Snort: A Commonly Used Intrusion Detection System
Snort is a commonly used open-source intrusion detection system widely used in penetration testing, network security monitoring, and intrusion detection fields. As a penetration testing engineer, understanding the principles, configuration, and usage of Snort is essential. This article will detail the working principles, configuration methods, and usage tips of Snort, hoping to help readers better understand and apply this tool.
I. Working Principles of Snort
The working principle of Snort can be summarized as real-time analysis and detection of network traffic to discover and report abnormal traffic and security events on the network. Specifically, Snort achieves intrusion detection through the following steps:
- Capturing Network Traffic
Snort captures network traffic in real-time through the network interface card (NIC) or network mirroring (SPAN). The captured network traffic can be packets sent from other network devices on the internet or local network packets.
- Analyzing Network Traffic
Snort deeply analyzes the captured network traffic. It can extract and analyze the protocol, source address, destination address, port number, and payload information of the packets. Additionally, Snort can parse and analyze application layer data through an application layer protocol detection engine (ALPD).
- Detecting Security Events
While analyzing network traffic, Snort matches and detects traffic based on predefined rule sets. These rule sets include various types of security events, such as network scanning, malware propagation, and denial-of-service attacks. If Snort detects matching rules, it triggers an alert and logs the relevant information.
- Generating Reports
Snort can generate reports of detected security events and send them to administrators or other security systems. These reports include detailed information such as alert content, event classification, occurrence time, source address, and destination address, helping administrators quickly identify and respond to security threats.
II. Configuration Methods of Snort
The configuration process of Snort is relatively complex and involves several steps:
- Installing Snort
Snort can run on operating systems like Linux and Windows. Before installation, ensure that the system meets Snort’s requirements, such as system memory, processor performance, and network adapters. Installation methods can be found in the official documentation or other related tutorials.
- Configuring the Snort.conf File
The Snort.conf file is the main configuration file for Snort, containing various configuration options and rule sets. Before configuring the Snort.conf file, understand the meaning and function of each configuration option. Common configuration options include:
- HOME_NET: The IP address range of the local network;
- EXTERNAL_NET: The IP address range of the external network;
- RULE_PATH: Path to store rule sets;
- OUTPUT: Alert output methods (console output, file output, Syslog output, etc.);
- PREPROCESSOR: Configuration options for preprocessors.
- Configuring Rule Sets
Snort’s rule sets are the core components for detecting security events. Rule sets can be customized and modified as needed or downloaded and imported from the internet. Understanding the syntax and meaning of various rules is essential before configuring rule sets. Common rule types include:
- Alert Rules: Used to detect security events and generate alerts;
- Log Rules: Used to log security events into log files;
- Pass Rules: Used to allow specific traffic;
- Drop Rules: Used to discard specific traffic;
- Reject Rules: Used to reject specific traffic.
- Starting the Snort Service
After completing the above configurations, you can start the Snort service and begin intrusion detection. Methods for starting the Snort service can be found in the official documentation or related tutorials.
III. Usage Tips for Snort
Snort is a powerful intrusion detection system with many features and advantages. Here are some usage tips and considerations:
- Creating Suitable Rule Sets
Snort’s rule sets are the core of intrusion detection. Creating suitable rule sets is crucial for detecting security events. Penetration testing engineers need to create rule sets that align with system characteristics and security requirements.
- Multiple Alert Output Methods
Snort supports multiple alert output methods, such as console output, file output, and Syslog output. Penetration testing engineers can choose the appropriate output method as needed.
- Monitoring Log Files and Statistical Reports
Snort can log detected security events and generate statistical reports. Penetration testing engineers can understand the network’s security events and attack trends by monitoring log files and statistical reports.
- Regularly Updating Rule Sets
Snort’s rule sets need regular updates to adapt to new security threats and attack methods. Penetration testing engineers need to update the rule sets regularly to ensure effective intrusion detection.
- Using in Conjunction with Other Security Tools
Snort can be used in conjunction with other security tools, such as Nmap and Metasploit. Penetration testing engineers can integrate Snort into the intrusion detection process and use it alongside other tools for comprehensive penetration testing.
