Typically, when using tcpdump on Linux to capture packets, you capture a portion of the data packets on the remote Linux machine, then transfer them back to the local machine, and use Wireshark for analysis. This method mainly captures non-real-time data packets and cannot perform real-time data analysis. Additionally, transferring files each time is not very convenient. Therefore, a very detailed introduction to remote packet capture with Wireshark is provided, summarizing three different methods for remote packet capture on Windows, Linux, and Mac.
Local Windows Remote Packet Capture on Linux
Install rpcapd on Linux
rpcapd is a daemon that provides remote traffic capture for the Windows version of the Wireshark protocol analyzer. It is provided with the WinPcap network capture library for Windows but is not available in the libpcap for Linux. Installation requires root privileges.
Install on Ubuntu Linux:
apt-get build-dep libpcap -y git clone https://github.com/rpcapd-linux/rpcapd-linux.git cd rpcapd-linux/libpcap/ ./configure && make cd ../ make
Install on Centos/Fedora/Redhat Linux:
The libcrypt.a in glibc-static is broken, so you need to delete -static from the Makefile in the rpcapd-linux directory before compiling.
yum install -y byacc glibc-static libgcrypt-devel git clone https://github.com/rpcapd-linux/rpcapd-linux.git cd rpcapd-linux/libpcap/ ./configure && make cd ../ sed -i 's/-static//' Makefile make
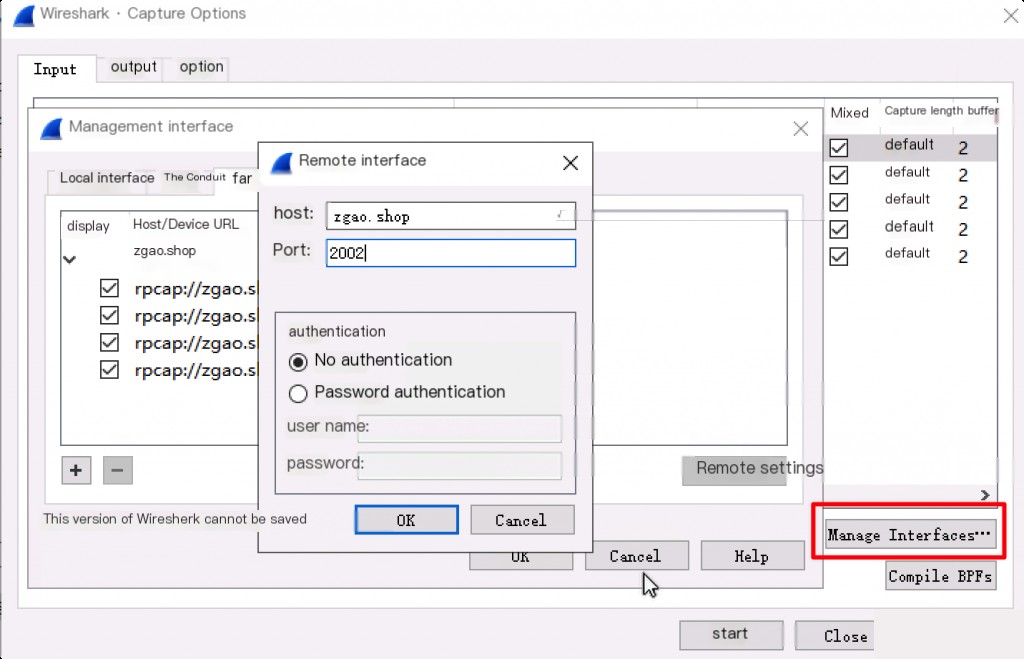
If no port is specified, it listens on port 2002 by default.
