The Windows Registry is a database that stores configuration settings and options for the Windows operating system. It contains information about user preferences, system settings, installed applications, device drivers, and more. Windows Registry forensics involves examining the Windows Registry to obtain valuable information about activities and user behavior on a Windows operating system. It provides important clues about malware activity, user actions, system changes, and more. The Registry Editor is a tool used to view and modify the Windows Registry.
Registry Editor: Registry Structure
Press Win + R to open the Run dialog and type regedit to open the Registry Editor.
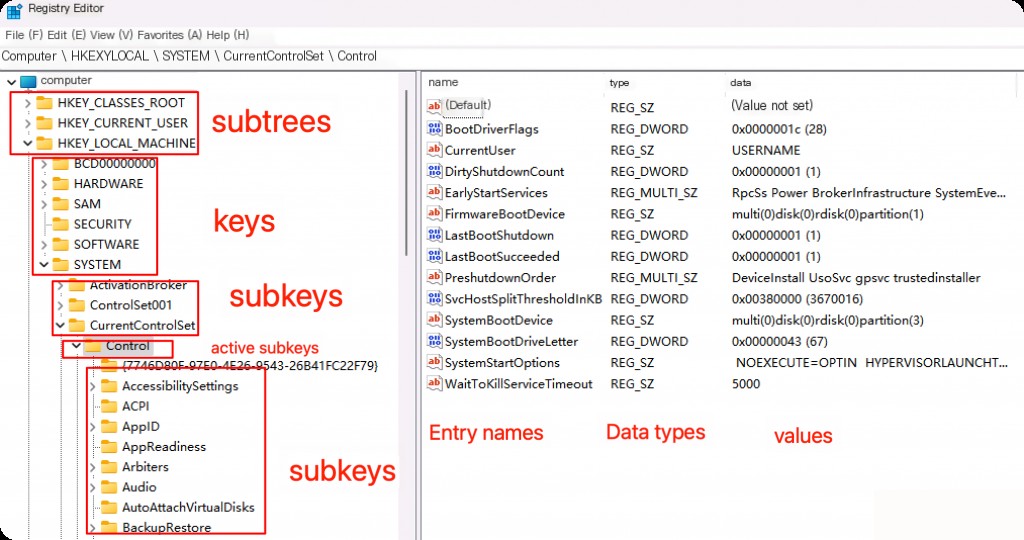
Each key in the registry can contain various values, which are the actual data stored in the registry. These values are organized into name-value pairs, where the name identifies the value, and the value contains the actual data.
For example, a value named “WallPaper” stores the path to the desktop background. Windows loads the background image from the path found in the registry.
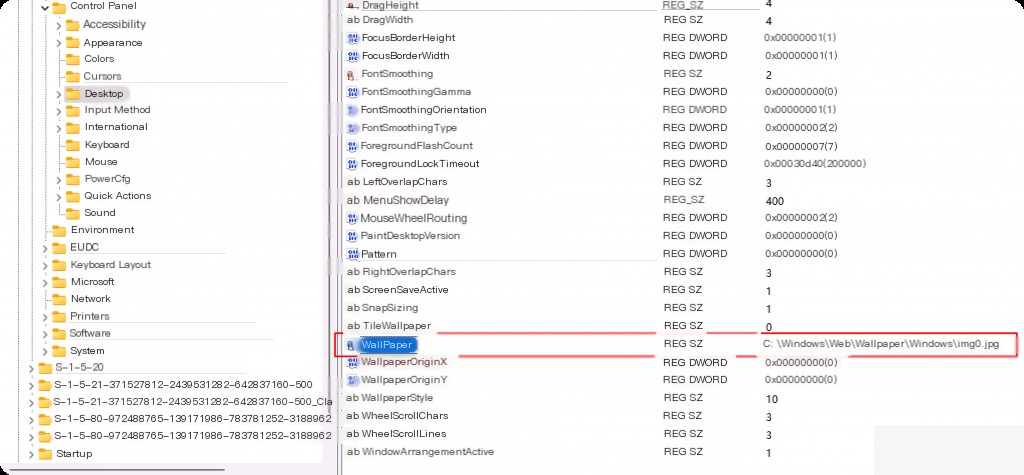
We see that the value named “WallPaper” is “C:\Windows\Web\Wallpaper\Windows\img0.jpg”. Windows knows to load this image from the registry location as the wallpaper.