IV. Conclusion
As a commonly used intrusion detection system, Snort has many features and advantages. Penetration testing engineers can better address network security threats by understanding Snort’s working principles, configuration methods, and usage tips. In practical applications, it is essential to flexibly use Snort’s various functions and features in conjunction with other security tools for comprehensive penetration testing and intrusion detection.
Bro: A Tool for Network Security Monitoring and Intrusion Detection
Bro is a tool for network security monitoring and intrusion detection developed with funding from the National Science Foundation (NSF) at the University of California, Berkeley. It aims to provide a flexible and efficient network security monitoring solution. This tool has a wide range of applications, such as monitoring network traffic, detecting network intrusions, and providing critical security intelligence in large enterprises, government agencies, financial institutions, and service providers.
The main feature of Bro is its powerful network traffic analysis function. Bro can monitor and record all packets passing through the network and provide a series of functionalities such as protocol parsing, event discovery, content retrieval, and traffic statistics. Bro also supports custom plugins that can extend its capabilities as per specific requirements.
Bro’s architecture employs a distributed design, allowing it to run on multiple machines to achieve higher scalability and performance. The core engine of Bro, known as Bro Core, is responsible for processing all network traffic and converting it into useful events. Bro also comes with several additional plugins like HTTP, FTP, SMTP protocol parsers, and various detection plugins for DDoS attack detection, malware detection, etc.
Bro offers flexible usage methods. Users can write custom scripts using the Bro language to accomplish specific monitoring and detection tasks. The Bro language is a powerful programming language with syntax structures similar to C, which can be used to write complex network traffic analysis scripts. Furthermore, Bro supports other programming languages like Python, Perl, and Lua.
One of Bro’s main application scenarios is penetration testing. Penetration testing is a security testing method that assesses a system’s security by simulating attacks. Bro can monitor the network traffic during penetration testing and detect any anomaly related to the testing process. For instance, if attackers use unknown malware or exploits, Bro can detect these attacks using its built-in malware detection plugin. Additionally, Bro can detect various network attacks like port scanning, brute-force attacks, and SQL injections.
Bro can also be used for network security threat intelligence collection. Network security threat intelligence involves information about potential network attacks that can help organizations better understand security threats and take appropriate measures to protect their networks. By monitoring network traffic and detecting security events, Bro can collect threat intelligence. For example, if Bro detects an unknown malware sample, it can upload the sample to a global malware repository (VirusTotal) for analysis and provide feedback to the user.
It’s important to consider several key issues when using Bro. Firstly, configuring and using Bro requires technical knowledge. Users need to be familiar with network security fundamentals, TCP/IP protocols, and the usage of the Bro language and plugins. Secondly, considering performance and scalability is crucial. Appropriate hardware and network equipment should be selected based on the actual circumstances, and configurations should be optimized accordingly.
In summary, Bro is a powerful network security monitoring and intrusion detection tool with extensive application scenarios. It can monitor network traffic, detect network intrusions, and provide critical security intelligence. Bro plays a significant role in penetration testing and threat intelligence collection. However, using Bro requires technical knowledge and experience, along with considerations of performance and scalability.
OSSEC: An Open-source Host-based Intrusion Detection System
OSSEC is an open-source host-based intrusion detection system designed to provide enterprises with a powerful security monitoring solution. OSSEC can monitor and detect abnormal behavior on hosts, providing real-time alerts and incident response. This tool suits various operating systems, including Linux, Windows, and Mac OS X. In penetration testing, OSSEC can monitor host behavior and detect any anomalies related to the testing process.
The main feature of OSSEC is its powerful log analysis function. OSSEC can monitor various log files on hosts, including system logs, application logs, and security logs. OSSEC performs real-time analysis of these logs and detects any security-related events. It also supports custom rules to expand its capabilities according to specific requirements.