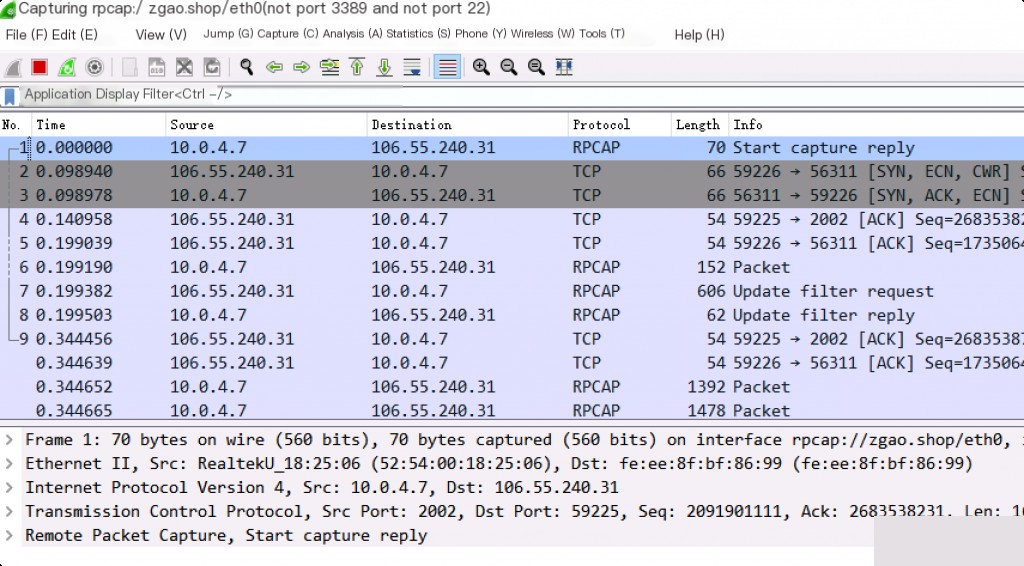
Wireshark GUI Configuration for Remote Interface
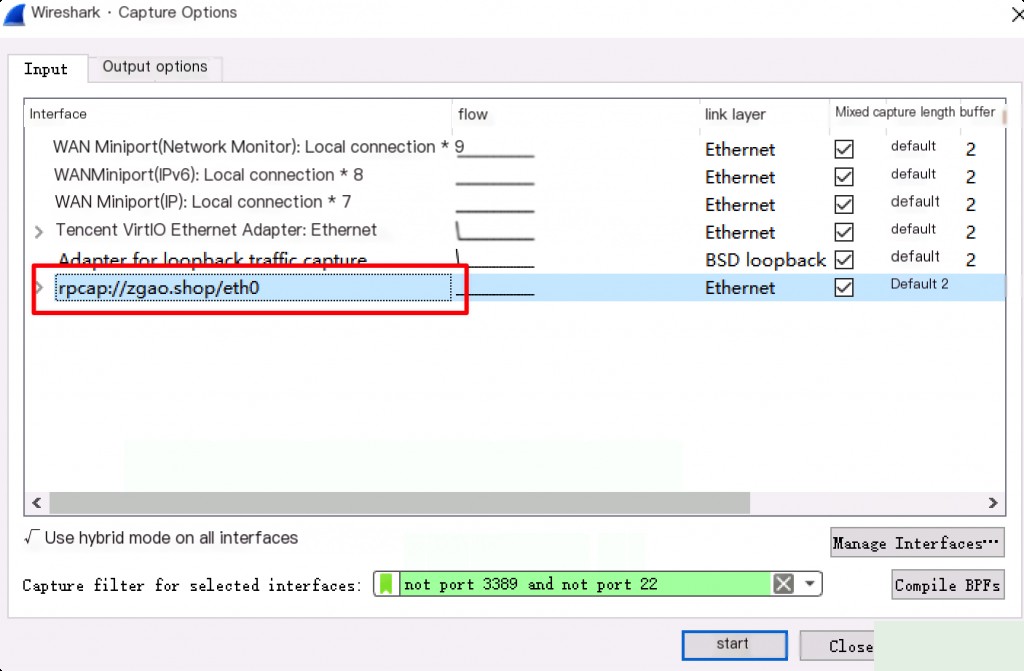
Start capturing packets.
