Troubleshooting Windows is straightforward for me because it is mouse-driven, and there’s an abundance of small tools to assist in Windows troubleshooting, making the process quite easy. This article mainly covers general capabilities that apply not only to Tencent Cloud but also to other cloud services. For those specifically interested in Tencent Cloud, I recommend a document I wrote about pitfalls and solutions for the Tencent Cloud SDK. This document is the result of over 100 hours of work and compiles 10 articles from the Cloud+ Community. You can find it here: [The Basics of Tencent Cloud API Explorer: Mastering the Use of 6 SDKs](https://cloud.tencent.com/developer/article/1604932?from_column=20421&from=20421).
Returning to the theme of this article, before discussing Windows troubleshooting ideas, I want to remind everyone about some unexpected behaviors of PC software on Windows servers, which I have specifically introduced here, Use PC Software on Servers Carefully. Additionally, obtaining and analyzing Windows logs is not difficult. I generally analyze them myself, figuring out the reasons even faster than submitting a support ticket (personally, I find Alibaba Cloud’s service tickets the slowest, Tencent Cloud’s tickets have the highest call frequency to users, and I’m still experiencing Huawei Cloud’s service).
Getting back to the core topic, this article briefly introduces Windows troubleshooting ideas from ten aspects: system drivers, application software, scheduled tasks, startup items, critical system directories, virus and malware, dmp file analysis, common software sets nirsoft.net and sysinternals.com, and general software.
1. System Drivers
① process explorer
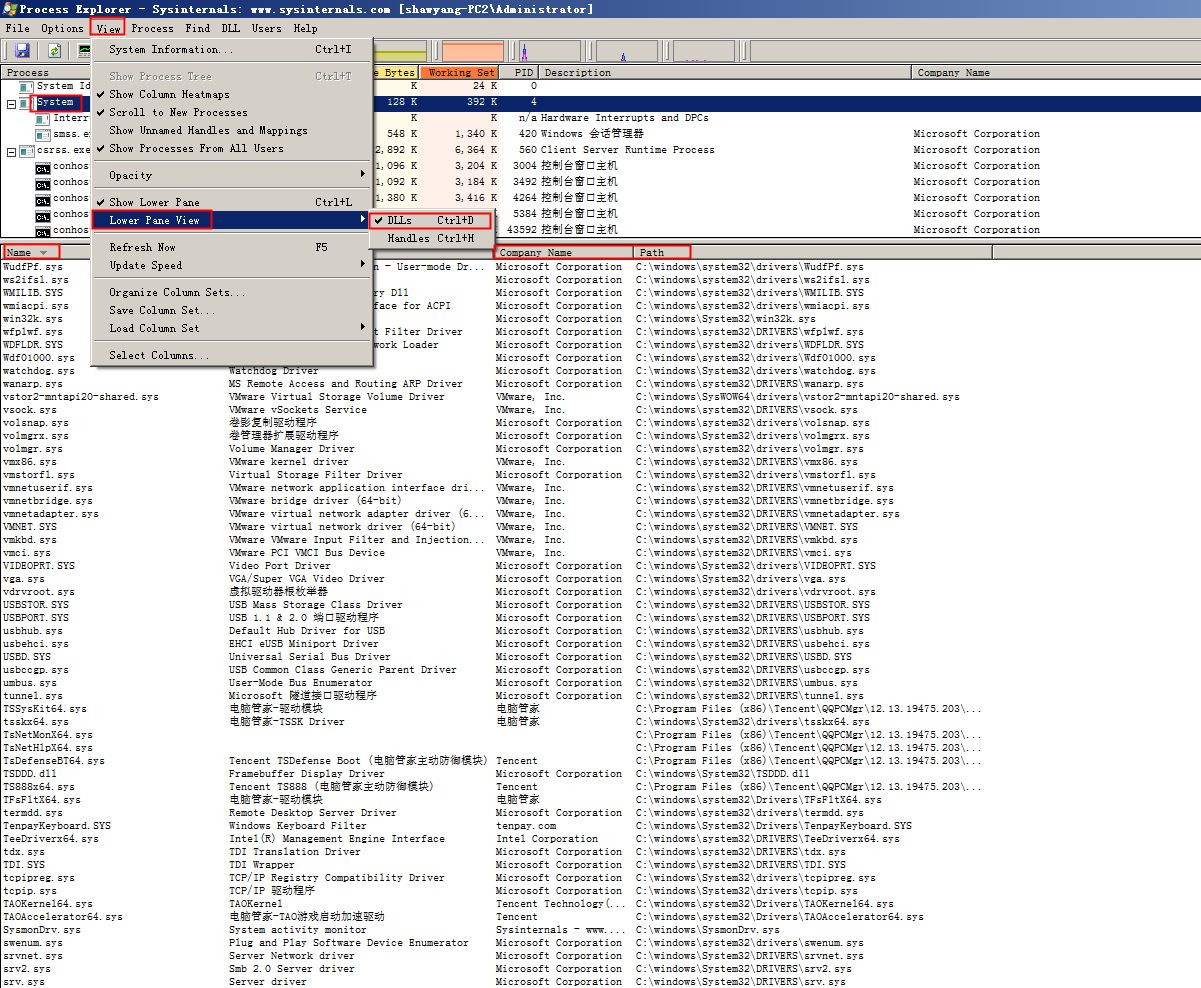
As shown above, you can only select the System process. After selection, click “view → Lower Pane View → Dlls (Ctrl+D)” to view all system drivers below, with four columns: Name, Description, Company Name, Path; by checking the “Company Name” column, it is easier to identify newly introduced drivers.