OSSEC’s architecture employs a distributed design, allowing it to run on multiple hosts for higher scalability and performance. The core engine of OSSEC, called the OSSEC Agent, monitors log files on hosts and converts them into useful events. OSSEC includes several additional plugins, such as Windows registry monitoring plugin, Apache web server plugin, etc.
OSSEC offers flexible usage methods. Users can write custom rules using the OSSEC rule language to accomplish specific monitoring and detection tasks. The OSSEC rule language is a powerful programming language with regular expression-like syntax structures, allowing users to write complex log analysis rules. Additionally, OSSEC supports other programming languages like Python and Lua.
In penetration testing, OSSEC can monitor host behavior during the testing process and detect any anomalies related to the test. For instance, if penetration testers attempt brute force attacks to gain access to a host, OSSEC can detect these attacks using its built-in brute force detection plugin. Moreover, OSSEC monitors host files and processes to detect any abnormal behavior.
OSSEC also includes other functionalities such as real-time alerts, incident response, and report generation. It can send alerts to administrators through various methods like email, SMS, and Syslog. OSSEC also provides a web interface for viewing real-time events and generating reports.
Overall, OSSEC is a powerful host-based intrusion detection system capable of monitoring and detecting anomalies during penetration testing. OSSEC has powerful log analysis functions and a flexible rule language, allowing the extension of its capabilities based on specific requirements. Moreover, OSSEC’s distributed design and multiple alert methods offer higher scalability and flexibility.
Additional Thoughts
New entrants to the computer industry or recent college graduates in computer-related majors often face difficulties in employment due to a lack of practical experience. Let’s look at two sets of data:
The 2023 cohort of national college graduates is expected to reach 11.58 million, with a challenging employment scenario;
According to data released during the National Cybersecurity Awareness Week, by 2027, China will have a shortfall of 3.27 million cybersecurity professionals.
On one hand, each year’s graduates face a tough job market. On the other hand“There is no national security without cybersecurity.” Currently, cybersecurity has been elevated to the level of national strategy, becoming one of the crucial factors influencing national security and social stability.
Characteristics of the Cybersecurity Industry
1. High salaries and rapid pay raises According to Liepin.com’s 2022 report, the average annual salary in the cybersecurity industry is as high as 337,700 yuan!
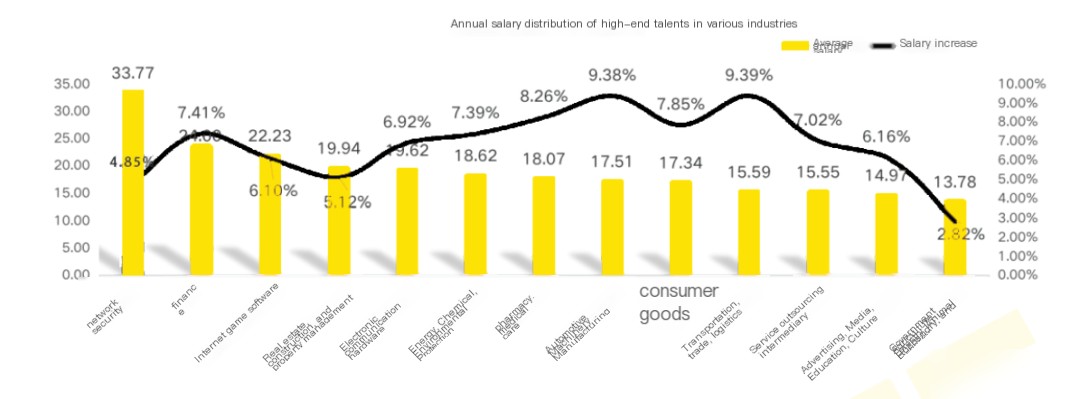
2. Significant talent gap and numerous job opportunities in open-source intrusion detection
On September 18, 2019, the official website of the Central People’s Government of the People’s Republic of China stated that the country needs 1.4 million cybersecurity professionals, but universities produce fewer than 15,000 trained professionals annually. Liepin.com’s “2021 H1 Cybersecurity Report” predicts that by 2027, the demand for cybersecurity professionals will reach 3 million, while currently, there are only 100,000 professionals working in the field.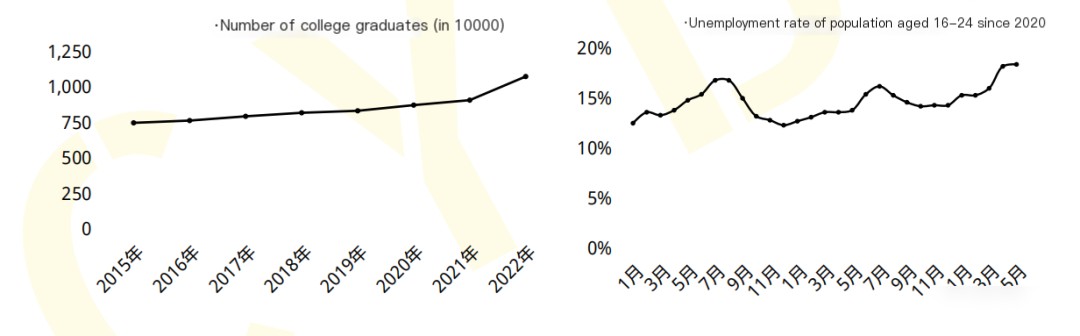
The industry’s development potential is vast, and there are many positions available.
