I. Overview of Snort and NIPS
Snort is a powerful network intrusion detection/prevention system known as NIDS/NIPS, featuring cross-platform, real-time traffic analysis, and network IP packet logging.
1. Operating Modes
Snort operates in three modes: sniffer, packet logger, and network intrusion detection system.
1. Sniffer: The sniffer mode reads packets from the network and displays them continuously on the terminal. 2. Packet Logger: The packet logger mode writes packets to the hard drive. 3. Network Intrusion Detection: The network intrusion detection mode is the most complex and configurable. We can let Snort analyze network data streams to match user-defined rules and take appropriate actions based on the detection results.
When using Snort, the network card is automatically set to promiscuous mode
II. Snort Installation and Download
[The experiment was conducted on a Win7 virtual machine]
For 32-bit systems, WinPcap must be installed when using Snort.
Snort download link: https://www.snort.org/downloads#snort-downloads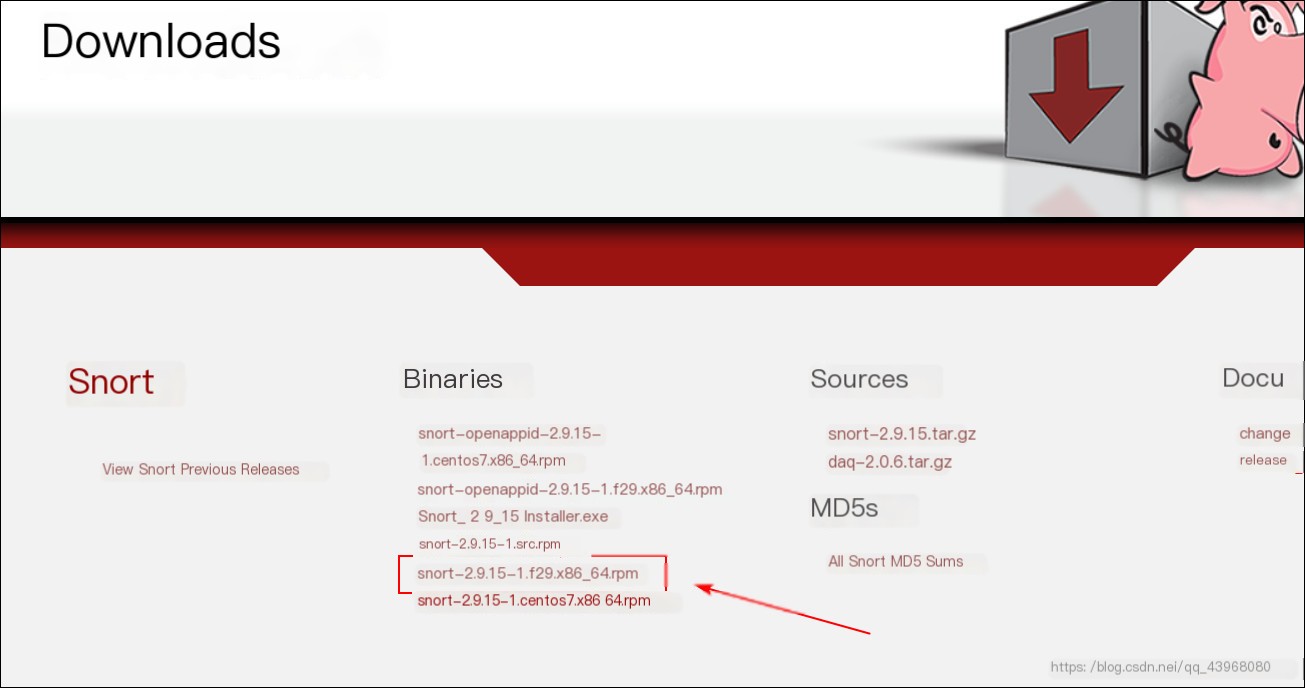 WinPcap download link: https://www.winpcap.org/install/default.htm
WinPcap download link: https://www.winpcap.org/install/default.htm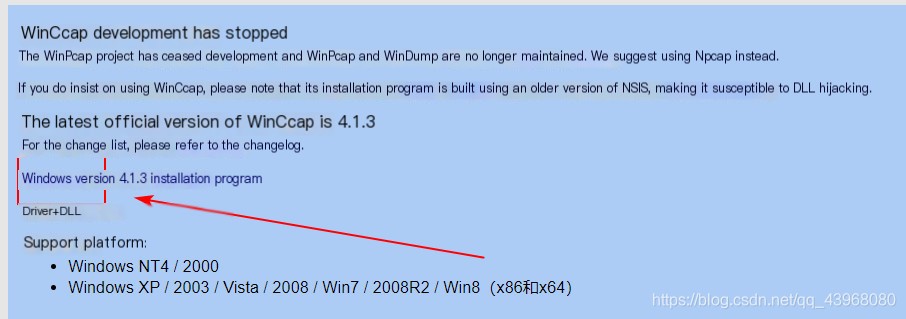
