I. Introduction: An Overview of PCAPdroid
On Android devices, it is often necessary to capture packets to troubleshoot issues. For capturing packets within the system, the well-known popular methods include using tools like PCAPdroid.
- After rooting the phone, install certain packet capture software;
- Known proxy software on the market, such as Burp Suite, Wireshark, Charles, require the computer to open proxy ports for the phone to access, and Burp Suite and Charles can only capture HTTP/HTTPS application layers;
- No root required, but can only capture HTTP/HTTPS application layer interactions, unable to capture TCP/UDP raw packets, like HttpCanary.
The above scenarios have their drawbacks to varying degrees. So, what method can comprehensively cover the packet capture scene without root or proxy, while allowing capturing native packets anytime and anywhere on the phone, and even exporting packets for analysis on a computer? The answer is PCAPdroid, which we will discuss today.
PCAPdroid is a privacy-friendly application that allows you to track and analyze all the connections of applications on your device. Additionally, it allows you to export in PCAP format for dumping, perform TLS decryption, extract metadata, and many other functionalities.
II. Installing PCAPdroid
Choose one of the following methods:
|
Method |
Link |
|---|---|
|
github | |
|
Google Play Store |
https://play.google.com/store/apps/details?id=com.emanuelef.remote_capture&hl=en_US |
|
F-Droid | |
|
Cloud Storage |
https://data.linux-code.com/?dir=filelist/Software/PCAPdroid |
Just install the main program above, the following installation is for optional features. The installation links are provided here, and the specific installation and usage will be introduced later.
If you want to see the decrypted HTTPS/TLS packets on the phone, you need the additional component PCAPdroid-mitm:
|
Method |
Link |
|---|---|
|
github | |
|
Cloud Storage |
https://data.linux-code.com/?dir=filelist/Software/PCAPdroid-mitm |
If you need the APP name displayed in Wireshark, you need to install the official lua script. Script link:
|
Method |
Link |
|---|---|
|
github |
https://github.com/emanuele-f/PCAPdroid/blob/master/tools/pcapdroid.lua |
|
Cloud Storage |
https://data.linux-code.com/?dir=filelist/Software/PCAPdroid |
III. Practical Packet Capture with PCAPdroid
1. Real-time Packet Capture with PCAPdroid
Once it is displayed as ready, click the ready button or start button above :arrow_forward: to start capturing, and then go to the connection page to view all connections in real-time:
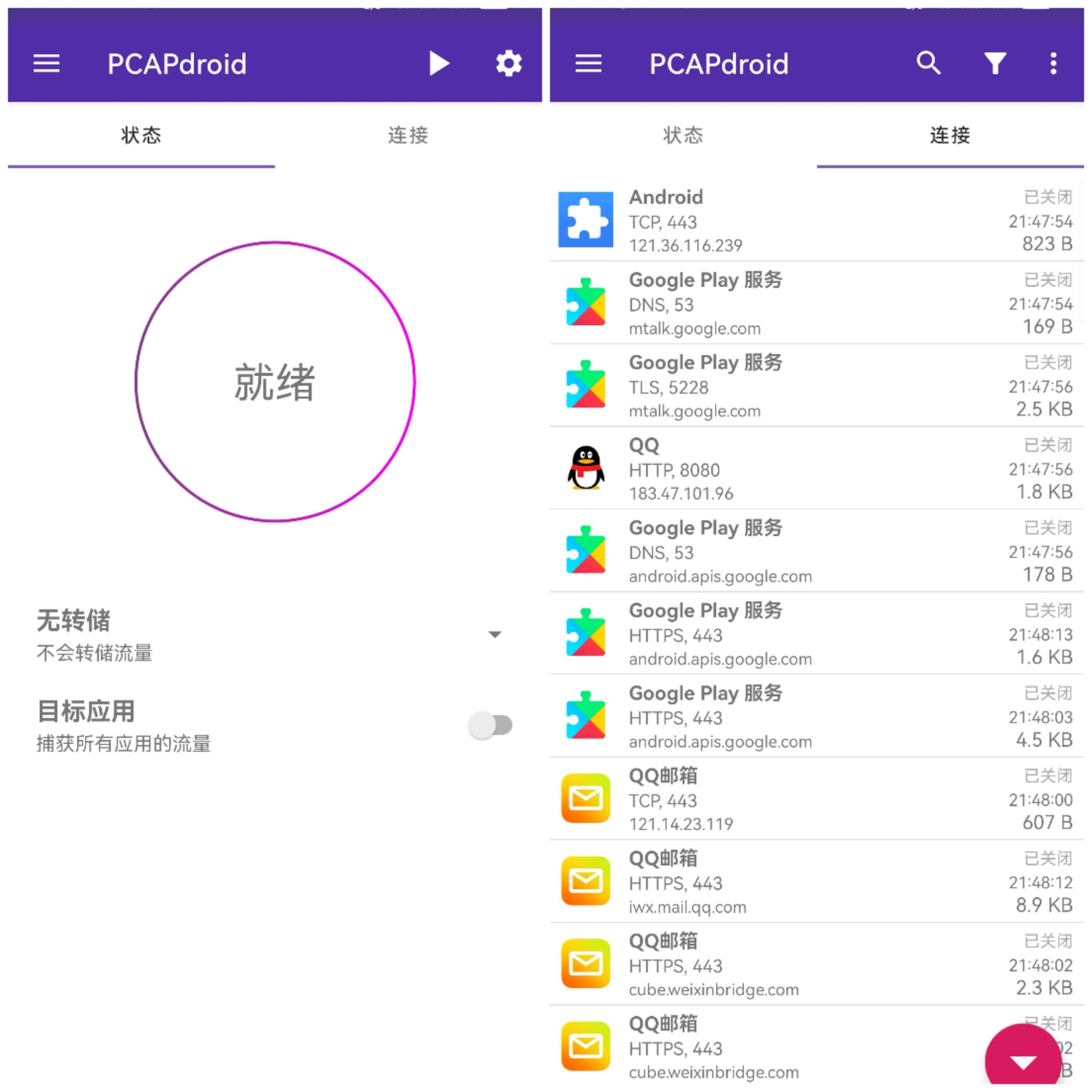
You will find that these connections will indicate which APP processes generated them, and show the destination domain, protocol, port, and connection status, etc.