Since the emergence of the cybersecurity industry, numerous job positions have been created, including: cybersecurity expert, cybersecurity analyst, security consultant, cybersecurity engineer, security architect, security operations engineer, penetration tester, information security manager, data security engineer, cybersecurity operations engineer, cybersecurity emergency response engineer, data forensics specialist, cybersecurity product manager, cybersecurity service engineer, cybersecurity trainer, cybersecurity auditor, threat intelligence analyst, disaster recovery specialist, and practical attack and defense specialist…
Great potential for career value enhancement.
The field of cybersecurity exhibits strong technical attributes, especially in mastering core network architecture and security technologies in the workplace, providing an irreplaceable competitive advantage in career development.
As personal capabilities continually improve, the career value of one’s role naturally increases with experience and project maturity, creating ample opportunities for career advancement, which is a primary reason for its popularity.
To some extent, the field of cybersecurity is akin to the medical profession: the older one becomes, the more valuable they are, as their techniques mature, naturally garnering more attention, with promotions and salary increases following suit.
How to Learn Hacking & Cybersecurity
Today, just by liking my article, I will share my collection of cybersecurity learning materials with you for free. Take a look at what resources are available.
1. Learning Roadmap
The industry’s development potential is vast, and there are many positions available.
Since the emergence of the cybersecurity industry, numerous job positions have been created, including: cybersecurity expert, cybersecurity analyst, security consultant, cybersecurity engineer, security architect, security operations engineer, penetration tester, information security manager, data security engineer, cybersecurity operations engineer, cybersecurity emergency response engineer, data forensics specialist, cybersecurity product manager, cybersecurity service engineer, cybersecurity trainer, cybersecurity auditor, threat intelligence analyst, disaster recovery specialist, and practical attack and defense specialist…
Great potential for career value enhancement.
The field of cybersecurity exhibits strong technical attributes, especially in mastering core network architecture and security technologies in the workplace, providing an irreplaceable competitive advantage in career development.
As personal capabilities continually improve, the career value of one’s role naturally increases with experience and project maturity, creating ample opportunities for career advancement, which is a primary reason for its popularity.
To some extent, the field of cybersecurity is akin to the medical profession: the older one becomes, the more valuable they are, as their techniques mature, naturally garnering more attention, with promotions and salary increases following suit.
How to Learn Hacking & Cybersecurity
Today, just by liking my article, I will share my collection of cybersecurity learning materials with you for free. Take a look at what resources are available.
1. Learning Roadmap
There is a lot to learn regarding both attack and defense. I have outlined everything in the above roadmap. If you manage to complete all of it, you will have no problem securing a job or freelance work.
