Network Security Anti-Penetration Solutions
Introduction
With the rapid development of the Internet, network security issues are becoming increasingly prominent. Penetration attacks, as a common means of cyber attacks, pose significant threats and losses to enterprises and individuals. Therefore, effectively preventing penetration attacks has become an important topic in the field of network security. This article will explore solutions and strategies for network security anti-penetration and provide corresponding code examples for reference.
Basic Principles of Penetration Attacks
Penetration attacks usually include the following stages:
- Information Gathering: Attackers collect information about the target system through various means.
- Scanning and Probing: Use scanning tools to detect vulnerabilities and weaknesses in the target system.
- Gaining Access: Exploit vulnerabilities or weaknesses to gain access to the target system.
- Privilege Escalation: Further attacks to elevate permissions and gain more control.
- Maintaining Access: Install backdoors and other means to ensure long-term access to the target system.
- Clearing Tracks: Delete logs and evidence to hide attack activities.
Anti-Penetration Solutions
1. Strengthening Network Perimeter Defense
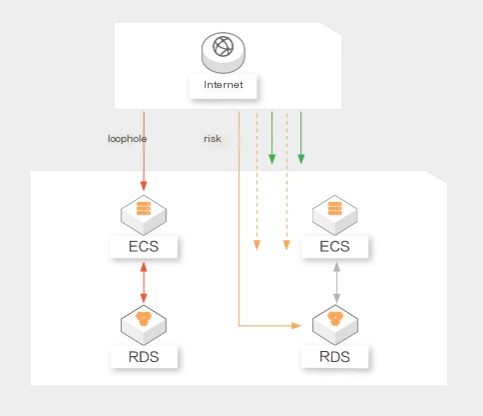 image-20240714191847502
image-20240714191847502
Firewall Configuration
A firewall is an important tool for protecting the network perimeter. By reasonably configuring firewall rules, illegal access can be effectively blocked.
from iptc import Chain, Rule, Table
def add_firewall_rule(src, dst, target='DROP'):
table = Table(Table.FILTER)
chain = Chain(table, 'INPUT')
rule = Rule()
rule.src = src
rule.dst = dst
rule.target = target
chain.insert_rule(rule)
# Block access from malicious IP
add_firewall_rule('192.168.1.100', '0.0.0.0/0')2. Vulnerability Management and Patch Updates
Regular vulnerability scanning and patch updates are important measures to prevent penetration attacks.
import subprocess
def scan_vulnerabilities():
result = subprocess.run(['nmap', '-sV', '192.168.1.1'], capture_output=True, text=True)
print(result.stdout)
# Perform vulnerability scanning
scan_vulnerabilities()
def update_system():
subprocess.run(['sudo', 'apt-get', 'update'])
subprocess.run(['sudo', 'apt-get', 'upgrade'])
# Update system patches
update_system()3. Authentication and Access Control
Mandatory use of multi-factor authentication (MFA) and strict access control policies can effectively prevent unauthorized access.
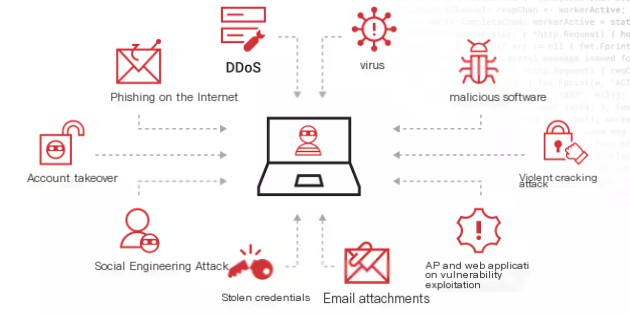 image-20240714191901975
image-20240714191901975
Configure MFA
import pyotp
def generate_mfa_secret():
return pyotp.random_base32()
def verify_mfa_code(secret, code):
totp = pyotp.TOTP(secret)
return totp.verify(code)
# Generate MFA secret
secret = generate_mfa_secret()
print(f"MFA Secret: {secret}")
# Verify MFA code
code = input("Enter MFA code: ")
if verify_mfa_code(secret, code):
print("MFA code is valid.")
else:
print("Invalid MFA code.")4. Log Auditing and Monitoring
Through log auditing and real-time monitoring, abnormal behaviors can be detected and responded to promptly.