 Install as instructed (strongly recommended to install in the root directory of the C drive for convenience in future experiments)
Install as instructed (strongly recommended to install in the root directory of the C drive for convenience in future experiments)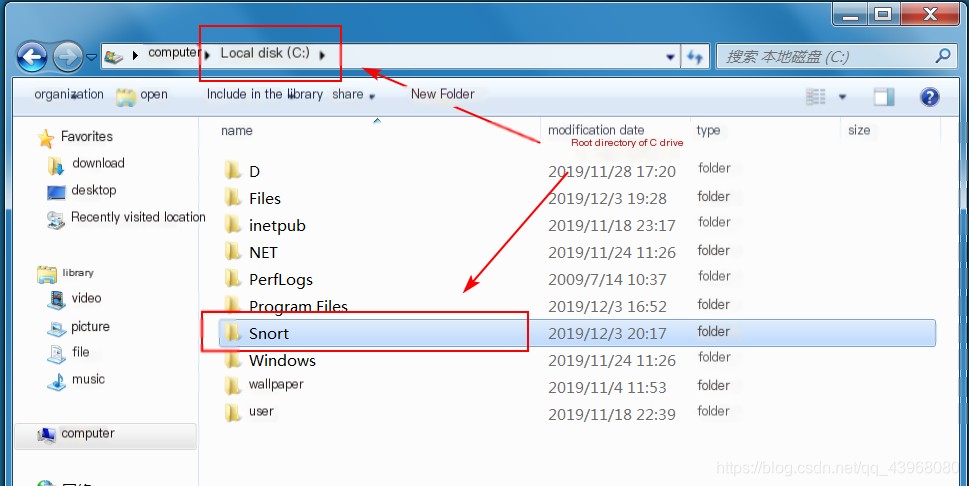
III. Sniffing and Data Logging
1. Sniffing
Open cmd in Snort’s bin directory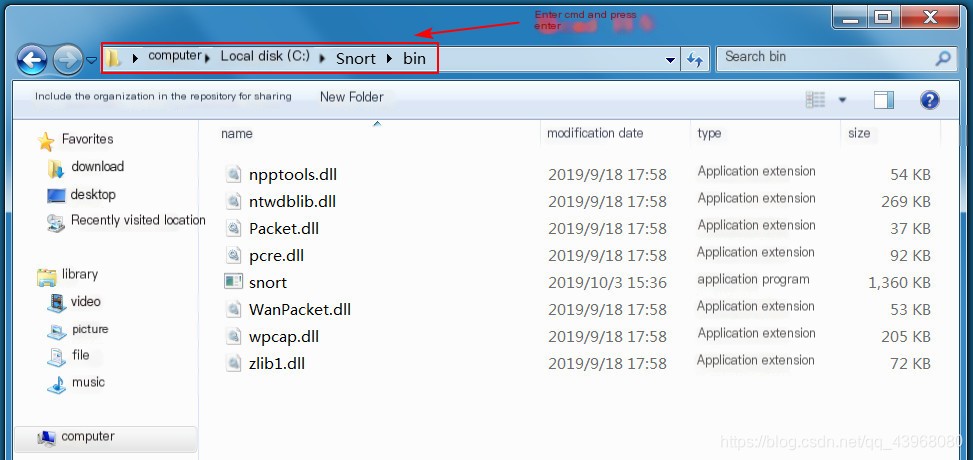 Enter snort -W to view the current network card
Enter snort -W to view the current network card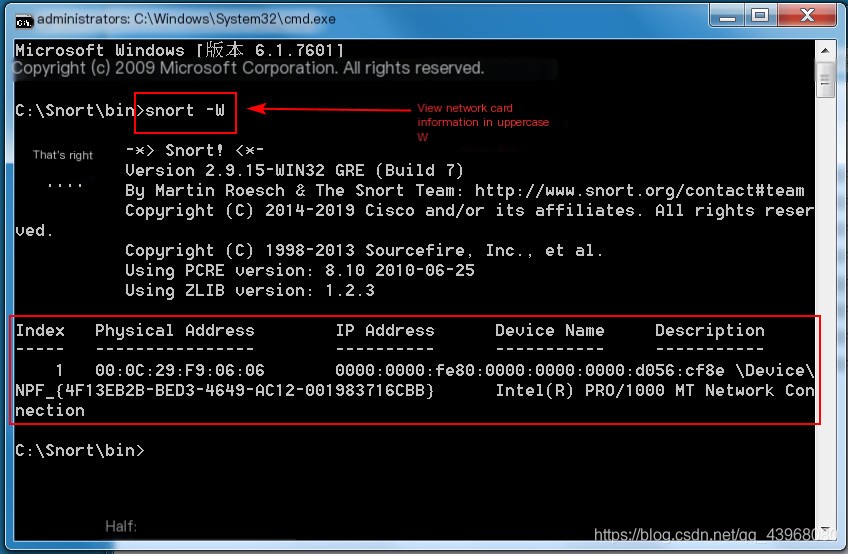 Sniffing network card 1: Snort -v -i1
Sniffing network card 1: Snort -v -i1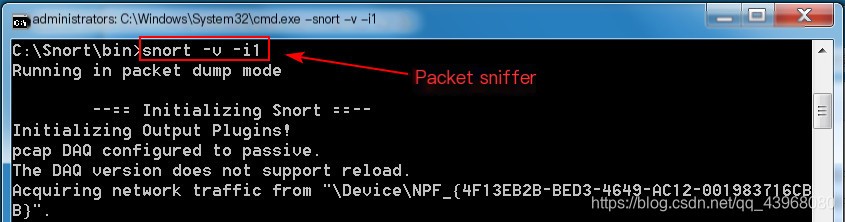 Use another machine to ping this host
