee /etc/apt/sources.list.d/security:zeek.list curl -fsSL https://download.opensuse.org/repositories/security:zeek/xUbuntu_22.04/Release.key | gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/security_zeek.gpg > /dev/null sudo apt update sudo apt install zeek-6.0
RITA works with Zeek by importing Zeek logs and analyzing them. Therefore, the first step in processing the captured traffic is to convert it into Zeek logs.
After installation, the path to Zeek is not added to $PATH, and Zeek is located at:
/opt/zeek/bin/zeek -h
Generating Zeek Logs with Real Intelligence Threat Analytics
Install tshark and capture host traffic, then use Zeek to parse the pcap and generate logs.
apt install tshark -y tshark -i eth0 -w capture.pcap /opt/zeek/bin/zeek -r capture.pcap
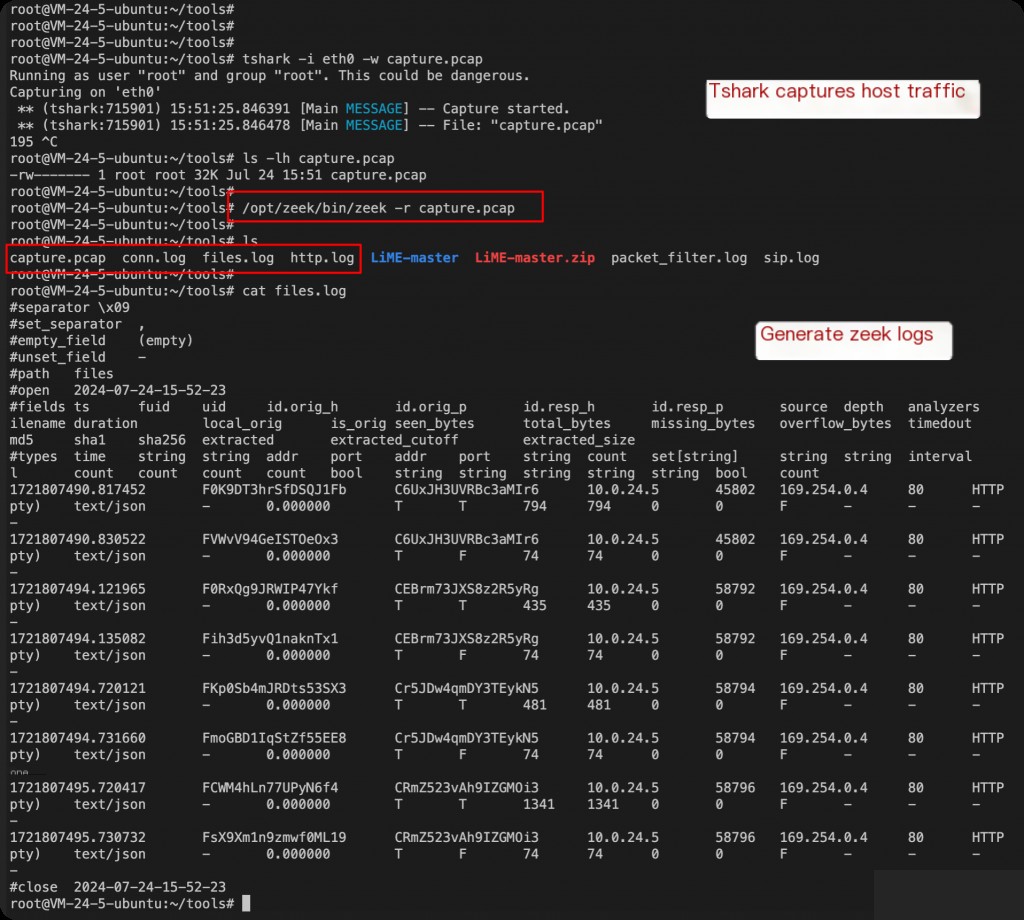
Installing RITA and Importing Zeek Logs