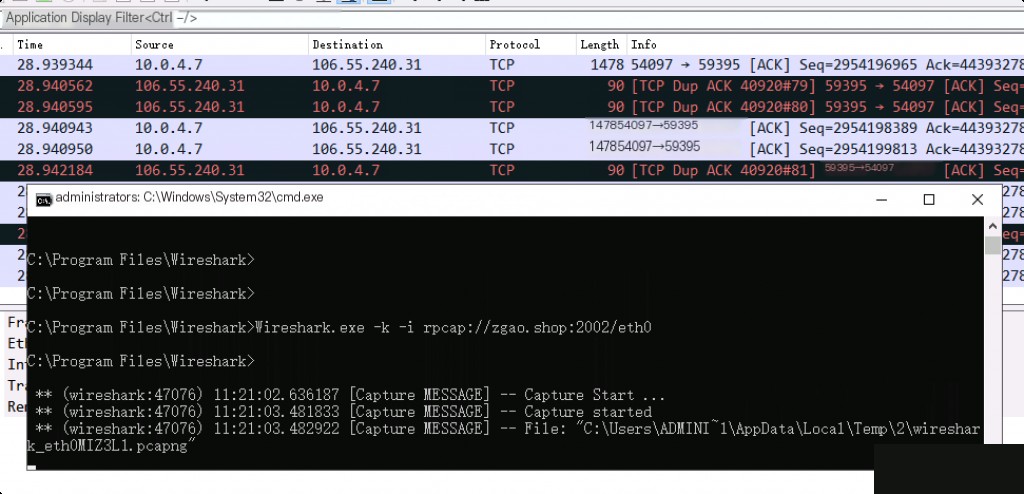
Wireshark Command Line Configuration for Remote Interface
If the Wireshark environment variable is not configured, open the Wireshark installation directory and execute the following command.
wireshark -k -i rpcap://:/
Local Mac Remote Packet Capture on Linux
Local Mac Configuration for sshdump
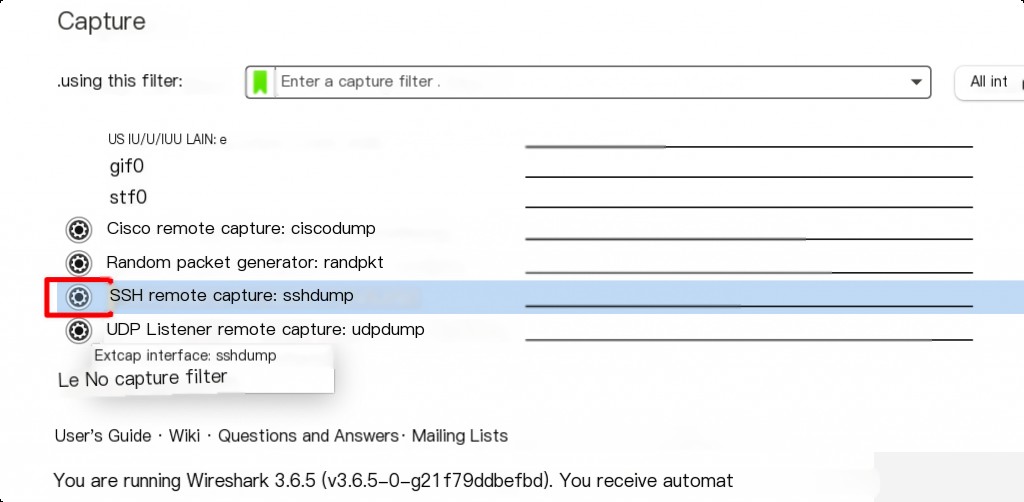
The Wireshark on Windows does not have this option by default, and you need to install the OpenSSH client locally.