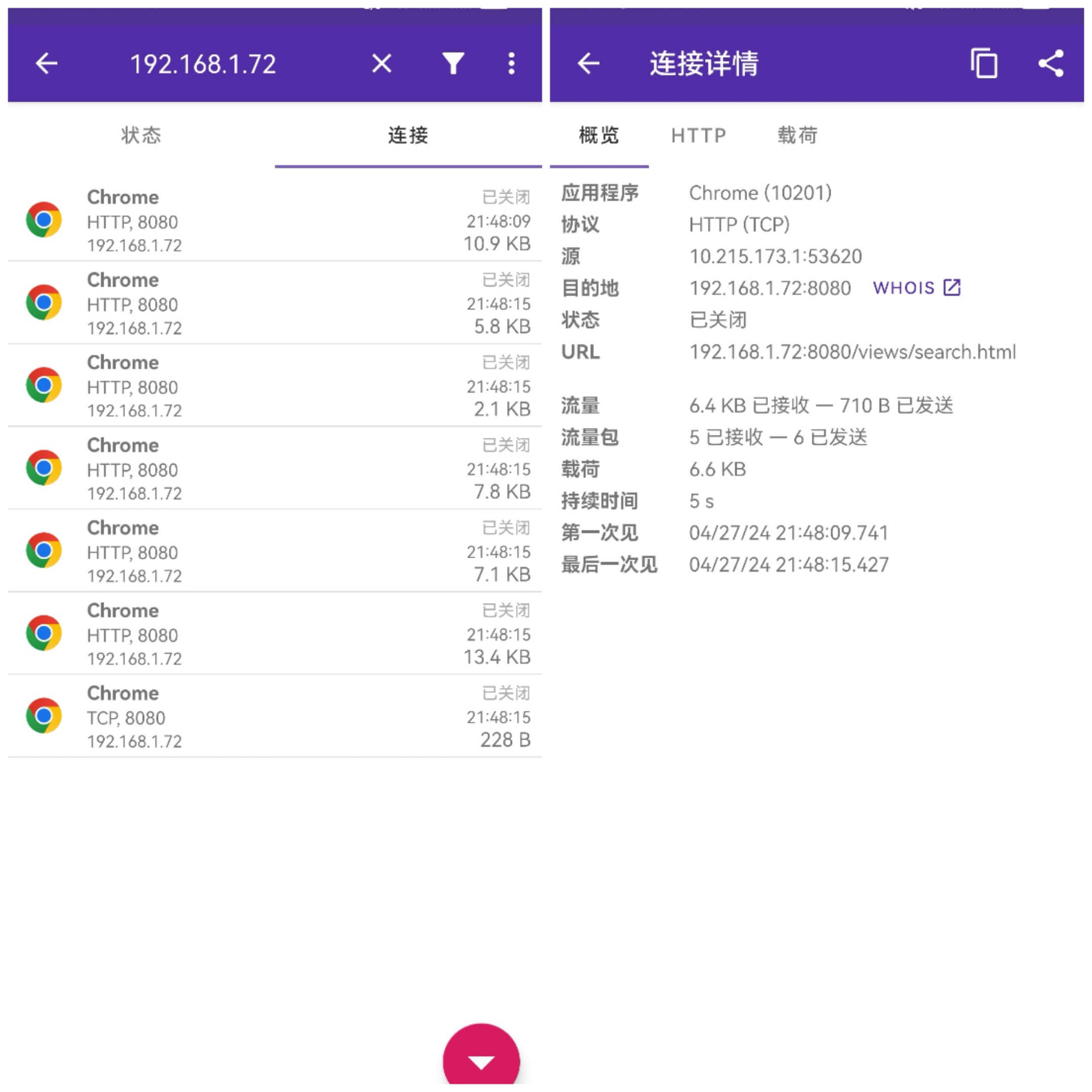
1) Filtering Specific Targets
By filtering specific target hosts through the search box on the left, you can see that these connections are currently closed (CLOSED) because they are using short connection scenarios; clicking on any connection gives an overview, including connection duration, accessed URL, protocol, process APP, and process ID, as well as traffic size and payload length:
2) Viewing HTTP Requests and Payload
Additionally, the HTTP and payload options clearly display the content requested and content responded to by this TCP connection:
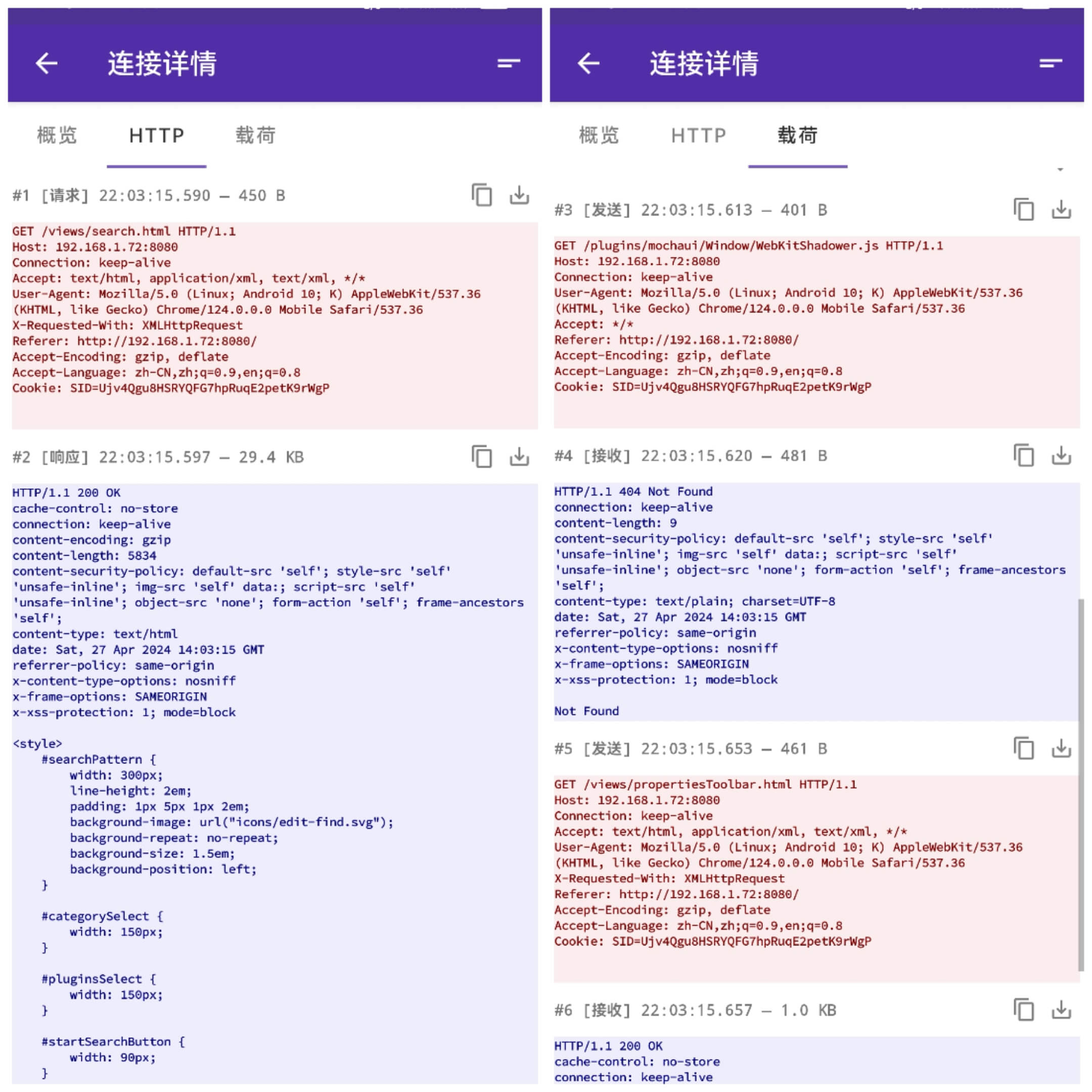
These texts can be copied or exported as desired.
