During a recent emergency, a low-privilege user on the machine was successfully brute-forced via SSH, and after the intrusion, a malicious script was executed with root privileges?
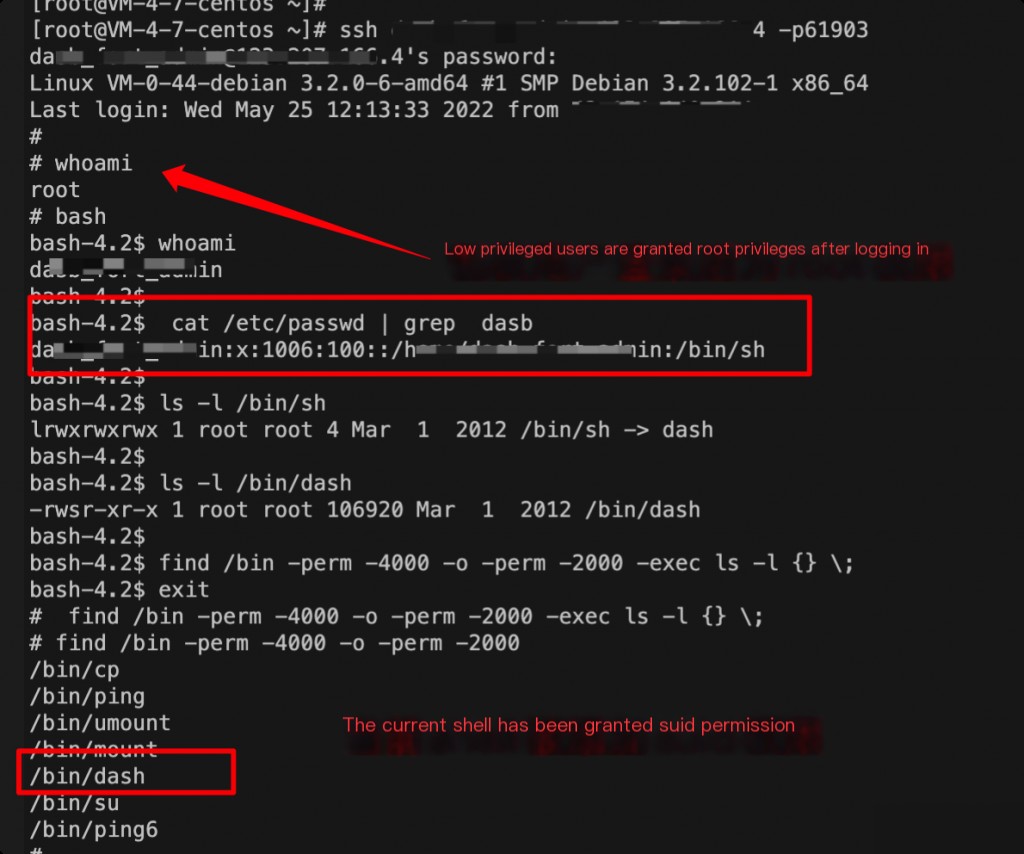 Added SUID permission to the shell
Added SUID permission to the shell
Initially, I thought there was a privilege escalation vulnerability, so I checked for Dirty COW, Dirty Pipe, and polkit, but none of these were present.
The files modified by this low-privilege user had a UID of root but the GID remained the same.
I then speculated that there might be an issue with the PAM configuration, but it shouldn’t have a significant impact on permissions.
It seemed like the shell itself had a problem. After investigation, it was found that the xxx user was a low-privilege user, and since the sh shell was given SUID permission, all users with /bin/sh specified as their shell in /etc/passwd could directly obtain root privileges upon login.
This pitfall has been noted. Previously, I only considered privilege escalation through SUID, but I never thought that directly adding SUID to the shell would immediately grant root privileges. This really caught me off guard.