You can also use autoruns to check system drivers, service lists, and scheduled tasks to find anomalies.
https://docs.microsoft.com/en-us/sysinternals/downloads/autoruns
https://cloud.tencent.com/developer/article/1557575
Overall, autoruns and process explorer are essential tools for Windows troubleshooting, offering the best cost-effectiveness for troubleshooting Windows.
② nirsoft.net ServiWin
The ServiWin utility displays the list of installed drivers and services on your system.
ServiWin utility shows a list of drivers and services installed on the system.
http://www.nirsoft.net/utils/serviwin.html
nirsoft.net also offers a small tool called InstalledDriversList, whose function is self-explanatory.
2. Application Software
appwiz.cpl
Third-party software such as Revo Uninstaller Pro, UninstallView (another tool from nirsoft.net), can all check the software already installed on the system. These programs can show more details on the installation order of each software, and uninstalling them tends to be cleaner than using appwiz.cpl.
3. Scheduled Tasks
① Location of scheduled task shortcut
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Administrative Tools\Task Scheduler.lnk
② Command:
taskschd.msc
③ Scheduled tasks exist in four locations:
C:\Windows\SysWOW64\Tasks
C:\Windows\System32\Tasks
C:\Windows\System\
C:\Windows\Tasks\
4. Startup Items
① Software useful for analyzing startup items:
AnVir Task Manager
WhatInStartup
Autoruns
Security Task Manager
Startup Delayer
WinPatrol
② Winlogon Shell, open and analyze Group Policy. If not present, skip it.
③ Registry analysis locations
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad\
④ Startup directories
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
C:\Windows\SysWOW64\config\systemprofile\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
C:\Windows\System32\GroupPolicy\Machine\Scripts\Startup
C:\Documents and Settings\All Users\StartMenu\Programs\Startup
C:\ProgramData\StartMenu\Programs\Startup
⑤ %xxx% Directories
%APPDATA%
%CommonProgramFiles%
%TEMP% and %TMP%
%ProgramW6432%
%programfiles(X86)%
%programfiles%
%SYSTEMROOT%
%WINDIR%
%HOMEDRIVE%
%SYSTEMDRIVE%
%ALLUSERSPROFILE%
%USERPROFILE%
%public%
[c:\progra~1]=[C:\Program Files]
[c:\progra~2]=[C:\Program Files (x86)]
[c:\progra~3]=[C:\ProgramData]
[c:\progra~1\Intern~1\]=[C:\Program Files\Internet Explorer\]
[C:\Users\ADMINI~1\]=[C:\Users\Administrator\]
5. Critical System Directories
C:\Windows\Fonts
C:\Users\Administrator\Desktop
C:\Windows\Web
C:\Windows\Temp
C:\Windows\System
C:\Windows\System32
C:\Windows\
C:\Windows\System32\Logs
C:\Windows\security
C:\Windows\INF
C:\Windows\debug
C:\ProgramData\Microsoft\Windows\Caches
C:\Windows\apppatch
C:\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files
C:\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5
……
Enter the folder names above into the Run dialog to open them
For example
⑥ System Environment Variables
echo %path% (unlike in Linux, where it’s echo $PATH)
6. Service List
services.msc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\
Many trojans and viruses exist on the hard drive and are registered in the registry as “services,” but these services are hidden and cannot be seen in the services.msc list.