Configure Log Auditing
import logging
logging.basicConfig(filename='/var/log/security.log', level=logging.INFO)
def log_security_event(event):
logging.info(f"Security event: {event}")
# Record security event
log_security_event('Suspicious activity detected from IP 192.168.1.100')5. Security Training and Awareness Development
Conduct regular security training and increase staff security awareness to prevent social engineering attacks.
6. Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are important tools for monitoring network and system activities and detecting and blocking malicious behaviors. IDS is mainly used to detect and record potential intrusion activities, while IPS can actively take measures to block attacks upon detection.
Snort IDS Configuration Example
Snort is an open-source network intrusion detection system widely used in network security protection.
- Install Snort
sudo apt-get update
sudo apt-get install snort- Configure Snort rules file (/etc/snort/snort.conf)
Add detection rules, for example:
alert tcp any any -> 192.168.1.0/24 80 (msg:"HTTP Traffic Detected"; sid:1000001; rev:1;)- Start Snort
sudo snort -A console -q -c /etc/snort/snort.conf -i eth0Suricata IPS Configuration Example
Suricata is another commonly used open-source intrusion detection and prevention system, known for its high performance and usability.
- Install Suricata
sudo apt-get update
sudo apt-get install suricata- Configure Suricata rules file (/etc/suricata/suricata.yaml)
- Start Suricata
sudo suricata -c /etc/suricata/suricata.yaml -i eth07. Data Encryption and Transmission Security
Data encryption can effectively protect sensitive information and prevent it from being intercepted or tampered with during transmission.
 image-20240714192010657
image-20240714192010657
Use SSL/TLS for Encrypted Transmission
Enabling SSL/TLS on web servers can encrypt HTTP traffic and protect the security of data transmission.
- Generate SSL Certificate
openssl req -newkey rsa:2048 -nodes -keyout domain.key -x509 -days 365 -out domain.crt- Configure Nginx to use SSL/TLS
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /etc/nginx/ssl/domain.crt;
ssl_certificate_key /etc/nginx/ssl/domain.key;
location / {
proxy_pass http://localhost:8080;
}
}- Start Nginx
sudo systemctl restart nginxDatabase Encryption
Ensure that sensitive data stored in the database is encrypted to prevent data breaches.
from cryptography.fernet import Fernet
# Generate key
key = Fernet.generate_key()
cipher_suite = Fernet(key)
# Encrypt data
data = "Sensitive data"
encrypted_data = cipher_suite.encrypt(data.encode())
# Decrypt data
decrypted_data = cipher_suite.decrypt(encrypted_data).decode()
print(f"Decrypted data: {decrypted_data}")8. Security Development Lifecycle (SDL)
Introducing a security development lifecycle during software development ensures that security issues are considered during the development phase.
Secure Coding Practices
- Input Validation: Strictly validate user input data to prevent common vulnerabilities such as SQL injection and cross-site scripting attacks (XSS).
import re
def validate_input(user_input):
if not re.match("^[a-zA-Z0-9_]*$", user_input):
raise ValueError("Invalid input")
return user_input
user_input = input("Enter username: ")
try:
validated_input = validate_input(user_input)
print(f"Validated input: {validated_input}")
except ValueError as e:
print(e)- Use Secure Libraries and Frameworks: Choose verified secure libraries and frameworks to reduce vulnerabilities in custom code.
9. Regular Security Audits and Assessments
Conducting regular security audits and assessments helps identify and fix security vulnerabilities.
 image-20240714191938280
image-20240714191938280
Security Audit Process
- Plan the Audit: Define the audit scope and objectives.
- Conduct the Audit: Use a combination of tools and manual checks.
- Analyze Audit Results: Examine identified issues and vulnerabilities.
- Develop Improvement Measures: Create a plan to fix vulnerabilities based on the audit results.
- Re-audit: Verify the effectiveness of improvement measures.
10. Zero Trust Architecture
Zero Trust Architecture is a new security concept emphasizing “never trust, always verify”. All internal and external access requests must undergo strict verification and authorization. This architecture better adapts to modern distributed systems and cloud computing environments.
Core Principles of Zero Trust Architecture
- Verify Every Access Request: All access requests must undergo identity verification and authorization, regardless of origin.