RITA: https://github.com/activecm/rita
RITA Download Link: https://github.com/activecm/rita/releases
wget https://github.com/activecm/rita/releases/download/v5.0.6/rita-v5.0.6.tar.gz tar xvf rita-v5.0.6.tar.gz ./rita-v5.0.6-installer/install_rita.sh 127.0.0.1
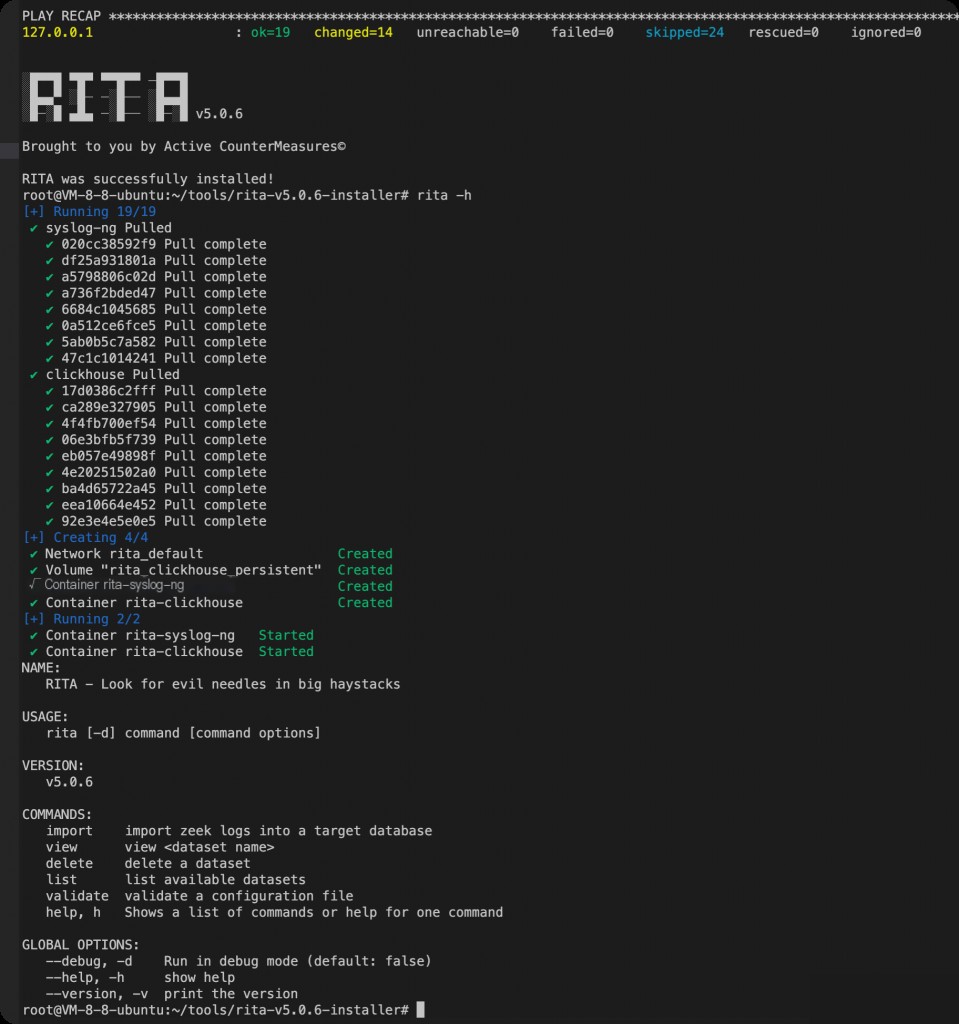
The installation script for RITA takes a while to complete as it installs many dependencies. The appearance of the logo above indicates that RITA has been successfully installed. Now, import the Zeek logs into RITA.
rita import --logs ./ -database mylogs --rebuild
rita view mylogs
Since there was no malicious traffic captured on the host earlier, RITA’s analysis does not show much content.
Hunting C2 Beacons
Use cs to create an HTTP communication beacon.exe and transfer it to our test Windows host.
On the Windows machine, start Wireshark to capture all traffic on the network interface.