Use another machine to ping this host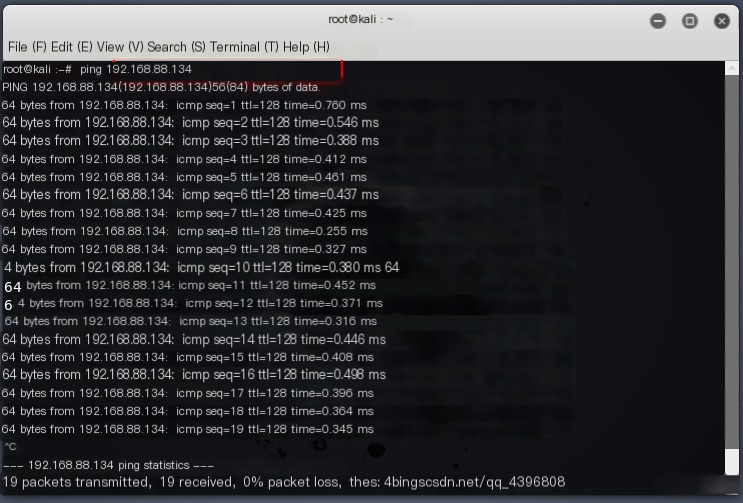 Packets begin to display
Packets begin to display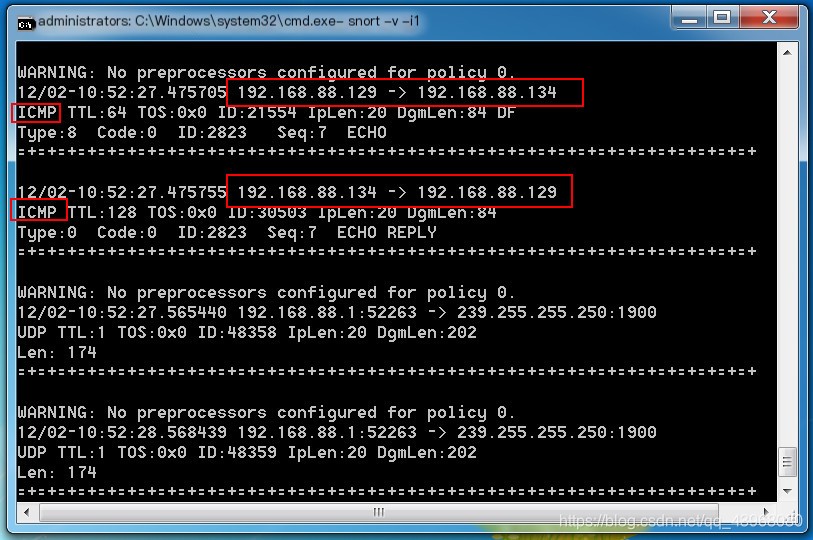 Terminate with ctrl + c, then view packet analysis
Terminate with ctrl + c, then view packet analysis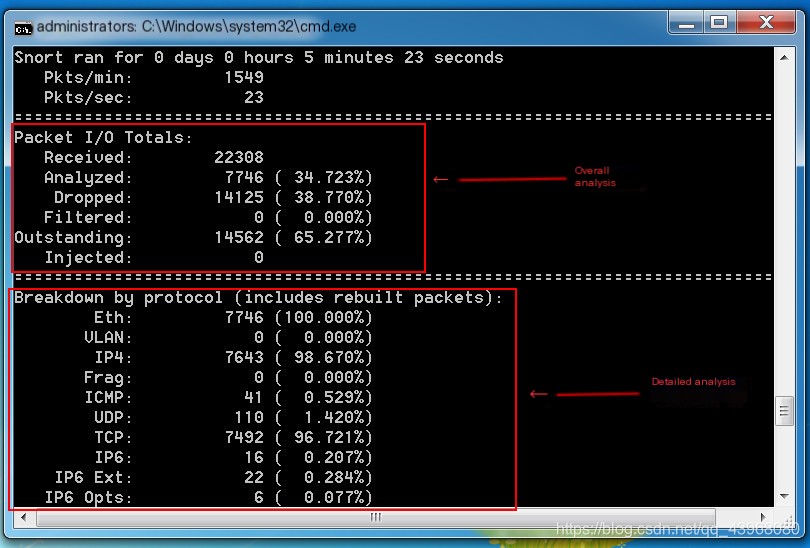
2. Packet Logging
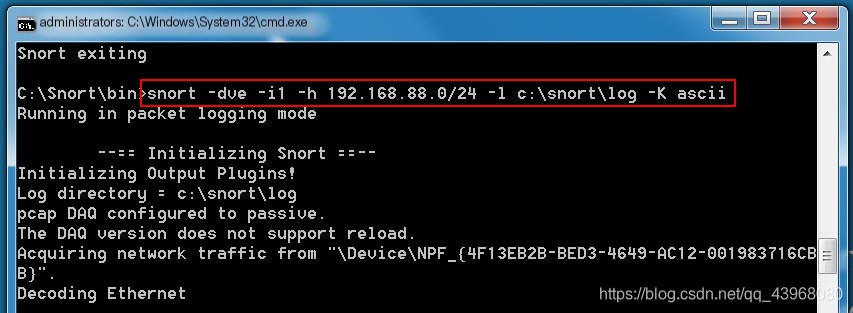
The default log folder in the Snort directory can directly save logs here Use Snort -dve -i1 -h 192.168.88.0/24 -l c:\Snort\log -K ascii to log packets, where
Use Snort -dve -i1 -h 192.168.88.0/24 -l c:\Snort\log -K ascii to log packets, where
