1. Introduction to Snort
Snort is an open-source software written in C language and complies with the requirements of the GPL (GNU General Public License).
According to Snort’s official website, it is a cross-platform, lightweight network intrusion detection software.
Snort is a lightweight network intrusion detection system based on Libpcap. It operates on a “sensor” host, monitoring network traffic.
Snort does not require high specifications for the host. The machine can be a repurposed PC running a FreeBSD system, but it must have at least one network interface card. Snort performs pattern matching between network data and rule sets to detect potential intrusion attempts. Alternatively, it can use the SPADE plugin to perform anomaly detection on network data using statistical methods.
Snort employs a modular architecture that is easy to extend, allowing users to add custom modules to enhance its functionality. These modules include HTTP decoding plugins, TCP stream reassembly plugins, port scan detection plugins, FLEXRESP plugins, and various logging input plugins.
The typical operating environment of Snort is shown in the diagram below: 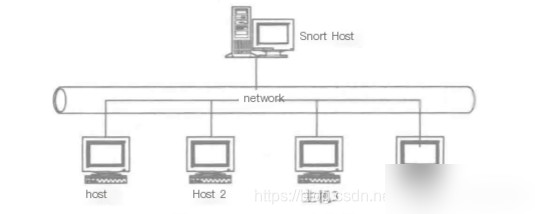
2. Features of Snort
Snort is a powerful and lightweight intrusion detection system with real-time traffic analysis and IP network packet capture capabilities. It can perform protocol analysis and content search/matching. Snort can detect various types of attacks and provide real-time alerts for targeted systems. Additionally, Snort is highly extensible and portable. It adheres to the GPL, allowing any organization or individual to use it as long as they comply with the license.
1. Excellent Cross-Platform Performance
Unlike most commercial intrusion detection software that supports only one or two operating systems—or even requires specific operating systems—Snort is cross-platform and supports a wide range of operating systems.
2. Powerful Functionality
- Snort has real-time traffic analysis capabilities, enabling it to quickly detect network attacks and issue timely alerts. Its alert mechanisms are diverse, including syslog, user-specified files, UNIX sockets, and WinPopup messages sent to Windows clients via the SAMBA protocol.
- Snort can perform protocol analysis, including TCP, UDP, and ICMP.
- Snort’s logging format can be either Tcpdump-style binary format or decoded into ASCII characters, making it easier for users to inspect.
- Using the TCP stream plugin, Snort can reassemble TCP packets. While Snort can match content in IP packets, TCP-based attacks can evade detection if an attacker sends only one-byte TCP packets at a time. The target host’s TCP stack will reassemble these packets and deliver them to the listening process at the destination port, bypassing Snort’s pattern matching.
- With the SPADE (Statistical Packet Anomaly Detection Engine) plugin, Snort can report anomalous packets, effectively detecting port scans.
- Snort also has robust system protection capabilities.
3. Good Extensibility
- As a lightweight network intrusion detection system, Snort has sufficient extensibility. It uses a simple rule description language. The most basic rules include only four fields: action, protocol, direction, and port of interest.
- Snort supports plugins, allowing users to extend its functionality with specific reporting or detection subsystems.
- Snort’s rule language is very simple, enabling it to quickly respond to new network attacks.
- It adheres to the GPL (General Public License).
3. Components of Snort
Snort consists of three critical subsystems: the packet decoder, the detection engine, and the logging and alerting system.
(1) Packet Decoder
The packet decoder primarily parses and preprocesses packets across various protocol stacks to prepare them for rule matching by the detection engine. The decoder operates across protocol stacks, from the data link layer to the transport layer and finally to the application layer.
(2) Detection Engine
Snort stores its detection rules in a two-dimensional linked list, with one dimension referred to as the rule header and the other as the rule options. The rule header contains general attribute characteristics, while the rule options contain specific intrusion characteristics.
To improve detection speed, frequently used destination IP addresses and port information are typically placed in the rule header linked list, while unique detection flags are placed in the rule options linked list.
Rule matching is performed using a recursive search method. The detection mechanism checks the current established linked list options. When a packet matches a rule, the corresponding action is executed.
(3) Logging and Alerting Subsystem
The logging and alerting subsystem can be configured interactively via the command line when running Snort. There are three logging formats and five alerting formats available.
Snort can log packets in either decoded text format or Tcpdump binary format. The decoded format facilitates system analysis of the data, while the Tcpdump format ensures quick disk recording. The third logging option is to disable logging entirely.
Alert information can be sent to the system log, recorded in two formats in alert files, or sent as WinPopup messages via Samba. Alerts recorded in files can use either full or fast formats. Full alerts log both the packet header and alert information, while fast alerts log only part of the header to improve logging efficiency. System log alerts can be monitored conveniently using tools like Swatch. WinPopup alerts can be displayed directly on the Windows desktop. Similarly, the fifth option is to disable alerts entirely.