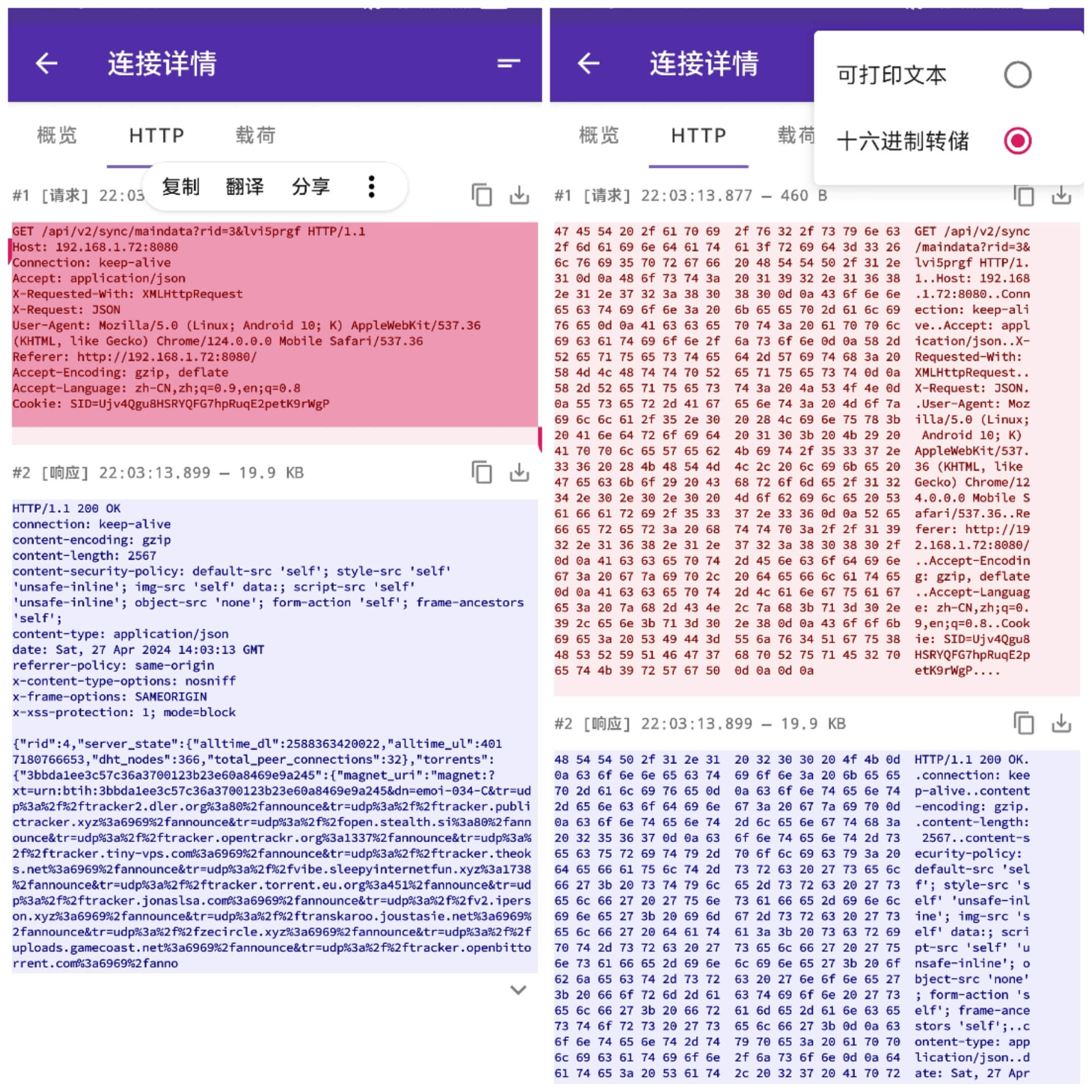
The display can even be in hexadecimal format by clicking on format conversion at the top right, as shown in the right image:
2. Saving for Analysis in PCAPNG Format
1) Unlocking and Enabling PCAPNG Format Dump Option
Saving in PCAPNG format is a feature unlocked after payment, currently available for 13 Hong Kong dollars, and once unlocked, allows TLS decryption, checked in settings:
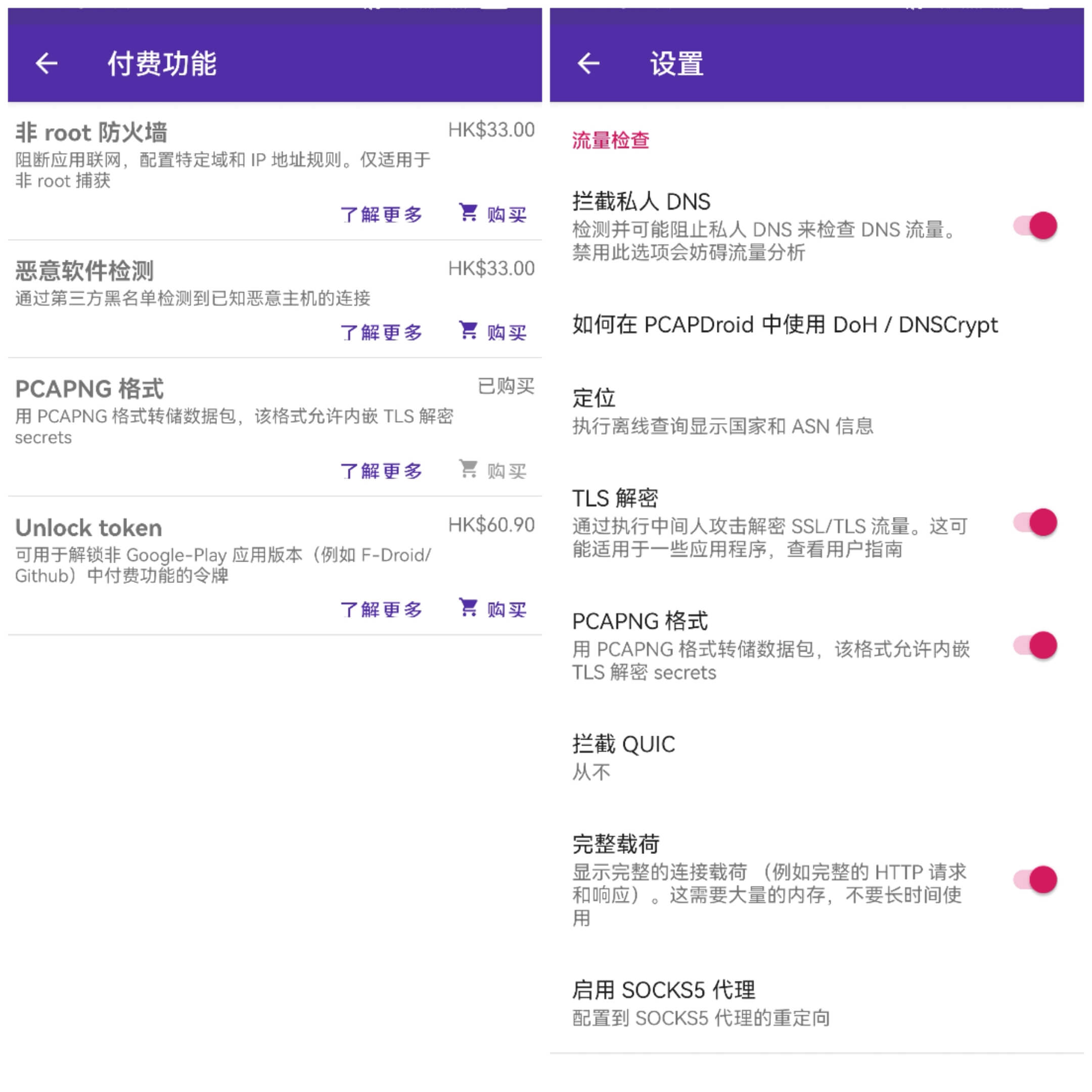
2) Setting Packet Dump
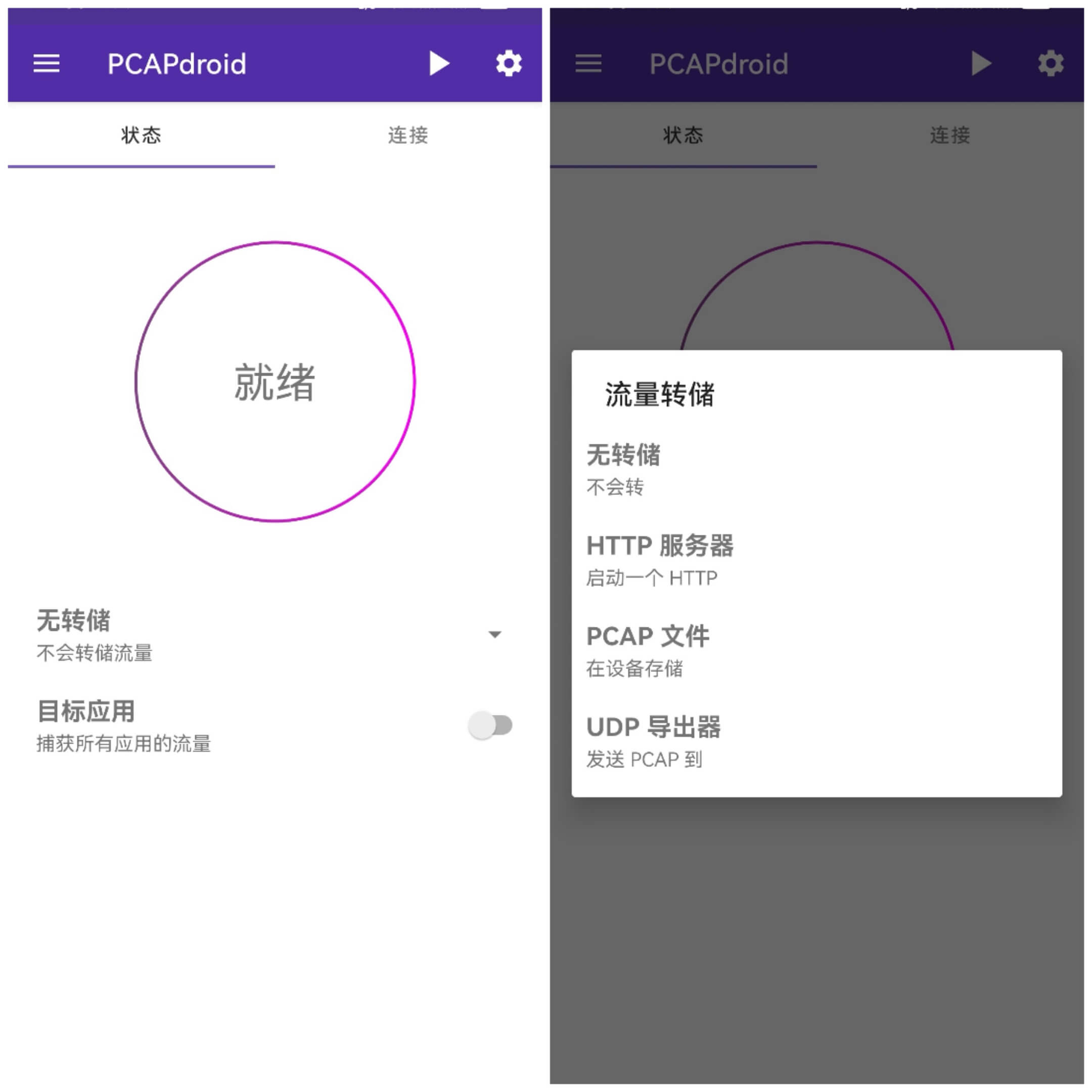
Packet dump is divided into three categories:
- HTTP server dump: Android will start an HTTP service, providing PCAP packet download;
- PCAP File: Directly store as a PCAP format file on the phone;
- UDP Exporter: Send PCAP file to a remote UDP receiver.