Summary of the Registry Editor Structure
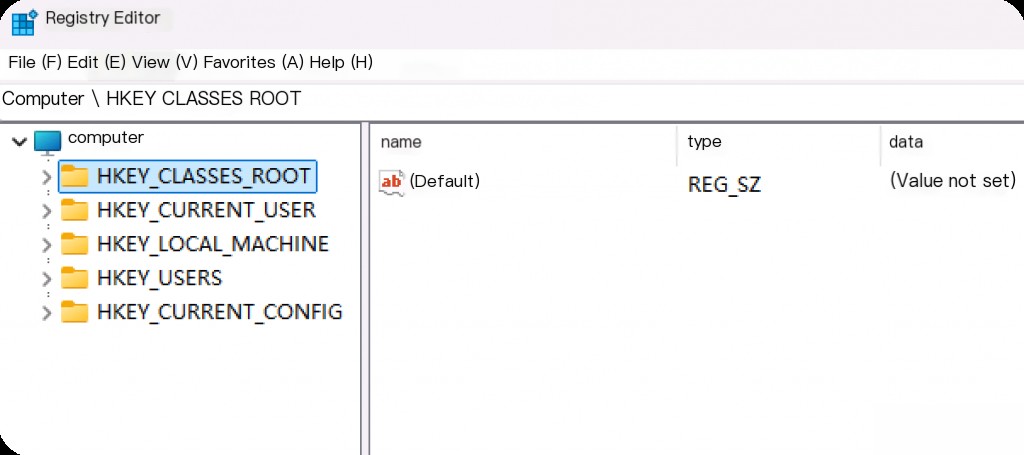
- HKEY_CLASSES_ROOT (HKCR)
Purpose: Maintains records of file extensions and associated applications, helping Windows determine which program will open a file when double-clicked.
Significance: Provides information on how and with which applications files are opened. In some cases, malware may attempt to hide itself by changing file associations.
- HKEY_CURRENT_USER (HKCU)
Purpose: Maintains settings specific to the active user profile, such as desktop settings, browser settings, and user-specific application settings.
Significance: Displays the activities, preferences, and configurations of the active user, including recently opened files, search history, and customized application settings.
- HKEY_LOCAL_MACHINE (HKLM)
Purpose: Contains settings and information common to all users of the system, including hardware configurations, operating system settings, and installed software.
Significance: Includes overall system configuration, installed programs, system-wide security policies, and services that run at startup. This area may reveal general changes made to the system by malware or users.
- HKEY_USERS (HKU)
Purpose: Contains settings for all user profiles. HKCU is essentially a subkey view associated with the SID of the active user under HKU.
Significance: Allows examination of settings and preferences for all users on the system. If there are multiple user profiles, this section can be checked for each user.
- HKEY_CURRENT_CONFIG (HKCC)
Purpose: Contains information specific to the system’s current hardware configuration. The registry hive is a view of the current hardware configuration details, typically located under HKLM.
Significance: Contains settings for the system’s current hardware configuration, screen resolution, etc. It can be used to detect hardware changes made to the system.
Registry Hives in the Registry Editor
Root keys are supported by registry hives that contain the actual registry data. Hives are logical groups of keys, subkeys, and values in the registry. For example, in HKLM, the following important hives are located at “C:\Windows\System32\Config\*”.
- DEFAULT Hive: Contains default settings for the operating system and applications, used as a template when creating new user accounts.
- SYSTEM Hive: Contains settings for low-level system components such as drivers and services.
- SAM (Security Accounts Manager) Hive: Contains information about user accounts on the local computer, including hashed versions of their passwords.
- SOFTWARE Hive: Contains information about installed programs and their settings.
- SECURITY Hive: Contains security-related settings, such as access control information for system resources.