2. Video Tutorials
Although there are many learning resources online, they are often incomplete. These are the cybersecurity video tutorials I recorded myself, with a corresponding video explanation for each knowledge point in the roadmap above.
The content covers essential cybersecurity learning topics such as learning cybersecurity laws, cybersecurity operations, protection evaluation, basic penetration testing, vulnerability details, and basic computer knowledge.
3. Technical Documents and eBooks
The technical documents are my own compilation of experiences and key points from participating in significant cybersecurity operations, CTFs, and SRC vulnerability hunting. There are also over 200 eBooks. Due to the sensitivity of the content, I won’t list them all here.
4. Toolkits, Interview Questions, and Source Codes
“A craftsman must sharpen his tools before he can do his work well.” I have summarized the most popular hacker tools for everyone. They mainly focus on information gathering, Android hacker tools, automation tools, and phishing, among others. Interested students should not miss this.
Additionally, there are source codes and toolkits for the cases discussed in my videos, which are available if needed.
These questions are often encountered during interviews with companies like Sangfor, Qi An Xin, and Tencent. If you have good questions or insights, feel free to share them.
Reference analysis: Sangfor official website, Qi An Xin official website, Freebuf, CSDN, etc.
Content characteristics: Clear structure, includes visual representations for better understanding.
Content overview: Includes internal network, operating systems, protocols, penetration testing, security services, vulnerabilities, injections, XSS, CSRF, SSRF, file upload, file download, file inclusion, XXE, logical vulnerabilities, tools, SQLmap, NMAP, BP, MSF…
Due to space constraints, only some materials are displayed. Click the link below to access the full extent
If you are interested in getting started with cybersecurity, click here 👉 Cybersecurity Grand Benefits: Beginner & Advanced Complete 282GB Learning Resource Package Free Shared! Ways to learn cybersecurity technology are mainly threefold:
The first way is to enroll in a cybersecurity major, now called the cyberspace security major. The main courses include: program design, computer organization principles, data structures, operating system principles, database systems, computer networks, artificial intelligence, natural language processing, social computing, cybersecurity laws and regulations, network security, content security, digital forensics, machine learning, multimedia technology, information retrieval, and public opinion analysis.
The second way is self-study, which involves finding resources and tutorials online or trying to connect with experts. However, this method can be time-consuming and lacks structure, potentially leading to long periods of feeling unprogressive, which can be discouraging.
If you are interested in getting started with cybersecurity, click here 👉 Cybersecurity Grand Benefits: Beginner & Advanced Complete 282GB Learning Resource Package Free Shared!
The third way is to find a training program.
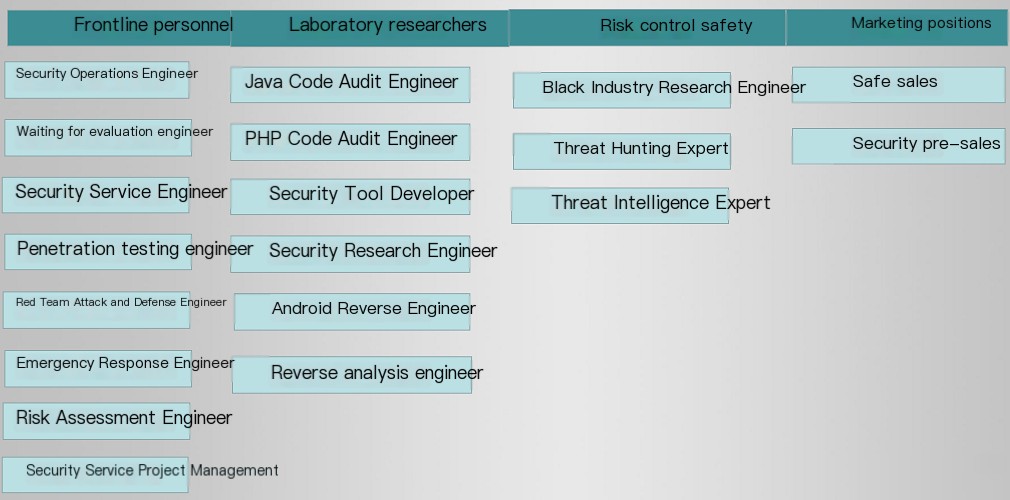
Next, I’ll teach you how to quickly get started with cybersecurity from scratch.