Without specific needs, the second option is the straightforward recommendation.
3) Real-time Capturing and Saving as pcapng Format
Taking the second dumping method as an example, start capturing by clicking ready, and the packet files will be named in a time format:
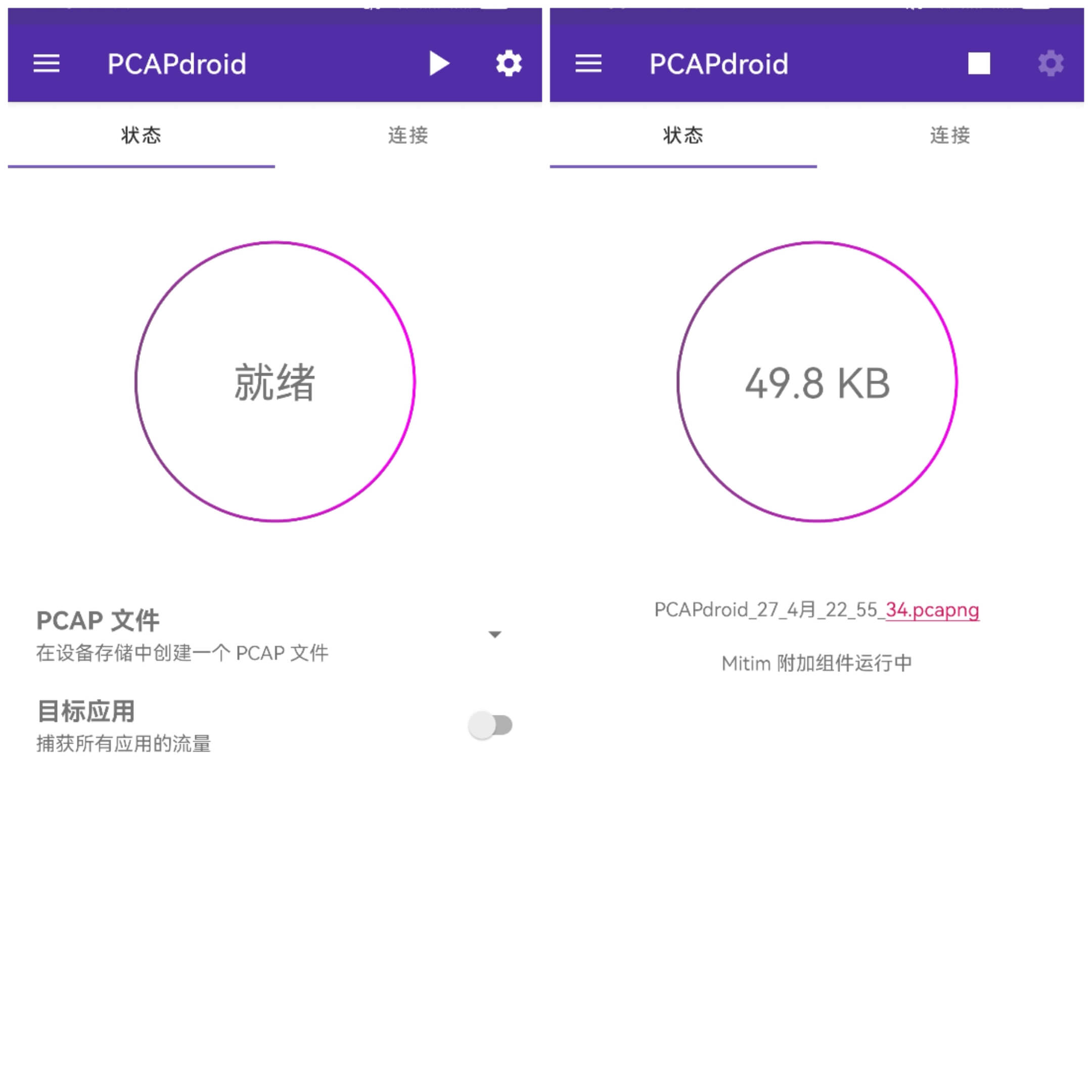
Afterwards, stop capturing and find the dumped packet file in the file manager:
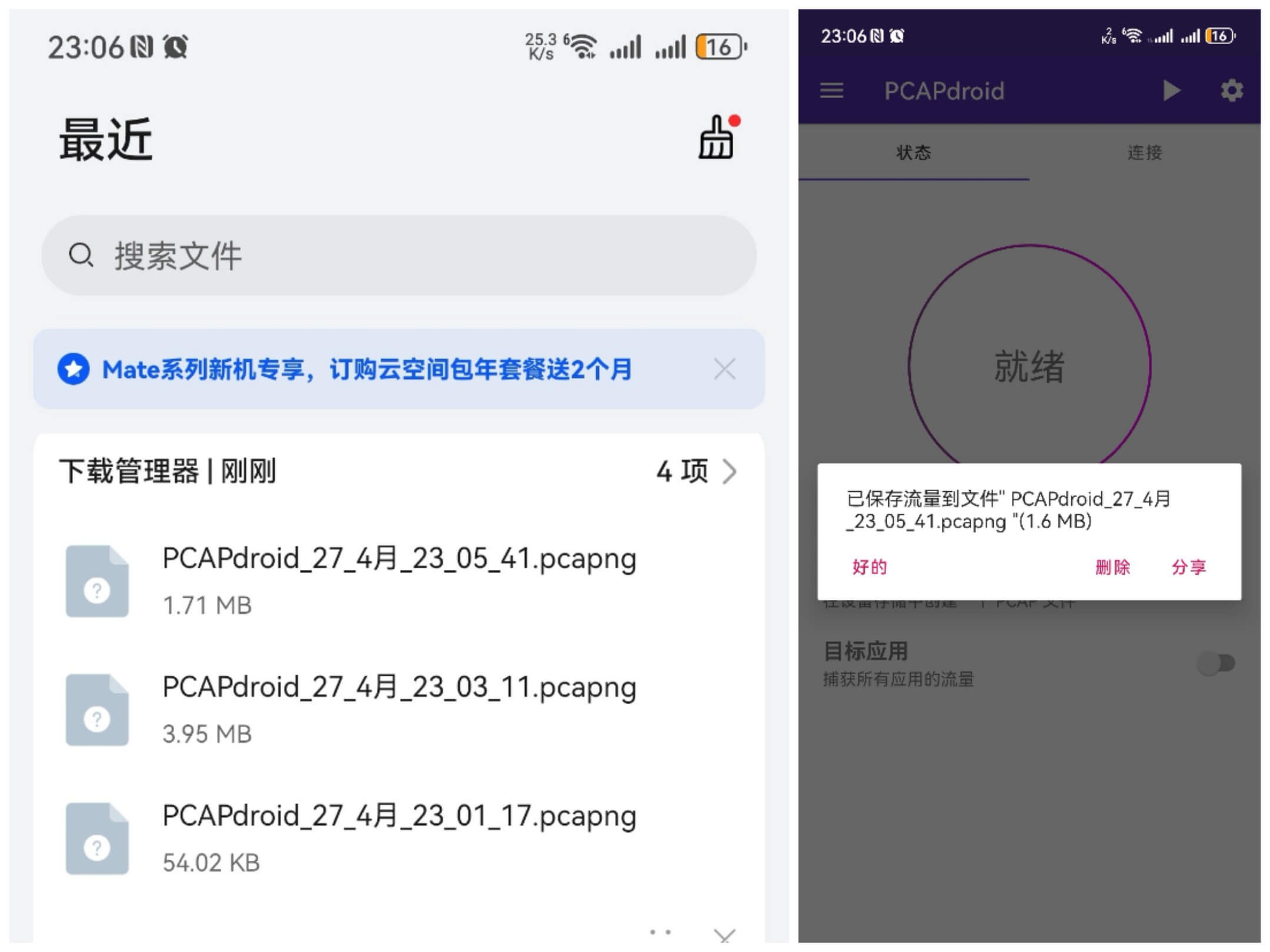
Export it to the computer and open it with Wireshark to check:
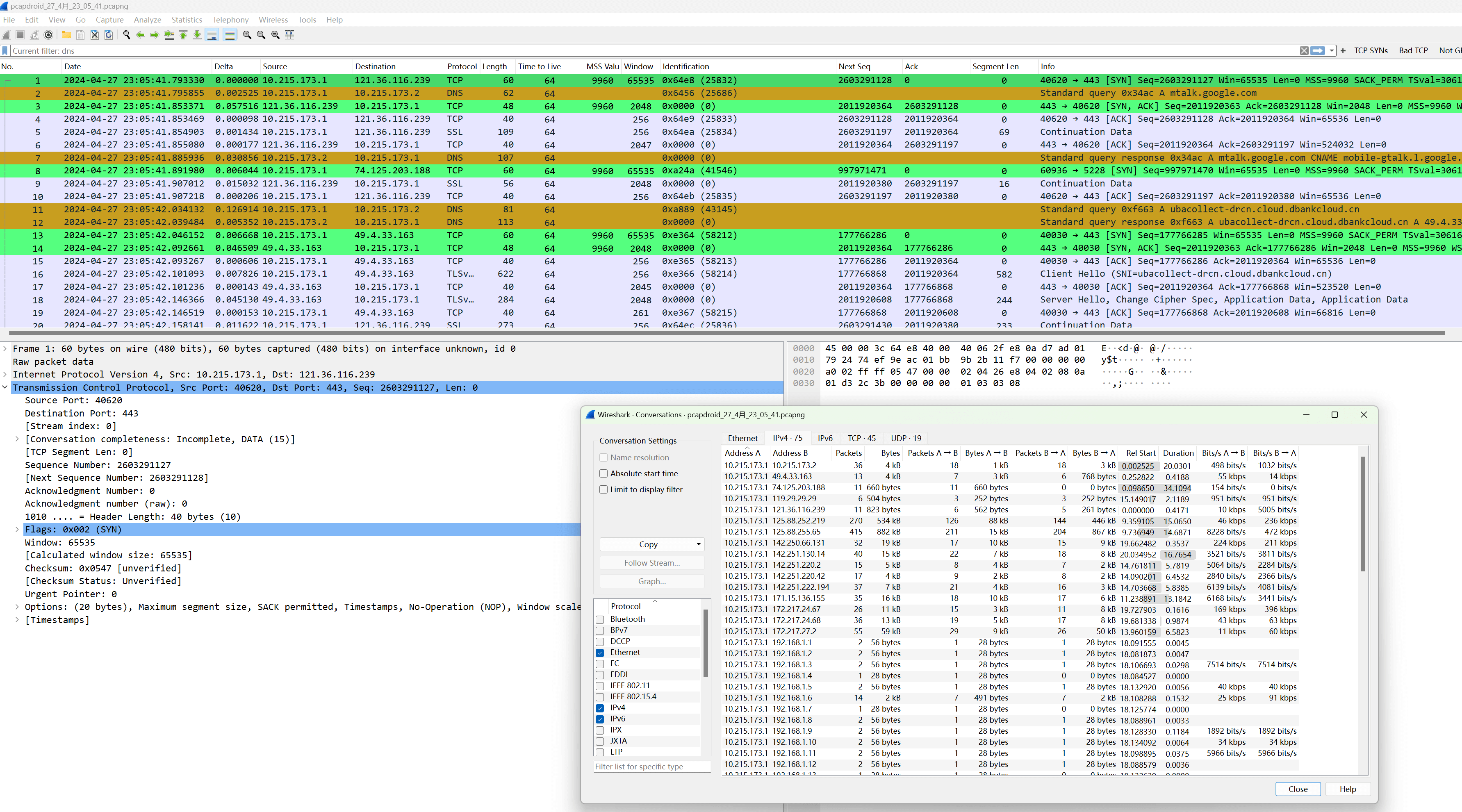
After opening, it is a standard packet format with complete interactive messages, including TCP handshake, DNS queries, TLS handshake, etc. This step practically surpasses all Android packet capture software currently on the market.
