Building an Efficient Snort Network Intrusion Detection System: A Complete Guide to Configuration Files
Published: 2025-01-09 09:43:09
Reading Volume: 21
Subscriber Count: 12

“Snort+Base – A Common IDS Solution for Building Intrusion Detection Systems.docx”
Download Now
Snort+Base is a popular solution for building Intrusion Detection Systems (IDS), where Snort serves as the core detection engine, and Base is an efficient PHP-based Snort analysis and query system. Below is a detailed introduction to Snort+Base:
### I. Overview of Snort
#### 1.1 Definition and Background
Snort is an IDS (Intrusion Detection System) software developed by the American company Sourcefire and released under GPL v2. Since its development in 1998 by Martin Roesch using the C programming language, Snort has evolved into a powerful network intrusion detection/prevention system (NIDS/NIPS) with features such as multi-platform support, real-time traffic analysis, and network IP packet logging.
Snort supports various operating systems, including Windows, Linux, Solaris, and more. The source code and installation packages are available on the Snort official website.
#### 1.2 Working Modes
Snort operates in three main modes: Sniffer, Packet Logger, and Network Intrusion Detection System (NIDS) mode.
– **Sniffer Mode**: This mode only captures packets from the network and displays them continuously on a terminal.
– **Packet Logger Mode**: This mode logs packets to disk.
– **NIDS Mode**: This mode analyzes network traffic to match user-defined rules and takes appropriate action based on detection results.
### Detailed Analysis of Building an Intrusion Detection System with Snort+Base
#### I. Overview of Snort
##### 1.1 Definition and Background
Snort is a powerful IDS software developed by Sourcefire and released under the GPL v2 open-source license. Written by Martin Roesch in C in 1998, Snort has grown to become a comprehensive intrusion detection/prevention system (NIDS/NIPS) with cross-platform compatibility, real-time traffic analysis, and network IP packet logging capabilities. It supports various operating systems, including but not limited to Windows, Linux, Solaris, etc., and its source code and installation packages are available on the Snort official website.
##### 1.2 Working Modes
Snort offers three primary working modes:
– **Sniffer Mode**: This mode mainly listens to network packets and displays them as continuous data streams on the terminal, allowing users to view network communications in real-time.
– **Packet Logger Mode**: In this mode, Snort logs packets to the disk for post-analysis and review.
– **Network Intrusion Detection System Mode**: This is one of Snort’s core and most complex modes. In this mode, Snort analyzes network traffic and matches it against predefined rule sets. Upon detecting suspicious behavior or conditions that meet preset rules, Snort takes corresponding actions such as triggering alerts or executing specific operations.
##### 1.3 Key Features
Snort’s main features include but are not limited to:
– Real-time communication analysis and packet logging
– Payload inspection
– Protocol analysis and content matching queries
– Detection of buffer overflows, stealth port scans, CGI attacks, SMB probes, OS intrusion attempts, etc.
– Real-time alerts to system logs, specified files, Unix sockets, or via Samba’s WinPopup
##### 1.4 Plugins and Extensions
Snort supports various forms of plugins, extensions, and customization options, including database or XML logging, small frame detection, and anomaly detection statistics, significantly enhancing Snort’s flexibility and adaptability.
#### II. Overview of Base
##### 2.1 Definition
Base (Basic Analysis and Security Engine) is an efficient PHP-based Snort analysis and query system widely used for visual analysis and querying of Snort logs.
##### 2.2 Features
Base provides users with an intuitive interface to view and analyze Snort-generated log files, helping users better understand detected security events and respond promptly.
#### III. Setup and Application of Snort+Base
##### 3.1 Setup Environment
– **System Environment**: Choose Windows or Linux systems based on actual needs. Considering performance and functionality, Linux systems (such as CentOS, Fedora, Red Hat, etc.) are often better choices.
– **Software Environment**: Besides Snort and Base, you may also need to install other supporting software, such as WinPcap (for Windows), DAQ (for Linux), MySQL (for log data storage), etc.
##### 3.2 Setup Steps
– **Install Snort**: Download and install Snort software according to the chosen operating system, handling any dependency issues that may arise.
– **Install Base**: Download and install the Base system, configuring it to work with Snort.
– **Configure Snort and Base**: Edit Snort configuration files (e.g., snort.conf), set up log output formats and paths, ensuring Base can accurately read Snort-generated log files.
– **Import Rule Files**: Import Snort rule files into the system so Snort can perform intrusion detection based on these rules.
##### 3.3 Application Scenarios
Snort+Base is widely used in various network environments, including campus and enterprise networks, for building intrusion detection systems that monitor network traffic in real-time, promptly detecting and responding to potential security threats.
#### IV. Considerations
– Pay particular attention to the security and stability of the system during the Snort+Base setup process to avoid introducing new security risks.
– Regularly update Snort rule files to ensure the latest security threats can be detected.