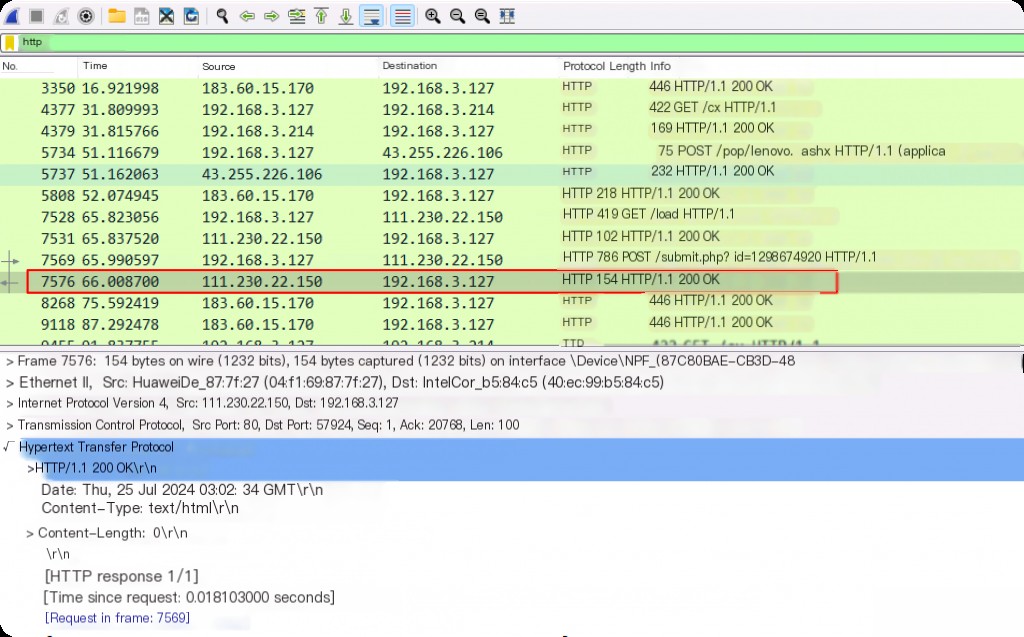
Then, use Zeek to parse the captured traffic into log files and import them into RITA for analysis.
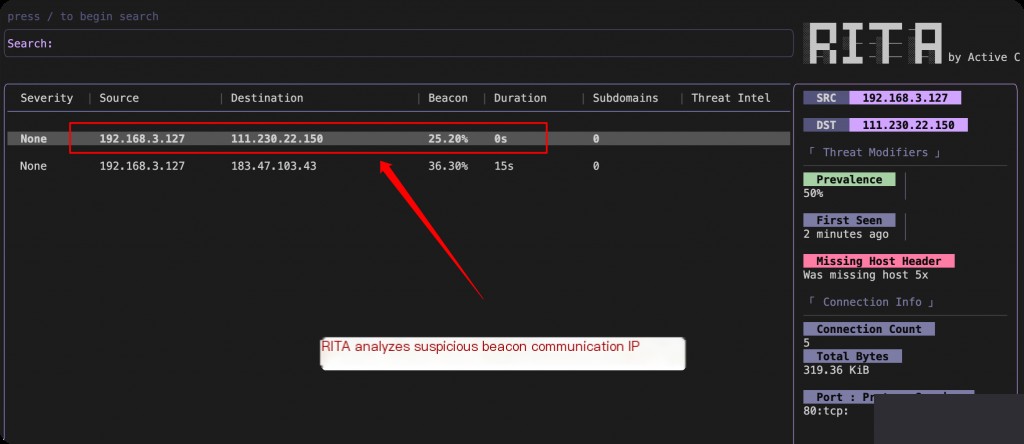
Hunting DNS Tunnels
DNS (Domain Name System) Command and Control (C2) is a technique used by malware authors and attackers to establish communication channels and control infected systems through DNS traffic. The Domain Name System is primarily used to translate human-readable domain names into IP addresses, but malicious actors can exploit this protocol for covert communication.
In a DNS C2 scenario, the malware-infected system communicates with a malicious DNS server controlled by the attacker. Instead of using traditional network protocols like HTTP or IRC for command and control, the malware uses DNS queries and responses to exchange information with the attacker’s server.
A brief overview of how DNS C2 works:
1. Infection: The target system is infected with malware that includes DNS C2 capabilities. This malware may be part of a larger attack, such as a botnet or an Advanced Persistent Threat (APT).
2. DNS Queries: The malware generates DNS queries to specific domains or subdomains controlled by the attacker. These queries may contain encoded information or actual commands.
3. Command and Control (C2) Server: The attacker sets up a malicious DNS server or compromises an existing DNS server. This server is responsible for handling incoming DNS queries from infected systems.
4. Responses: The attacker’s DNS server responds to the queries with information or commands for the malware. The responses may be encoded or encrypted to evade detection.
5. Execution: The malware on the infected system interprets the DNS responses and executes the specified commands. These commands may involve data exfiltration, downloading additional payloads, or performing other malicious activities.
DNS C2 Channels: Advantages for Adversaries
- Stealth: DNS traffic is ubiquitous, making it difficult for security tools to distinguish between legitimate and malicious DNS activities.
- Persistence: Since DNS is a fundamental part of internet communication, DNS C2 can maintain persistent communication even in environments where other communication channels are restricted.