Should you learn programming or basic computer skills first when starting with cybersecurity? This is a highly debated question. Some recommend starting with programming, while others suggest beginning with basic computer skills. Both are indeed critical for learning cybersecurity. However, for complete beginners or those eager to switch careers, both learning programming and basic computer skills can be challenging and time-consuming.
Stage One: Basic Preparation (4-6 Weeks)
This stage includes essential learning for entering the security industry. As the saying goes: “Without a solid foundation, the ground will shake.” 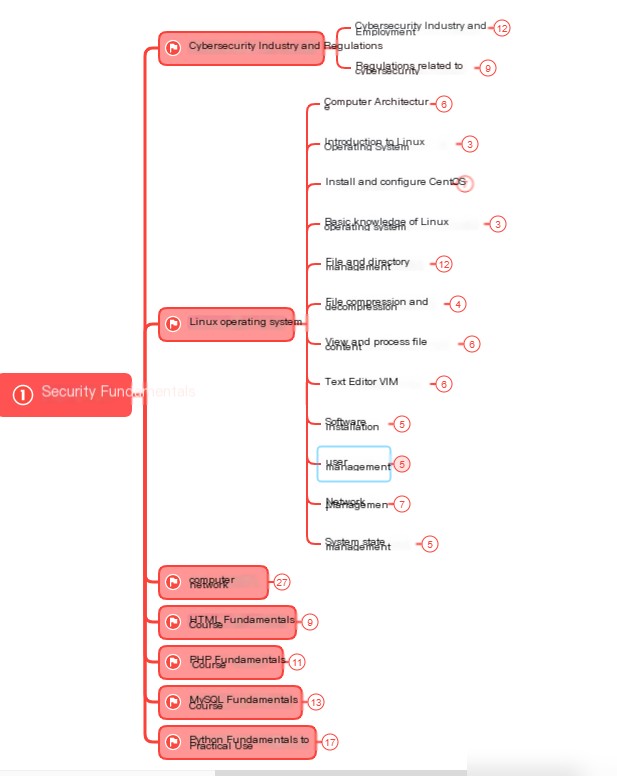
Stage Two: Web Penetration
Basic Learning Time: 1-2 Weeks:
① Understand basic concepts such as SQL injection, XSS, uploads, CSRF, and webshells to lay a foundation for future web penetration testing. ② Check out forums for web penetration tips and learn the thought process behind different cases as each site is unique. ③ Master the art of asking questions—don’t hesitate to ask if you do not understand something. 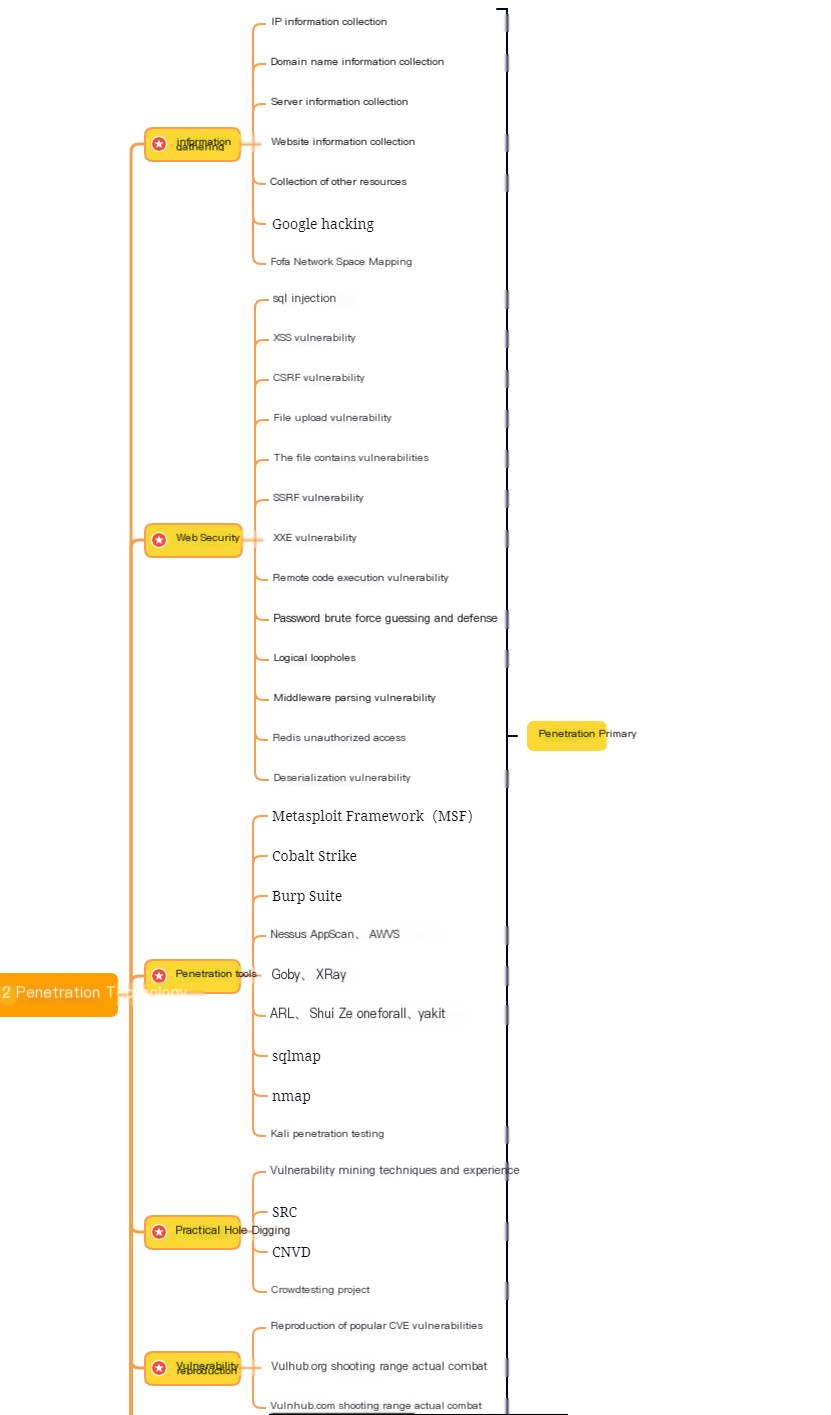
Configuring Penetration Environment Time: 3-4 Weeks:
① Familiarize yourself with commonly used penetration testing tools like AWVS, SQLMAP, NMAP, BURP, China Chopper, etc. ② Download and install backdoor-free versions of these tools. ③ Understand the usage scenarios of these tools and learn their basic usage, recommended to search on Google.
Practical Penetration Operations Time: About 6 Weeks:
① Search for real-world penetration cases online, thoroughly study the use of SQL injection, file upload, parsing vulnerabilities, etc., from practical scenarios. ② Set up a vulnerable environment for testing, recommended DWVA, SQLi-labs, Upload-labs, bWAPP. ③ Understand the stages of penetration testing and actions needed at each stage, referring to PTES (Penetration Testing Execution Standard). ④ Get in-depth knowledge of manual SQL injection, find ways to bypass WAF, and develop your own scripts. ⑤ Study the principles of file uploads, how to conduct truncation, double-extension deception (IIS, PHP), and parsing vulnerability exploitation (IIS, Nginx, Apache), referring to: upload attack frameworks. ⑥ Learn the principles and types of XSS, practice using DWVA, implement XSS vulnerabilities in a CMS, and test using security software. ⑦ Understand the concept of a webshell and try writing a bypass anti-virus webshell. ⑧ Explore privilege escalation techniques on Windows and Linux; Google the keyword “privilege escalation.”