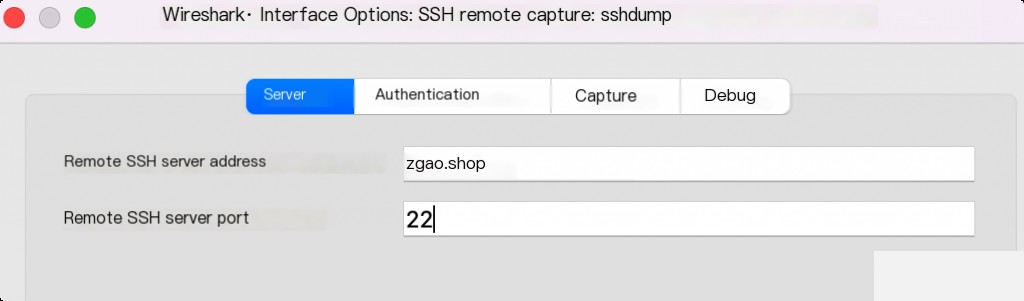
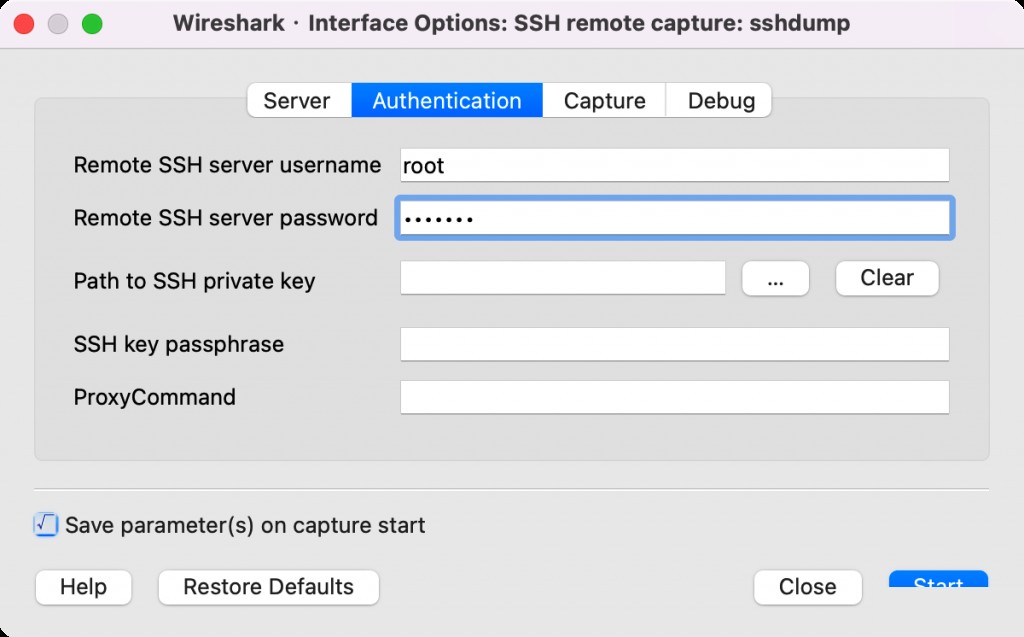
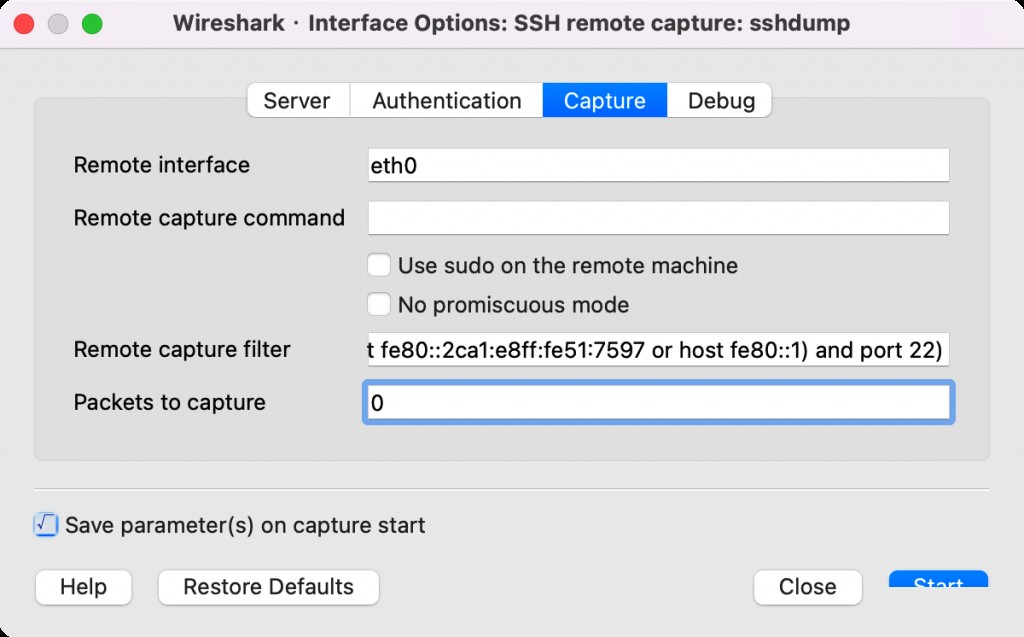
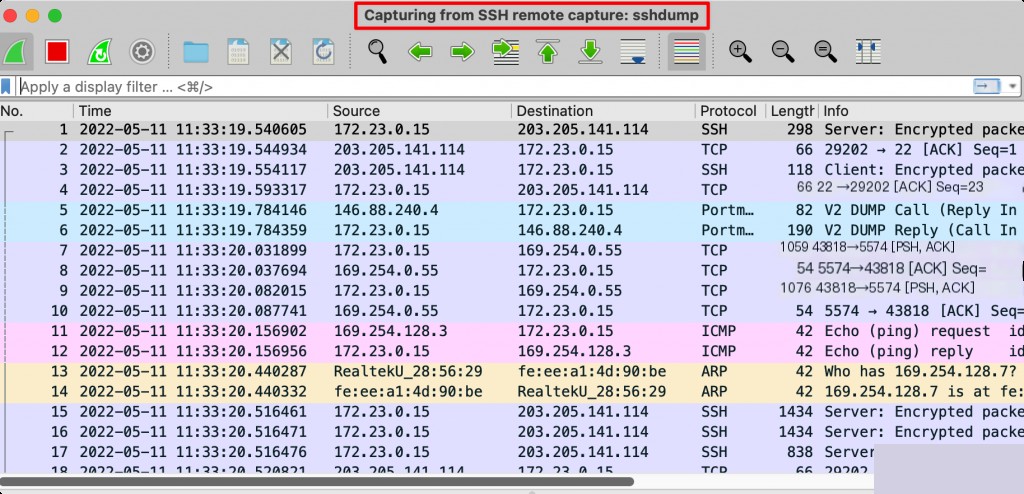 Remote packet capture successful
Remote packet capture successful
Similarly, on Mac, you can also use the above local Windows rpcap method to capture packets.