– Configure Snort and Base according to the specific network environment for optimal detection effectiveness.
Snort+Base provides a powerful and highly flexible solution for building intrusion detection systems. Through proper setup and meticulous configuration, this combination can effectively protect network environments from security threats.
conf
reassemble`启用了对流量的重组功能。
一个常见的预处理程序是`http_inspect`,它解析和规范化HTTP流量数据,以便进行更详细的检查。以下是一个简单的预处理程序配置示例:
preprocessor http_inspect: global \
iis_unicode_map unicode.map 1252
preprocessor http_inspect_server: server default \
profile all \
ports { 80 8080 3128 } \
inspect_uri_only
**代码解释:**
– `preprocessor http_inspect`: global 定义全局配置选项。
– `iis_unicode_map unicode.map 1252`定义Unicode映射文件,用于处理UTF-8编码。
– `preprocessor http_inspect_server` 定义针对特定服务器的预处理规则,以`profile all`启用所有分析功能,并指定侦测的端口,启用`inspect_uri_only`选项以仅检查URI部分,从而提升性能。
## 4.2 自定义插件和脚本集成
Snort支持通过插件和脚本的扩展来增强其功能。用户可以根据自身需求编写插件或使用脚本来实现特定功能,例如自定义报警处理、日志格式化或数据外发处理。
### 4.2.1 编写和配置自定义插件
自定义插件可以用C/C++语言编写,并通过修改`snort.conf`文件来加载和配置。以下是一个示例,展示如何加载一个假设的自定义插件`custom_plugin.so`。
conf
dynamicpreprocessor directory /usr/local/lib/snort_dynamicpreprocessor/
dynamicpreprocessor file custom_plugin.so
**代码解释:**
– `dynamicpreprocessor directory`定义动态预处理程序插件的存放目录。
– `dynamicpreprocessor file` 指定插件文件名并加载。
### 4.2.2 利用脚本实现报警处理
用户还可以使用脚本来处理和转发Snort生成的报警信息。例如,配置Snort与Python脚本进行集成,生成报警后的延迟处理。在`snort.conf`文件中通过定义输出插件并调用外部脚本来实现:
conf
output alert_unified2: filename snort.alert, limit 128
output alert_exec: /usr/local/bin/alert_handler.py
**代码解释:**
– `output alert_unified2` 设置报警日志格式和文件。
– `output alert_exec` 配置执行脚本路径,当生成报警时调用`alert_handler.py`脚本。
以下是一个简单的Python报警处理脚本示例`alert_handler.py`:
python
#!/usr/bin/env python3
import sys
import smtplib
from email.mime.text import MIMEText
def send_alert(alert_message):
msg = MIMEText(alert_message)
msg[“Subject”] = “Snort Alert”
msg[“From”] = “[email protected]”
msg[“To”] = “[email protected]”
with smtplib.SMTP(“localhost”) as server:
server.sendmail(msg[“From”], [msg[“To”]], msg.as_string())
if __name__ == “__main__”:
alert = sys.stdin.read()
send_alert(alert)
**功能说明:**
– 脚本从标准输入读取报警信息。
– 创建邮件消息并通过SMTP服务器发送邮件给管理员。
通过自定义插件和脚本,用户可以更精准地定制Snort行为,加强与其他安全工具的集成,从而构建出更灵活、更强大的入侵检测系统。
# 5. Snort在实际环境的部署
## 5.1 部署策略和拓扑设计
在实际环境中部署Snort需要考虑网络拓扑、设备性能和监控范围等因素。可以将Snort部署在以下几个关键位置:
– 入侵防护设备前端:实时监控外部流量,检测和阻止入侵尝试。
– 内网关键节点:内网隔离区流量监控,防范内部威胁。
– 核心交换机后端:全面监控网络流量,分析全局安全态势。
以下是几个常见的部署策略:
### 5.1.1 单点模式
单点模式通常用于小型网络或特定位置的监控。会在网络出入口或关键服务器前部署Snort,单点集中的监控特定流量。
### 5.1.2 分布式模式
分布式模式适用于大规模企业或复杂网络。一些重点节点使用独立的Snort实例监控各个子网或区域流量,各实例集中在中心管理系统统一收集和分析警报。
### 5.1.3 混合模式
混合模式结合单点和分布式的优点,将Snort部署在关键区域和核心交换机位置来监控全网流量,同时根据需要在特殊位置部署额外实例,保证优化的网络覆盖和安全监控。
## 5.2 性能调优和故障排除
为了确保Snort在大型网络环境中高效运行,性能优化和故障排除是必要的步骤。
### 5.2.1 性能优化技巧
1. **规则优化**: 定期审查和调整规则集,移除冗余或产生误报的规则,增大匹配效率。
2. **硬件优化**: 使用专有的高速网卡和硬件加速技术,如PF_RING或DAQ,提升数据包处理能力。
3. **预处理程序调整**: 调整或禁用不必要的预处理程序,减少不必要的CPU和内存消耗。
4. **多线程与分布**: 利用多线程和分布式部署技术,提升并行处理能力和整体吞吐量。
### 5.2.2 常见问题与解决方案
1. **高误报率**: 通过调试和调整规则,使用白名单和漏斗保护技术,分离合法流量和威胁。
2. **性能瓶颈**: 分析系统资源使用情况,通过优化规则和硬件升级,减轻CPU和内存负载。
3. **数据丢包**: 调整捕获和缓冲参数,确保及时处理高流量下的数据包。
4. **配置错误**: 定期检查配置文件及其更新状态,使用语法检查工具减少误操作。
# 6. Snort未来发展与社区贡献
## 6.1 未来发展方向
未来Snort的发展将围绕以下几个方向:
1. **人工智能与机器学习**:集成AI和ML技术,帮助构建基于行为分析的动态检测模型,提高检测的准确性和效率。
2. **自动化与编排**:将Snort集成到自动化编排平台,实现威胁检测和响应流程的高度自动化,简化操作管理。