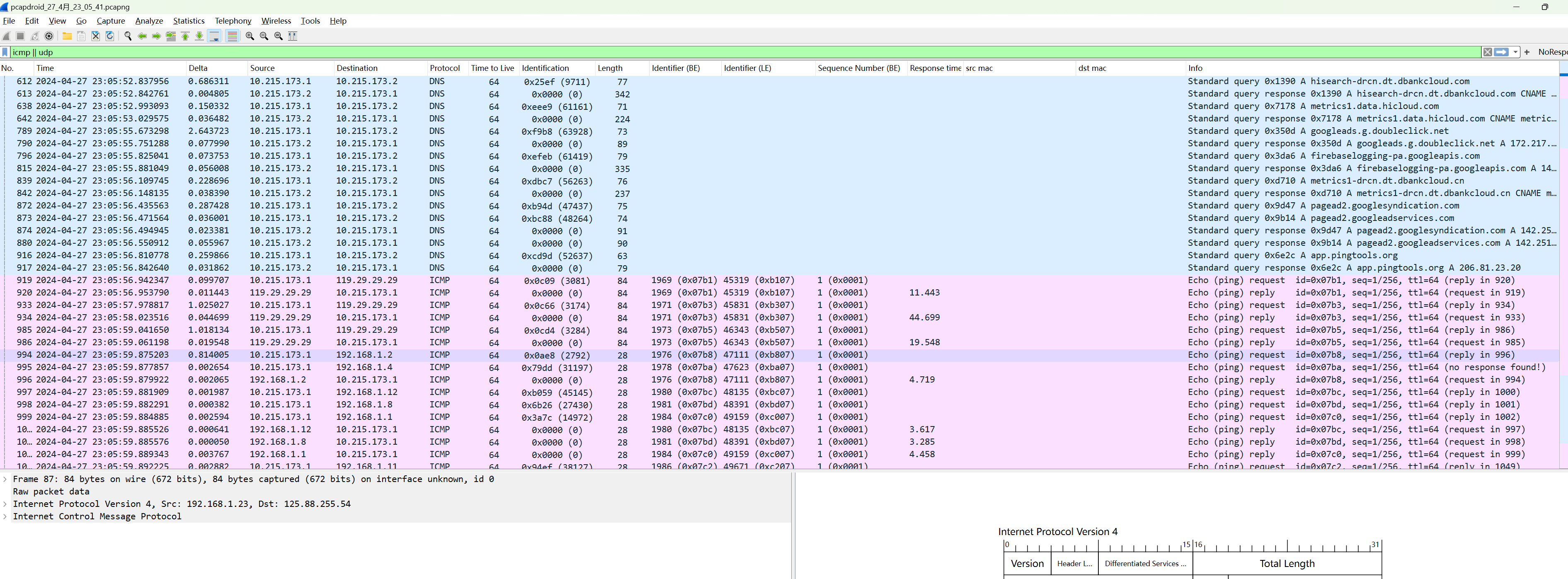
ICMP and UDP can also be fully captured:
4) Installing Wireshark Lua Plugin to Display APP Name
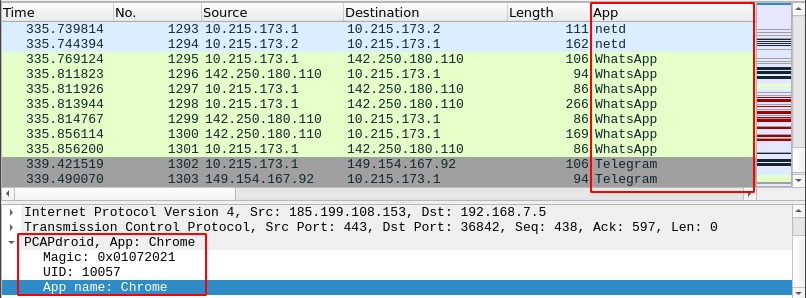
This is optional, the official provides a lua script. After enabling this script in Wireshark, you can see which process APP corresponds to each data frame:
Prerequisite:
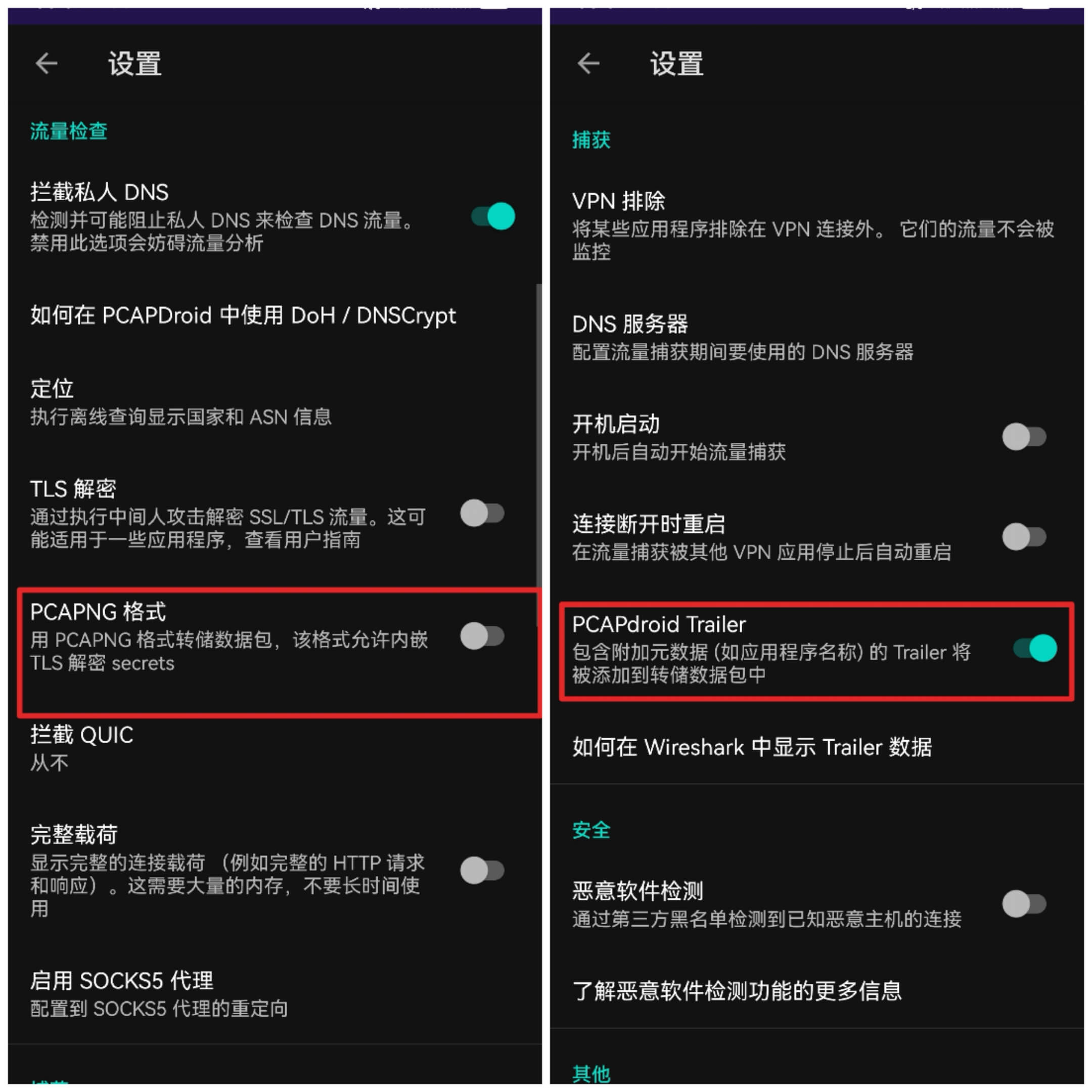
① PCAPdroid’s PCAPdroid Trailer option is enabled, and PCAPNG format is disabled (disabling PCAPNG format does not affect your ability to dump in PCAP format):
