You are likely familiar with the classic network architecture consisting of access, aggregation, core, and egress layers. In most cases, the access layer relies on layer 2 switches, often chosen for cost-saving reasons. These switches are typically configured to isolate broadcast domains and manage traffic. However, this approach can introduce challenges, particularly when it comes to Network Loop Prevention. Addressing network loops remains a persistent issue for network engineers, as loops can severely disrupt network performance and stability.
When data packets are transmitted in a closed path, a loop is formed, which can lead to a series of problems such as broadcast storms, resource exhaustion, and network performance degradation. These problems not only affect user experience, but may also cause critical business interruptions.
Many network engineers have put a lot of thought into preventing loops.
Let’s talk about basic operations. In order to prevent loops, most people will configure the spanning tree protocol at the access layer . But in addition to STP (Spanning Tree Protocol), do you know how to prevent and solve loops?
1 What is a Network Loop and Why is Network Loop Prevention Important?
A network loop occurs when data packets circulate continuously along closed paths in the network, often due to redundant connections between switches. Without proper Network Loop Prevention, these loops can disrupt network stability.
This phenomenon usually occurs when multiple paths connect the same set of devices, such as when redundant connections are formed between switches . When a node in the network cannot correctly identify the paths that have been visited, the data packets will endlessly cycle through these paths.
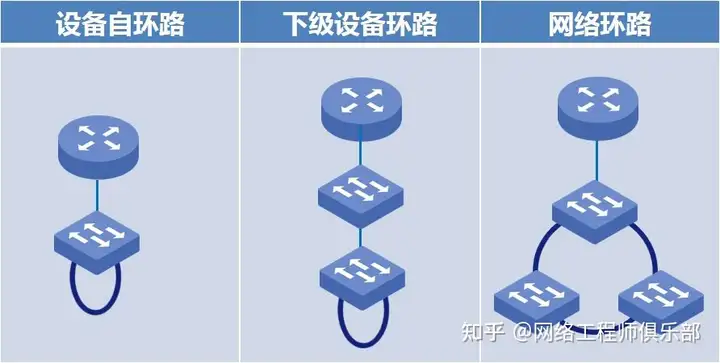
1.1 Impact of loops on network performance
Broadcast storm :When a loop occurs, broadcast packets are continuously replicated in the network, eventually causing a sharp increase in the number of broadcast frames and consuming a large amount of bandwidth.
Resource exhaustion: As data packets continue to circulate in the loop, network resources (such as memory and CPU) will be over-occupied, affecting normal data transmission.
Increased latency: Circulating packets occupy network resources and increase the transmission latency of legitimate packets.
Packet loss: Severe loops may cause switches and routers to be overloaded and unable to process new data packets, resulting in packet loss.
2 Network Loop Detection and the Role of Network Loop Prevention Tools
2.1 Common loop detection tools and techniques
Utilize tools like Ping, Traceroute, Network Management Systems, and Loopback Detection Protocol to detect network loops. Implementing Network Loop Prevention mechanisms ensures network reliability.
Ping Tool: Checks network connectivity by sending ICMP Echo requests . If there are continuous responses, it may be a sign of a loop.
Traceroute/Tracert: Traces each hop that a data packet takes from the source address to the destination address, helping to discover potential loop paths.
Network Management Systems (NMS): Use the SNMP protocol to monitor the status of network devices and detect abnormal behavior in a timely manner.
Dedicated loop detection tools: such as Loopback Detection Protocol (LDP) or similar dedicated software tools that can automatically detect loops and generate warnings.
2.2 How to use these tools for diagnosis
Ping test:
- Use the ping command to send a packet to the target device.
- Observe the timestamps and response counts of the responses. If the responses are continuous and increasing, there may be a loop.
Traceroute/Tracert test:
- Run the traceroute or tracert command to trace each hop that the data packet passes through.
- Check the path for duplicate IP addresses or device names, which is often a sign of a loop.
NMS Monitoring:
- Configure the NMS to monitor key network metrics, such as the number of broadcast frames, CPU utilization, and memory usage.
- Set up threshold alarms to sound an alert when a predetermined threshold is reached.
03 Network Loop Prevention Mechanisms for Physical and Logical Layers
3.1 Physical Level
Best practices for network topology design:
- Adopting the hierarchical design principle, the network is divided into the core layer, aggregation layer and access layer .
- Optimize the design of redundant connections to ensure that the connections between each layer form as few closed loops as possible.
- Use star or tree topologies and avoid full grid layouts.
Use port security policies to restrict access to devices:
- Enable port security on the access layer switches to limit the number of MAC addresses that can be learned on each port.
- If an unauthorized device is detected, the port will be automatically closed to prevent the illegal device from causing a loop.
3.2 Logical Level
Spanning Tree Protocol (STP) and its variants:
- STP: Prevents certain ports from forwarding data by calculating the spanning tree to eliminate loops.
- Rapid Spanning Tree Protocol (RSTP): Provides faster convergence speed than STP .
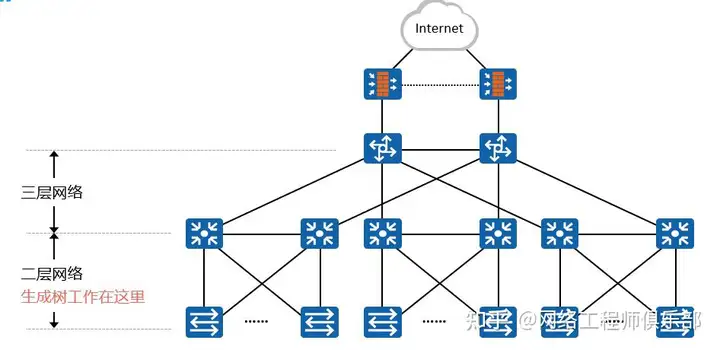
Multiple Spanning Tree Protocol (MSTP):
- Allows different spanning tree instances to be applied to different VLANs on the same physical network , thus improving network utilization.
Link Aggregation Control Protocol (LACP) and static link aggregation:
- Use LACP to dynamically aggregate multiple physical links to increase bandwidth while providing redundant paths .
- Manually configure static link aggregation when necessary to ensure that links in the link aggregation group do not form a loop.
3.3 VLAN Design and Management:
Reasonably divide VLANs to reduce the size of broadcast domains and reduce the possibility of loops.
Implement necessary isolation measures between VLANs to prevent the spread of broadcast storms.