3. **边缘计算**:将检测和分析能力延伸到边缘设备,满足IOT和边缘应用的安全需求。
4. **增强可视化**:利用高级数据可视化工具,提供直观的网络安全态势感知,帮助运维人员掌握实时安全状态。
### 6.2 社区贡献与合作
Snort作为开源系统,离不开社区贡献和合作:
1. **规则贡献**:鼓励开源社区成员编写和分享高质量的规则集,提升系统整体的检测能力。
2. **开发参与**:开放更加灵活的插件和API接口,允许开发者在Snort基础上开发定制功能。
3. **文档与培训**:提供详尽的文档和培训资源,构建用户知识库,帮助新手用户快速上手和配置系统。
4. **漏洞修复**:及时发现和修复系统漏洞,确保Snort的安全性与稳定性。
5. **合作开发**:与其他安全工具和平台合作,构建联合防御体系,提升整体网络安全防护水平。
通过积极参与社区活动和贡献开发,广大技术人员和社区成员可以共同推动Snort的发展,构建更加安全可靠的网络环境。
# 结论
本文深入探讨了Snort网络入侵检测系统的基础知识、安装与配置、规则管理和性能优化。通过合理部署和定制配置,网络管理员能够有效利用Snort提升网络安全防护能力。同时,借助社区力量和未来技术发展,可以持续增强Snort检测系统的功能和适应性,构建更加智能、高效的安全防护体系。
`$EXTERNAL_NET any (msg:”Possible HTTP attack detected”; flow:to_server,established; content:”/malicious/path”; sid:1000001; rev:1;)`
In this example, the rule monitors incoming TCP traffic to port 80 on the internal network (`$HOME_NET`). If a connection is directed towards the server and contains the specific content “/malicious/path,” an alert will be generated. The `sid` (Signature ID) and `rev` (revision) parameters uniquely identify and track this rule.
### 4.2.2 Anomaly-based Detection Customization
Anomaly-based detection can be customized to identify deviations from normal traffic patterns. This method is slightly more complex as it often involves profiling regular network behavior and setting thresholds for triggering alerts when anomalies are detected.
A sample configuration might involve monitoring DNS queries:
conf
preprocessor dns: ports { 53 5353 }
preprocessor frag3_engine: policy windows detect_anomalies
In this configuration, the `dns` preprocessor will monitor DNS traffic on the specified ports, while `frag3_engine` is set to use the Windows policy and to detect anomalies specifically.
### 4.2.3 Integration with Threat Intelligence
Integrating Snort with threat intelligence feeds can further enhance detection capabilities by incorporating known malicious IPs, domain names, and patterns into the custom rules.
conf
include $RULE_PATH/threatintel.rules
By including a dedicated `threatintel.rules` file that is regularly updated with the latest threat data, Snort can be kept current with dynamic threats, improving proactive detection capabilities.
## Conclusion
Implementing and customizing Snort’s configuration and rule sets require a deep understanding of the network environment and potential threats. Leveraging Snort’s modular preprocessor and output plugin functionalities, alongside specialized custom rules and threat intelligence integration, can significantly enhance the robustness and effectiveness of an intrusion detection system.$EXTERNAL_NET any (msg:”WEB-MISC Potential Exploit”; flow:to_server,established; content:”/bin/sh”; depth:10; nocase; sid:10000001; rev:1; classtype:web-application-attack;)
In this example, `alert tcp` specifies the protocol and action type; `$HOME_NET` and `$EXTERNAL_NET` represent the internal and external network IP addresses, respectively; `msg` is used to describe the alert message of this rule; `flow` is used to specify the traffic flow characteristics; `content` is used to specify the content of the packet to detect, and `nocase` indicates case insensitivity; `sid` is the Snort ID; `rev` is the revision number of the rule; `classtype` indicates the type of attack.