-dve indicates verbose sniffing mode -h specifies the monitored host segment; if not specified, it indicates the local IP -l specifies the log storage location -K indicates character set storage in ASCII
 Access any webpage, and capture results are available
Access any webpage, and capture results are available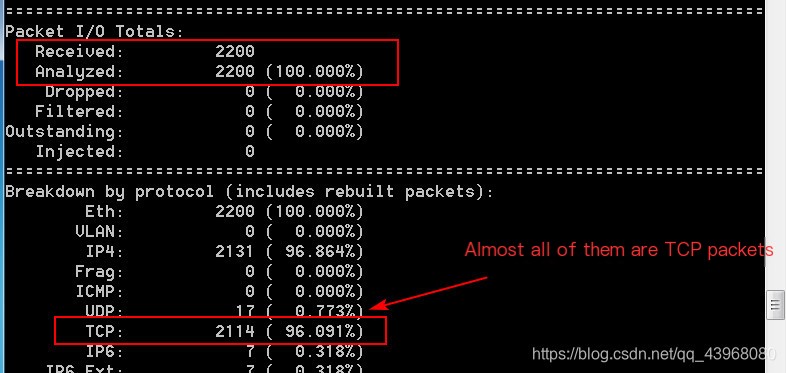
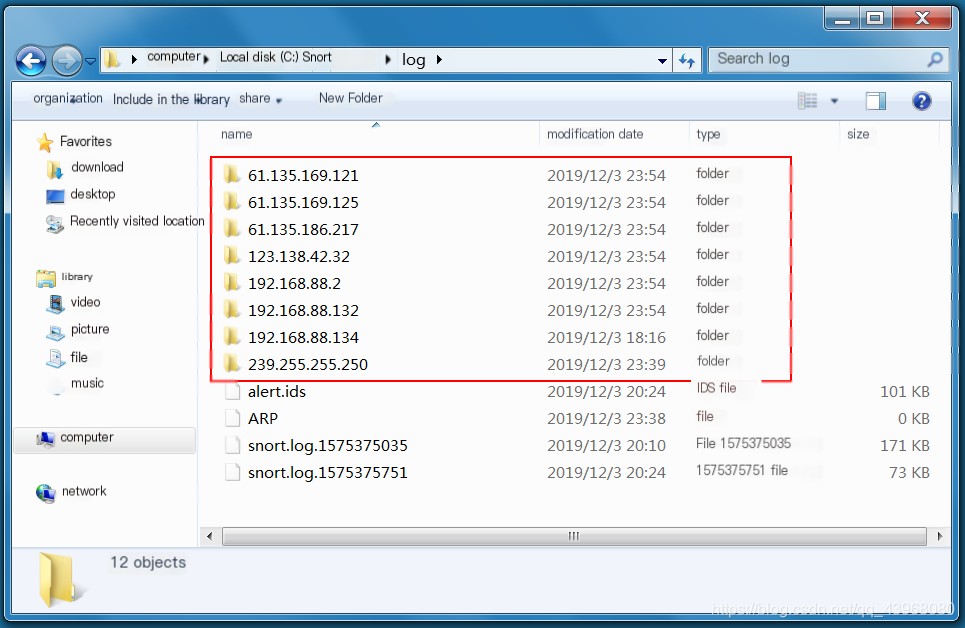 View file content, which is the data header
View file content, which is the data header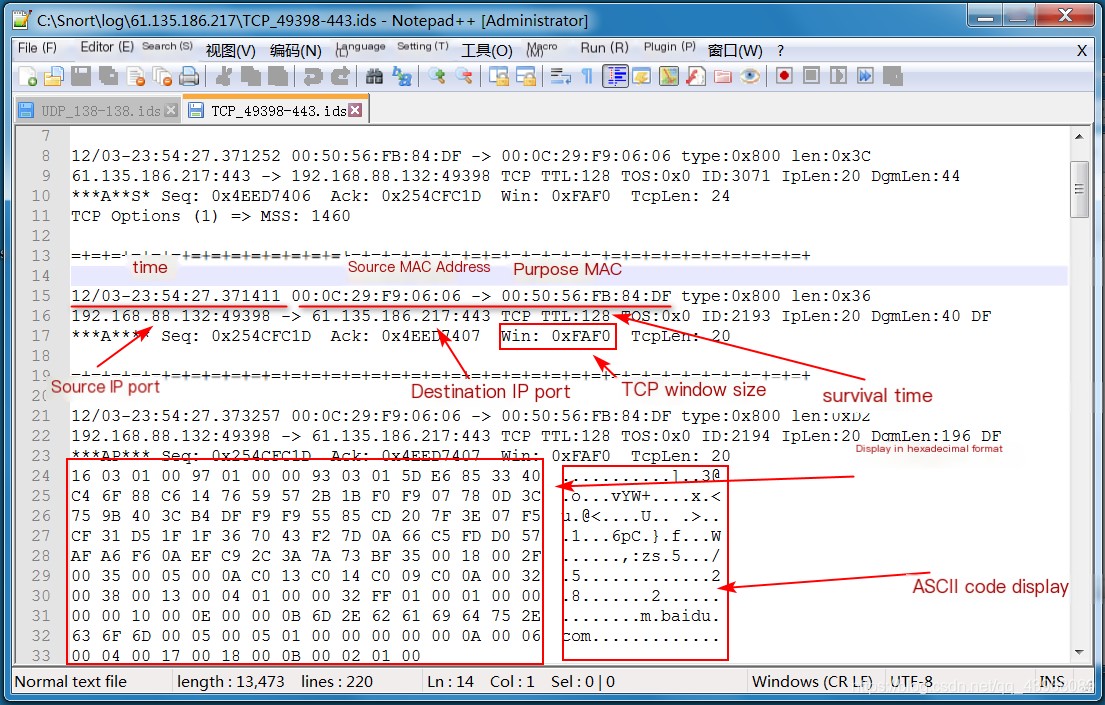 Link:Snort Usage Part Two: Intrusion Detection
Link:Snort Usage Part Two: Intrusion Detection