Remote Packet Capture on Linux Using tcpdump Linux
Local Wireshark Pipe Configuration
Create a pipe file on the local Linux
mkfifo /tmp/sharkfile
Install Wireshark on the remote Linux
yum install wireshark* -y
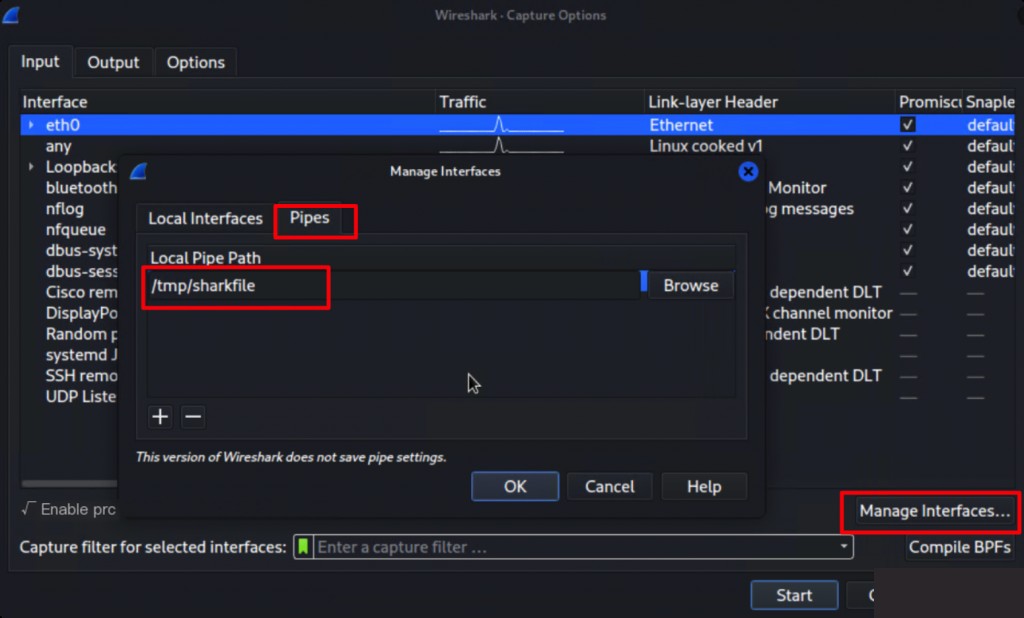
ssh user@remote-host "dumpcap -P -w - -f 'not tcp port 22'" > /tmp/sharkfile
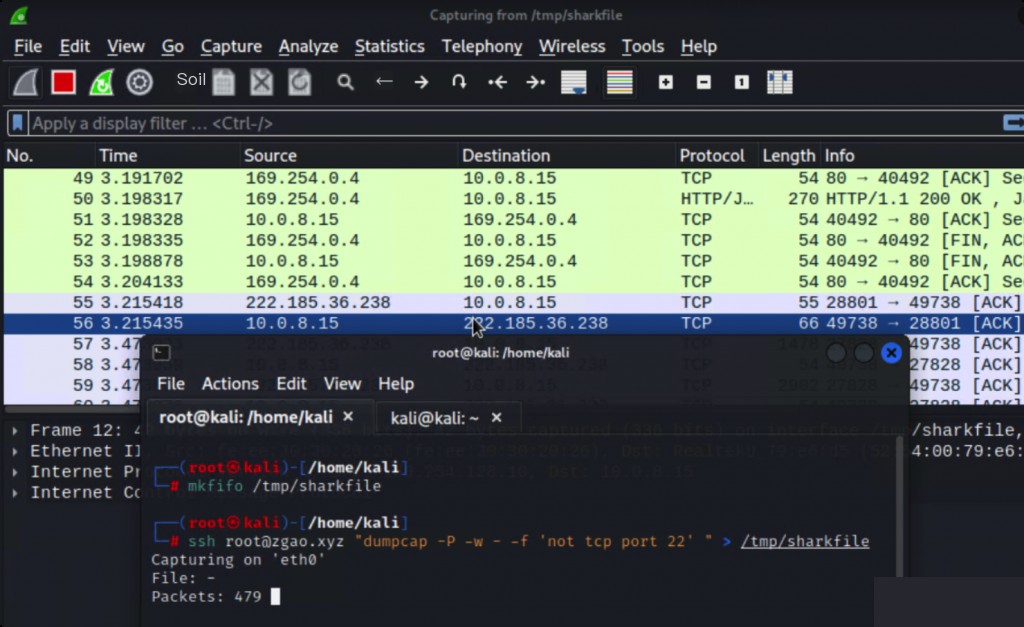 Packet capture successful
Packet capture successful
Similarly, local Linux can also use sshdump and rpcap methods to capture packets.