### 4.2.2 Integration and Management of Response Mechanisms
Response mechanisms refer to the specific actions the system should take after detecting an attack. These actions can include logging, alerting, and automatically executing certain commands to prevent or mitigate the attack.
For example, you can define a response action through the `react` keyword in the configuration file:
conf
react detection:alert,pass; target:shell,exec:echo “Detected attack”;
The above configuration will execute a shell command for detected alert-level events, such as logging the information to a file named `shell` and executing the `echo` command to output the detected attack information.
When configuring response mechanisms, administrators need to strike a balance between the risk of false positives and false negatives, setting appropriate rules for triggering responses to ensure effective protection without causing unnecessary interference in the production environment.
In the next section, we will explore the deployment strategies and architecture design of Snort in real-world environments, as well as performance tuning and troubleshooting.
# 5. Deploying Snort in Real-World Environments
## 5.1 Deployment Strategies and Architecture Design
### 5.1.1 Comparing Single Node and Distributed Deployments
In modern network security systems, choosing the appropriate Snort deployment strategy is crucial to ensuring the performance and coverage of the detection system. A single-node deployment is suitable for small network environments, being simple to operate, easy to manage, and maintain. In this configuration, Snort runs on a physical or virtual machine, responsible for monitoring the traffic of the entire network segment. However, as the network scale increases and security demands grow, a single-node deployment may struggle to handle large volumes of network traffic and complex attack scenarios.
In contrast, distributed deployment can run Snort on multiple nodes, providing a more flexible and scalable solution for large-scale networks. In a distributed architecture, Snort can be deployed in different parts of the network, such as the boundary, internal segments, and critical server areas. This strategy not only enhances detection capabilities but also improves performance and response speed by processing multiple data streams in parallel. Additionally, distributed deployment can leverage redundancy configurations to provide better high availability.
When implementing distributed deployment, it is important to carefully consider the positioning, roles, and how to effectively manage and synchronize rule sets across the nodes. For example, a centralized rule server can be used to manage rules for all nodes to ensure consistency. Also, data collection and logging mechanisms need to ensure that security events across all nodes can be aggregated and analyzed effectively.
### 5.1.2 High Availability and Load Balancing
With the increasing demand for network service availability, ensuring the high availability of the Snort system becomes particularly important. In high availability deployments, multiple Snort instances work in parallel, able to fail over to each other. This means that even if one node fails, the other nodes can continue to provide service, preventing an interruption in security monitoring. Methods for achieving high availability include:
– **Active/Active Architecture**: Multiple Snort instances run simultaneously, each monitoring network traffic and detection, sharing data storage for state synchronization.
– **Active/Passive Architecture**: A master node handles all traffic, with a backup node taking over if the master node fails. Master and backup nodes can maintain service continuity through heartbeat mechanisms and state synchronization.
To further improve the system’s handling capacity, load balancing technology is widely used in Snort deployments. Load balancers can distribute incoming traffic across different Snort instances, avoiding overloading a single node. When designing a load balancing solution, consider the following factors:
– **Session Persistence**: Ensure that traffic from the same session is always routed to the same Snort instance to maintain session state.
– **Load Balancing Algorithms**: Common algorithms include Round Robin, Least Connections, and Source IP Hash.
– **Failover**: Ensure that traffic can be quickly redirected to other healthy instances when a Snort instance fails.
Here is an example of configuring a load balancer using Nginx:
nginx
http {
upstream snort_nodes {
server node1.example.com;
server node2.example.com;
server node3.example.com;
}
server {
listen 80;
location / {
proxy_pass http://snort_nodes;
}
}
}
In this configuration, Nginx acts as a reverse proxy, forwarding all HTTP traffic hitting port 80 to the `snort_nodes` upstream server group. Such a configuration helps to distribute traffic load and ensures service continuity with Nginx’s failover capabilities.
## 5.2 Performance Tuning and Troubleshooting
### 5.2.1 Monitoring Tools and Performance Indicators
Monitoring tools are indispensable for ensuring the optimal performance of the Snort system. These tools allow administrators to understand the real-time running status of Snort, including CPU and memory usage, as well as the number of connections being processed and the number of warning events. Here are some common monitoring indicators:
– **CPU Utilization**: High CPU usage may indicate the system is processing a large amount of data or that the ruleset is too complex and needs optimization.
– **Memory Consumption**: Monitor the memory usage of Snort processes to ensure it does not exhaust available physical or virtual memory.
– **Rule Matching Speed**: Review the average and peak rate of Snort rule matches to assess rule set efficiency.
– **Packet Drop Rate**: High network traffic that Snort can’t process timely may cause packet drops, which need resolution by hardware resource enhancement or rule optimization.
– **Performance Bottlenecks**: Regularly run performance tests to identify system bottlenecks and optimize configurations affecting performance.