- Minimal Privilege Access: Grant only the minimal permissions necessary for users and devices to complete tasks, reducing potential attack surfaces.
- Granular Access Control: Dynamically adjust access policies based on user identity, device status, location, and other contextual information.
- Continuous Monitoring and Analysis: Continuously monitor system behavior and promptly detect anomalies and potential threats.
Steps to Implement Zero Trust Architecture
- Identify Critical Resources and Data: Determine key resources and sensitive data in the system for focused protection.
- Implement Strong Identity Verification: Use technologies like multi-factor authentication (MFA) and biometrics to ensure the authenticity of access identities.
- Apply Granular Access Control Policies: Dynamically adjust access rights based on user roles, device states, and context.
- Continuous Monitoring and Auditing: Real-time monitoring of system activities with regular security audits to promptly identify and respond to security events.
11. Threat Intelligence and Collaboration
Utilizing threat intelligence information can help foresee potential attack threats and take corresponding protective measures in advance. Meanwhile, sharing and collaborating on security intelligence with other organizations and institutions can more effectively counter complex cyber threats.
Using the Open Source Threat Intelligence Platform MISP
MISP (Malware Information Sharing Platform & Threat Sharing) is an open-source platform for collecting and sharing threat intelligence widely used in security intelligence operations.
- Install MISP
sudo apt-get update
sudo apt-get install misp- Configure MISP (/etc/misp/config.php)
- Start MISP
sudo systemctl start misp- Use MISP API to Collect Threat Intelligence
import requests
def get_threat_intel(api_url, api_key):
headers = {
'Authorization': api_key,
'Accept': 'application/json'
}
response = requests.get(api_url, headers=headers)
if response.status_code == 200:
return response.json()
else:
return None
api_url = 'https://misp-instance/events'
api_key = 'your_api_key_here'
intel_data = get_threat_intel(api_url, api_key)
if intel_data:
print("Threat Intelligence Data:", intel_data)
else:
print("Failed to retrieve threat intelligence data.")12. Security Incident Response and Contingency Plans
Develop and drill security incident response and contingency plans to ensure rapid response and recovery in the event of security incidents, minimizing loss and impact.
Security Incident Response Process
- Preparation Phase: Establish security incident response plans, configure security monitoring tools, and conduct regular security drills.
- Identification Phase: Identify security incidents through monitoring and alert systems, confirming the nature and scope of the incident.
- Containment Phase: Take measures to contain further spread of the incident, such as isolating affected systems and closing related services.
- Eradication Phase: Completely remove attacker remnants like deleting malicious code and fixing vulnerabilities.
- Recovery Phase: Restore systems and services ensuring normal operation and perform subsequent monitoring.
- Post-Incident Analysis and Improvement: Summarize lessons learned from the incident, improve security measures, and prevent similar incidents from occurring again.
Writing Emergency Plan Documentation
Emergency Plan Document
1. Objectives and Scope
- Define the goals and applicable scope of the emergency plan.
2. Organizational Structure
- Clearly define the roles and responsibilities of each department and personnel in emergency response.
3. Emergency Response Process
- Preparation Phase
- Identification Phase
- Containment Phase
- Eradication Phase
- Recovery Phase
- Post-Incident Analysis and Improvement
4. Communication Plan
- Determine the communication channels and methods among departments during emergency response.
5. Drill Plan
- Conduct regular emergency drills to test and improve the emergency plan.
6. Appendix
- Related tools and resources
- Contact information image-20240714192033063
image-20240714192033063
Conclusion
Network security anti-penetration is a complex and dynamic process that requires the comprehensive use of various technologies and methods. By strengthening network perimeter defense, vulnerability management, authentication and access control, log auditing and monitoring, security training, intrusion detection and prevention, data encryption, security development lifecycle, regular security audits, zero trust architecture, threat intelligence collaboration, and security incident response and contingency plans, system security can be effectively enhanced, reducing the risk of penetration attacks. It is hoped that the solutions and code examples provided in this article will serve as valuable references and assistance in readers’ actual work.
Original Declaration: This article is authorized for publication by the author to Tencent Cloud Developer Community, and may not be reproduced without permission.
If there is any infringement, please contact [email protected] for removal.