psservice (sysinternals.com pstools toolset https://cloud.tencent.com/developer/article/1617430)
7. Virus and Malware
360, PC Manager https://cloud.tencent.com/developer/article/1612225
https://www.virustotal.com/gui/home/upload
http://lockhunter.com/download.htm
Windows trojan viruses often hide in the following locations
C:\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
C:\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
Also other Content.IE5, search with Everything
C:\Windows\Temp
C:\Users\ADMINI~1\AppData\Local\Temp
C:\Users\Administrator\AppData\Local\Temp and same as above
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
(And other users’ temp directories, replace the username as needed)
XP, 2003 temp paths are as follows
C:\DocumentsandSettings\Username\LocalSettings\Temp
C:\DocumentsandSettings\Username\LocalSettings\Temporary Internet Files
C:\Windows\System32\wbem
C:\Windows\System32\drivers
C:\Windows\System32\……
C:\Windows\inf\
C:\Windows\Web\
C:\Windows\debug\
C:\Windows\Fonts
C:\Windows\……
System Volume Information of various partitions
Anti-virus commands (normal system files have fixed locations, files with the same names not in their original locations are usually viruses)
wmic process where “name=’svchost.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\svchost.exe’” call Terminate
wmic process where “name=’wininit.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\wininit.exe’” call Terminate
wmic process where “name=’csrss.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\csrss.exe’” call Terminate
wmic process where “name=’csrs.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\csrs.exe’” call Terminate
wmic process where “name=’WUDFHost.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\WUDFHost.exe’” call Terminate
wmic process where “name=’services.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\services.exe’” call Terminate
wmic process where “name=’taskhost.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\taskhost.exe’” call Terminate
wmic process where “name=’conhost.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\conhost.exe’” call Terminate
wmic process where “name=’winlogon.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\winlogon.exe’” call Terminate
wmic process where “name=’msinfo.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\msinfo.exe’” call Terminate
wmic process where “name=’explorer.exe’ and executablepath<>’%SystemDrive%\\windows\\explorer.exe’” call Terminate
wmic process where “name=’msinfo.exe’ and ExecutablePath<>’C:\\WINDOWS\\system32\\msinfo.exe’” delete
wmic process where “name=’explorer.exe’ and executablepath<>’%SystemDrive%\\windows\\explorer.exe’” delete
Command to get abnormal processes in the font directory, not all in the result set are viruses, the command is to exclude font files and list remaining files
wmic datafile where “drive=’c:’ and path=’\\windows\\fonts\\’ and extension<>’ttf’ and extension<>’fon’ and extension<>’ttc’ ” get Name
wmic datafile where “drive=’c:’ and path=’\\windows\\fonts\\’ and extension<>’ttf’ and extension<>’fon’ and extension<>’ttc’ ” get Name,Path,CreationDate,LastAccessed,LastModified
wmic datafile where “drive=’c:’ and path=’\\windows\\fonts\\’ and extension<>’ttf’ and extension<>’fon’ and extension<>’ttc’ ” get Name,Path,CreationDate,LastAccessed,LastModified /value
wmic datafile where “drive=’c:’ and path=’\\windows\\fonts\\’ and extension<>’ttf’ and extension<>’fon’ and extension<>’ttc’ ” get Name,Path,CreationDate,LastAccessed,LastModified /format:list
https://cloud.tencent.com/developer/article/1613296
8. dmp File Analysis
① bluescreen view
http://www.nirsoft.net/utils/blue_screen_view.html
② windbg
9. Other Potentially Useful Software
① Sysinternals.com toolset
Sysinternals has a bunch of useful small tools, like pstools, and it’s important to note that newsid.exe has been retired; don’t use newsid recklessly on cloud servers, as it can cause servers to black screen or enter recovery mode, rendering them unusable. If you need to change the SID, it’s recommended to use the sysprep command or third-party software like sidchg. Notably, sysprep has two drawbacks: it’s time-consuming and it wipes data in the “home directory.”
② nirsoft.net offers many good software options such as UninstallView, LastActivityView, TurnedOnTimesView, WinLogOnView, BlueScreenView, BrowsingHistoryView, CurrPorts, DevManView, DriverView, EventLogSourcesView, HashMyFiles, InstalledCodec, InstalledDriversList, ProcessActivityView, ProduKey, RegScanner, ShellMenuView, SmartSniff, SoundVolumeView, SpecialFoldersView, USBDeview, WebSiteSniffer, WhatInStartup, ServiWin
SpecialFolderView
AppReadWriteCounter
NTFSLinksView
HtmlDocEdit
SimpleWMIView
LoadedDllsView
UninstallView
FullEventLogView
RegScanner
RegistryChangesView
TaskSchedulerView
LastActivityView
ProcessThreadsView
ServiWin
SecuritySoftView
InstalledDriversList
WhatInStartup
10. General Software or Capabilities
Cloud platform security groups, system firewalls, everything, notepad++, powershell, wireshark, etc.