Tools like `top`, `htop`, `nmon` provide real-time performance data for administrators. Additionally, the Snort community offers numerous plugins and extensions to enhance built-in performance monitoring capabilities. For instance, using the `barnyard2` tool allows storing Snort’s output events in a database for subsequent analysis and querying.
Performance tuning is a continuous process, requiring regular assessment of the system’s workload, performance indicators, and security event logs. When performance issues arise, determine whether they are resource constraints or configuration deficiencies. If the issue is resource-related, consider increasing CPU cores, upgrading to higher-performance processors, or adding memory. For configuration issues, review and optimize the current rule set, inspect network configuration, or adjust Snort’s internal parameters.
### 5.2.2 Common Issue Diagnosis and Solutions
Despite Snort being a powerful intrusion detection system, various issues may occur during actual deployment. Below are some common issues and their solutions:
– **Slow Rule Matching**: A large or complex ruleset can slow down Snort’s processing speed. Solutions include optimizing the ruleset, removing unnecessary rules, using more specific matching rules, or enhancing hardware performance.
– **False Positives and False Negatives**: An IDS may misidentify legitimate network activity as attacks (false positives) or fail to detect actual attacks (false negatives). These issues can be addressed by fine-tuning existing rules, creating new custom rules, and adjusting Snort’s alert thresholds and confidence levels.
– **Incomplete Packet Capture**: In some cases, Snort may fail to capture complete network packets due to configuration issues, such as incorrect capture interfaces or network device limitations. Checking and adjusting the capture interface configuration and ensuring Snort has permissions to access the required network traffic are key steps to resolving this issue.
– **Resource Exhaustion**: Long-running Snort instances may consume significant CPU and memory resources, leading to system performance degradation. Monitoring and limiting Snort process resource usage and regular restarting of Snort services to free up memory can help reduce resource consumption.
– **Log Management Issues**: A large number of log files may consume significant disk space and complicate log analysis. Implementing log rotation and periodic deletion of old log files, as well as using log management tools to aggregate and analyze log data effectively can manage log data.
Structured troubleshooting should start from the simplest issues and gradually delve deeper. Tools like `tcpdump`, `wireshark`, and `snort -vd` capture and analyze raw network traffic, aiding in problem diagnosis. In some cases, network traffic capture and analysis may be necessary to determine if packets were corrupted or lost before reaching Snort.
Here is a sample command using `tcpdump` to capture network packets:
bash
tcpdump -i eth0 -w snort.cap
In this example, the `-i eth0` parameter specifies the monitoring interface as `eth0`, and the `-w snort.cap` parameter directs captured packets to the `snort.cap` file. This file can later be analyzed with tools like `wireshark` to help identify network issues.
Following these steps, administrators can ensure Snort’s proper operation and quickly respond to performance issues. Continuous monitoring and tuning are key to Snort’s long-term stable operation amid the evolving network environment and security threats.
# 6. Future Directions and Community Contributions for Snort
## 6.1 Community Dynamics and Contribution Methods
### 6.1.1 Ways to Contribute to Snort Development
As a benchmark for open-source Network Intrusion Detection Systems (NIDS), Snort has a large and active development community. For IT professionals wishing to contribute to Snort development, the following pathways are available:
– **Mailing List Subscription**: Join Snort’s mailing lists like snort-users and snort-dev to stay updated on development trends and engage with community members.
– **GitHub Contributions**: Snort’s source code is hosted on GitHub, where community members can submit pull requests to improve code or create their own branches to develop new features.
– **Documentation Writing**: For new users, writing or enhancing official documentation is a great starting point. This helps the community better understand and use Snort.
– **Attend Conferences and Meetings**: Participating in cybersecurity-related conferences and meetings not only expands your professional knowledge but also provides opportunities for face-to-face interaction with Snort developers and contributors.
– **Report Issues and Feedback**: Reporting issues encountered while using Snort to the community assists developers in identifying and resolving bugs, thereby improving software quality.
### 6.1.2 Community Maintenance and Latest Trends
The Snort community is not only the origin of code but also a hub for knowledge and resources. Community maintenance includes:
– **Code Maintenance**: Ensuring the codebase is updated and secure, timely merging community contributions, and maintaining the software’s vitality and progress.
– **Knowledge Sharing**: Creating and maintaining FAQs, tutorials, and best practices to help new users quickly get started and delve into Snort.
– **Security Research**: Community members continually research new security threats and attack patterns, adding new detection rules and features to Snort.
Recent trends in the Snort community spotlight machine learning and artificial intelligence to improve detection accuracy and real-time capability. Moreover, integrating more sophisticated threat intelligence is also a current hotspot, enabling Snort to adapt more rapidly to emerging threats.
## 6.2 Extending and Integrating with Other Security Tools
### 6.2.1 Integrating with Firewalls and SIEM Systems
Snort is not only a standalone intrusion detection system but also excels in its ability to integrate with other security tools. Below are examples of Snort’s integration with other security tools:
– **Firewall Integration**: Through routing protocols like OSPF and BGP, Snort can integrate with firewall devices to dynamically modify access control lists (ACLs) based on detected malicious traffic, achieving automated threat defense.