② Install the official lua plugin
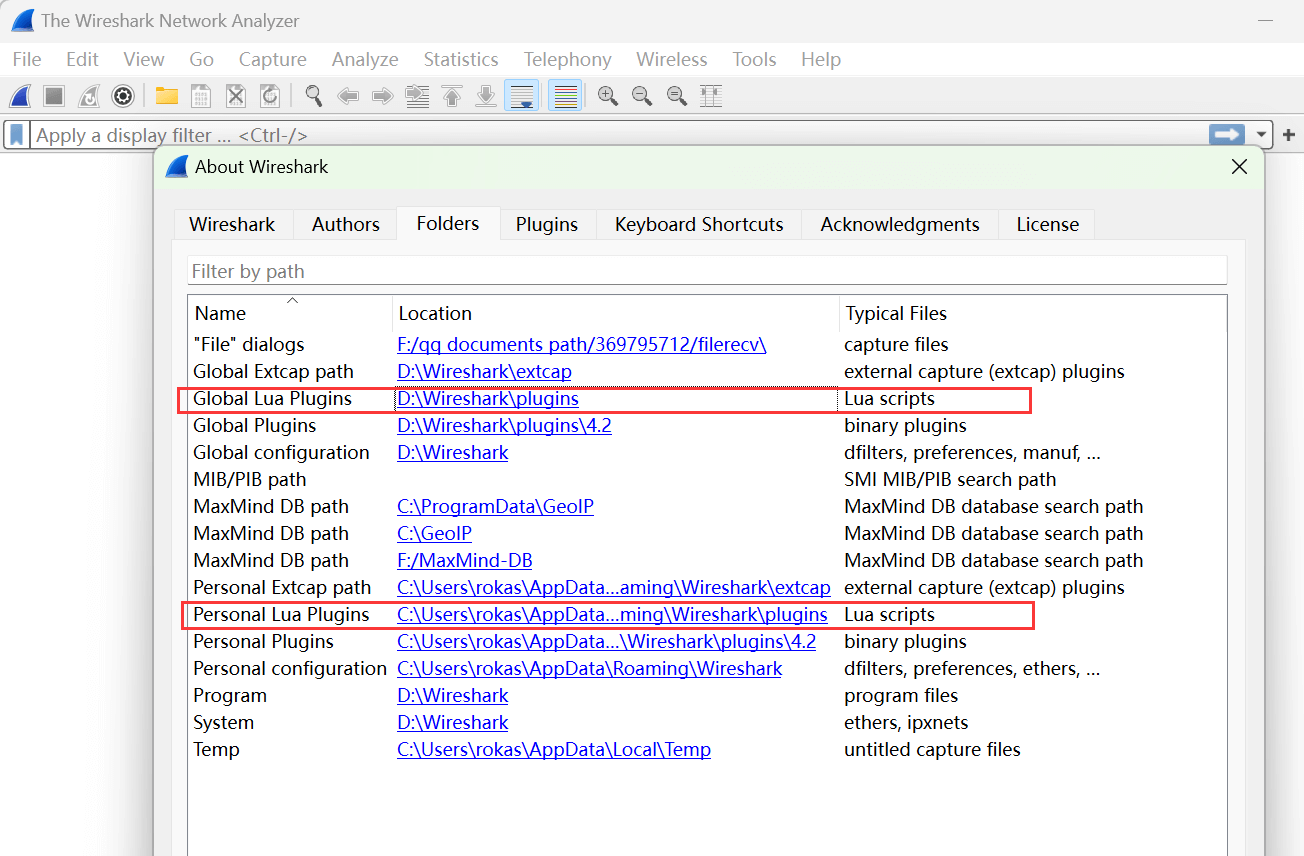
In the installation section of this article, there is a download link. After downloading the script locally, click Wireshark’s Help –> About Wireshark –> Folders to find the Lua plugin directory. It can be either the global Lua plugin directory or the personal Lua plugin directory:
Place the pcapdroid.lua plugin script in one of the above directories and reload the packets.
Then add a column in the edit options, with the field as