All these hives, except DEFAULT, are loaded into the HKEY_LOCAL_MACHINE key, meaning we can find the contents of the SYSTEM hive under the HKEY_LOCAL_MACHINE\SYSTEM subkey, the SAM hive under HKEY_LOCAL_MACHINE\SAM, and so on.
Key Registry Editor Entries in Forensics
When performing forensic analysis on Windows, it is crucial to examine certain registry values as they play a key role in identifying user activities, system changes, and potential malware activity. Below is a summary of key registry values to prioritize during Windows forensic analysis and their significance.
Registry data is physically stored in multiple files on the disk. Each of these files represents different parts of the registry hives. SYSTEM, SECURITY, and SAM files are located under the HKEY_LOCAL_MACHINE hive, in the C:\Windows\System32\Config folder.
Security Hive in the Registry Editor
Path: %SystemRoot%\System32\Config\SECURITY
Purpose: The Security hive contains details about Windows OS security policies, access control lists (ACLs), and granted user rights. It also contains audit policies for security-related events and user login information.
Significance: Analyzing the Security hive is used to detect attempts at privilege escalation, changes to security policies, and potential security vulnerabilities. Changes in permissions and security policies may indicate network attacks or malicious activity.
“Registry Editor: SAM Hive”
Path: %SystemRoot%\System32\Config\SAM
Purpose: The Security Accounts Manager (SAM) hive contains user accounts, groups, and hashed versions of passwords associated with these accounts. User logins, usernames, and group memberships are stored in this hive.
Significance: Analyzing the SAM hive is crucial for understanding user accounts, group policies, and user access to the system. It provides insights into the use of potentially weak passwords, unauthorized account creation attempts, and user activities on the system.
System Hive in Registry Editor
Path: %SystemRoot%\System32\Config\SYSTEM
Purpose: The System hive contains general details about the operating system and hardware settings, such as hardware, installed drivers, service startup settings, and boot configuration.
Significance: Analyzing the System hive provides a detailed examination of system and hardware configuration, driver installations, and changes to the startup process. This hive can be used to detect traces of malware, system changes, and potential security vulnerabilities.
Registry Entries for User Activities and Behavior
Startup Programs
Path: HKLM\Software\Microsoft\Windows\CurrentVersion\Run HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Purpose: These keys list programs that automatically run when the system starts.
Significance: Malware often uses these keys as one of the strategies to ensure persistence on the system. These keys provide important information to help detect malicious software or startup programs added by users.
Recently Opened Files
Path: HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Purpose: Retains a list of recently opened files.
Significance: Provides detailed information about user activities and behavior. It shows which files were accessed or executed within a given time frame.
History of Connected USB Devices
Path: HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR HKLM\SYSTEM\CurrentControlSet\Enum\USB
Purpose: Stores the history of USB devices connected to the computer.
Significance: Provides clues about potential security vulnerabilities by showing which USB devices have been connected to the computer and when. It plays an important role in investigating incidents such as data theft and malware infections.
User Profile Creation and Last Login Time
Path: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
Significance: The creation time and last login time of user profiles provide information about when specific users were active on the system. This is especially important when investigating unauthorized access or user activities.
Registry Entries for System and Security Settings
Windows Security Center Settings
Path: HKLM\SOFTWARE\Microsoft\Security Center
Significance: Used to detect events such as the disabling of security software due to system security settings potentially being modified by malware.
Installed Programs
Path: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
Significance: Information about installed programs on the system and their installation and uninstallation details can help gain insights into user activities and potential malware installations. The installation and uninstallation dates of programs can be used to track user changes and software changes on the system.
Registry Entries for Malware Detection
Shell Extensions and Explorer Add-ons
Path: HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects
Significance: Indicates where malware can integrate into the system. By mimicking user interactions or making unauthorized changes, shell extensions and browser add-ons can create an attack vector for malicious activities.
Services and Drivers
Path: HKLM\SYSTEM\CurrentControlSet\Services
Significance: Lists the services and drivers of the system. Malware may hide in this area or disguise itself as legitimate services. The presence of malicious services or drivers can severely compromise system security.