– **SIEM Integration**: Integrating with Security Information and Event Management (SIEM) systems allows Snort’s detection results to be analyzed alongside logs and other security event data, providing a more comprehensive security view.
### 6.2.2 Exploring New Intrusion Detection Technologies
As the network environment evolves rapidly, new intrusion detection technologies are continually developing. Below are some new technology directions of interest to the Snort community:
– **Cloud-Native Security**: With the proliferation of cloud computing, cloud-native intrusion detection and defense technologies are becoming a new research field.
– **Microservices Security**: Microservices architecture requires intrusion detection systems to integrate with service meshes and other containerized technologies for fine-grained security control.
– **Artificial Intelligence and Big Data Analysis**: Utilizing AIAs low as 0.47 RMB/day Unlock the exclusive column Buy 1 year, get 3 months free Click to read the next article  Millions of
Millions of
high-quality VIP articles for unlimited learning Tens of millions of
Tens of millions of
high-quality resources for unlimited downloads C-Know
C-Know
Free questions (generative AI product)
0 0
Related Recommendations for IDS Solution

Snort IDS Solution Source Code
Source Code Analysis of the Snort IDS Solution
Implementing an Open Source IDS Solution: Snort Configuration Details and Rule Writing
Snort IDS Solution: Research, Application, and Rule Analysis
Detailed Explanation of the Snort IDS Solution: Sniffing, Recording, and Network Defense
IDS Solution with Snort: A Practical Guide to Rule Analysis and Configuration for Building an Intrusion Detection System
Snort IDS Solution User Manual: Detailed Configuration and Use
Snort3 Common Rule Templates: Building an Efficient Detection System
Constructing Snort Rules: Fundamentals of Intrusion Detection
SW_Sun Wei
Development technology expert Engineering at a renowned technology company, equipped with extensive experience and professional knowledge in the development technology field. He has been responsible for designing and developing multiple complex software systems involving large-scale data processing, distributed systems, and high-performance computing.
Column Introduction
This column provides an in-depth analysis of the Snort Network Intrusion Detection System’s installation, configuration, and application. From basic configuration file parsing to advanced alarm mechanism settings, it offers comprehensive guidance, helping readers construct efficient intrusion detection systems. Additionally, the column explores the deployment of Snort in cloud environments, applications in IoT security, and the extension of Snort functions with custom output plugins. Through in-depth case studies and practical guides, this column provides valuable resources for readers to comprehensively understand Snort and effectively apply it in the field of network security.
Column Directory
Building an Efficient Snort Network Intrusion Detection System: Complete Parsing of Configuration Files
Preview
Detailed Explanation of Snort Alarm Mechanism: Setting Effective Alarm Notifications
Preview
Snort Deployment in Cloud Environments: Detailed Explanation of Virtualization Installation and Configuration
Preview
New Weapon for IoT Security: Case Analysis and Practical Guide to Snort Applications
Extending Snort Functions: Application Scenarios of Custom Output Plugins

The articles are continuously updated, stay tuned~
As low as 0.47 RMB/day Unlock the exclusive column
Buy 1 year, get 3 months free Millions of
Millions of
high-quality VIP articles for unlimited learning Tens of millions of
Tens of millions of
high-quality resources for unlimited downloads C-Know
C-Know
Free questions (generative AI product)
Latest Recommendations

[Practical Application]: Efficient Use of UML Class Diagrams in House Rental Management Systems

# Summary
This article aims to discuss the basics, design principles, and practical applications of UML class diagrams in software engineering. Through a detailed analysis of the definition, composition, and integration of UML class diagrams with other UML models in the context of the house rental management system. 
Duplex Walkie-Talkie Power Solution: Key Points in Ensuring Stable Power Supply

# Summary
Duplex walkie-talkies are essential communication devices that require continuous and reliable power support in various applications. This article first outlines the basic requirements of the walkie-talkie power solution and deeply analyzes the foundational theories of power system design, including the power demands of walkie-talkies, different power types, and optimizing efficiency and power factor. The article then showcases the practical aspects of power design through hardware selection, circuit design, debugging, and testing. Strategies for power management and optimization, such as dynamic power management and energy recovery techniques, are also discussed. 
[Bonfiglioli Inverter Fault Repair Manual]: Ten Key Steps for Quick Resolution of Practical Issues
# Summary
This article delves into the fault diagnosis, rapid repair techniques, and preventive maintenance strategies of Bonfiglioli inverters. It first explains the working principles of inverters and common fault types, followed by theoretical knowledge on fault troubleshooting. Key practices and testing and validation processes for quick repair techniques are introduced. The importance of preventive maintenance strategies and how to perform performance evaluations and continuous improvements post-maintenance are emphasized. Lastly, real fault case analyses are provided to summarize the repair experience and lessons learned, along with an outlook on future developments in Bonfiglioli inverter fault repairs, including the application of emerging technologies and innovation in maintenance service models.
# Keywords
Inverter; Fault Diagnosis; Quick Repair; Preventive Maintenance; Technological Development Trends; Case Analysis
Reference resource link: [Bonfiglioli Inverter ACT201/ACT401 Series Chinese Operation Manual](https://wenku.c 
[Historical Retrospective]: Challenges and Solutions for Installing .NET Framework 3.5 on Older Systems
# Summary
.NET Framework 3.5 is a key version of Microsoft’s .NET platform, noted for its extensive support and rich development features for older systems. However, installing .NET Framework 3.5 on older systems faces numerous challenges, including system compatibility issues, installation source and permission barriers, as well as file corruption and integrity check problems. This article thoroughly explores these issues and their solutions and introduces the details of .NET Framework 
[Guide to Resolving the Greyed Out Run Button in Android Studio]: From Novice to Expert

# Summary
This article provides an in-depth analysis of the greyed out, unclickable run button issue in Android Studio. It first explains the function of the run button and its influencing factors, including its relationship with the build process and project configuration interactions. Then, common methods for diagnosing and resolving these issues are introduced, such as addressing project synchronization problems, device connection compatibility, and clearing build caches. 
[Cadence 17.4 Automation Script Tutorial]: Implement Design Automation and Improve Work Efficiency

# Summary
This article systematically introduces the core concepts, basic syntax, fundamental operations, control flows, practical cases, advanced techniques, and hands-on skills of Cadence 17.4 automation scripts. First, it outlines the importance of automation scripts and elaborates on keywords, command structures, variables, and data types of the scripting language. Next, it illustrates basic operations through specific examples of file operations, data processing, and control flows. Further, practical cases demonstrate automation design processes, data collection, and report generation, along with user interaction and error handling techniques. In advanced scripting techniques, data 
Coding Optimization Secrets: Eight Code Tips for Beginners to Grow into Programming Experts

# Summary
This article deeply explores the importance of coding optimization, focusing on the art of code clarity, algorithm and data structure optimization, code review, and error prevention, along with advanced code optimization techniques. It emphasizes the significance of comments, naming conventions, and code formatting in enhancing code readability, and analyzes how to select appropriate data structures and algorithms to improve software performance. The article also discusses code review processes, test-driven development (TDD), and static code analysis tools in ensuring code quality and error prevention. Lastly, performance analysis tools, parallel programming practices, and techniques for building maintainable and scalable code architectures are introduced. 
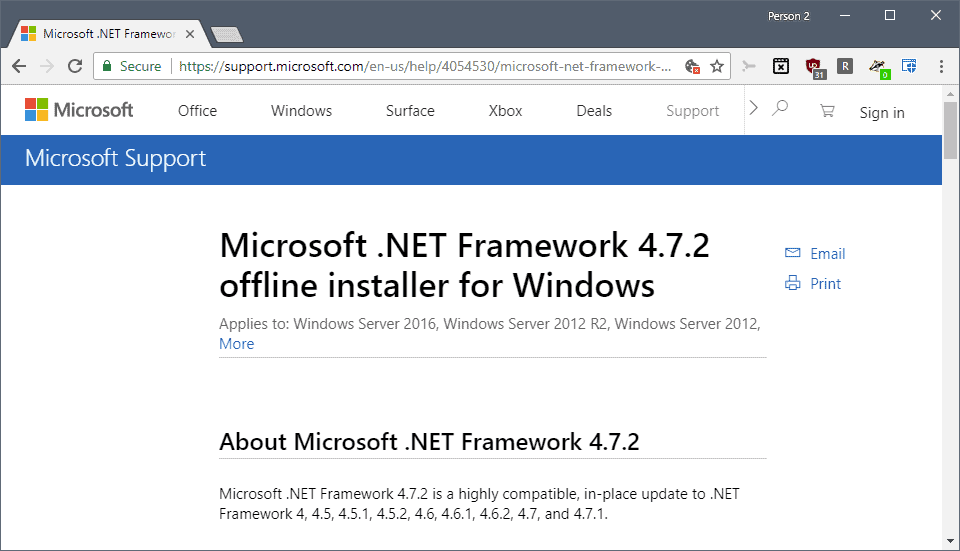
ASIO4ALL_v2 Complete Installation and Configuration Manual: Avoid Common Traps, Ensure Perfect Sound Quality
# Summary
ASIO4ALL_v2 is a popular audio interface adapter that offers extensive compatibility and enhanced control options for audio devices on the Windows platform. This article first outlines the basic concepts of ASIO and ASIO4ALL_v2 and their significance in various application domains. Following this, the article details the installation steps, basic and advanced configurations, and how to optimize and avoid common pit 
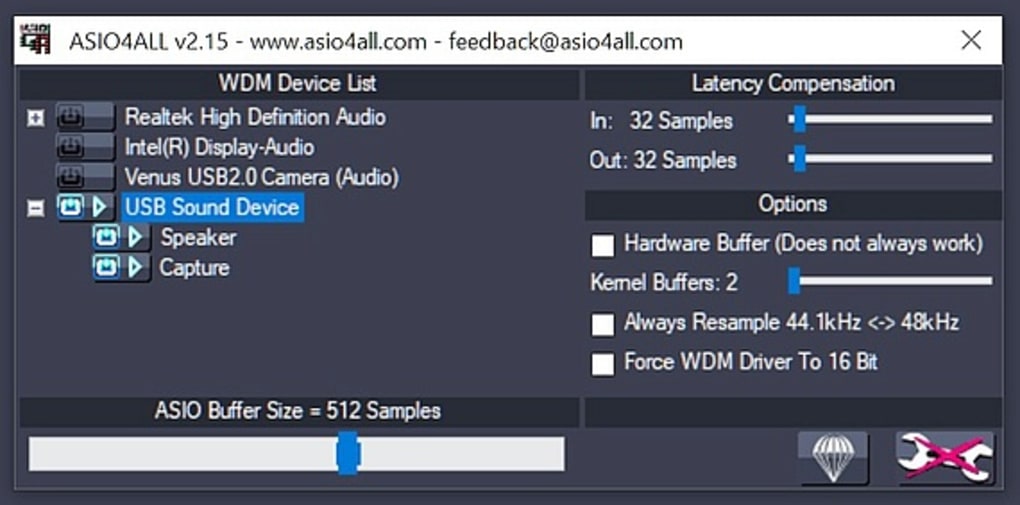
[Coding Standards in Software Development]: BIG5 Encoding Case Analysis and Practical Application
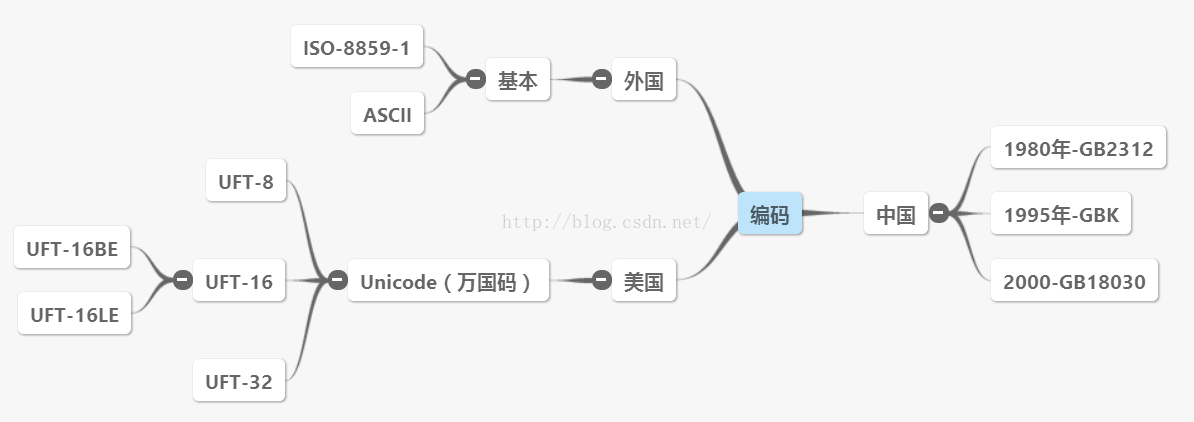
# Summary
This article systematically explores the role, importance, and challenges of implementing coding standards in software development along with best practices. It starts with an overview of the concept of coding standards and their significance in improving code quality, promoting collaboration, and reducing maintenance costs. It then delves into the detailed analysis of BIG5 encoding standards. If you have any questions or suggestions during the resource upload/download, course learning process, feel free to provide valuable feedback. We’ll address it promptly!
Click here to give feedback

Column Directory
Building an Efficient Snort Network Intrusion Detection System: Comprehensive Analysis of Configuration Files
Sample Read
Detailed Explanation of Snort Alert Mechanism: Setting Up Effective Alert Notifications
Sample Read
Snort Deployment in Cloud Environments: Detailed Guide on Virtualization Installation and Configuration
Sample Read
New Weapon in IoT Security: Use Case Analysis and Practical Guide for Snort Application- Extending Snort Functionality: Application Scenarios for Custom Output Plugins

The article is being continuously updated, stay tuned~
As low as $0.47/day Unlock the column
Buy 1 year and get 3 months free Access to millions of high-quality VIP articles for unlimited learning
Access to millions of high-quality VIP articles for unlimited learning Download millions of premium resources at will
Download millions of premium resources at will








